Chromebooks and ChromeOS have earned themselves a deserved reputation for being more secure than many other devices and operating systems, so much so that “Chromebooks don’t get viruses” is the new “Macs don’t get viruses”. But as many Mac users of the past will now tell you today, complacency in taking proper security measures is the first step on the path to compromise.
The popularity of Chromebooks among students and in educational institutions means they provide an enticing target to threat actors looking to scoop up PII for sale, or credentials to leverage in targeted attacks. Chromebooks may not have the same kind or number of security problems as, say, Windows devices, but that’s not to say there are not genuine threats that ChromeOS users need to be aware of.

1. Actors Actively-Exploiting Chrome Zero Days
One of Chromebooks’ most-vaunted security features is its ability to check and repair the integrity of the operating system on reboot. It’s a great feature and one partly copied by Apple’s macOS, where Apple’s signed system volume (SSV) protection checks the integrity of the OS on boot.
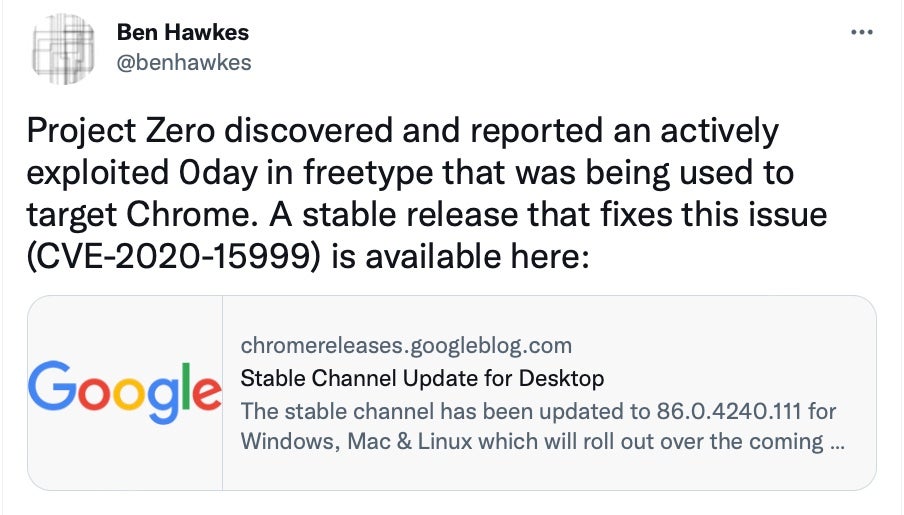
But such a system cannot protect the user or their data against zero-days that are invisible to the operating system. Flaws like CVE-2020-15999 were found to be actively exploited in the wild and needed Google to push out an update to protect users after-the-fact.
Google fixed another actively-exploited Chrome zero-day, CVE-2021-21148, in 2021. While details of how these bugs were deployed against users in the wild is scarce, the fact that Google stated they were “actively exploited” should be enough to tell Chromebook users that the device and the OS is being targeted and attackers are finding ways through.
And indeed, there is no shortage of high-risk bugs being found in Chrome and ChromeOS by security researchers. 2021 alone saw Google patch over 300 bugs, with some 260 or more related to potential or actual remote attacks.
2. Android Apps and App Stores
When Chromebooks were first introduced, they were touted as being highly secure because they prevented the most common way for security compromises to occur: the download and execution of executable files. The only problem was, Chromebooks weren’t that useful. Most people’s computing needs extended beyond the reach of the limited, and sometimes clunky, web apps being offered by Google.
Since those days, Chromebooks have gained the ability to download many different kinds of apps, increasing both their utility and their attack surface at the same time. Android apps give Chromebooks more versatility, but Android malware is also extremely common.
In November 2021, researchers discovered four different families of malware infecting more than 300,000 Android devices via malicious apps downloaded from Google Play Store. The threat actors had uploaded initially benign apps to get past Google’s automated review, then later delivered banking trojan malware to select users via an app update.
