Last week, PinnacleOne examined China’s application of emerging AI tools to augment their rapidly improving cyber capabilities and emphasized the urgency for defenders to keep pace.
This week, we focus on the recent arrest of a PRC national indicted for theft of Google AI IP and we identify lessons learned for firms to improve malicious insider threat detection and response.
Please subscribe to read future issues — and forward this newsletter to your colleagues to get them to sign up as well.
Feel free to contact us directly with any comments or questions: [email protected]

Insight Focus: Malicious Insider Threat to Strategic Enterprises
The recent indictment and arrest of a PRC national for theft and transfer of Google’s AI related trade secrets illustrates the nature and scope of the insider threat facing strategic enterprises.
The case shows how relatively unsophisticated techniques were able to evade Google’s data loss prevention system and insider threat program, and how a delayed response increased risk.
Firms working at the leading edge of technology (like frontier AI model labs) and those in the crosshairs for strategic geopolitical targeting must catch up to the scale of the threat, immediately.
Google’s Insider Detection and Investigation Failures
- An indicted lead software engineer, Ding Linwei worked on confidential LLM infrastructure and software systems that trained and ran Google Brain, DeepMind, and Anthropic IP.
- He exfiltrated over 500 confidential files by copying data from Google source files into the Apple Notes application on his Google-issued MacBook laptop, converted those notes into PDF files, and uploaded them from the Google network into a separate, personal Google drive account, which evaded detection by Google’s data loss prevention systems.
- He also had a fellow employee use his access badge to scan into his assigned Google office building while he was in China conducting business activities using the stolen information.
- Ding was only investigated by Google when he uploaded files from the Google network to a second personal account while he was in the PRC, but his access was not subsequently limited. He arrived in China on October 29th, but his presence was not detected until December 8th, 2023.
- Google suspended his network access and remotely locked his laptop 27 days after the investigation began, three days after he resigned, and only when Google discovered that Ding had presented his business plan at a Beijing investor conference as CEO of a company that would focus on the same technology stolen from Google.
Lessons Learned
- The attack surface goes beyond narrow trust boundaries and access control for crown jewels and extends across distributed or 3rd-party networks and infrastructure.
- Malicious insiders may spend years in the firm enhancing their access and conducting covert collection – more overt indicators tend to only arise after the horse has left the barn.
- Physical correlation of network detections enhanced by AI are necessary but not sufficient. Expert counterintelligence investigators must discern and mitigate at speed to mitigate enterprise risk.
- Tradecraft for lone wolf commercial espionage is less sophisticated than a foreign intelligence operation, but it was nevertheless successful in this case – the accelerating economic returns from AI businesses will exponentially increase the financial incentive for insider employees to steal.
- Frontier model labs and other firms working on strategic and prized technologies should consider (as an ideal, if potentially unreachable goal) security controls that mirror those used to protect government special access programs, including strict compartmentalization, personal reliability examinations, travel monitoring and reporting, comprehensive network monitoring, and continuous insider threat hunting. Design programs with the future value of the tech in mind.
Insider Threat Mitigation
Firms should develop and assess a comprehensive set of insider threat scenarios tailored to their threat model, technical controls, organizational design, and internal culture. See below for some example threat scenarios that span nation-state and lone-wolf/commercial threat actor profiles, plausible targets and objectives, and attack paths/exploitation methods.
