In partnership with vx-underground, SentinelOne recently ran its first Malware Research Challenge, in which we asked researchers across the cybersecurity community to submit their research to showcase their talents and bring their insights to a wider audience.
In today’s guest post, researcher Natacha Bakir (Senthorus/Cefcys) digs into the destructive world of wipers: a special class of malware that has neither espionage nor financial gain in mind, but exists solely to destroy data and disrupt the services provided by an organization to its consumers. From MeteorExpress to AcidRain and HermeticWiper, the current increase in the use of wipers since the start of Russia’s invasion of Ukraine has been unprecedented and is a subject worthy of greater attention.

In February 2022, Ukraine was targeted by a new malware named ‘HermeticWiper’. Amid reports of ransomware incidents increasing by 62% in 2021, and the number of ransomware attacks estimated at 236.1 million in the first half of 2022, this new malware, as sophisticated as it was, had a simple goal: to erase the target’s disks.
While wipers have been known for over 10 years, a significant rise in this destructive kind of malware has been noted since 2022. In this post, I will briefly discuss the history of wiper malware before focusing on the the techniques used in some of the most recent attacks.
History of Wipers
2012 was an important year for wipers. On August 15th, Shamoon wiped 30000 systems within a day. The New York Times estimated that 75% of the victim’s computers had been wiped. At the time, it was one of the most destructive attacks ever seen. A group calling itself “Cutting Sword of Justice” claimed responsibility for the attack, blaming the al-Saud regime for crimes against humanity.
In 2015, an attack on the Ukraine Power grid caused a power outage for nearly a quarter of a million people. It was coordinated with a Denial-of-service attack on a call center to deny consumers up-to-date information on the blackout.
In 2022, WhisperGate wiper targeted multiple organizations in Ukraine. The wiper was later seen throughout the world.
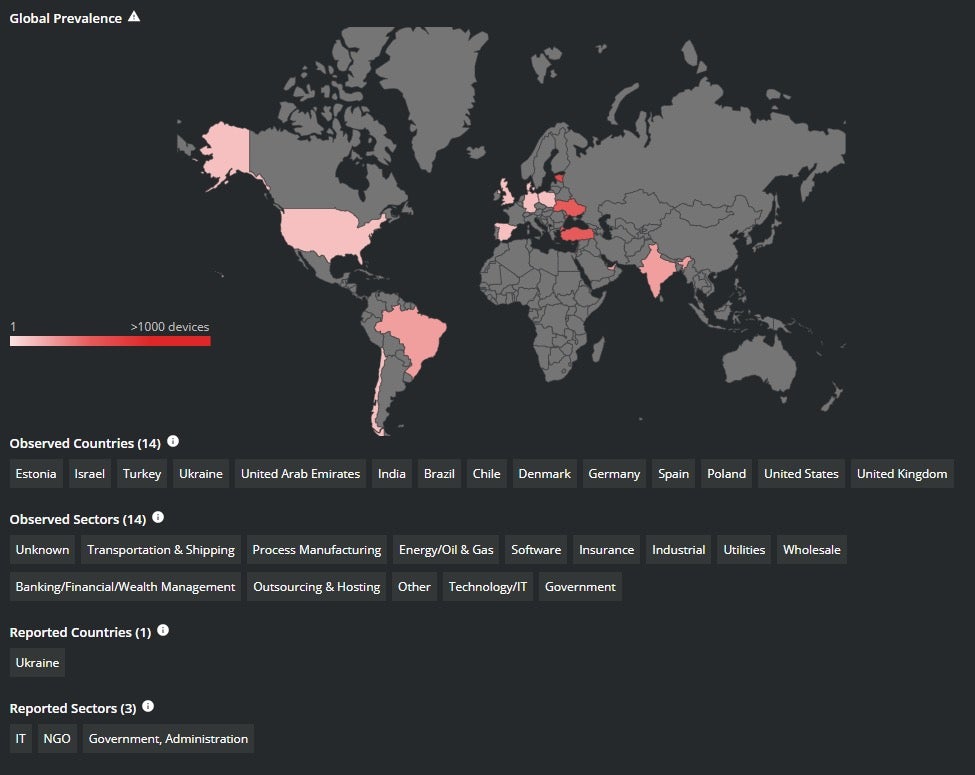
The WhisperGate wiper had a decoy ransom note to mislead Incident Response teams. The wiper analyzes the victim’s environment enumerating OS attributes and disks to improve their access and gain the desired privileges to disarm the victim and attack.
