It’s been two months since Apple dropped the initial release of macOS Catalina, and after a rapid few supplemental updates and a first point upgrade in the first month, things appear to have slowed down to a normal cadence. This week, Apple dropped the public release of 10.15.2, a full month after showing developers the first beta. So, what’s changed in this update? Let’s take a look and see!

Features and Tweaks
After installing the 10.15.2 update, users should find they are now on build 19C57. While point updates are not typically opportunities for Apple to add new features, 10.15.2 does bring a small number of user level additions.
Apple News receives a new layout and now carries content from the Wall Street Journal and other “leading newspapers”, while Stocks adds links to related content at the end of articles. The Music app restores column browser view for managing the music library, while iTunes Remote now supports using an iOS device to remotely control the Music and TV apps on a Mac. More details are provided by Apple here.
Bug Fixes
The 10.15.2 update brings six patches for what appear to be privilege escalations in, among other APIs and services, CFNetwork Proxies (CVE-2019-8848), the Kernel (CVE-2019-8833, ) and Security (CVE-2019-8832).
There is also a fix for an arbitrary code execution bug in FaceTime (CVE-2019-8830) when handling a maliciously crafted video, and Catalina’s Bluetooth receives a patch for CVE-2019-8853 which could allow an application to read restricted memory.
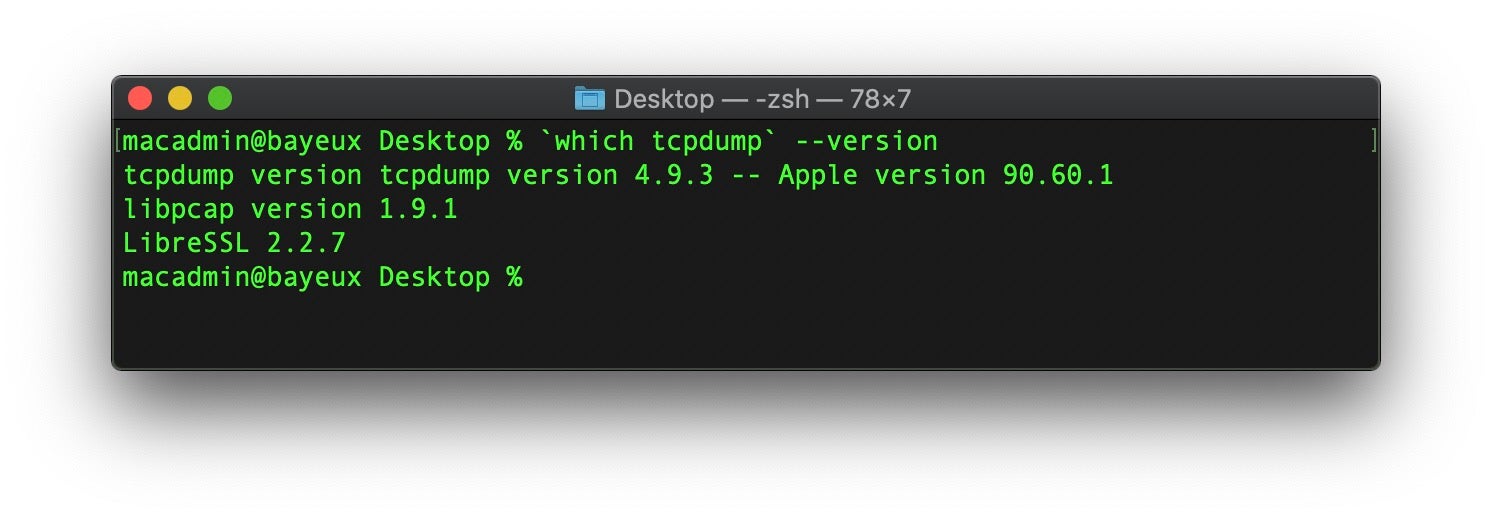
Apple also finally applied a patch for the opensource tcpdump and libpcap networking utilities. That patch has been available since September, but for reasons only Apple know this didn’t make the cut for the initial release of Catalina in October or the first point update after that. Having now just made it into macOS, it’s worth noting that the tcpdump 4.9.3 and libpcap version 1.9.1 are exclusive to Catalina, at least at the moment. Mojave and earlier OSs haven’t received the updated versions, which plug an astonishing 32 vulnerabilities with CVEs stretching back all the way from 2017 to 2019. While the vulns all have ‘Modified’ status in the NIST database, they at least have a description indicating the issue, save for the most recent one, CVE-2019-15167, which remains reserved.
