KeyPass is a new ransomware threat that has hit at least 20 countries since August 7th and appears to be spreading still further by means of fake software installers.
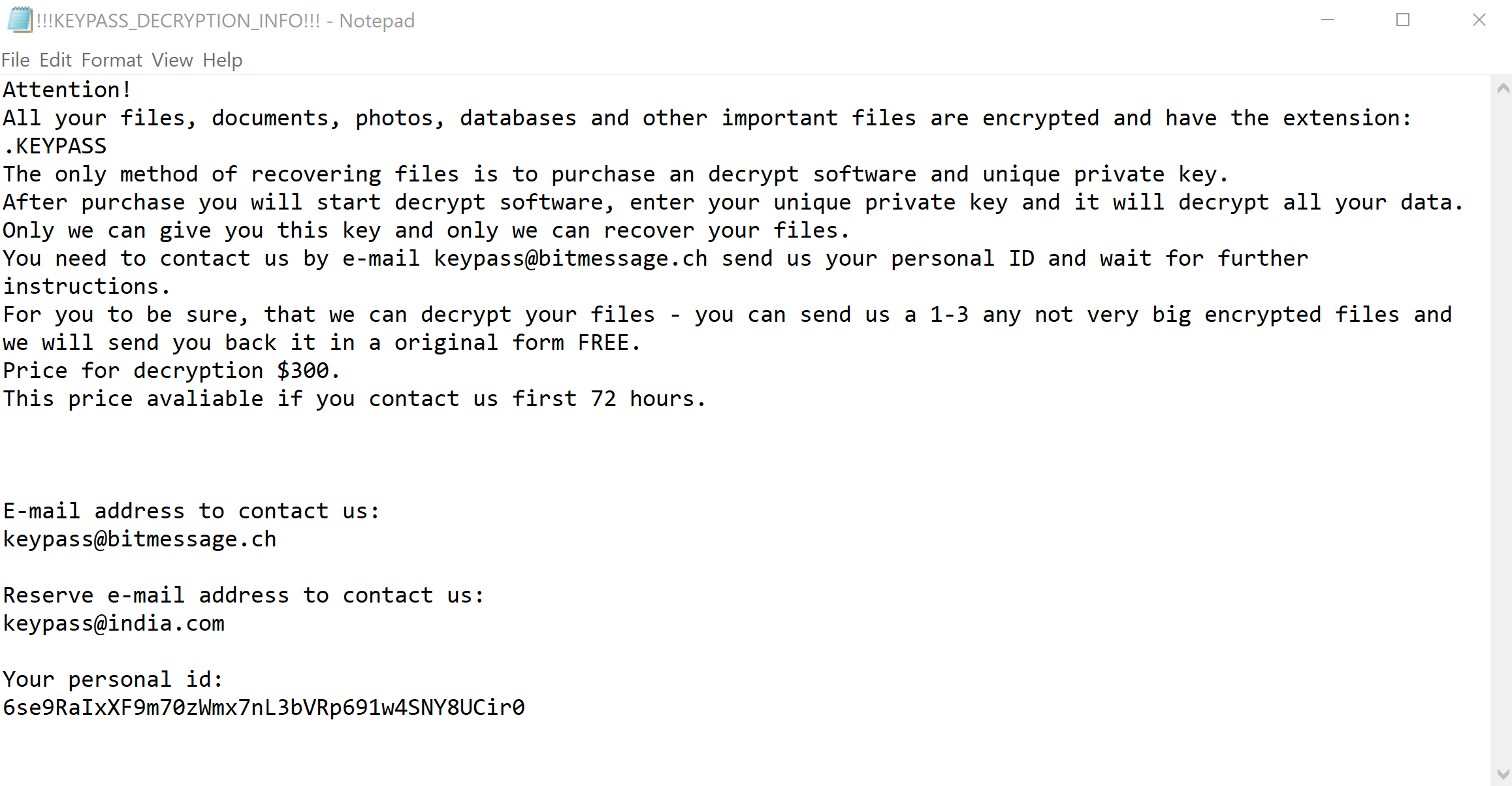
The victim’s data is encrypted with a “.KEYPASS” extension and ransom notes are deposited in each directory that is successfully encrypted. The ransom note demands $300 and attempts to reassure the victim by offering to send proof of decryption ability in advance of payment. The victim is encouraged to send the attacker a sample of a small encrypted file. After doing so, according to the note, the victim will receive an unencrypted version of the file for free. Clearly, the attackers are adopting the same level of concern for ‘user experience’ as legitimate software developers in order to maximise their profits.
Demo and Findings
As can be seen in the accompanying video, SentinelOne customers are automatically protected from KeyPass.
The agent detects the malicious activity immediately, and the malware is then deleted. While deletion is expected behaviour when the SentinelOne policy is set to ‘Protect’, in the demonstration we use the ‘Detect-only’ policy in order to observe the ransomware’s behaviour. So what causes the malware to be deleted?
