The Good | DoJ Indicts Hackers Working for i-Soon & APT27
Since 2011, U.S. federal and state government agencies, as well as foreign ministries of several governments across Asia, have been the targets of attacks attributed to PRC-backed APT27 and i-Soon (aka Anxun Information Technology), a hacking contractor based in China. This week, the U.S. Justice Department charged eight members of i-Soon and two actors linked to APT27 for their roles in these breaches.

Working as freelancers or i-Soon employees, these individuals conducted attacks on behalf of China’s Ministry of Public Security (MPS) and Ministry of State Security (MSS), who paid them for stolen data. Along with the charges, the DoJ has also seized i-Soon’s domain, which was used to promote its hacker-for-hire services. The State Department now offers a $10 million reward for information on the ten defendants, including i-Soon’s CEO, COO, Sales Director and several key members of its technical staff.
The unsealed indictments reveal that i-Soon hacked targets at the MSS’s request and sold stolen data to at least 43 MSS and MPS bureaus across 31 Chinese provinces, charging up to $75,000 for every compromised email inbox.
Alongside the i-Soon charges, APT27-linked threat actors Yin Kecheng (aka YKCAI) and Zhou Shuai (aka Coldface) were also indicted for exploiting vulnerabilities, deploying PlugX malware, and selling stolen data.
Both individuals remain at large but OFAC has placed sanctions on them, while the State Department offers $2 million for their arrests. These charges and sanctions are part of ongoing efforts to counter Chinese cyber threats and to stem a fast-growing hacking ecosystem funded by the PRC.
The Bad | EncryptHub Bulk Distributes Malware via Phishing, PPI Services & Trojanized Apps
EncryptHub (aka LARVA-208), rising in the cybercrime ecosystem as a financially-motivated threat group, is now being observed conducting advanced phishing campaigns to deploy infostealers and other malware while developing a new tool called “EncryptRAT”.
The group emerged in summer of last year and uses social engineering and phishing techniques such as SMS-based (smishing) and voice-based (vishing) attacks to trick victims into installing remote monitoring software. They often target high-value entities and create phishing sites that mimic an organization’s IT support to steal VPN credentials. Victims receive calls instructing them to enter details on these fake sites or, in SMS-based attacks, are sent fake Microsoft Teams links.
EncryptHub hosts phishing sites on bulletproof hosting providers like Yalishand before executing PowerShell scripts to deploy malware such as Fickle, StealC, and Rhadamanthys. The group is also known for exploiting the trust users have for legitimate software such as Q Talk, WeChat, DingTalk, Google Meet, and Microsoft Visual Studio. Once the victim installs a trojanized version of these apps, launching it triggers a multi-stage infostealer attack.
Most recently, security researchers tracking the group note that EncryptHub is leveraging third-party Pay-Per-Install (PPI) services like LabInstalls to distribute malware in bulk, paying between $10 (100 installs) and $450 (10,000 installs). The group even left positive feedback on the Russian cybercrime forum XSS, confirming their use of the service. EncryptHub is also currently developing EncryptRAT, a C2 panel for managing infections, issuing remote commands, and accessing stolen data.