Apple’s security notes also gave additional recognition to Kishan Bagaria and Tom Snelling for their assistance in what Apple have only described as an issue in “Accounts”. The same recognition also appears in the iOS and iPadOS 13.3 release notes. Bagaria has published a blog post detailing an iOS/iPadOS bug that allows a malicious user to cause a Denial-of-Service attack on nearby devices that have AirDrop enabled. Whether the bug applied to macOS as well hasn’t been mentioned, but credit in the Catalina security release notes suggests that macOS may have either been susceptible to some version of “AirDoS”, as Bagaria has dubbed it, or needed some kind of update to maintain AirDrop compatibility with patched mobile devices.
Security Changes Apple Didn’t Announce
As usual with macOS updates, there’s a few things under the hood that have occurred that Apple do not make public statements about but which are nevertheless of interest to the security community. As described by researcher Scott Knight and independent macOS developer and blogger Howard Oakley, 10.15.2 has seen some important changes to XProtect.
Let’s take a look at the two XProtect bundles side by side to see how they differ. Here, I’ve made local copies of the original 10.15.1 and 10.15.2 bundles so that I can safely mess with them.
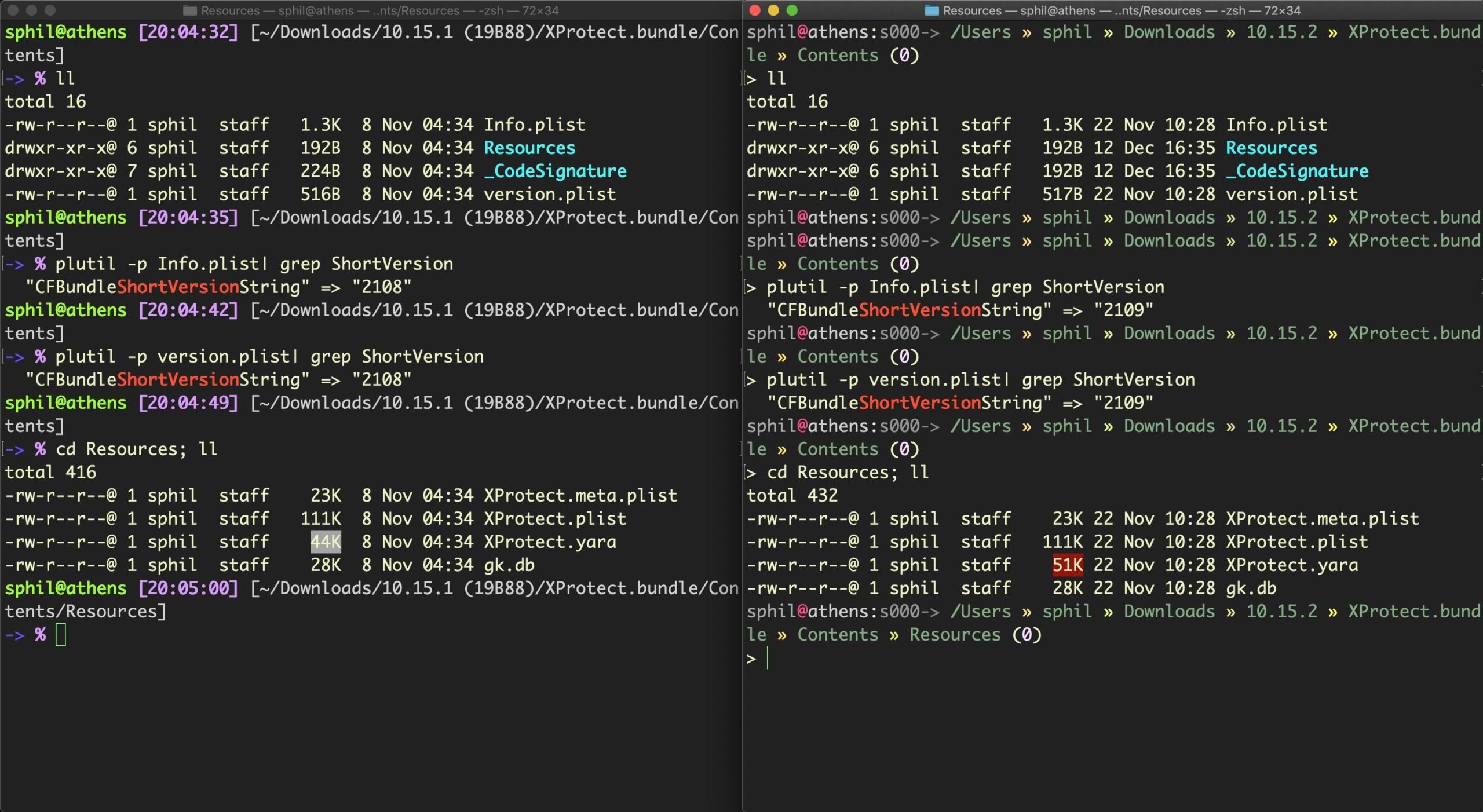
As we can see, the version number has been bumped in the Info.plist and version.plist files from v2108 to v2109.
The most obvious change is in the XProtect.yara files, with the updated file having increased in size from 44KB to 51KB. Let’s run a diff on them and output only the additions to a new text file (here I’ve changed the respective file names to make it easier to see which is which).
$ diff XProtect_10_15_1.yara XProtect_10_15_2.yara | grep > | sed 's/>//' >> Xprotect_new.txt
