Responding to a cyber threat takes time as defenders want to do more than merely stop malicious threats; they also need to ensure any compromised identities or accounts are restored, that any lingering phishing emails sitting in inboxes ready to re-detonate and restart the attack are cleaned up, that if vulnerable software was involved it’s patched or removed from endpoints, and the list goes on.
For years now, the only way to do this efficiently was via a SOAR, and that required high costs and usually additional headcount to build and maintain the playbooks. All this led to a very ‘human-centric’ manual response process, which added up to a longer containment and response time.
XDR was made to solve problems like these. Singularity XDR unifies and extends detection, investigation and response capability across the entire enterprise, providing security teams with centralized end-to-end enterprise visibility, powerful analytics, and automatable response across the technology stack – making every security workflow faster, more effective and more accurate.
Recently, we introduced XDR apps for response that take this approach to the next level with one-click remediations. Let’s find out more.

XDR Response Actions for One-Click Remediation
Our recent launch of additional XDR apps for response is an XDR milestone that will continue to strengthen Singularity XDR. With XDR Response actions, a user can drop an API Key into our Marketplace, choose the automatic actions and conditions they desire, and SentinelOne will do the rest.
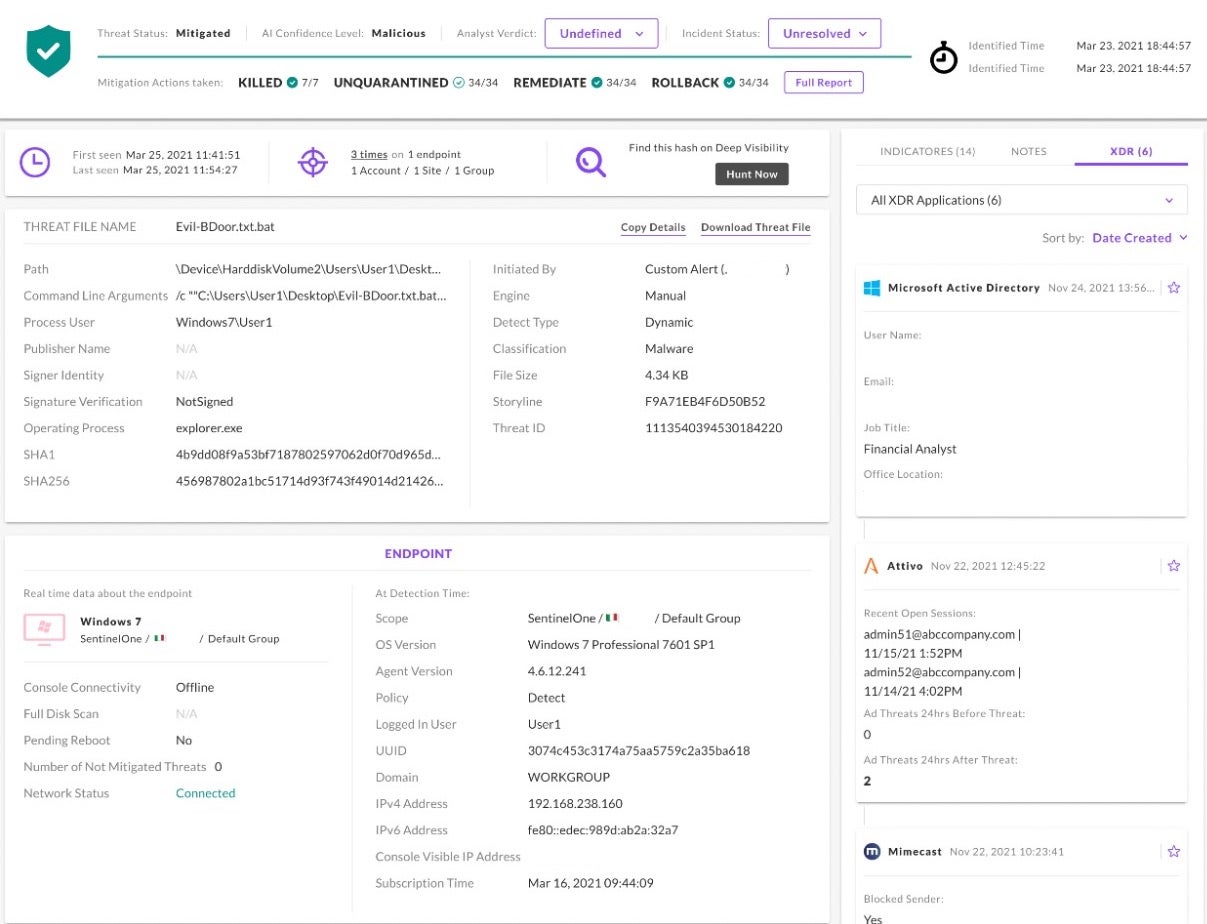
Take the act of resetting a user’s password and expiring their sessions. Most SOC analysts don’t have access to the proper Identity Provider portals (IdPs) to do this as the identity team doesn’t want to add the entire SOC to the portal. At best, it would have required the identity team creating very specific RBAC roles in AD, Okta, etc to have security roles. Without access, the analyst must open a ticket and wait. With XDR, there’s a button for that. Where is it? Right in the threat.
