The Good
Schools are trying to get kids back to their desks while also dodging outbreaks of viruses both physical and cyber. Fortunately, at least one roadblock was flattened when a 16-year-old student at South Miami Senior High was charged with launching a DDoS that paralyzed the school district’s computer network for the first three days of virtual classes. Over those three days, all students saw when they tried to log in for the new school year were error messages.
Make that a pummeling of attacks: The Miami-Dade school district said last week that the student admitted to pulling the strings behind eight DDoS attacks targeting the district’s networks, including the web-based systems needed for its online learning platform, called My School Online.

The school system has actually been targeted about two dozen times since the school year began, according to the Miami Herald. Investigators are trying to figure out who else might be behind the attacks besides the student, who admitted to succeeding with an embarrassingly basic attack: He used a decade-old, open-source tool called a Low Orbit Ion Cannon (LOIC) that even the most bare-bones firewall should be able to catch.
The Bad
Zeppelin ransomware has wafted back, again casting its shadow over IT and healthcare providers. This time, it’s picked up an obnoxious passenger: a new Trojan downloader that helps it to sneak around antivirus apps and evade detection.
Analysts at Juniper Threat Labs say that the misery starts with a Microsoft Word document that has a malicious macro hiding in its gut. The rigged email, which aims to lure victims into enabling VBA macros that will trigger infection, includes a blurred “invoice” and text box that are actually just images.
Push the blurry bits aside, and you’ll find random gobbledygook that actually hides snippets of Visual Basic scripts. The Visual Basic interpreter extracts the garbage text from the document, treats it as commented-out code, and ignores it, leaving just the malicious commands. Strip it down to just those commands and you get to the meat of the matter: a Zeppelin ransomware.exe that sleeps for 26 seconds as it tries to out-wait dynamic analysis in an automated sandbox before going on to run the ransomware executable.
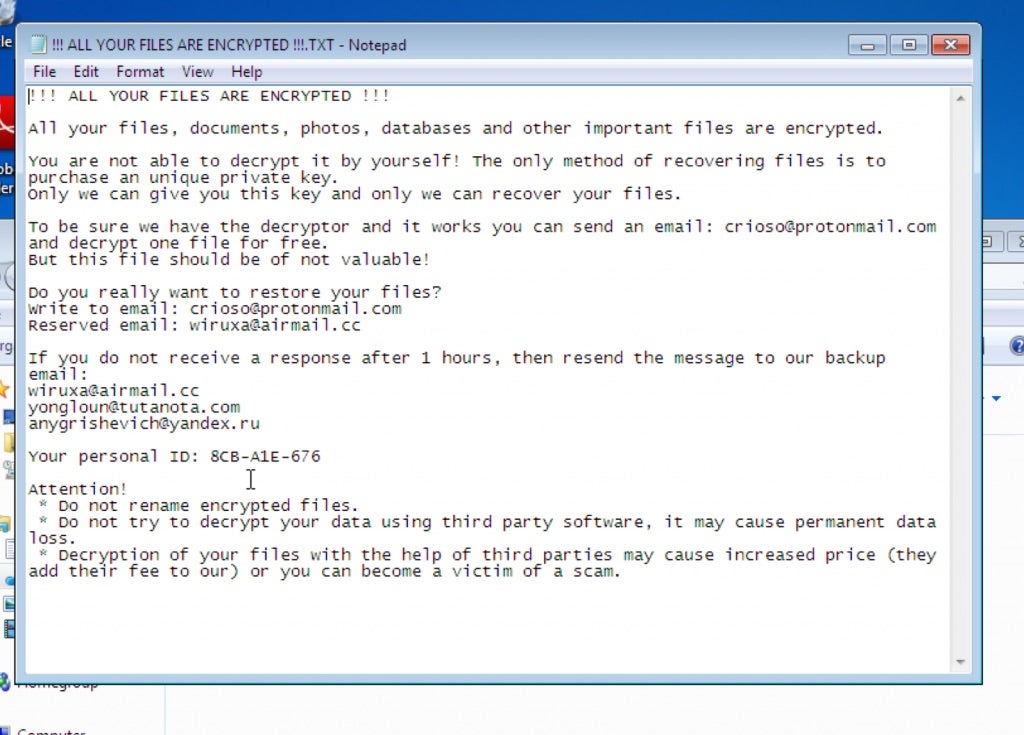
As you can see, the ransom note includes its own mini helpdesk manual warning users against trying to rename or decrypt files. The crooks’ argument: You don’t want to add to the cost of your ransom by paying for help that won’t work, now do you? Besides, “you can become the victim of a scam”, the Zeppelin crooks ironically caution their victims. So helpful!