Let’s examine that in Vi and see what we’ve got. There’s 109 additional lines.
We can do a quick grep to see how many rules or new families there are.
$ grep 'rule XProtect_' Xprotect_new.txt
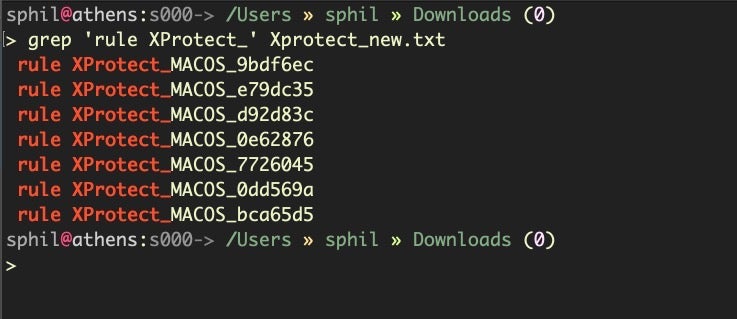
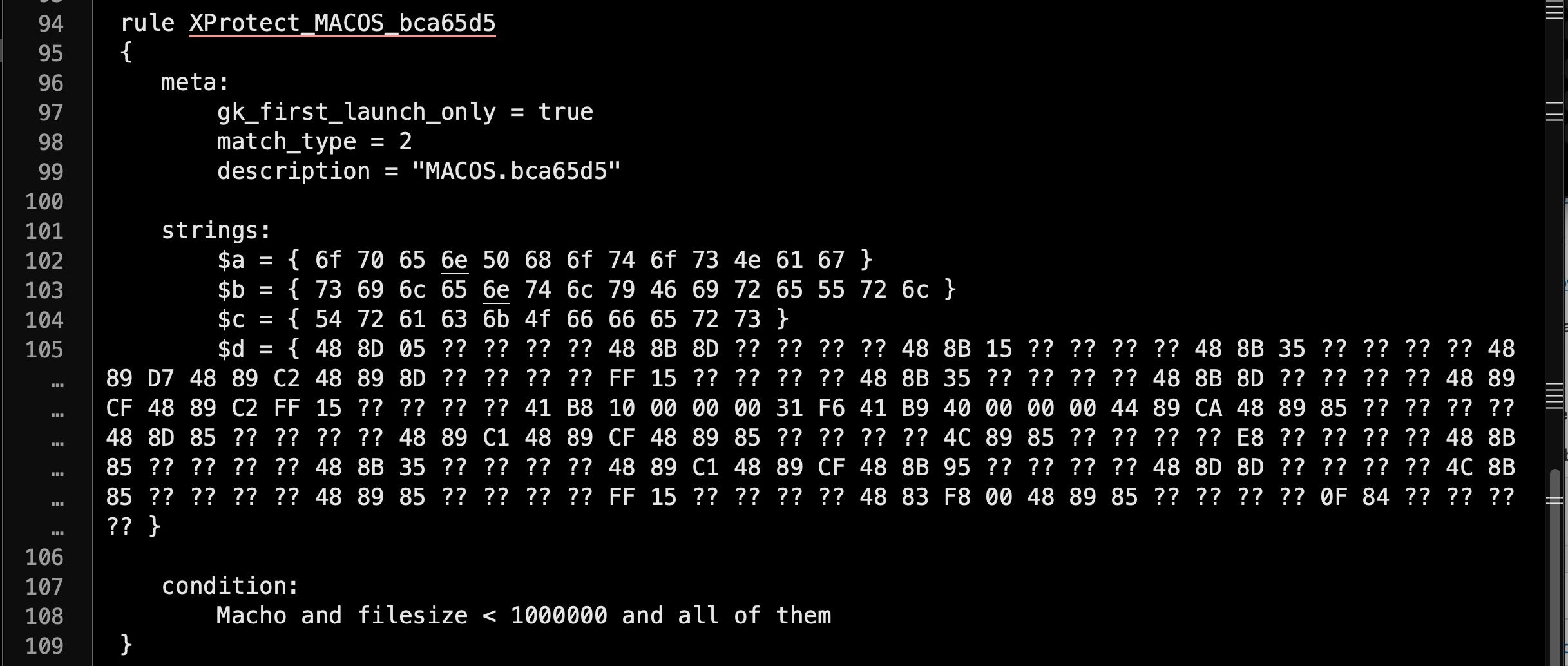
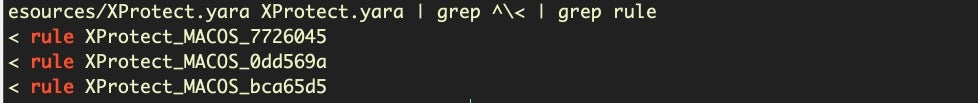
It appears there are 7 new families, three of which – MACOS_7726045, MACOS_0dd569a, and MACOS_bca65d5 – have a curious new meta label gk_first_launch_only set to the value of true.
$ grep -B3 'gk_first' Xprotect_new.txt
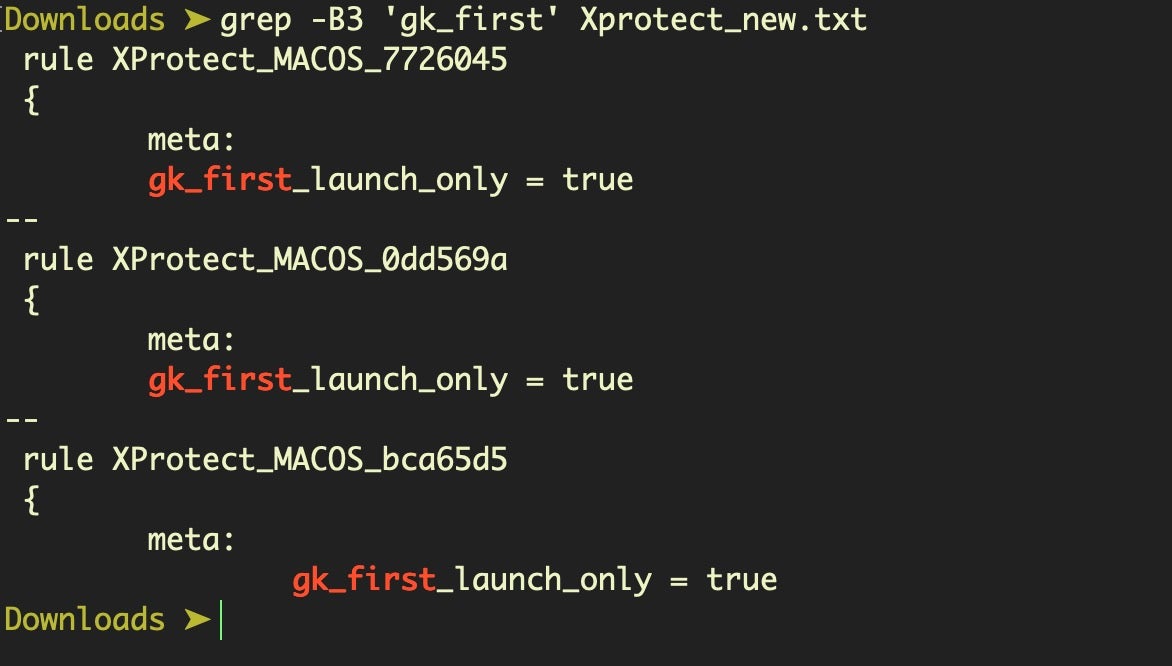
As one of the changes made to Catalina’s Gatekeeper protections is to include security checks not just on first launch but at unspecified times after that, it’s plausible that this label may be related to that, perhaps telling XProtect to skip these checks on code that’s already been checked and passed. At this point that remains speculation until we’ve had