As it turns out, the ransomware is in fact deleting itself. Let’s take a closer look at exactly what’s going on under-the-hood by examining the attack storyline in SentinelOne’s Management Console.
Upon execution, the KeyPass ransomware.exe creates the file
/c "C:UsersadminAppDataLocalTempdelself.bat"
Then, this file deletes both files at:
DeviceHarddiskVolume2UsersadminDesktopKeyPass ransomware.exe
DeviceHarddiskVolume2UsersadminAppDataLocalTempdelself.bat
Several seconds later, the ransom note appears:
A few minutes later, it begins encrypting the victim’s files, including shortcuts and the Desktop background, resulting in this state:
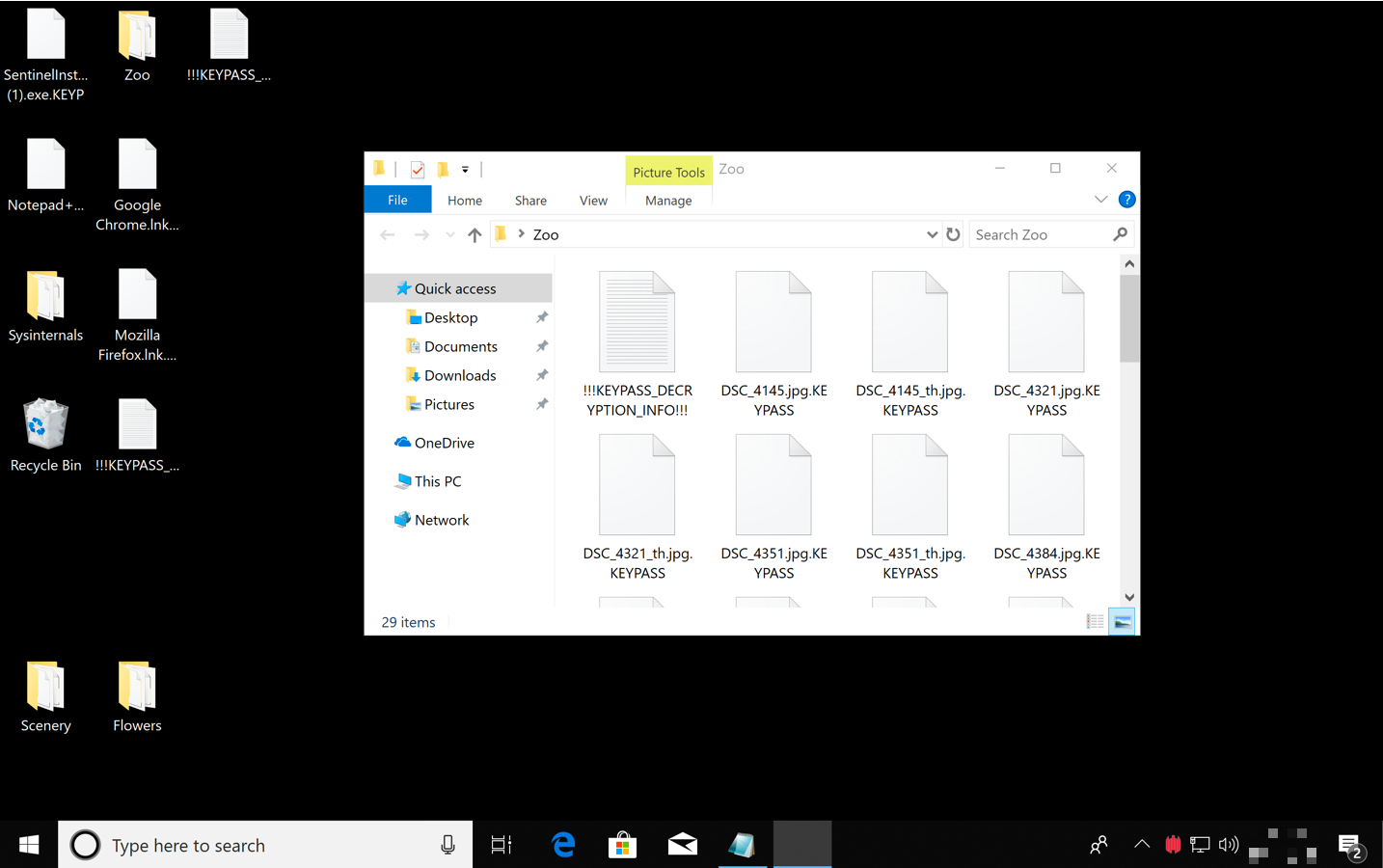
For the purpose of this demo, we used the Detect-only policy and allowed the ransomware to complete its encryption of the entire device. In such cases, SentinelOne’s rollback feature can easily roll back the device to its original estate with one-click. In a real-life scenario, the ransomware would be blocked before it had the chance to cause any damage.
