As we get ready to wave goodbye to 2023, this week’s The Good, Bad and the Ugly takes the opportunity to rewind and revisit the best, the worst, and the ugliest cybersecurity news from the past 12 months.
The Best
Of all The Good things we reported on in cybersecurity this year, there can be no doubt that the most needful was a joined-up, coordinated approach to cyber led from the top, and the Biden-Harris administration’s National Cybersecurity Strategy went a long way toward that end. The strategy is a comprehensive approach to defend critical infrastructure, disrupt threat actors, promote data privacy and security, invest in cyber resilience, and establish international partnerships to combat cyber threats.
It’s a response to the increase in cyber attacks on various sectors in the U.S. and has already led to some useful initiatives, including the Counter Ransomware Initiative. We hope and expect to see more in 2024.
We reported on plenty of criminals being brought to justice during 2023, including the arrest of core members of the prolific ransomware gang, DoppelPaymer, in a joint operation conducted by Europol, the FBI, and the Dutch police in Germany and Ukraine.
Joseph James O’Connor was another significant capture of the year. Known as PlugWalkJoe, O’Connor was sentenced to five years in prison for various cybercrimes, including his role in the 2020 Twitter Hack, in which he and his associates used SIM swaps along with social engineering tactics to gain access to Twitter’s back-end tools and transfer control of high-profile accounts to various unauthorized users.

While some accounts were hijacked by the actors themselves, O’Connor sold the access rights of several well-known accounts to third parties. O’Connor was also charged with stealing cryptocurrency, money laundering, cyberstalking, and unauthorized access to TikTok and Snapchat.
Of course, AI has been one of the big themes of 2023. Again, the government, in collaboration with tech companies like OpenAI and Anthropic, has taken a leading role. The “AI Cyber Challenge” (AIxCC), led by the Defense Advanced Research Projects Agency (DARPA), offers up to $20 million in prizes for entries that use artificial intelligence to protect critical U.S. infrastructure from cybersecurity threats.
Leveraging AI to enhance cybersecurity is, of course, the core DNA of SentinelOne. In 2023, we announced Purple AI, a game-changing generative AI dedicated to threat-hunting, analysis and response that empowers security teams to identify and respond to attacks faster and easier using natural language conversational prompts and responses.
The Worst
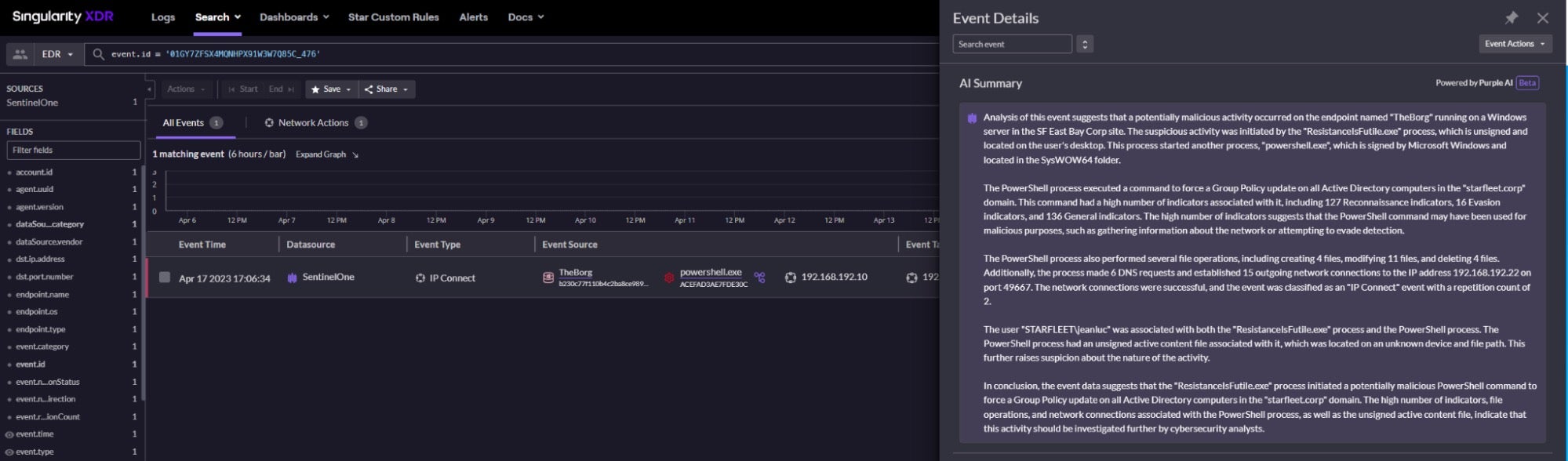
Picking out the worst of The Bad things that happened in cybersecurity in 2023 is a challenging task, given just how many attacks, compromises, breaches and ITW vulnerabilities we reported on this year, but among the more standout stories of concern was Winter Vivern APT’s exploitation of a zero-day vulnerability (CVE-2023-5631) in Roundcube’s webmail software, used to steal email data from European governments and think tanks.