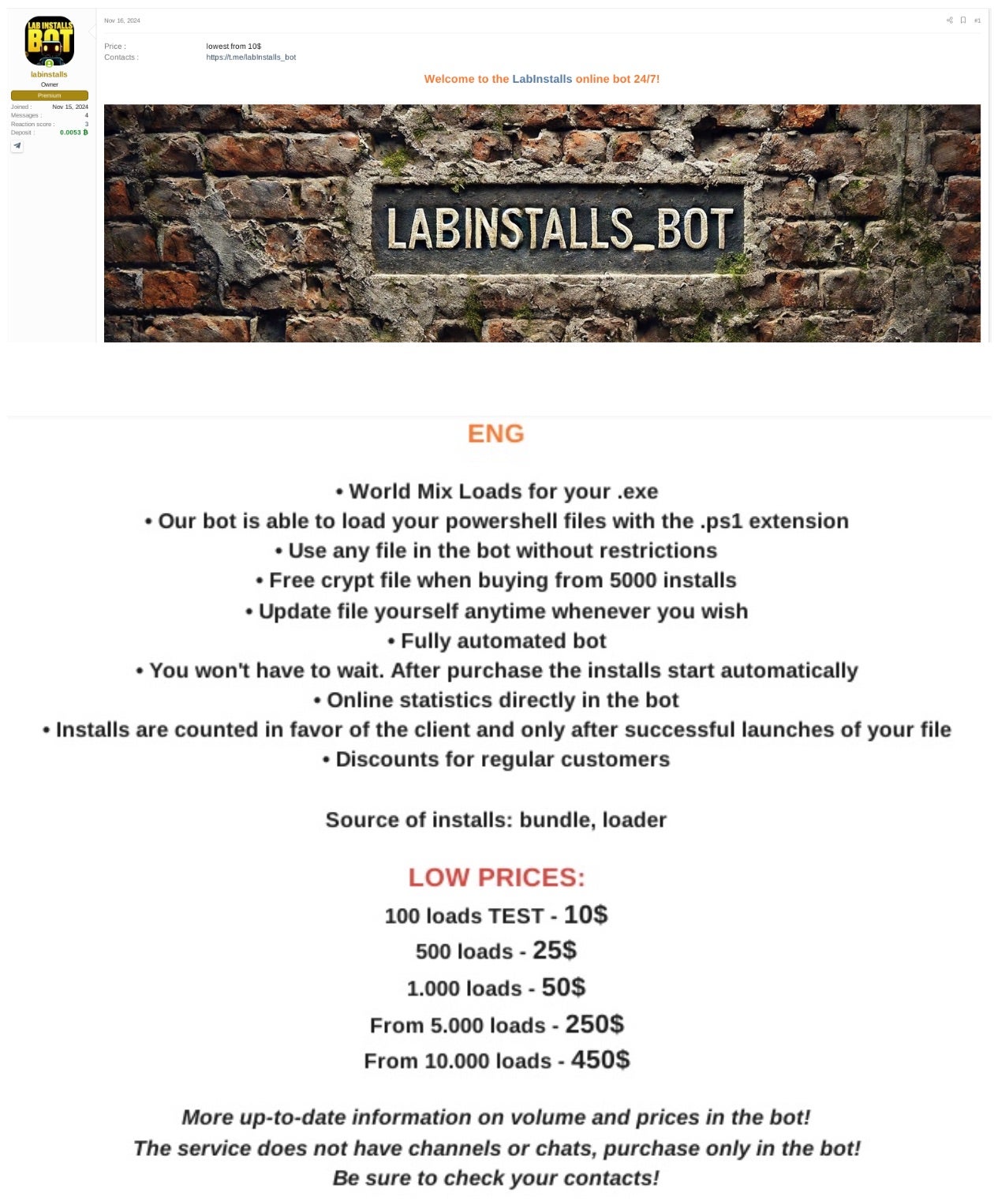
As EncryptHub continues refining its attack methods and developing EncryptRAT, organizations can adopt multi-layered security to counter evolving threats.
The Ugly | ClickFix Attacks Deploy Havoc C2 Framework Through MS SharePoint
ClickFix first emerged last year as a phishing technique, tricking users into executing malicious PowerShell commands through fake error messages. Cybercriminals would use phishing websites and attachments to prompt victims into clicking a ‘fix’ button. The action copies a malicious command to the clipboard, which users are then instructed to paste into a terminal, unknowingly launching malware. ClickFix tactics have since evolved with the newest version of the campaign tricking users into installing the Havok post-exploitation framework for remote access.
The newly discovered campaign involves phishing emails that tell recipients they have a ‘restricted notice’ to review, directing them to open an attached HTML file. The file displays a fake OneDrive error (“Error 0x8004de86”), urging users to update the DNS cache. Clicking “How to fix” copies a PowerShell command that executes a remote script from the attacker’s SharePoint server.