further time to correlate the rules against actual samples (a list of samples that match the rules has already been collated by Scott Knight here).
Importantly, macOS users that are still on Mojave 10.14.6 or earlier should be aware that at present the v2109 XProtect update has not been seeded to those earlier macOS versions, so you are only getting the updated protection if you are on Catalina.
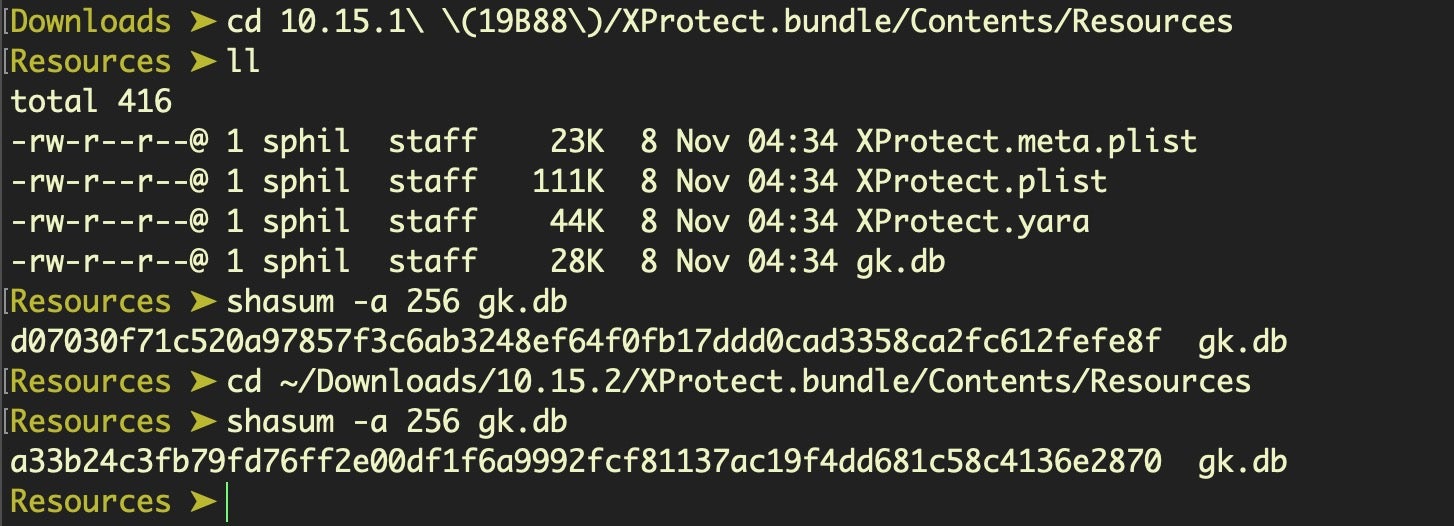
The gk.db database, a new security resource in Catalina that blocks developers by Team ID and which may be related to Notarization, resides within the XProtect bundle’s Resources folder. The 10.15.1 and 10.15.2 versions turn out to have different shasums, and if you dump the SQLite3 databases and run a diff on them they might seem at first glance to be different. In fact, the two databases have identical contents, but the data in the tables appears to have been sorted differently.
