The Good | Global Crackdowns on Cybercrime: Arrests, Malware Takedowns & Data Theft Charges
The actor behind the PowerSchool attacks, a Massachusetts college student named Matthew D. Lane, has agreed to plead guilty after compromising data of over 70 million students and teachers. Lane and co-conspirators accessed PowerSchool systems in December 2024 using stolen contractor credentials, demanding $2.85 million in Bitcoin to prevent a leak. More recently, they tried extorting individual school districts even after the initial payment. Lane now faces up to 17 years in prison for combined cyber and identity theft charges.
Infrastructure used by Lumma, a widely distributed malware-as-a-service (MaaS) infostealer, was seized this week in a global law enforcement operation with private sector support. Authorities seized 2,300 domains powering Lumma’s command-and-control (C2) network, hindering its ability to exfiltrate data. Active since 2022, Lumma enabled over 10 million infections, stealing browser data, credentials, and crypto keys that were then used to facilitate bank fraud and cryptotheft. Known for its rapid distribution through phishing, malvertising, and cracked software, Lumma’s adaptability, stealth, and widespread use made it one of the most dangerous infostealers in recent years.
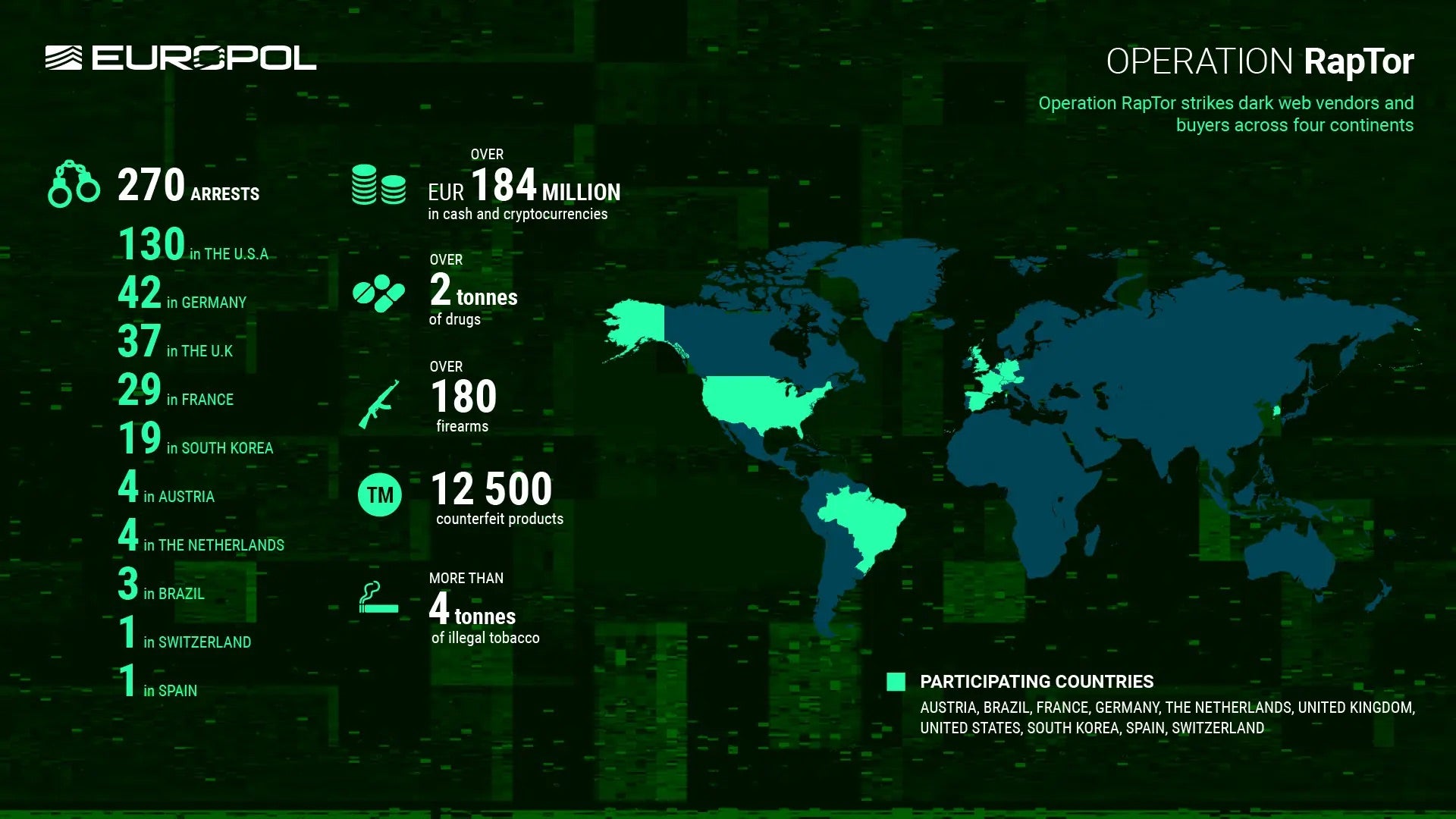
In another major blow to cybercriminals, Europol’s “Operation RapTor” led to 270 arrests across ten countries, targeting dark web vendors and customers. Authorities seized $207 million in cash and crypto, 2 tons of drugs, and over 180 firearms. Many suspects were linked to sales on dismantled dark web markets like Nemesis and Kingdom Market. Most of the arrests occurred in the U.S., Germany, and the U.K., and Europol emphasized that anonymity on the dark web is no shield, with ongoing efforts to identify more criminals through shared intelligence and past takedown data.
The Bad | Attackers Exploit Abandoned Cloud Subdomains to Spread Scams & Malware