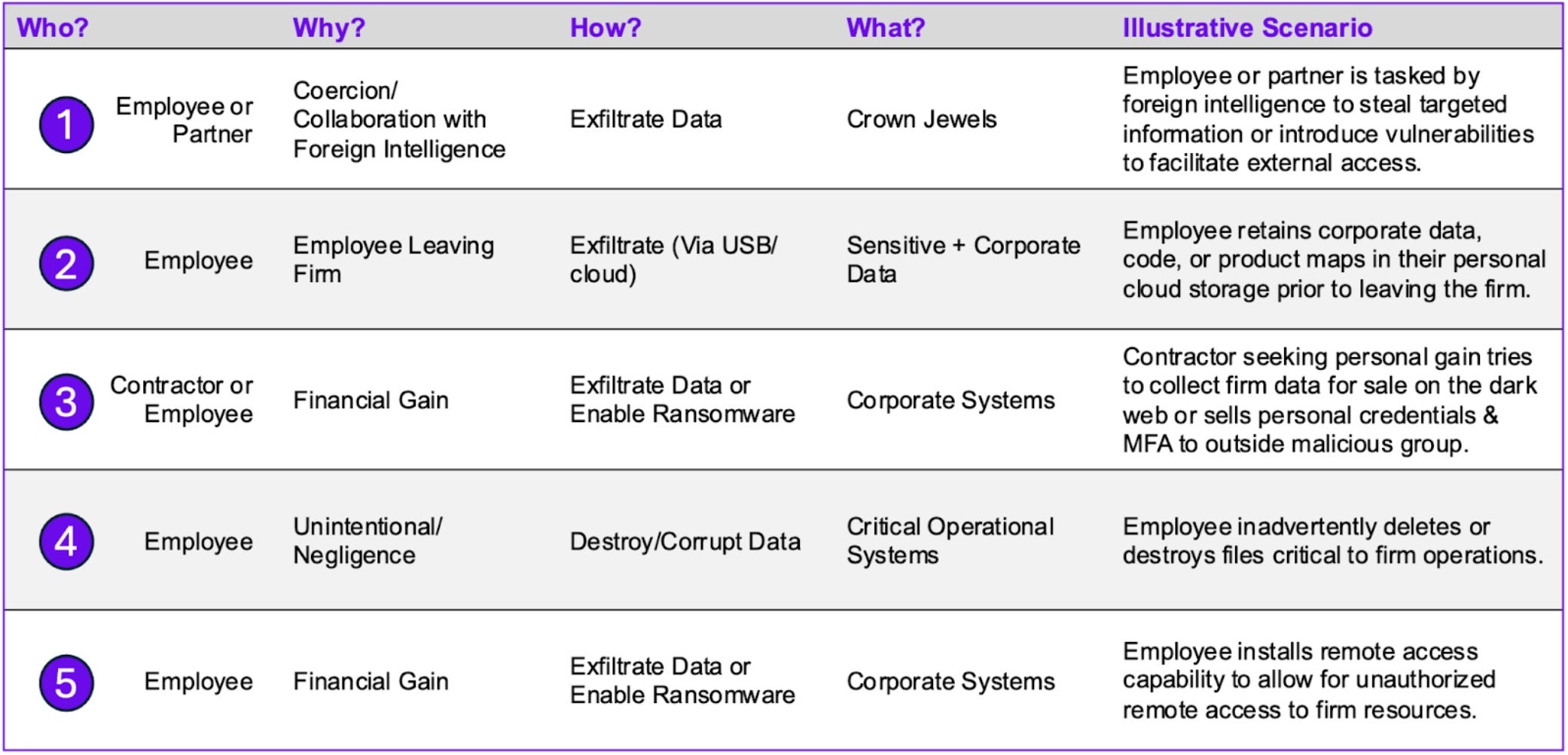
These scenarios are by no means comprehensive but should serve as a starting point for firms to validate controls and develop a roadmap for process, technology, and organizational improvements. In 2022, PinnacleOne worked with a firm exiting Russia to test over 100 insider scenarios. We found their detection and response capabilities (alerts, triage, escalation, etc.) mostly inadequate. We are also currently helping a systemically important SaaS firm assess and improve their insider trust program.
