The Good
This week saw a number of security updates and fixes as part of Microsoft’s “Patch Tuesday” release on August 10th. Notable among them was the inclusion of a fix for the recently disclosed PetitPotam attack (aka CVE-2021-36942). This flaw was originally discovered by researcher Gilles Lionel (aka Topotam), and is a novel NTLM-relay attack which provides enterprising attackers a simple way to overtake exposed domain controllers. Once they have established a presence on the DCs, full environment takeover is trivial.

Essentially, “PetitPotam” provides quick access to the ‘keys to the kingdom’, or maybe a better analogy would be to the ‘battering ram to the kingdom’. According to Microsoft’s advisory, PetitPotam takes advantage of servers where Active Directory Certificate Services (AD CS) is not configured with protections for NTLM Relay Attacks. Organizations are potentially vulnerable if they use AD CS with either Certificate Authority Web Enrollment or Certificate Enrollment Web Service.
Seeing this fix included in the August patch cycle from Microsoft will be a welcome relief for many. We encourage all enterprise security teams to review the guidance from Microsoft and take appropriate action to reduce exposure and mitigate the risk of exploitation via CVE-2021-36942.
The Bad
This week saw another high-profile ransomware attack and another threatened leak of sensitive corporate data unless the victim pays a hefty sum, rumored to be around the $50 million mark. The attacker and victim in this case were criminals using LockBit ransomware and global consulting firm Accenture, respectively.
According to various news sources, Accenture was able to restore affected systems from backups by Wednesday, limiting disruption to services, but the threat to leak up to as much as 6TBs of the company’s data still stands.
In common with other ransomware groups, the LockBit operators publish a countdown timer to pressure victims to pay up within a few hours. Notably, the LockBit timer for Accenture has reset at least once, suggesting either that the operators were experiencing some technical issues or, perhaps, that negotiations are ongoing and require more time to resolve.
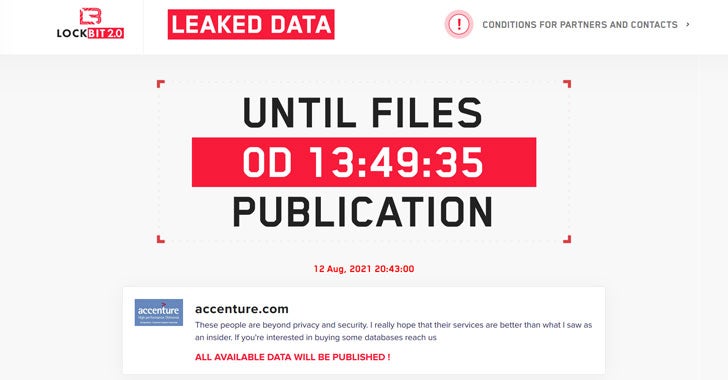
Meanwhile, the leaks site added ‘Dudos every day” to the Accenture entry, which some have interpreted to mean “DDoS every day”. At present, we have not been able to confirm if indeed Accenture is also being hit with DDoS attacks, but the tactic is not uncommon among ransomware threat actors.
LockBit 2.0 has been around since early 2020, and by some estimates has hit anywhere between 10,000 and 40,000 victims in that time. In order to attract affiliates (criminals who pay the operators for use of the ransomware), the operators have made various unconfirmed claims that LockBit 2.0 can encrypt and exfiltrate data much faster than competing ransomware services. Whether these claims are true or not is less important than whether they are believed and encourage others to buy the service and use it to attack organizations. Given the number of estimated incidents, it seems likely that the operators have been reasonably successful in that regard.
The Ugly
This week’s ‘Ugly’ could be the tale of a Robin Hood, or a bad guy caught red-handed and trying to change the narrative to avoid jail time. Whichever way you look at it though, it’s less than pretty from some angle. The story begins with what has been described as one of the “biggest heists to target the cryptocurrency industry” after an estimated $600 million worth of crypto coins were stolen from tens of thousands of wallets on Tuesday.
The heist involved a hacker exploiting a vulnerability to breach decentralized finance (DeFI) platform Poly Network. However, as of Thursday, it appears that around half of the coins had been returned and the remaining assets “gradually transferred”.
An individual claiming to be responsible for the attack said they had never intended to steal the money but were merely holding on to it for “safe keeping”. Hmmm.
A competing explanation goes like this. Having read Poly Network’s later tweet stating that “Law enforcement in any country will regard this as a major economic crime and you will be pursued”, and their advice that the hacker should “return the hacked assets” and “talk to us to work out a solution”, that that is exactly what the hacker did.
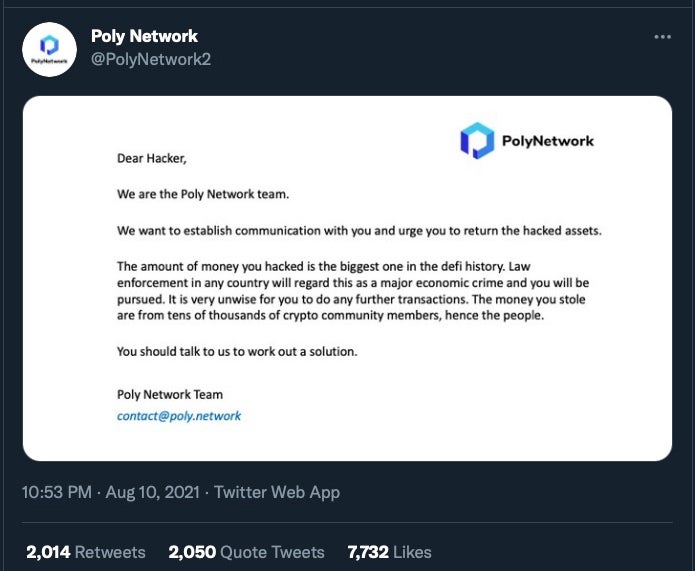
Realizing that cashing out that kind of haul would have been impossible and that, indeed, the chances of getting away with such a huge crime were incredibly low, the hacker may well have decided to take up the offer and try to change the narrative of what happened.
“White hat” researcher? We don’t think so. That’s not the way good guys operate. On the other hand, despite what appears to be the safe return of the money, trust in Poly Networks could now be seriously dented. The company will have some serious PR work to do convincing current and prospective members that their digital assets are safe from now on.