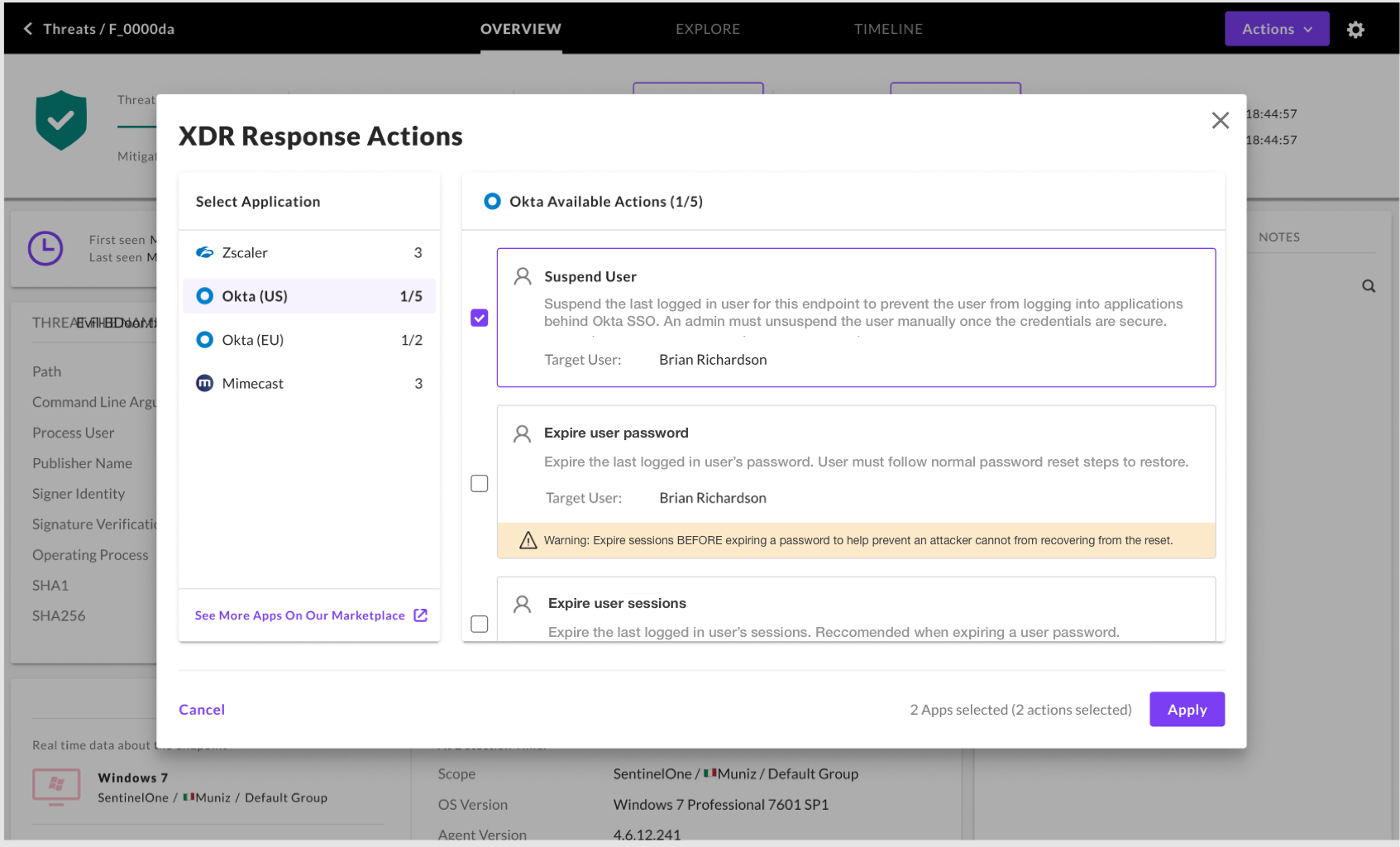
XDR Response actions are the single click that can stop expansion. If an analyst finds a threat where an internal user’s credentials have been used to log into email and send phishing links, XDR can suspend the user’s email access or just block the hash from being passed around. Until the credentials can be trusted again, that analyst can also move the user to a more restrictive SASE policy to ensure data like financial results and intellectual property stored in cloud apps are protected.
How Does It Work?
The identity team provides the SentinelOne admin an API key which is then input into the Marketplace. The key can be broadly permissive or purpose fit to ensure least privilege just for the SentinelOne XDR use cases.
Next, the user selects which integrations to turn on and which to leave disabled. They then select if the action should happen on all threats or just those SentinelOne has higher confidence on as being malicious. The user is now done with configuration.
The app they selected is pre-programmed with all the logic needed. The next time a matching threat pops up, SentinelOne will automatically take the chosen action.
For admins that want to allow analysts to evaluate threats before taking actions, manual actions can be enabled in the same Marketplace flow. Manual actions allow admins to browse a list of all enabled XDR actions to remediate a threat across the stack, whether it be banning a hash, a user, or an IP address.
This keeps the analyst in the loop before actions are taken while still helping accelerate remediation to minutes instead of hours or even days when there are dependencies on another team.
XDR Offers Greater Flexibility Than a SOAR
While a SOAR can be a tremendous tool for those who have the budget and staff, XDR is the turnkey tool that allows more teams to adopt orchestration. SOAR playbooks can run highly customized flows but maintaining them as processes and tools change has proved a barrier or unsustainable for many.