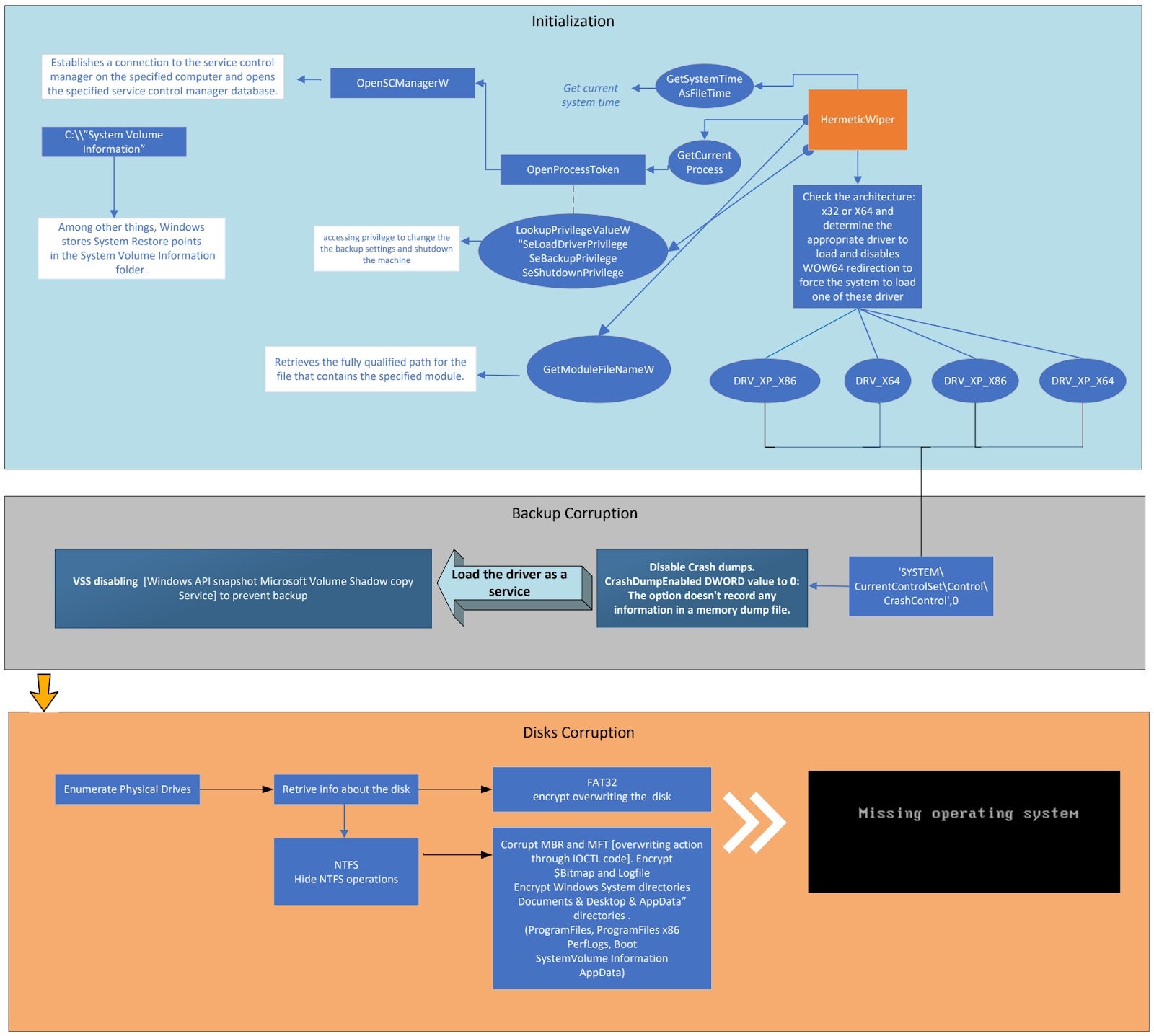
In February 2022, HermeticWiper was dropped on victims via a compressed package, creating the EaseUS driver file, and enumerating the physical drives. The driver then loads and runs as a service. The driver is used through execution codes [dwIoControlCode] to overwrite the master boot record (MBR) and the master file table (MFT) before restarting the system.