Casinos MGM and Caesars were among some of the big name victims of the year’s record number of ransomware attacks.
All ALPHV ransomware group did to compromise MGM Resorts was hop on LinkedIn, find an employee, then call the Help Desk.
A company valued at $33,900,000,000 was defeated by a 10-minute conversation.
— vx-underground (@vxunderground) September 13, 2023
2023 saw a 95% year-on-year increase in extortion attacks as threat actors continue to leverage social engineering, weak or misconfigured cloud assets, and old vulnerabilities to lock files and steal data.
A feature of 2023 ransomware has been a new focus on compromising ESXi hypervisors through a slew of variants built out of the leaked Babuk (Babyk) code. A wave of ESXiArgs ESXi targeted attacks was reported early in the year, encrypting extensive amounts of data across servers in the US, Canada, and Central Europe.
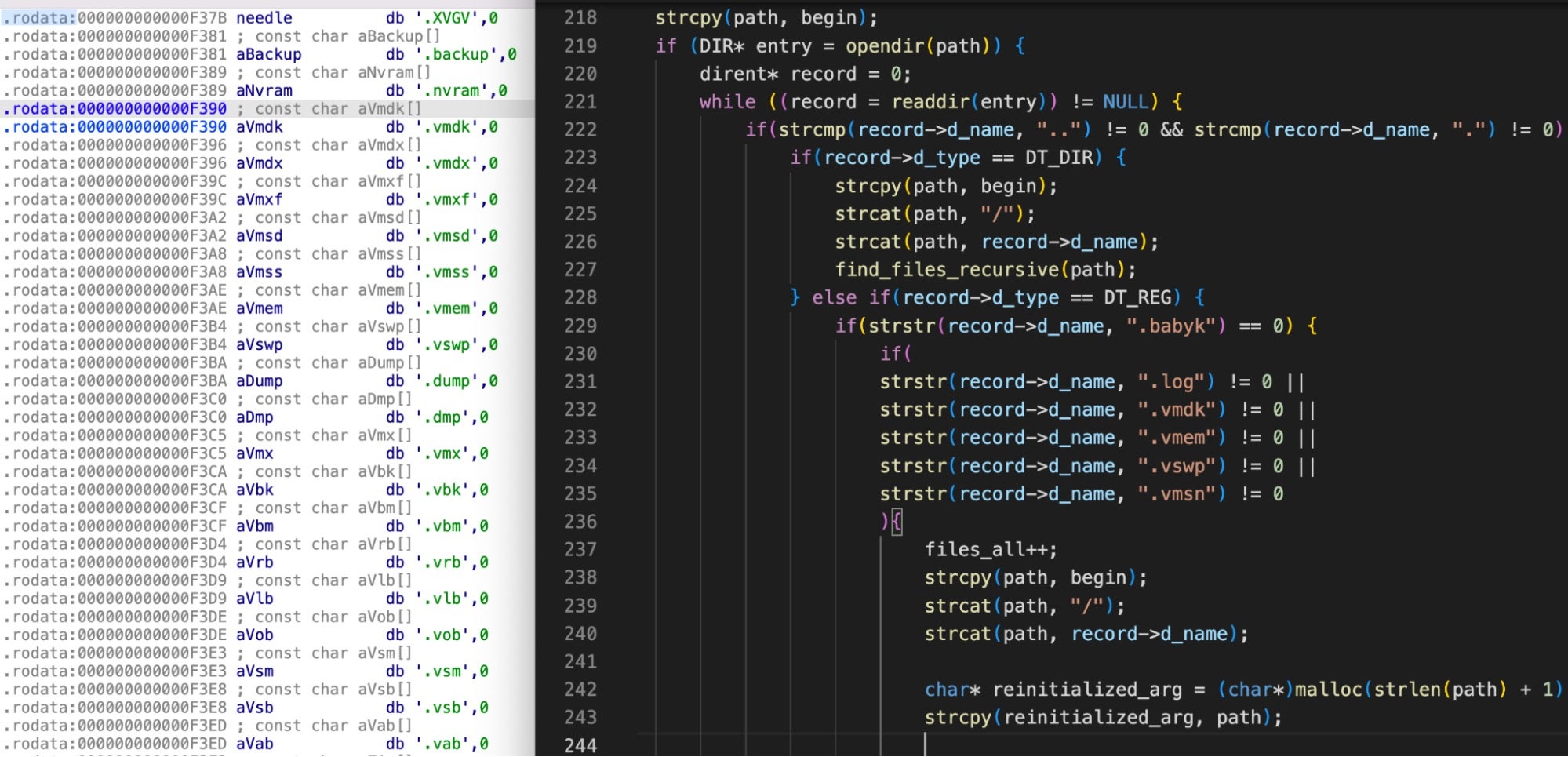
A report by SentinelLabs in May detailed how numerous threat actors were hopping on the easy availability of source code for Linux ransomware to target vulnerable EXSi servers.