Implications for Geopolitically Targeted Multinationals
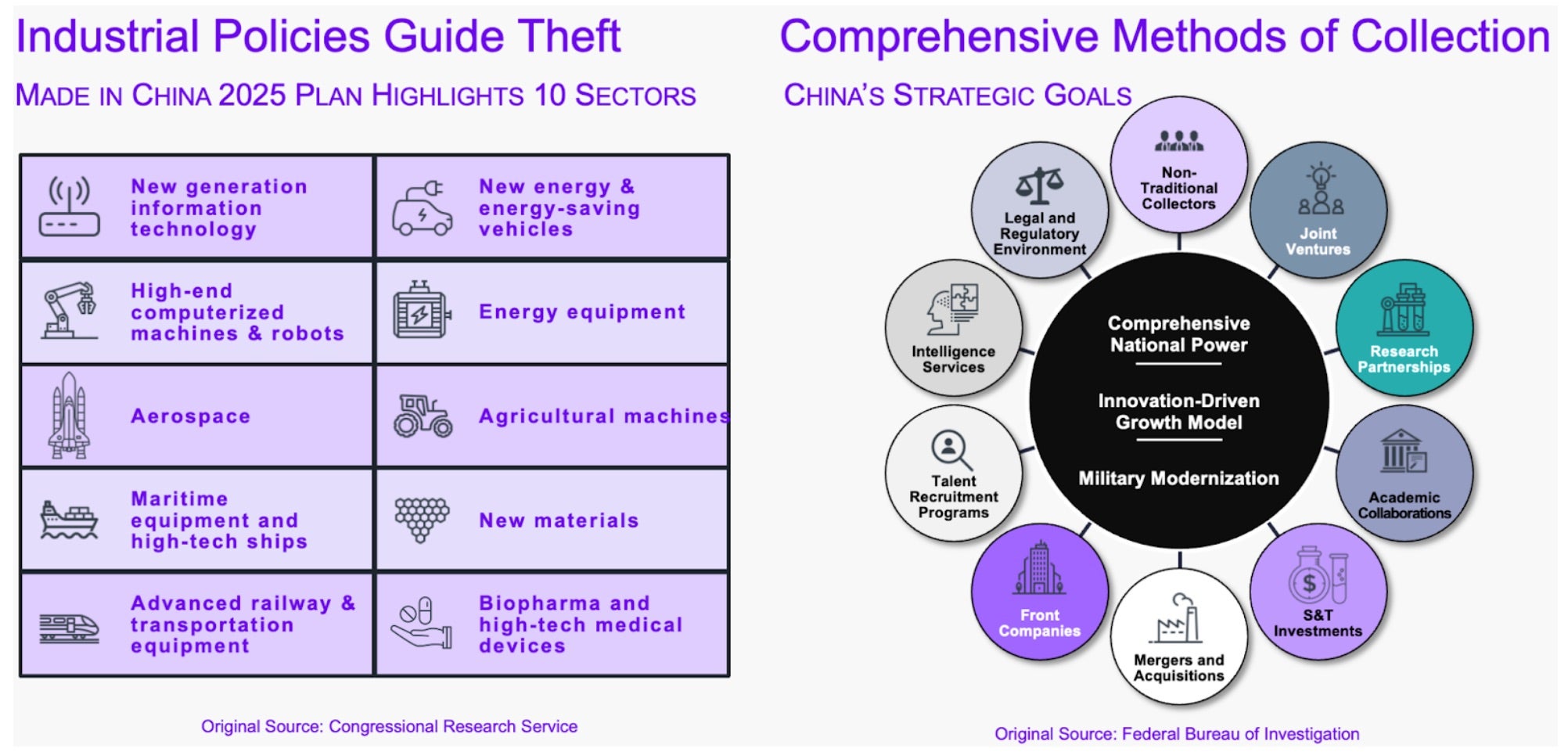
China has an explicit strategy to target industries via insider and cyber espionage to transfer valuable IP and know-how that supports economic competitiveness and military capabilities. The set of firms that fall into this geopolitical bullseye are known, but the list is expanding and the political incentives to pursue more aggressive targeting will continue to grow.
Insider threats extend beyond IP theft and include intentional weakening of cybersecurity controls (e.g., cloud misconfigurations by IT insiders) or even covert sabotage of products or services (where such sabotage might support tactical objectives in a conflict scenario). The threat is real and growing.