The Ugly
As they struggle to open, schools aren’t just dealing with the COVID-19 pandemic. They’re also dealing with an onslaught of ransomware attacks; DDoS attacks like the one I mentioned above in Miami-Dade, for which police arrested a high school student; and Zoom-bombing: all of it conspiring to delay children’s return to school.
As Threat Post reports, just this week we saw ransomware attacks on the school districts in Hartford, Conn. and Clark County, Nev. On Tuesday, Hartford Public Schools said that a ransomware attack had postponed school openings, both for in-person and online learning. AP reports that yesterday—Thursday, Sept. 10—the Clark County School District in Nevada said that it, too, experienced a ransomware attack during the first week of school and that some employee personal information may have been exposed.
In fact, according to Recorded Future, so far, there have been nine recorded ransomware attacks against school districts in July, August and September. That might sound bad, but it’s been worse: Last year, Recorded Future collected data from hacker forums, threat feeds, news reports and code repositories that showed that at least 15 school districts had been hit by ransomware attacks during a two-week period in September 2019.
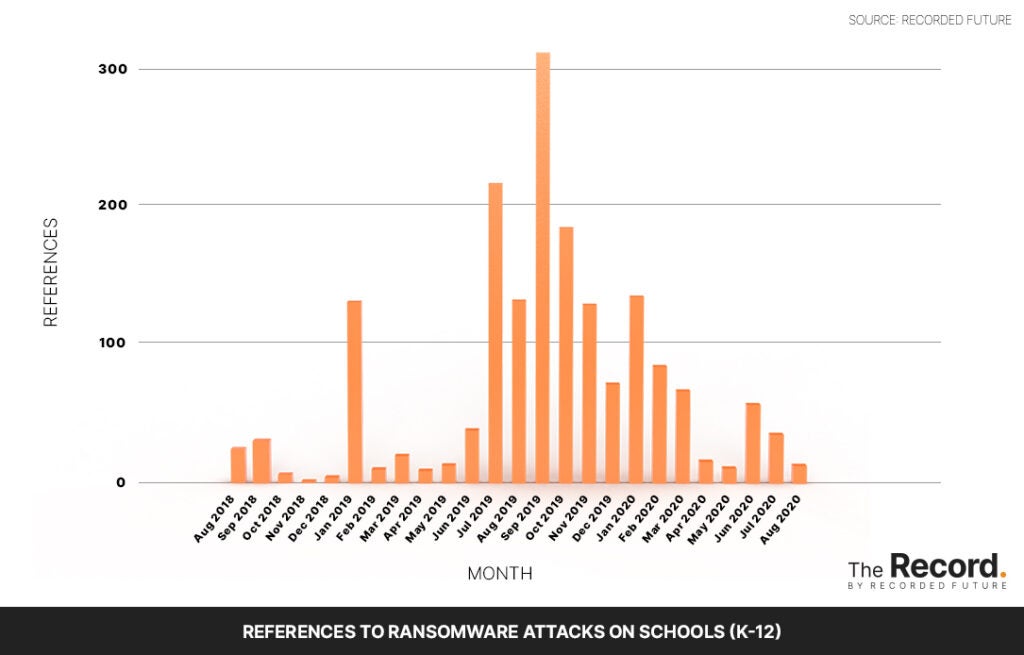
Allan Liska, a ransomware specialist at Recorded Future, said that the shift to remote learning might actually cause the trend to point downward. “We are definitely in an uncharted territory,” Liska said. “There has been a small uptick in ransomware attacks as schools get back into session, but with so many school systems going remote this semester there is a much smaller attack surface for the ransomware groups to target.”
Let’s hope he’s right: The kids need a break.