The Ugliest
What have 3CX, JumpCloud and macOS users involved with cryptocurrency got in common? You guessed it: North Korea. From supply chain attacks to espionage and financially-motivated cybercrime, DPRK-aligned threat actors have been keeping us busy and many victims awake at night throughout 2023.
The SmoothOperator campaign disclosed in early 2023 was a supply chain attack targeting both macOS and Windows users, exfiltrating victim data over https using a custom data encoding algorithm. The macOS version of the trojanized 3CX application was delivered via a maliciously crafted version of libffmpeg.dylib contained within the application bundle’s Electron Framework folder.
../3CX Desktop App.app/Contents/Frameworks/Electron Framework.framework/Versions/A/Libraries/libffmpeg.dylib
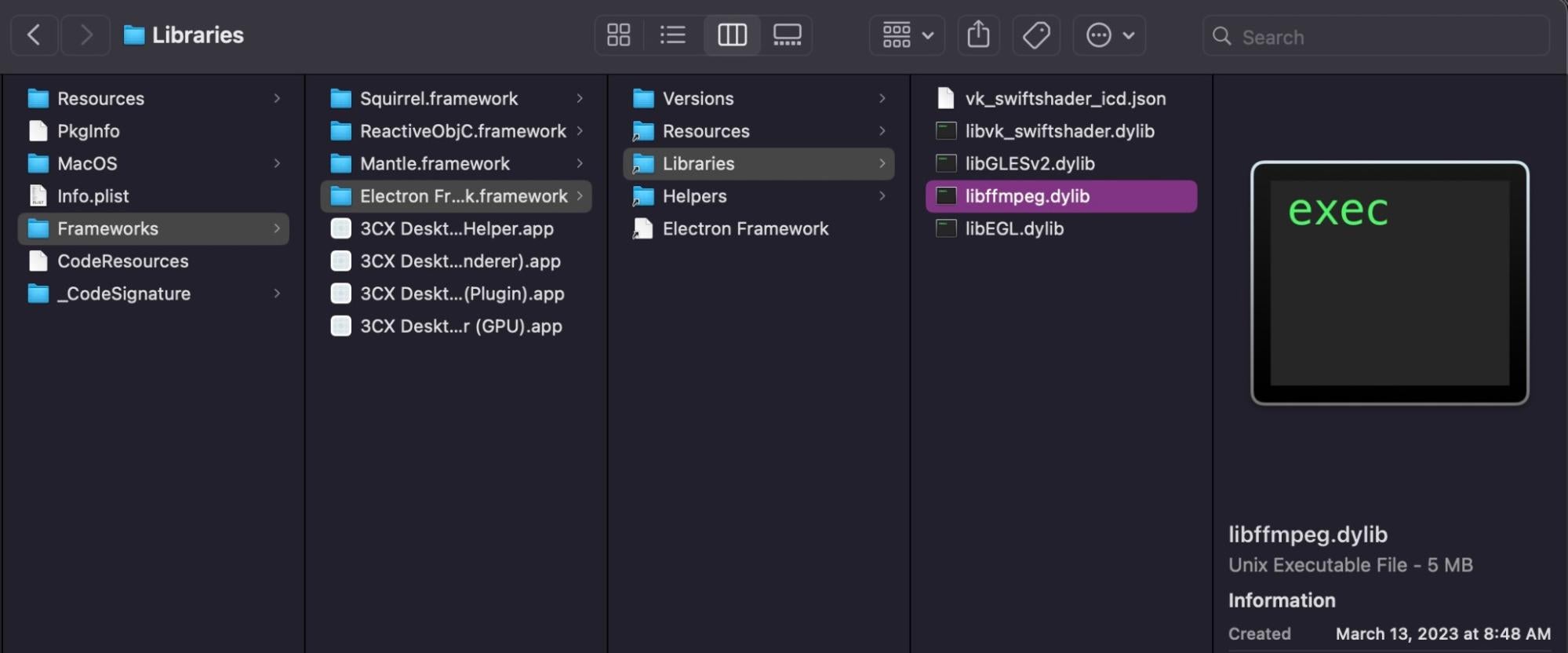
Although the full extent of the attack remains unclear, reports at the time suggested that over 240,000 IP addresses were using the trojanized 3CX Phone System Management Console.
