The LostTrust ransomware operation is a new multi-extortion threat that emerged in September 2023. Our analysis of LostTrust malware payloads indicates that the family is an evolution of SFile and Mindware, and that all three follow similar operations and tradecraft to MetaEncryptor. Similarities between the LostTrust leaks sites and the earlier MetaEncryptor leaks sites are also apparent, while aspects of SFile encryptor previously observed with MetaEncryptor campaigns are still in use with the LostTrust payloads we analyzed.
In this analysis, we provide a high-level technical outline of where these ransomware families and their operations overlap. We will examine LostTrust payload behavior as well as compare artifacts to the SFile and Mindware families.

LostTrust Ransom Demands
LostTrust victims are presented with a ransom note that attempts to portray the gang as providing a service, a fake veneer that is commonly adopted by cybercriminals perpetrating intrusions. An excerpt from a LostTrust ransom note illustrates this approach:
However, clients usually considered the found vulnerabilities to be minor and poorly
paid for our services.
So we decided to change our business model. Now you understand how important it is
to allocate a good budget for IT security.
This is serious business for us and we really don’t want to ruin your privacy,
reputation and a company.
We just want to get paid for our work whist finding vulnerabilities in various networks.
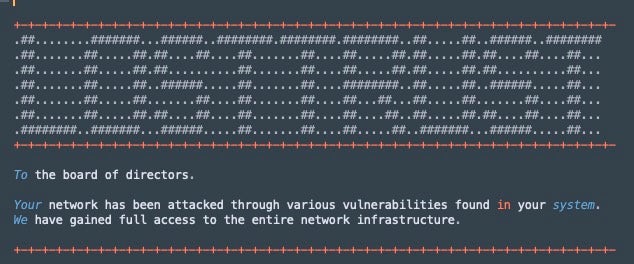
The LostTrust leaks site contains information claiming that the gang are “young people who identify themselves as specialists in the field of network security”. Thinly-veiled threats that stolen data will be made available to interested parties if the gang do not receive payment are followed by a warning that notification of the victim’s breach will be widely publicized.

LostTrust Execution Details
In order to prevent existing processes on the victim device inhibiting encryption or data exfiltration, LostTrust ransomware payloads attempt to discover and terminate a plethora of services and processes. Critical services associated with the processes belonging to Microsoft Exchange, MSSQL, SharePoint, Tomcat, postgresql and others are terminated if identified.
The ransomware initiates numerous, hidden CMD.EXE sessions in order to carry out these tasks. The hidden CMD.EXE windows subsequently host the observed WMIC, NET, SC, taskkill, VSSADMIN and wevtutil commands.
In addition to process discovery and termination, the ransomware attempts to remove VSS (Volume Shadow Copies) via VSSADMIN, as well as clearing out all Windows Event Logs via wevtutil.exe.
LostTrust payload execution output is streamed to a visible command window, allowing for clear observation of the various encryption stages.