In January 2023, ESET researchers uncovered a new wiper attack targeting Ukraine called SwiftSlicer. The wiper uses Active Directory Group Policy and is written in Go. ESET attributed this attack to Sandworm.
#BREAKING On January 25th #ESETResearch discovered a new cyberattack in 🇺🇦 Ukraine. Attackers deployed a new wiper we named #SwiftSlicer using Active Directory Group Policy. The #SwiftSlicer wiper is written in Go programing language. We attribute this attack to #Sandworm. 1/3 pic.twitter.com/pMij9lpU5J
— ESET Research (@ESETresearch) January 27, 2023
Wiper Techniques
Wipers primary goal is to destroy data. This can cause disruption and service outage affecting not just the organization targeted but entire populations. Wipers can also be deployed after an initial attack, in order to erase evidence. Although wipers can be disguised as ransomware and ask for a ransom, they don’t offer the capability to recover data and the goal is not financial gain, but rather a diversionary tactic while data is erased.
Depending on the hacker’s goal (discretion, speediness), several techniques of wiping are used, including:
- enumerating the filesystem
- overwriting the disks with other data like zero (0x00) bytes
- corrupting MBR and MFT
- fragmenting disks
- using driver to gain kernel access
- pass order through IOCTL
DeviceIoControl()function.
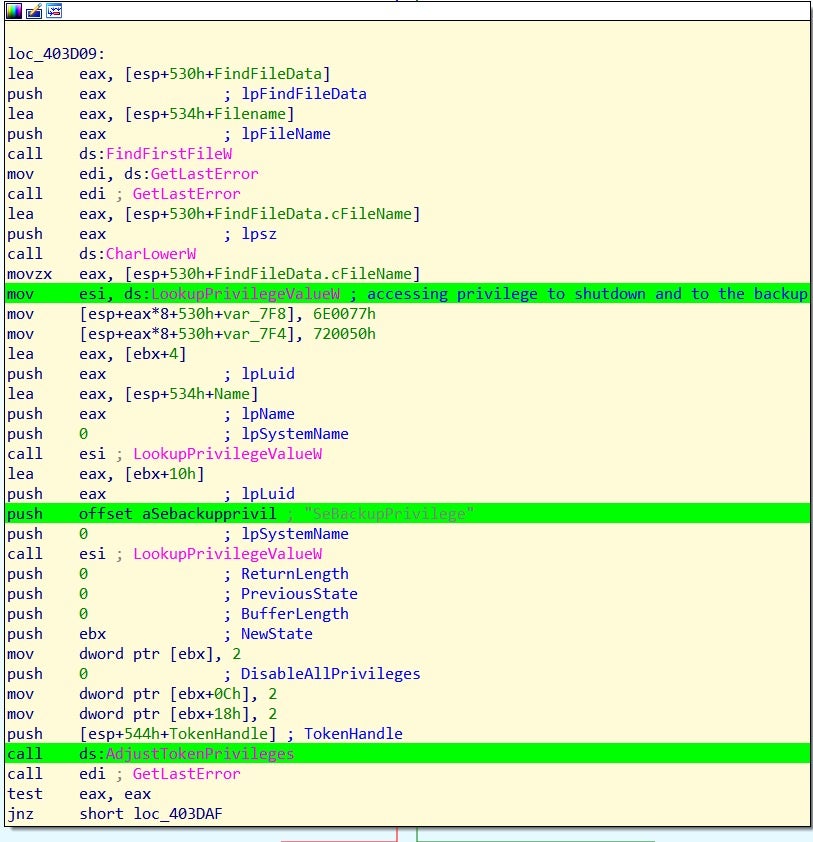
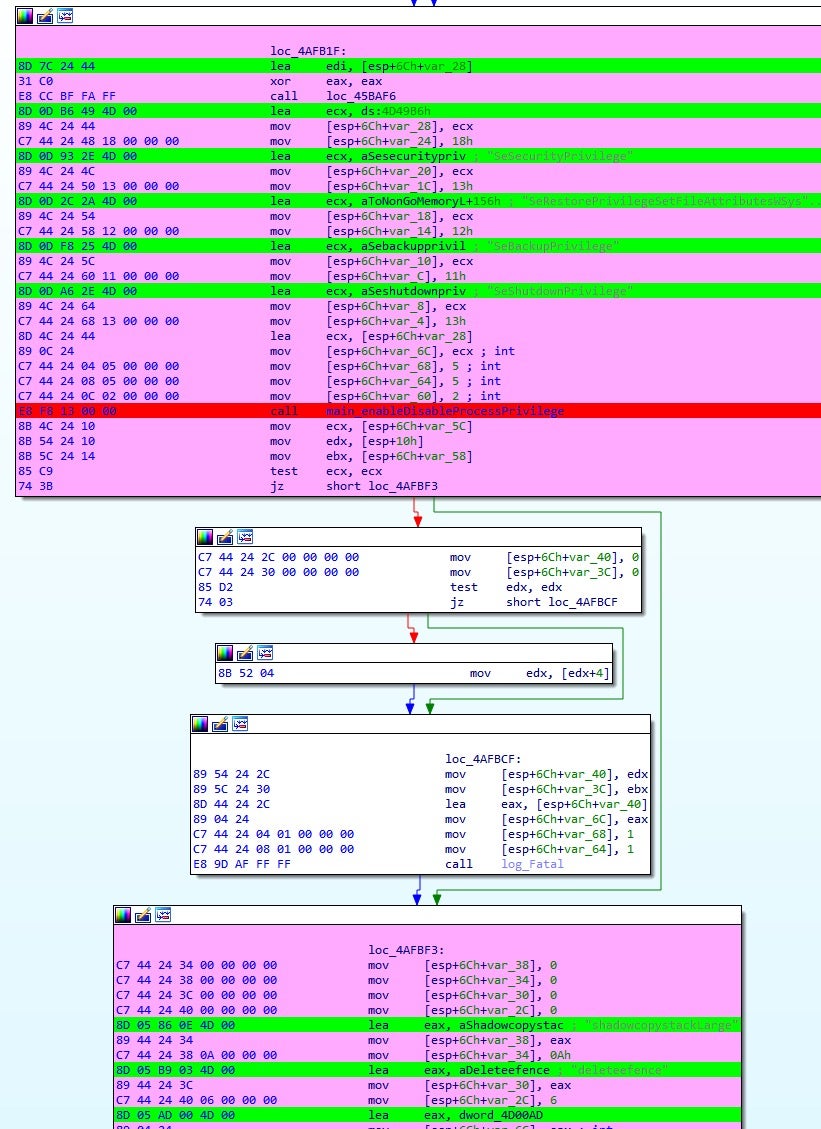
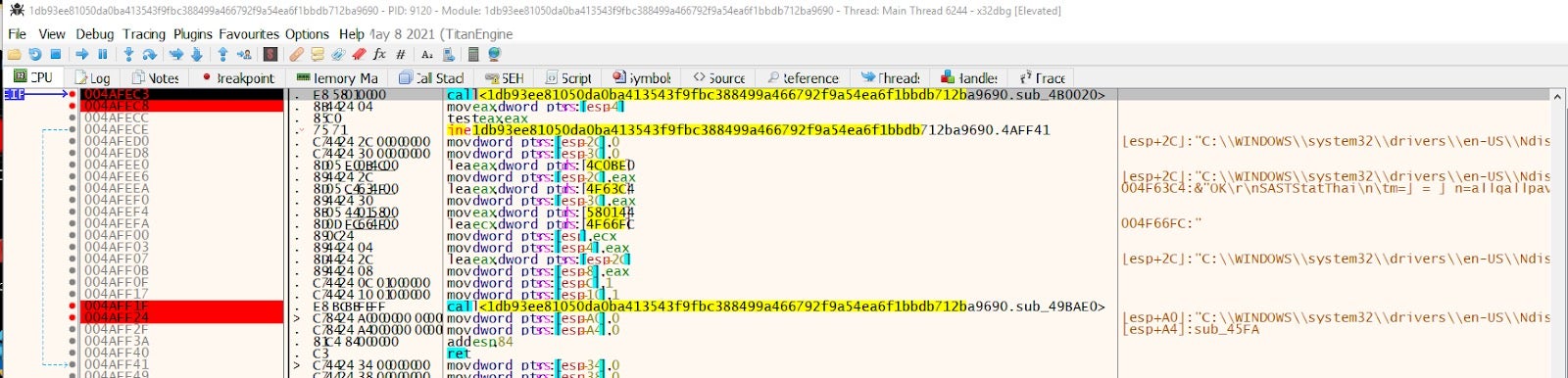
[caption] SwiftSlicer disassembly
Given the simplicity of the goal, Wipers can be written in many different programming languages. Although SwiftSlicer is written in Go, similarities in the malware’s functionality can clearly be seen.
The Ukrainian CERT-UA reports that SwiftSlicer was distributed to network computers through GPO (Group Policy Object), the same method used to deploy most of the malware mentioned in this article.
They also noted that the malware targets the %CSIDL_SYSTEM_DRIVE%\Windows\NTDS folder, showing that SwiftSlicer tries to destroy files and bring down the entire Windows domain.
Why Write a Wiper in Go?
Go is increasingly used in malware programming. With Go, malware developers can write code once and compile binaries from the same codebase for multiple platforms. As a result, they can target different operating systems like Unix, Linux, Windows and those that work on mobile.