Breaches of government networks are always among the ugliest of the Ugly, and several concerning attacks were recorded throughout 2023. In December, a high-severity vulnerability, tracked as CVE-2023-26360, found in Adobe’s ColdFusion was used to gain initial access into U.S. government servers.
CISA highlighted two incidents in which CVE-2023-26360 was used to compromise federal agency systems. Both instances involved outdated server software vulnerable to various CVEs, with threat actors leveraging the vulnerability to deploy malware through HTTP POST commands to the ColdFusion-associated directory path. It seems the government still has plenty of work to do to implement its own cybersecurity best practices.
Finally, it’s been a tough year across OSes in terms of in-the-wild exploitation of vulnerabilities, but it appears to have been a record year for Apple’s increasingly troubled iOS platform, with 19 zero days reported as being abused by threat actors in 2023. The phrase “Apple is aware of a report that this issue may have been exploited…” may have never been more oft-seen by Apple users than this year.
Google HQ, aka “GooglePlex”, sits 7 miles from Apple Campus and staff there also appear to have had their hands full patching security bugs throughout 2023. Among the more severe bugs patched this year were:
- CVE-2023-2033 (CVSS score: 8.8) – Type Confusion in V8
- CVE-2023-2136 (CVSS score: 9.6) – Integer overflow in the Skia graphics library
- CVE-2023-3079 (CVSS score: 8.8) – Type Confusion in V8
- CVE-2023-4863 (CVSS score: 8.8) – Heap buffer overflow in WebP
- CVE-2023-5217 (CVSS score: 8.8) – Heap buffer overflow in vp8 encoding in libvpx
However, the WebP vulnerability likely had the largest impact on users, as the flawed library is used across Apple, Google, Microsoft, Mozilla and other non-browser products. The bug in the widely used image encoding and compression library was first reported by Citizen Lab to Apple as part of an in-the-wild attack.
Microsoft, meanwhile, has continued to patch up its regularly exploited backlog of vulnerabilities, while at times ignoring newly-discovered security issues. In June, the company said that a bypass found by researchers that can allow malware to be delivered to any Teams account from external accounts did not ‘meet the bar for immediate servicing’. The response came as a surprise as researchers showed that all MS Teams accounts running in the default configuration were susceptible to their PoC attack.
In an attempt to cut through the scarcity of candor these days, let’s state some things plainly. Let’s talk about Microsoft. With the upfront caveat that every security vendor has made mistakes and has skeletons in their respective closets that need addressing. None without sin.
— J. A. Guerrero-Saade (@juanandres_gs) July 23, 2023
The way Microsoft corporate has been acting for the past few years (SolarWinds, Hafnium, general JCDC collaboration, and now Storm-0588) is enraging, duplicitous, disappointing, counterproductive, and most importantly unnecessary.
— J. A. Guerrero-Saade (@juanandres_gs) July 23, 2023
Conclusion
So much for the highlights and low spots of 2023: You can find more on all these stories as well as all the others we reported on this year right here.
Our regular weekly roundups will return next Friday; in the meantime, let us wish you a happy and secure New Year 2024 from all of us here at SentinelOne!