A cyberattacker dubbed ‘Hazy Hawk’ is exploiting forgotten DNS CNAME records still pointing to decommissioned cloud services to hijack valuable cloud resources. This tactic has allowed the threat actor to take control of subdomains belonging to trusted entities, including government agencies, Fortune 500 companies, and top universities. The hijacked subdomains are then used to distribute scams, fake apps, and malicious advertisements.
A new report notes how Hazy Hawk identifies vulnerable CNAME records through passive DNS analysis before registering a cloud service with the same hostname, causing the original subdomain to resolve to the attacker’s cloud-hosted infrastructure. The hijacked subdomains are then used to generate hundreds of seemingly legitimate URLs, all of which benefit from the parent domain’s brand reputation and high rankings in search engines. High-profile hijacked domains include cdc.gov, honeywell.com, berkeley.edu, ted.com, and unicef.org.
Victims who click malicious links are redirected through a Traffic Distribution System (TDS), which profiles the user based on IP, browser, and device information. Based on this profiling, they are funnelled to tech support scams, fake antivirus alerts, phishing pages, and adult content portals. Many of these pages prompt users to allow browser push notifications, leading to persistent spam and scam alerts that continue even after they leave the site.
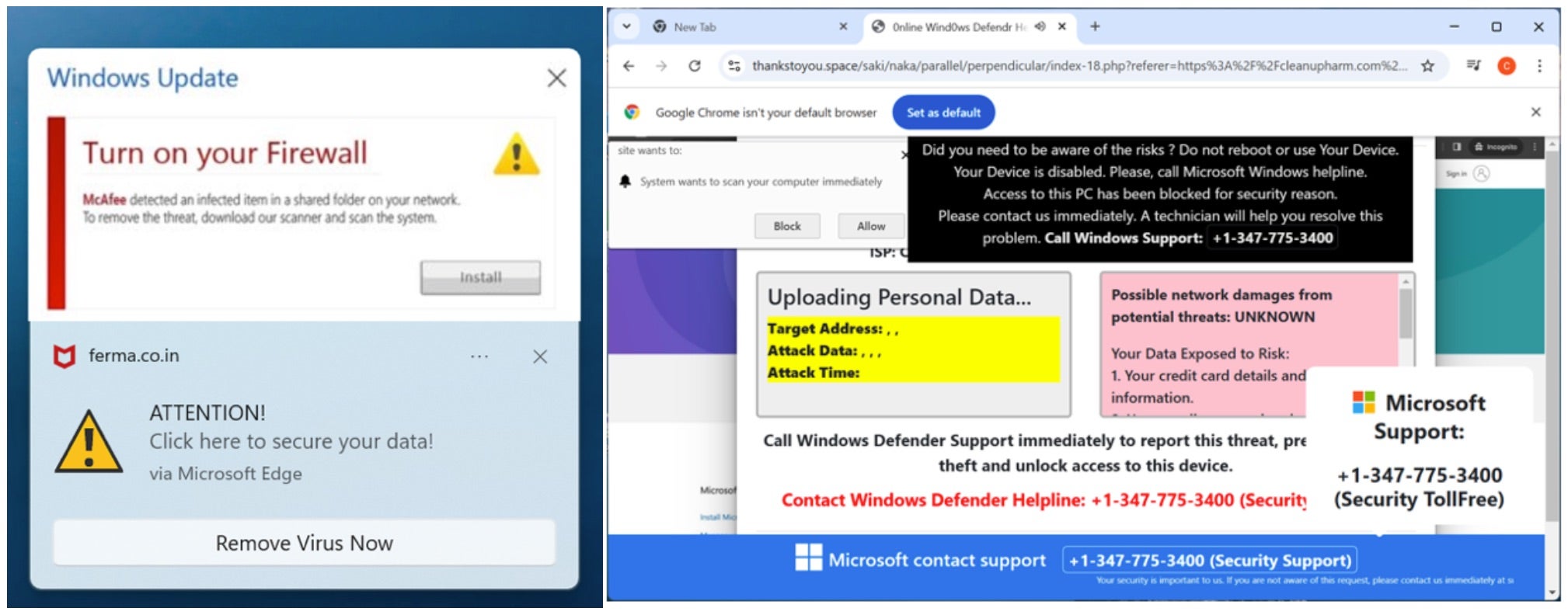
Security researchers suggest these hijacking tactics may be provided “as a service,” enabling a broader actor group to participate in the monetization schemes. In the U.S. alone, tech-vulnerable groups such as senior citizens lose billions of dollars annually due to the type of fraudulent content that actors like Hazy Hawk publish. Organizations can mitigate against fraudulent risks by deleting unused DNS records, while users should avoid granting notification permissions to unknown websites.
The Ugly | Russian APT28 Targets Ukraine Aid Efforts in Ongoing Cyberespionage Campaign
