The Good | High-Severity Flaws Patched in Firefox and Chrome Updates
Browsers are our windows to the internet and due to both their ubiquity and the amount of information they collect, they are often prime targets for threat actors, so there’s good news for Firefox and Chrome users this week as new security patches have been rolled out for both.
On Tuesday, Mozilla released new versions of Firefox 116, Firefox ESR 115.1, and Firefox ESR 102.14, which all include patches for several high-severity vulnerabilities, most prominently CVE-2023-4045, CVE-2023-4046, and CVE-2023-4047. The new iterations prohibit HTML and JavaScript code displayed on one site from accessing content on another site, correct a potentially exploitable crash caused by wrong values during WASM compilation, and resolve a clickjacking issue where users are tricked into giving up risky permissions for microphone, location, and notification services.

On the Google side, the tech firm handed out over $60,000 in bug bounties for three high-severity type confusion vulnerabilities in Chrome’s V8 engine. The latest update, Chrome 115, addresses six other severe flaws relating to issues such as a heap buffer overflow problem which often results in unpredictable behavior or generates incorrect results, crashes, or memory access errors, an insufficient data validation bug, and an inappropriate implementation issue. Users are encouraged to update to versions 115.0.5790.170 for Mac and Linux and to versions 115.0.5790.170/.171 for Windows.
The Bad | More Vulnerabilities Found in Ivanti’s Mobile Device Management Product
Following a maximum severity bypass vulnerability reported last week by Ivanti, the Utah-based IT firm has since issued warnings for two more vulnerabilities also found in its Endpoint Manager Mobile (EPMM) software.
The first of the two is a new path traversal vulnerability, tracked as CVE-2023-35081 (CVSS 7.2), allowing arbitrary file write capabilities. Threat actors exploiting this vulnerability could potentially bypass admin authentication and ACL restrictions to execute OS commands. All supported versions of EPMM, including releases 11.10, 11.9, 11.8, and older are impacted.
The company says that this new vulnerability differs from July’s CVE-2023-35078; however, it acknowledged that attackers could chain the two together for malicious purposes. A joint cybersecurity advisory from both CISA and the Norwegian National Cyber Security Centre (NCSC-NO) explains that chaining the two flaws could translate to privileged access across EPMM systems and the ability to execute uploaded files such as webshells.
👇 Another one for the same product: CVE-2023-35082, CVSS 10.0 😳
👉 Search: https://t.co/T9uvu0P8Wr
👉Advisory: https://t.co/1o2GQSgkgm#vulnerability_map #cybersecurity https://t.co/w6TnuJpSFe— Netlas.io (@Netlas_io) August 3, 2023
The second vulnerability announced this week is tracked as CVE-2023-35082 (CVSS 10.0) and could allow unauthenticated attackers to access the API in older, unsupported versions of the product (11.2 and below).
If exploited, attackers could access users’ personally identifiable information (PII) and make unauthorized changes to the server. Security researchers noted the bug’s close relation to last week’s remote unauthorized API access flaw in that both target the permissive qualities of certain entries in the mifs web application’s security filter chain.
Ivanti has released patches for all three vulnerabilities within the span of two weeks and urged its customers to upgrade to the latest version of EPMM and monitor their systems for signs of breaches.
The Ugly | Microsoft Domains Leveraged in Russian-Backed Teams Phishing Campaigns
Cyber threat group APT29, attributed to Russia’s Foreign Intelligence Service (SVR), was linked this week to a series of attacks on dozens of organizations. Likely indicative of an espionage campaign, the group targeted government agencies, non-government organizations (NGOs), IT and tech services, private manufacturing, and media sectors through phishing messages sent via Microsoft Teams.
According to a report released Wednesday, the attackers used compromised Microsoft 365 tenants to create tech support-themed domains and sent various social engineering lures to trick victims into granting approval for multi-factor authentication (MFA) prompts. The new domains were part of a legitimate Microsoft domain ‘onmicrosoft.com’ that is used when a custom domain is not successfully created.
Using this domain, the spoofed tech support messages would have appeared more trustworthy to the targeted users.
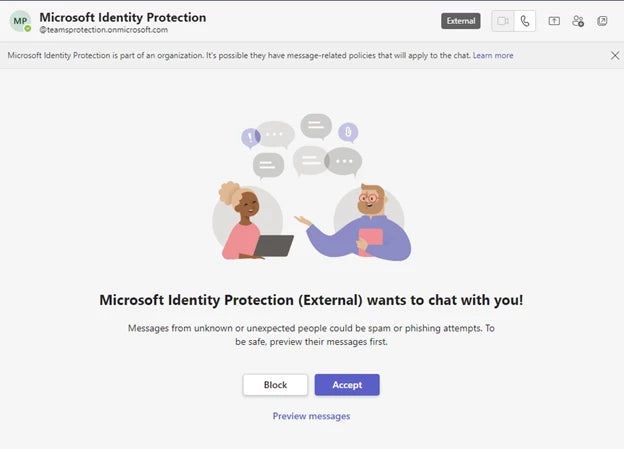
APT29 has been operating since at least 2008, crafting attacks against government networks in NATO member countries and in Europe, think tanks, and research institutes. Notoriously, the group is attributed to the SolarWinds supply chain attack that led to the compromise of as many as 18,000 government entities and Fortune 500 companies, at least nine federal agencies, and more than 100 businesses globally.
This latest activity is a timely reminder of just how pernicious and persistent these groups are, and organizations in all verticals are urged to be equally relentless in reinforcing strong cyber hygiene and continued awareness and education efforts.