In January 2022, researchers reported another financially motivated scamware campaign dubbed Dark Herring that, they say, poses a threat to all devices capable of running Android apps. The threat actors behind Dark Herring uploaded almost 470 malicious apps to the Google Play store and achieved over 100 million installations.
3. Sideloading Linux and Linux Apps
Making Chromebooks more useful has been one of the major demands of its users over the years, and back in 2018 they got their wish when Google made it possible to run Linux apps and share the ChromeOS downloads folder with a natively-hosted Linux VM. Perfect for developers and others that want to do more with their Chromebook device. The catch? An increased attack surface. Linux malware may not be common in comparison to Windows, but it’s on the rise, by 35% in 2021 according to some estimates.
The question for those managing Chromebooks that allow Linux app installations, as with Android app installations, is what to do about visibility? In other words, if you did get hit by some Linux malware, how would you know? On top of that, ChromeOS has no native security mechanisms that can protect, detect or mitigate Linux-based malware.
4. Windows Malware on ChromeOS? Oh, Yes (Oh, No!)
Despite Google’s best intentions, it seems that in the end everything comes full circle. The original idea to deliver an OS that didn’t have Windows’ horrific problem with malware is finally undermined when it turns out that savvy users can in fact install Windows 10 apps if they choose.
But who would do that? Well, for one, users coming from a Windows background. Many students and teachers were brought up on Windows machines and Microsoft software, and old habits–and dependencies–die hard. Data that may be locked in proprietary software or just software that users are long-habituated to can now be accessed on a Chromebook by running Windows apps on ChromeOS.
On older versions of ChromeOS, they would have been out of luck, but thanks to the ability to run Linux apps discussed above, they can also install WINE, a Windows emulator, and with WINE they can download and execute Windows 10 applications.
Running Windows apps on a Chromebook doesn’t mean you will get malware, anymore than running Windows apps on a PC means you will get malware. But it does mean the attack surface has now opened up and the Chromebooks original promise–no downloading or launching of local, executable files–is entirely broken.
5. Malicious Chrome Extensions
Browser extensions have always been a security problem on every platform, and with ChromeOS’s heavy reliance on the Chrome browser, some of its biggest security headaches have been around users unknowingly installing malicious extensions.
The situation was particularly bad up until 2019, until Google started tackling the problem in more earnest, but the problem of malicious Chrome extensions is still with us in 2022.
6. Google Chromebook, The Internet and Scams
Chromebooks originally made their name on the concept of having users do everything in the cloud and on the web, but the internet is a dangerous place. The web only works because of JavaScript, and malicious websites that take advantage of the powers of JavaScript are easy to come across even during the safest of searches.
Some extortion sites use JavaScript to lock a user’s browser and try to extort money in order to “free” the computer. Others offer phoney ‘cloned’ login pages of popular websites in an attempt to steal credentials.
As with any other device, Google Chromebooks are susceptible to man-in-the-middle (MiTM) attacks when using public Wi-Fi. Coffee shops, beloved by study groups and tutors, are a prime location for an attacker to set up a fake network and sniff traffic. While encryption between the browser and most websites these days offer better protection than in the past, attackers can still scrape useful data that may help them target or profile users.
Secure Your Chromebooks Like Any Other Device
Here’s a simple truth that the recent history of malware and cyber attacks has proven time and time again: all computing devices are at risk of compromise if they contain valuable data, or are connected to a network where other devices contain valuable data. There is no such thing as a device or OS that can’t get malware. Threat actors have successfully exploited every kind of device and operating system at some point in time: Windows, Mac, iOS, Android, Linux, Docker containers, IoT devices, and yes, Chromebooks, too.
The only responsible security stance to take on all endpoints is to install an agent that offers you visibility and protection. If you would like to know more about how SentinelOne can help protect your Chromebooks and other devices, read more here, contact us, or request a free demo.