For the past three years, GRU-sponsored threat group APT28 (aka Sofacy, Forest Blizzard), has targeted international organizations supporting aid to Ukraine. A joint advisory from cybersecurity and intelligence agencies in several countries reveals that the ongoing campaign is focused on disrupting and monitoring both logistical and technical support heading into Ukraine.

APT28 has targeted organizations across defense, maritime, transportation, air traffic, and IT sectors in 13 countries, including the U.S., Ukraine, and several NATO members. APT28 hackers used a mixed range of TTPs to gain initial access, including brute-force password attacks, spearphishing (for credential harvesting and malware delivery), exploiting internet-facing VPNs via SQL injection, and leveraging vulnerabilities in Outlook, Roundcube webmail and WinRAR.
Post-compromise, they move laterally within networks, using tools like PsExec, Impacket, Certipy, and ADExplorer to gather Active Directory and email data. In many cases, they also manipulate mailbox permissions and enroll compromised accounts in MFA to maintain long-term access, allowing APT28 to identify additional targets such as figures responsible for coordinating transport and any other ancillary entities.
A particularly notable tactic involves hacking over 10,000 internet-connected cameras, mostly based in Ukraine but also in Romania, to track aid shipments, including cargo content and routes. The attackers have also been seen compromising SOHO devices near targets to route communications and remain undetected.
As part of the cyberespionage, malware like HeadLace and MASEPIE have been employed for persistence and data theft. APT28 also relies on both living-off-the-land (LOTL) binaries and custom malware for exfiltration, adjusting techniques to each victim’s environment.
The advisory stresses that organizations involved in aid logistics should consider themselves potential targets and outlines mitigations, IoCs, and detection strategies to combat this risk of espionage.