Enabling a list of automatic actions or manually selecting them from a threat triage model is the flexible approach that enables every team of every size to be more efficient and effective.
What Triggered This Innovation, Why Now?
This technological leap is arriving now because of the need to streamline security workflows, consolidate various tools in the SOC while rapidly responding to remediate threats across the enterprise. While partnerships and Marketplaces have been done before, they’ve never been done with this level of deeper, frictionless integration.
XDR requires vendors to work together to build integrations that go deeper and broader. We’ve found the market is ready to partner and that’s why we’ve taken a “native and open” approach to XDR, offering many solutions on our platform while partnering with best-in-class vendors from across the stack.
XDR is the result of a better understanding of how teams work and what fits budgets. Security is trending in the direction of tools that give teams flexibility without requiring them to build and maintain complex logic or code.
The market has been waiting for simple security that saves teams time and money without a large upfront investment. Technology, partnership, and knowledge have all converged to bring security into the next generation.
Conclusion
With XDR apps for response and one-click remediations, Singularity XDR and Singularity Marketplace continue to expand, offering deeper, more effective integrations that simplify the remediation cycle.
Automated actions are available today and will become more nuanced in how and when they are automatically invoked as our partners create new APIs for us to integrate with, to go deeper into their products, and unlock the full value of every layer in the stack to mitigate and remediate threats.
Interested in learning more? Read about our open approach to XDR that allows for connecting best-in-class products. Want to see how XDR works for your organization? Contact us or request a free Singularity XDR demo.