There does not appear to have been any significant change to Apple’s other security technology, the MRT (Malware Removal Tool) app. The executable does have a different shasum on 10.15.2, though:
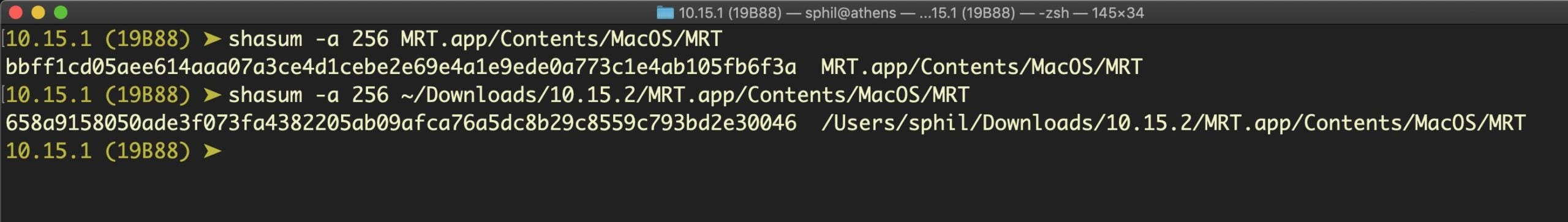
However, MRT.app’s version number remains the same as it is on both 10.15.1 and 10.14.6 at v1.50. Examination of the executables indicates the 10.15.2 version to be functionally identical to 10.15.1 despite the change in hash. The differing shasum looks to be simply a consequence of the application being re-signed. If you go looking for MRT.app, remember that on Catalina it has moved from /System/Library/CoreServices folder to /Library/Apple/System/Library/CoreServices, and now only keeps company with a few other security related tools. An alias is provided to this location from the main CoreServices folder in /System/Library/CoreServices.
Update
Just as we prepared this post, Apple dropped another XProtect update – it’s nice to see them coming so frequently again! – v2110. Analysis shows that this seems to be a correction for errors in 2109, including removing the three rules that contained the gk_first_launch_only meta tag.
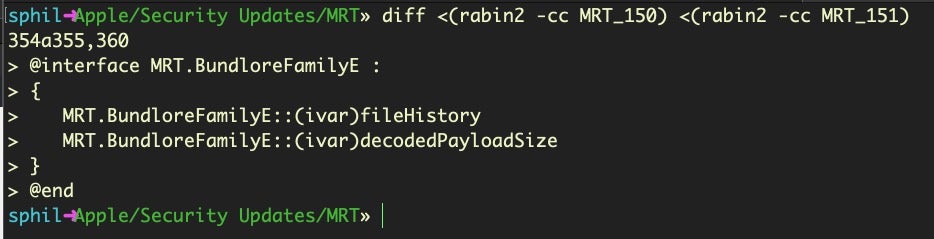
There was also an update to MRT.app, bringing it to version 1.51. The only change seems to have been adding a new variant of Bundlore commodity adware, BundloreFamilyE.
Conclusion
As always, users are reminded that timely patching is a crucial part of your security posture. As Catalina begins to mature and the number of security bug fixes that haven’t been back ported to Mojave and earlier grows, the urgency for those that haven’t yet made the jump to 10.15 to update will only increase.
Remember also that whether you’re running the latest macOS or an older, unpatched version, the built-in security tools are only going to block known malware families, and then only temporarily until the malware authors modify their code to avoid simple string search matches like those used in XProtect. To ensure that your devices are fully-protected, an on-device security solution that employs behavioral detection is the safest bet.