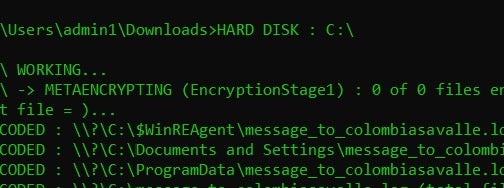
The full list of observed commands is as follows:
"C:\Windows\System32\cmd.exe" /c wevtutil cl Application "C:\Windows\System32\cmd.exe" /c wevtutil cl security "C:\Windows\System32\cmd.exe" /c wevtutil cl setup "C:\Windows\System32\cmd.exe" /c wevtutil cl system "C:\Windows\System32\cmd.exe" /c vssadmin.exe delete shadows /all /quiet "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%Firebird%'" CALL STOPSERVICE "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%MSSQL%'" CALL STOPSERVICE "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%SQL%'" CALL STOPSERVIC "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%Exchange%'" CALL STOPSERVICE "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%wsbex%'" CALL STOPSERVICE "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%postgresql%'" CALL STOPSERVICE "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%BACKP%'" CALL STOPSERVICE "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%tomcat%'" CALL STOPSERVICE "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%SharePoint%'" CALL STOPSERVICE "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%SBS%'" CALL STOPSERVICE "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%Firebird%'" CALL ChangeStartMode 'Disabled' "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%MSSQL%'" CALL ChangeStartMode 'Disabled' "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%SQL%'" CALL ChangeStartMode 'Disabled' "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%Exchange%'" CALL ChangeStartMode 'Disabled' "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%wsbex%'" CALL ChangeStartMode 'Disabled' "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%postgresql%'" CALL ChangeStartMode 'Disabled' "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%BACKP%'" CALL ChangeStartMode 'Disabled' "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%tomcat%'" CALL ChangeStartMode 'Disabled' "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%SharePoint%'" CALL ChangeStartMode 'Disabled' "C:\Windows\System32\cmd.exe" /c WMIC SERVICE WHERE "caption LIKE '%SBS%'" CALL ChangeStartMode 'Disabled' "C:\Windows\System32\cmd.exe" /c sc config FirebirdServerDefaultInstance start= disabled "C:\Windows\System32\cmd.exe" /c taskkill /IM fb_inet_server.exe /F "C:\Windows\System32\cmd.exe" /c net stop FirebirdServerDefaultInstance "C:\Windows\System32\cmd.exe" /c C:\Windows\system32\net1 stop FirebirdServerDefaultInstance "C:\Windows\System32\cmd.exe" /c taskkill /IM sqlservr.exe /F "C:\Windows\System32\cmd.exe" /c sc config MSSQLSERVER start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSSQL$SQLEXPRESS start= disabled "C:\Windows\System32\cmd.exe" /c net stop MSSQLSERVER "C:\Windows\System32\cmd.exe" /c C:\Windows\system32\net1 stop MSSQLSERVER "C:\Windows\System32\cmd.exe" /c net stop MSSQL$SQLEXPRESS "C:\Windows\System32\cmd.exe" /c C:\Windows\system32\net1 stop MSSQL$SQLEXPRESS "C:\Windows\System32\cmd.exe" /c taskkill /IM pg_ctl.exe /F "C:\Windows\System32\cmd.exe" /c sc config postgresql-9.0 start= disabled "C:\Windows\System32\cmd.exe" /c net stop postgresql-9.0 "C:\Windows\System32\cmd.exe" /c sc config MSExchangeAB start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeAntispamUpdate start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeEdgeSync start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeFDS start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeFBA start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeImap4 start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeIS start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeMailSubmission start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeMailboxAssistants start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeMailboxReplication start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeMonitoring start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangePop3 start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeProtectedServiceHost start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeRPC start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeSearch start= disable "C:\Windows\System32\cmd.exe" /c sc config wsbexchange start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeSA start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeThrottling start= disabled "C:\Windows\System32\cmd.exe" /c sc config MSExchangeTransportLogSearch start= disabled "C:\Windows\System32\cmd.exe" /c net stop MSExchangeAB "C:\Windows\System32\cmd.exe" /c net stop MSExchangeAntispamUpdate "C:\Windows\System32\cmd.exe" /c net stop MSExchangeEdgeSync "C:\Windows\System32\cmd.exe" /c net stop MSExchangeImap4 "C:\Windows\System32\cmd.exe" /c net stop MSExchangeMailboxReplication "C:\Windows\System32\cmd.exe" /c net stop MSExchangeProtectedServiceHost
Supported Command-line Arguments
LostTrust payloads support the following command-line arguments:
| –enable-shares | enable discovery and encryption of accessible network volumes |
| –onlypath | Only encrypt files in the specified path. |
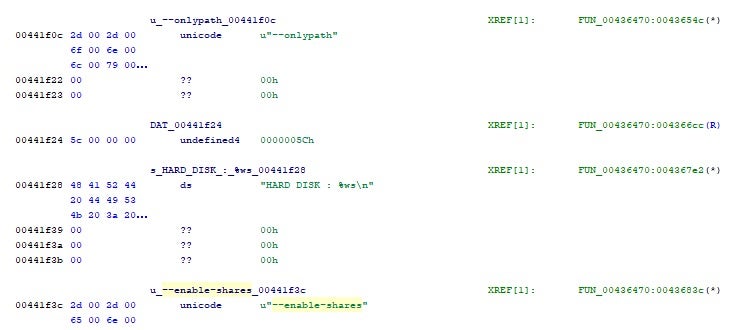
The --enable-shares option has been seen in previous Sfile/Mindware samples. Notably, however, LostTrust does not include previously seen SFile or Mindware parameters such as --killsusp.