Deep Visibility
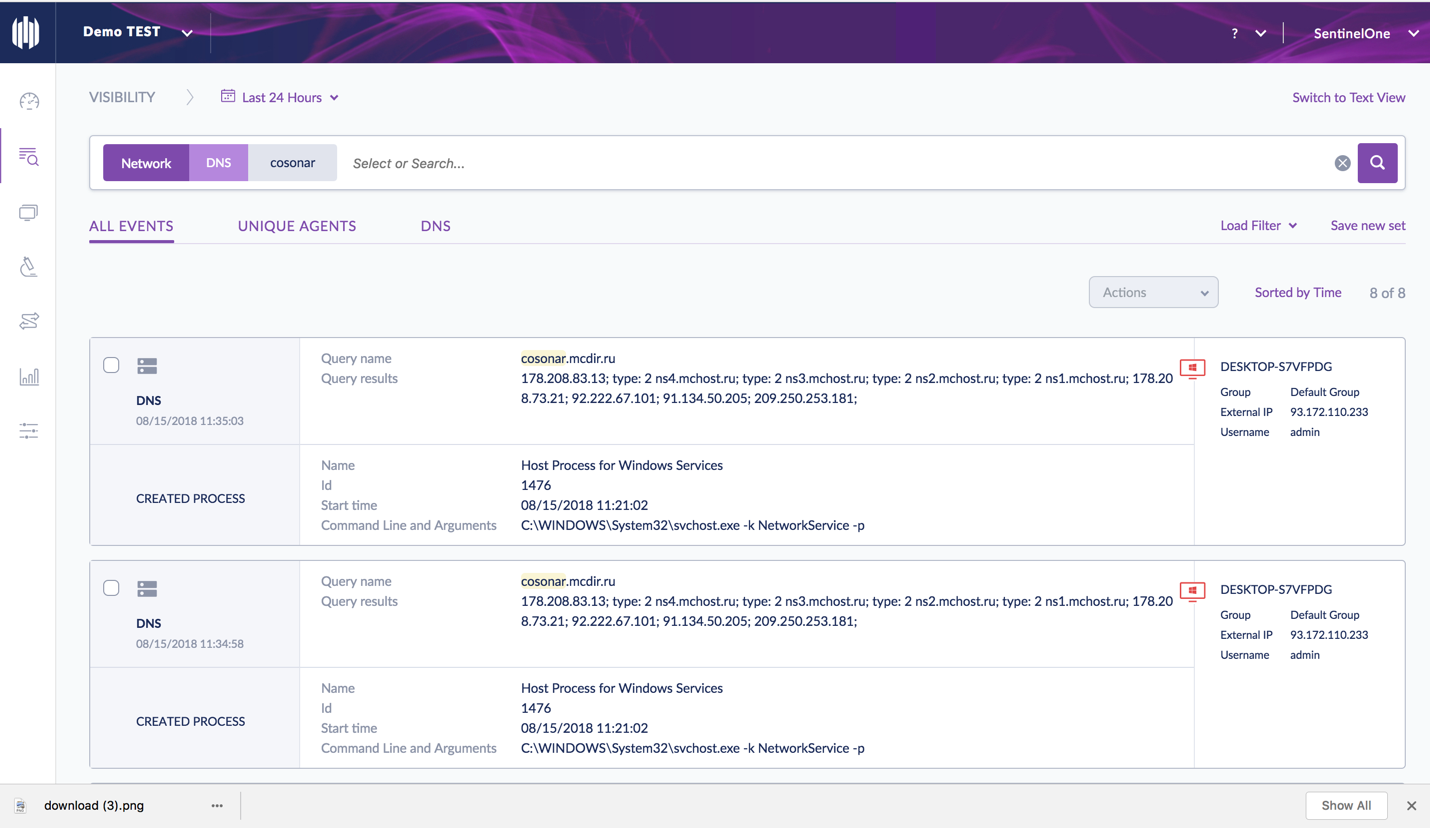
Deep Visibility provided through the SentinelOne Management Console reveals additional events behind the attack storyline. The Console shows that the malware first tries to communicate with four servers, physically located in Russia, and then deletes itself and its associated scripts.
You can see the communication and the exact DNS queries in the Console:
178.208.83.13; type: 2 ns4.mchost.ru; type: 2 ns3.mchost.ru; type: 2 ns2.mchost.ru; type: 2 ns1.mchost.ru; 178.208.73.21; 92.222.67.101; 91.134.50.205; 209.250.253.181;
Avoiding Downtime
Typically, victims of ransomware attacks are faced with a stark choice. In a recent ZDNet interview, SentinelOne customer, Lester Godsey, CISO for the city of Mesa, Arizona, points out that victims must either pay up and risk further attacks, or rely on their ability to restore from backups. With business critical services affected, avoiding downtime is a primary concern. As mentioned above, the SentinelOne agent offers prevention and if needed, a one-click restore option on all endpoints that avoids downtime. As can be seen above, the SentinelOne agent is able to roll back the infected machine instantaneously without interrupting the user. Want to see how SentinelOne can help improve your security efforts? Get a Demo Now