The Good | Charity Scammer Indicted For Defrauding $7.5 Million Through BEC Attacks
The philanthropic world saw justice this past week with the arrest of Olusegun Samson Adejorin, a Nigerian national currently facing charges for $7.5 million for business email-based scams. The attacks targeted two U.S.-based charitable organizations and has led to an eight-count federal grand jury indictment, encompassing wire fraud, aggravated identity theft, and unauthorized access to a protected computer.
Adejorin’s fraudulent activities reportedly unfolded between June and August 2020 through an elaborate scheme involving unauthorized access to email accounts and the impersonation of employees to perpetrate the embezzlement. To facilitate withdrawals exceeding $10,000, Adejorin leveraged stolen credentials to send emails masquerading as legitimate employees who had the authority to approve such transactions. The DoJ revealed that he also acquired a credential harvesting tool, registered deceptive domain names, and concealed fraudulent emails within a legitimate employee’s mailbox to carry out the fraud.
— US Attorney Maryland (@USAO_MD) January 3, 2024
The charges brought against Adejorin carry severe penalties, including a maximum of 20 years for wire fraud, five years for unauthorized access to a protected computer, and a mandatory two-year sentence for aggravated identity theft.
Business email compromise (BEC), also referred to as CEO fraud, has been a significant source of financial losses, with the FBI reporting billions of dollars in damages. To bolster defenses against such attacks, organizations are advised to implement measures such as multi-factor authentication (MFA), email filtering to detect and block phishing attempts, and robust verification procedures for wire transfer requests. Responding to suspicious requests, such as changes in bank account details, with a confirmation call to a predetermined number can serve as a crucial defense mechanism, potentially saving enterprises millions.
The Bad | Zeppelin Ransomware Source Code Found Listed On Cybercrime Forum For $500
Like the post-holiday sales that have trickled into the new year, dark markets and underground channels also continue to offer sales and promotions on malware kits, tools, and illicit services. Most recently, a threat actor known as ‘RET’ advertised the sale of Zeppelin ransomware builder’s source code and a cracked version for a mere $500 in a cybercrime forum.
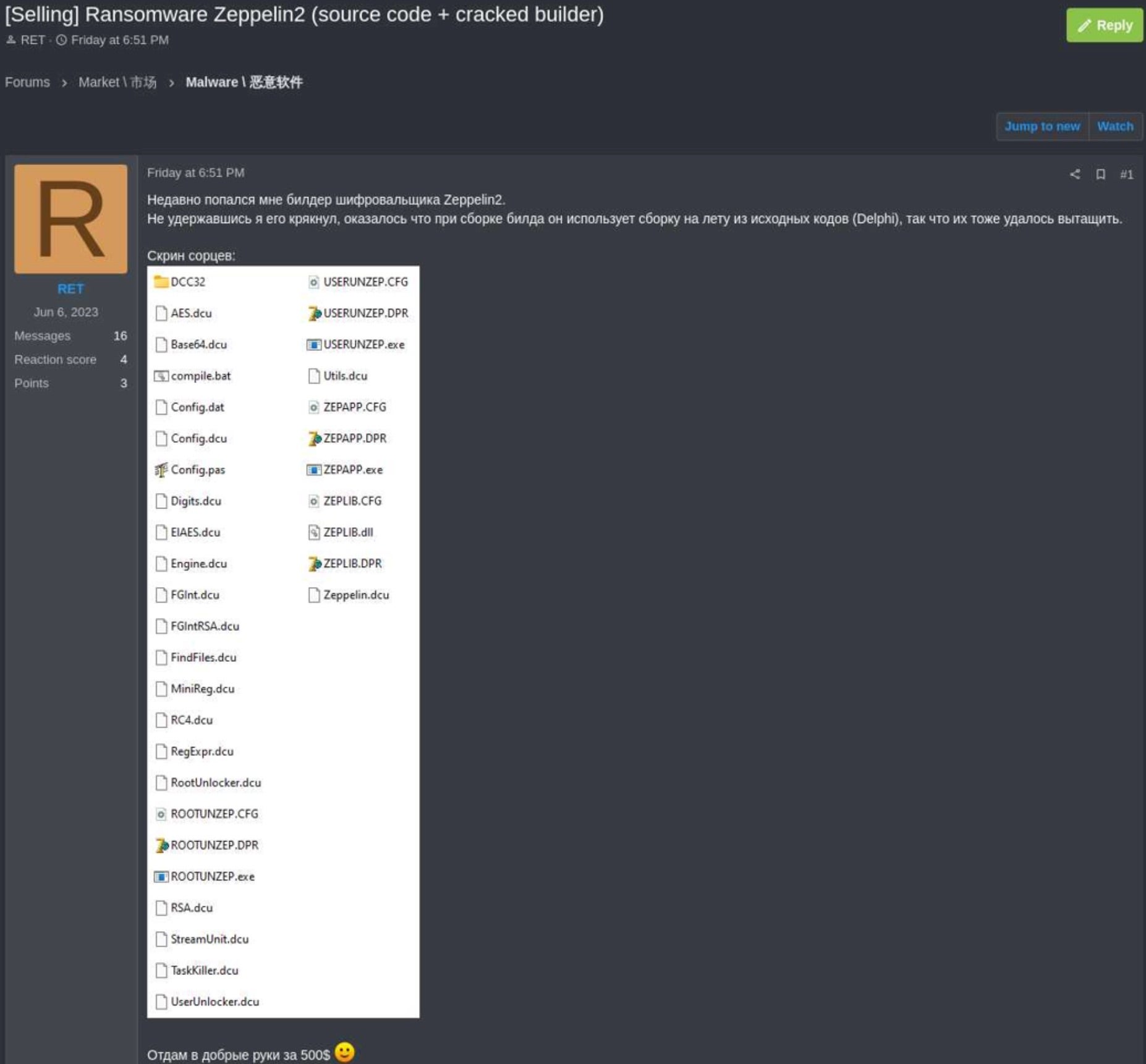
Originating from the Vega malware family, Zeppelin was active from 2019 to 2022, focusing on double extortion attacks to demand substantial ransoms from their victims. Zeppelin operators targeted a wide range of businesses and critical sectors including defense contractors, educational institutions, manufacturers, tech companies, and those in the healthcare field. According to the FBI and CISA, Zeppelin operators would execute their malware multiple times within a single compromised network, meaning victims would need several unique decryption keys to resume operations.