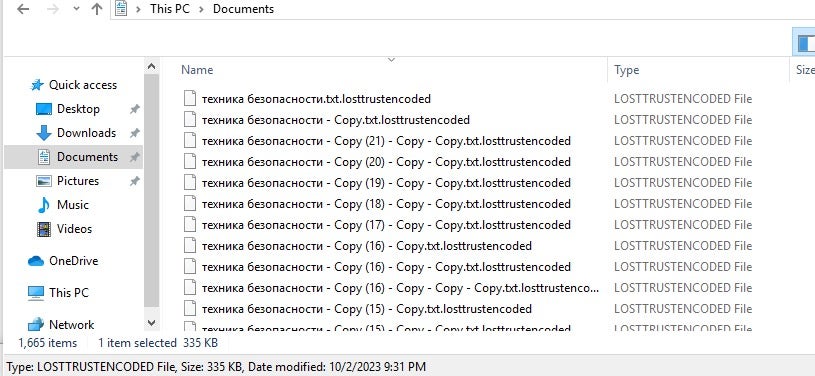
Encrypted files are modified with the “.losttrustencoded” file extension, and a LostTrust ransom note is written to each folder containing encrypted items as !!LostTrustEncoded.txt.
Similarities to Mindware and SFile
We previously reported on the connection between Mindware and SFile, and LostTrust bears indications that it is an extension of this lineage. LostTrust payloads, like those deployed by MetaEncryptor before, are based on the SFile encryptor. As such, the payloads for LostTrust and MetaEncryptor behave in a similar fashion, and