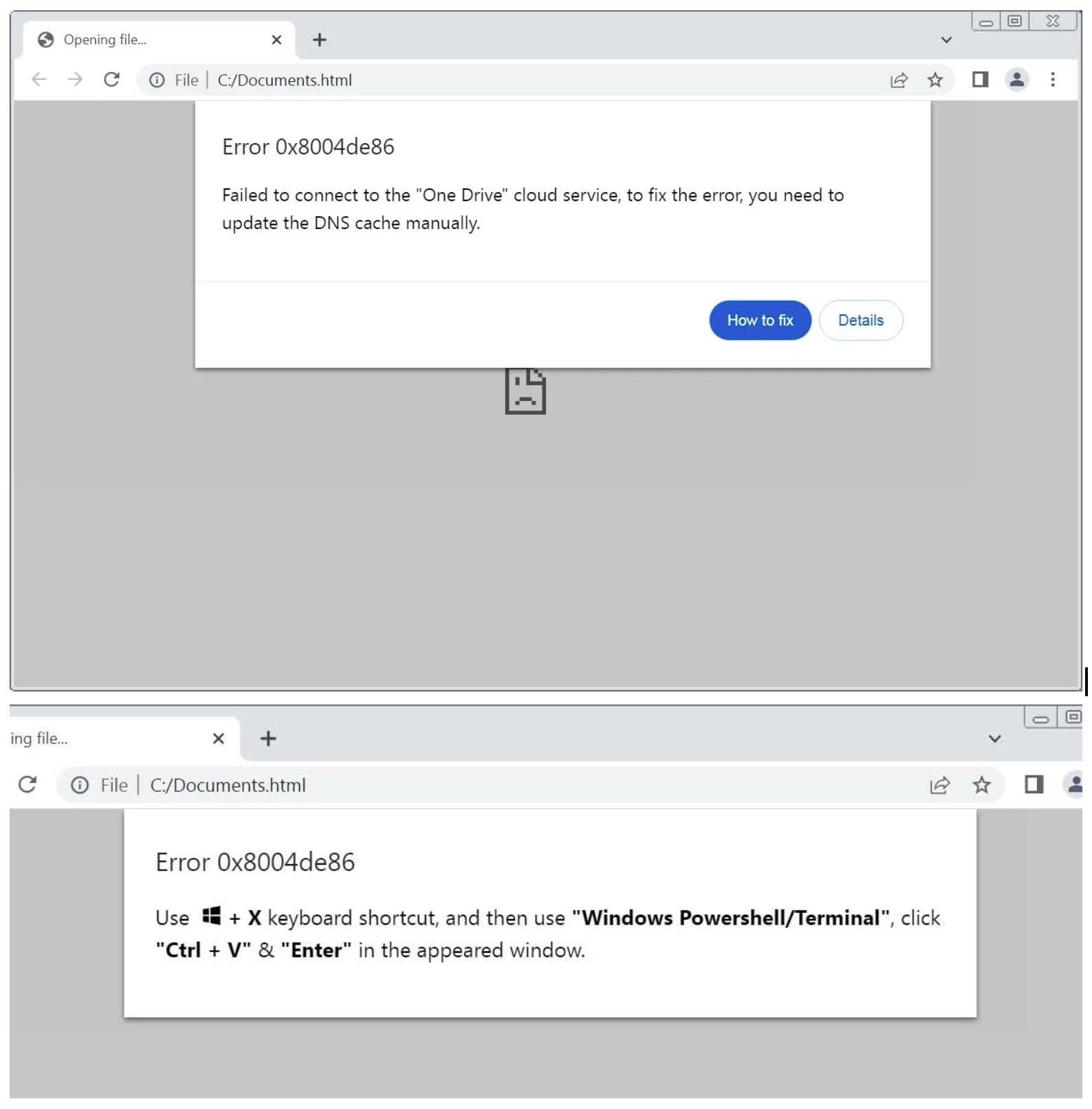
The script checks if it is running in a sandbox by querying the Windows domain. If detected, it terminates. Otherwise, it modifies the Windows Registry, verifies Python installation, and, if missing, installs it. It then downloads and runs a Python file to inject Havok, an open-source command-and-control (C2) framework similar to Cobalt Strike. Havok communicates with the attacker’s infrastructure via Microsoft’s Graph API, embedding malicious traffic within legitimate cloud services in an attempt to evade detection. Finally, the malware uses SharePoint APIs to send and receive commands, turning the attacker’s SharePoint account into a covert data exchange system.
As ClickFix attacks become more widespread, organizations can protect their data by educating employees on phishing tactics, restricting PowerShell execution, implementing email security filters, and monitoring for suspicious clipboard activity and unauthorized script execution with a trusted endpoint security solution.