When law enforcement and security researchers identified exploitable flaws in Zeppelin’s encryption scheme back in November 2022, a decrypter was developed to assist affected victims, eventually leading to the discontinuation of the RaaS infrastructure. RET has reportedly asserted that the posted builder source code and cracked version up for sale is no longer susceptible to the same cryptographic weakness.
Although the authenticity remains unverified, threat intelligence researchers have acquired screenshots suggesting the legitimacy of the offer. Prospective buyers could utilize the package to establish a new ransomware-as-a-service (RaaS) operation or create a customized locker based on the Zeppelin family. RET, clarifying they did not create the malware but only managed to “crack the builder”, insisted on selling to a single buyer, temporarily halting the sale pending completion of the transaction.
The Ugly | Concern Over NPM Dependency System Sparked by Troublesome Holiday Prank
An online prank over the holidays by an NPM author has caused a wave of issues this week, disrupting build pipelines and exhausting storage space for any who installed a package called ‘everything’. Its namesake is an apt one: the ‘everything’ package systematically fetches every NPM package ever published to npmjs.com when downloaded.
Significant consequences have followed the prank campaign. Not only was the registry inundated with over 3000 packages, these packages also listed every NPM package on npmjs.com as their dependency. What this means for published authors is that they are prevented from removing/unpublishing their packages due to their inadvertent association with the ‘everything’ package. Compounding this is NPM’s policy that makes it difficult for authors to unpublish their packages if there are dependencies.
The NPM package registry is a cornerstone for the global software development community, providing an extensive collection of JavaScript packages and tools. With millions of packages available, developers worldwide use NPM for collaboration, accelerating development cycles, and ensuring code reliability.
GitHub has since addressed issues arising from the ‘everything’ package, allowing packages to be removed if they meet the company’s unpublish criteria. As of this writing, the company has also confirmed that the ‘everything’ repository has been removed from GitHub and that the package itself is now appendaged with a warning message on the NPM registry where it remains.
The incident has sparked various reactions from developers facing challenges in unpublishing deprecated or experimental packages. While some deemed the stunt an exploitation of the open-source NPM system, others have highlighted its potential for malicious use such as denial of service (DoS) attacks.