produce similar artifacts. This includes overlap of the extensions to include in the encryption process, as well as what to exclude.
LostTrust handles exclusions via pattern/string (like the predecessors). The full list of excluded patterns in observed LostTrust samples is:
| \$RECYCLE.BIN\ | \all users\microsoft\ | \All Users\Microsoft\ |
| \Application Data\Microsoft\ | \boot\ | \cache\ |
| \cache2\ | \Common Files\ | \Common\Microsoft\ |
| \Default\Extensions\ | \drivers\ | \far manager\ |
| \google\ | \ida 6.8\ | \ida 7.0\ |
| \inetpub\logs\ | \intel\ | \Local Settings\Microsoft\ |
| \Local\Microsoft\ | \LocalLow\Microsoft\ | \mozilla\ |
| \msocache\ | \perflogs\ | \Program Files\Internet Explorer\ |
| \Program Files\Microsoft Games\ | \ProgramData\Microsoft\ | \Roaming\Microsoft\ |
| \System\msadc\ | \Temp\ | \Temporary Internet Files\ |
| \tor browser\ | \windows.old\ | \windows\system\ |
| \windows\system32\ | \windows\syswow64\ | \windows\winsxs\ |
| \WindowsPowerShell\ | \wsus\ | %windir% |
| $windows.~bt | $windows.~ws | autorun.inf |
| boot.ini | bootfont.bin | bootmgr |
| bootsect.bak | desktop.ini | iconcache.db |
| ntldr | ntuser.dat | ntuser.dat.log |