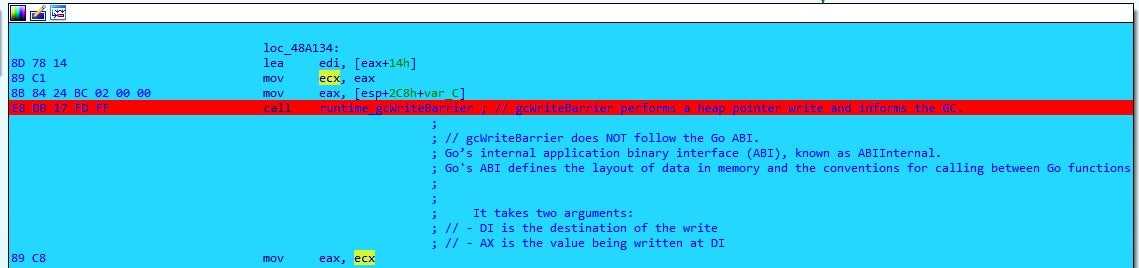
In addition, Go programs can be difficult to analyze. The arguments are not passed through registers but are directly copied onto the stack at the correct position. Further, Go functions can have multiple return values, so static analysis is limited. Typically, when reversing go malware, analysts will need to use dynamic analysis, such as isolating interesting functions by name and using a debugger to break on interesting calls to inspect the program’s state.
Conclusion
Wiper malwares are not new, and even Russia’s use of them against Ukraine can be dated back to interference in the Ukraine Presidential Election of 2014. However, the extent of the use of wipers by Russian APT groups, especially Sandworm, against Ukrainian targets is something not seen previous to this conflict.
Whether used for sabotage or cyberwarfare, wipers cross the boundary of the virtual to the real, with the potential to wreak devastating effects on those far beyond the organization targeted.