| ntuser.ini | thumbs.db | |
| :\system volume information\ | ! cynet ransom protection(don’t delete) | !losttrustencoded.txt |
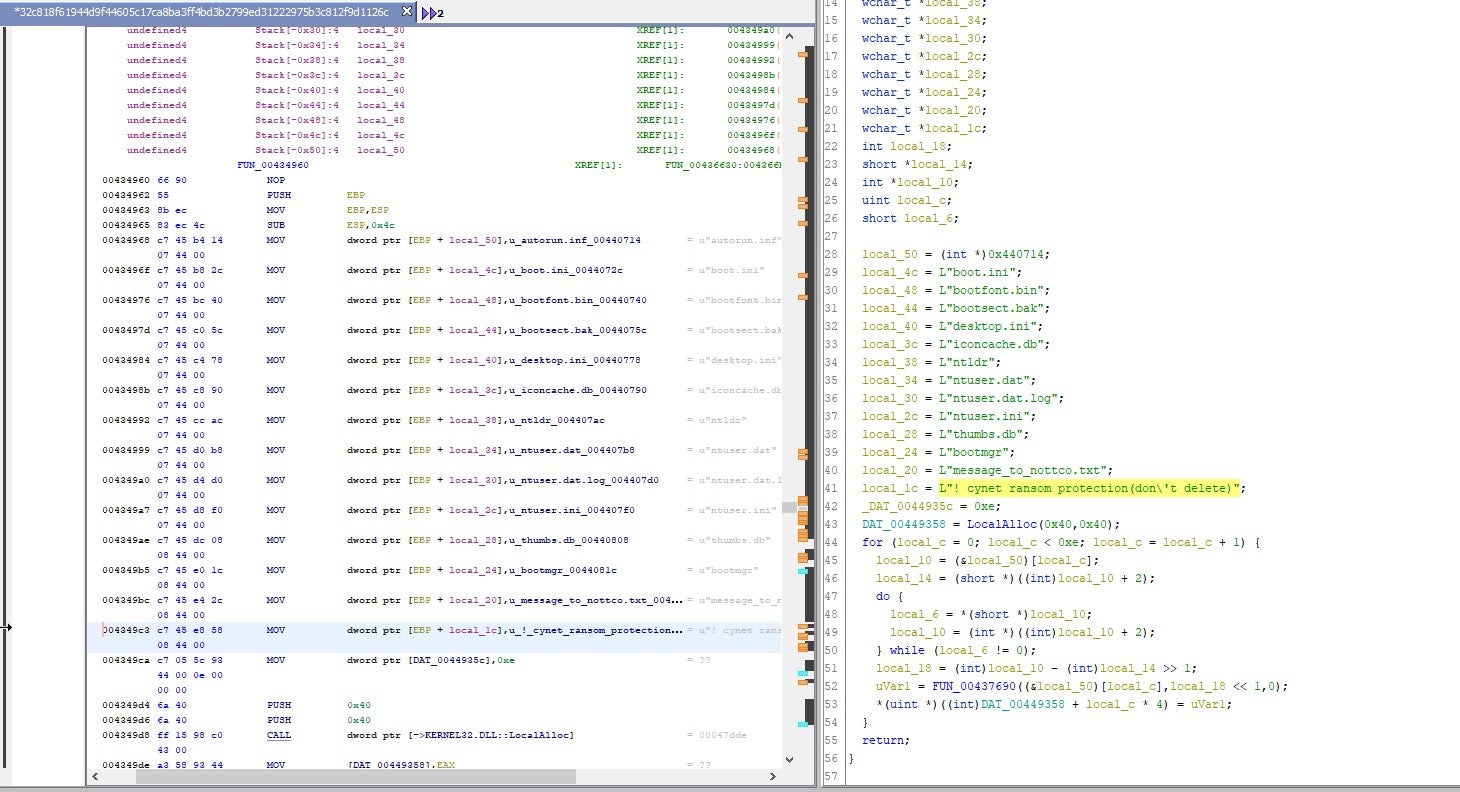
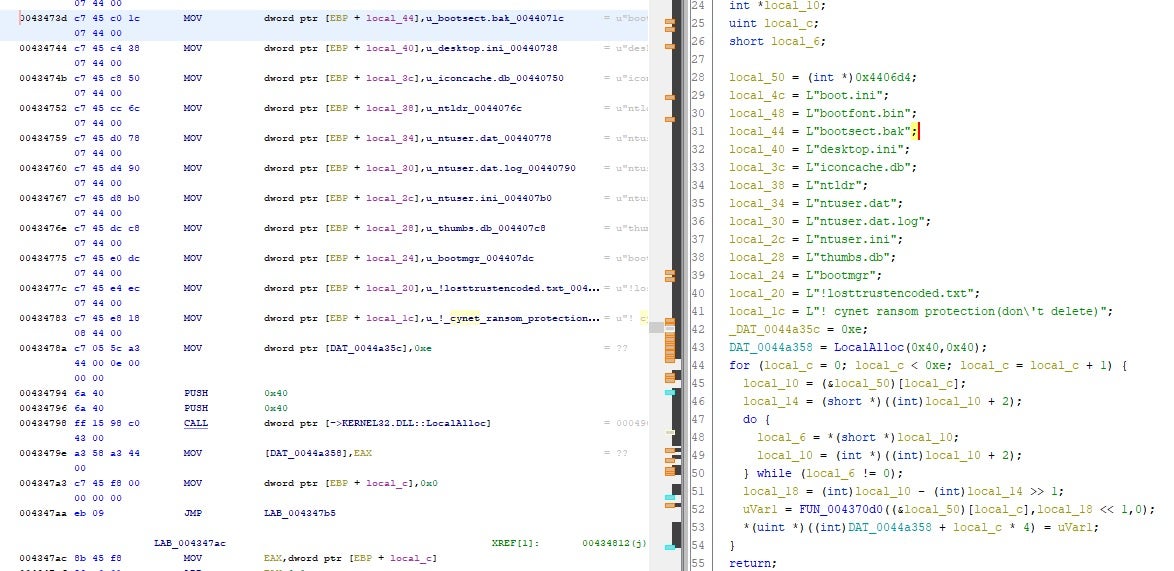
Encryption inclusion/exclusion in LostTrust looks similar to its Mindware and SFile predecessors.
Victim Blog Site
The TOR-based blog site for LostTrust appears to be a direct facsimile of the MetaEncryptor blog. Formatting and contact information (TOX) all match up. While there are no direct victim overlaps between the LostTrust and MetaEncryptor sites, some victims listed on LostTrust have been previously listed on leaks sites such as Royal, LockBit 3, and Medusa.
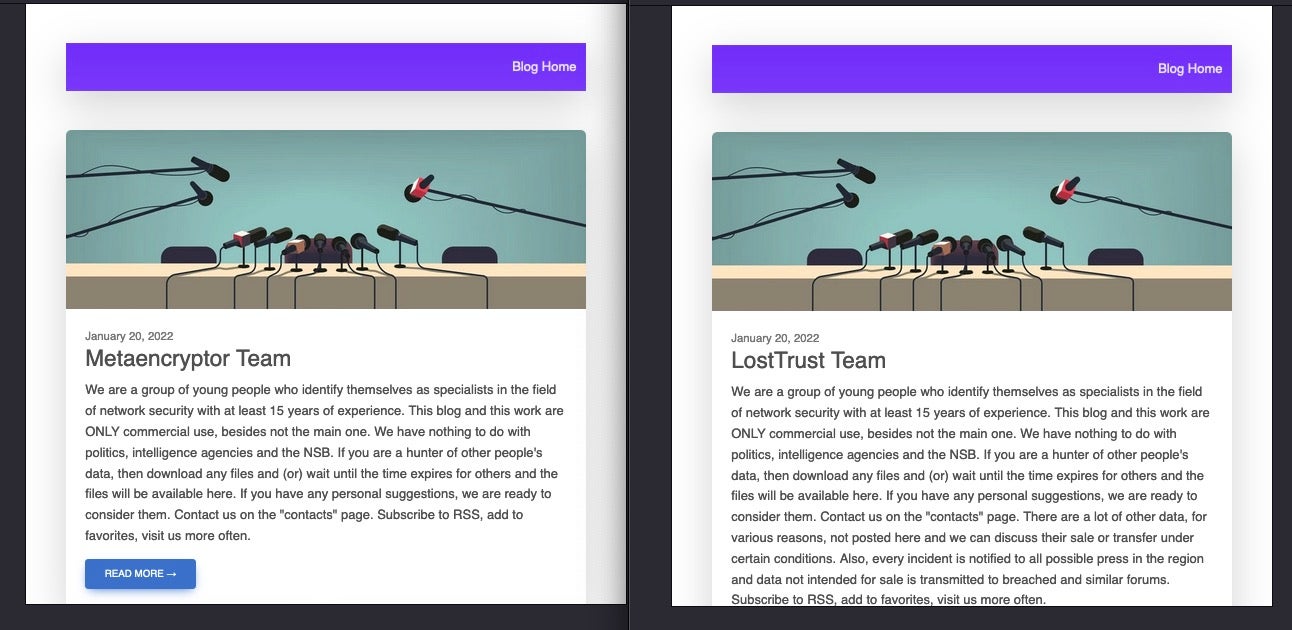
At the time of writing, 53 victims are listed on the LostTrust blog and 13 on the MetaEncryptor blog. Both blog sites remain active, while the MetaEncryptor blog has also been updated recently.
Comparison of LostTrust, Mindware and SFile Ransom Notes
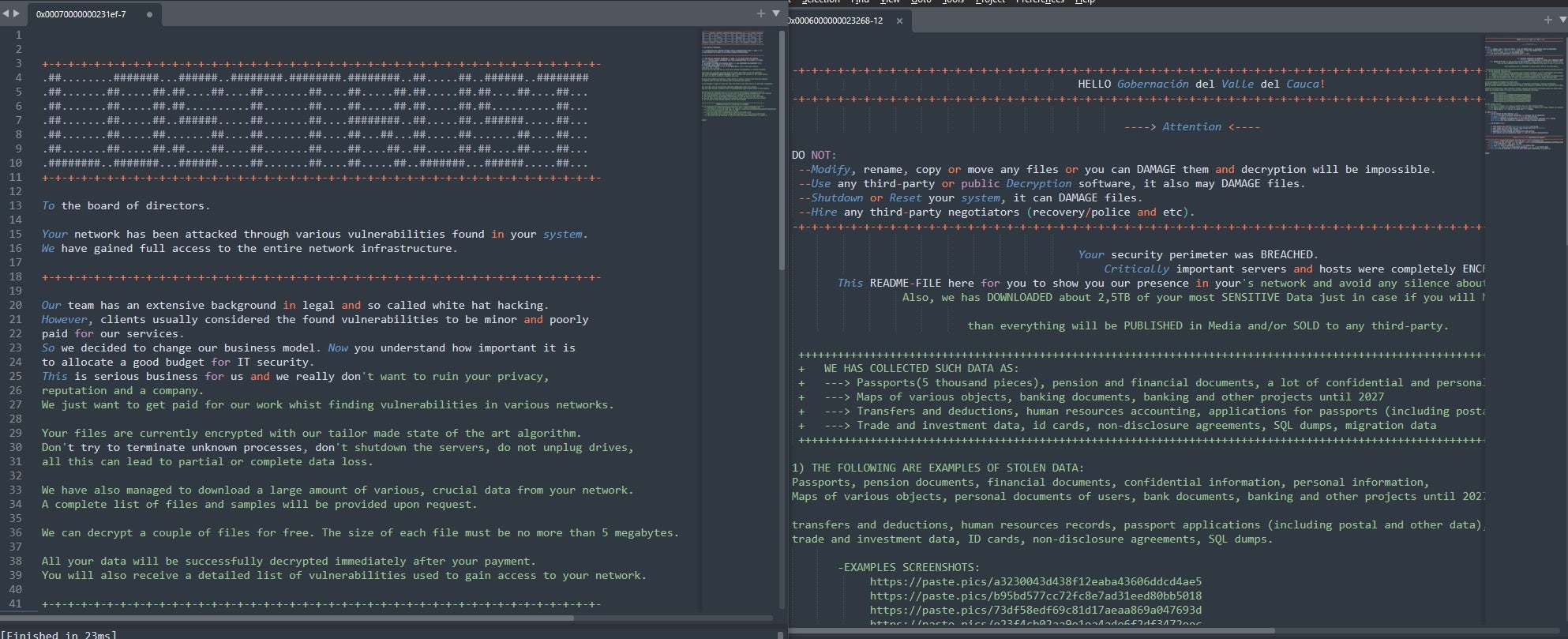
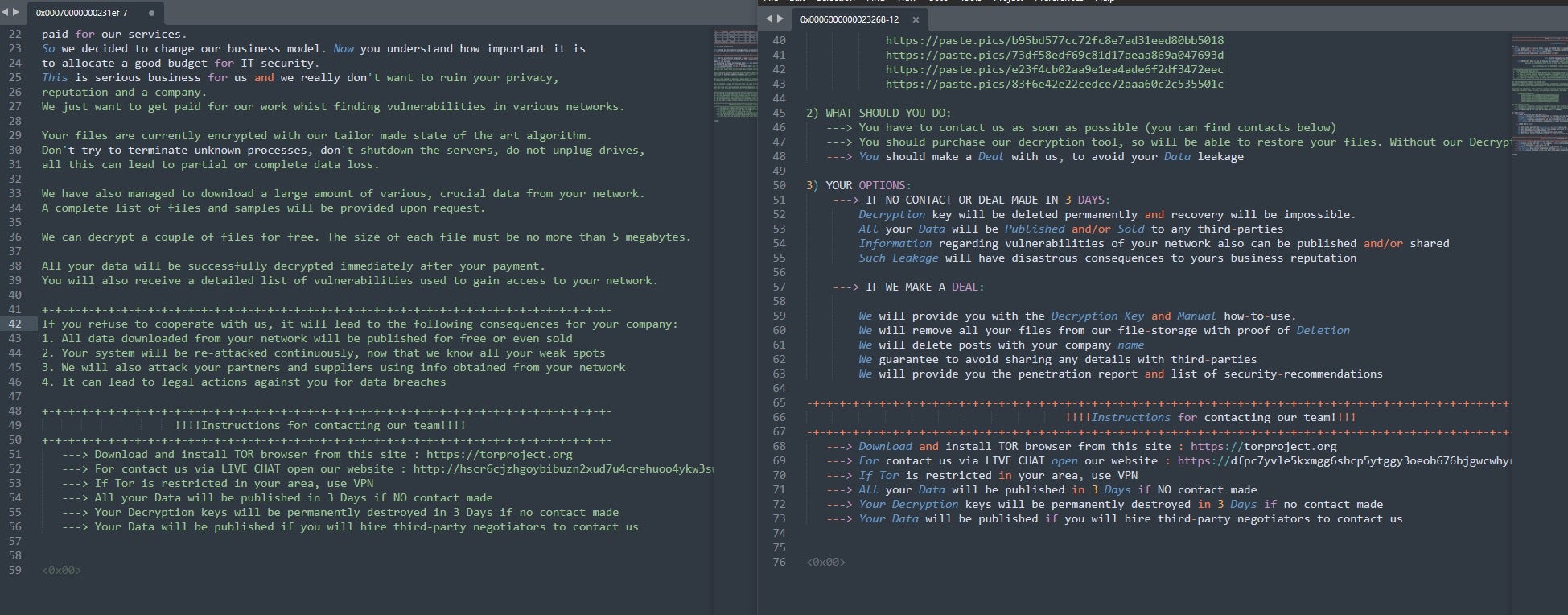
Ransom note construction is also similar across relevant Mindware and LostTrust malware samples.
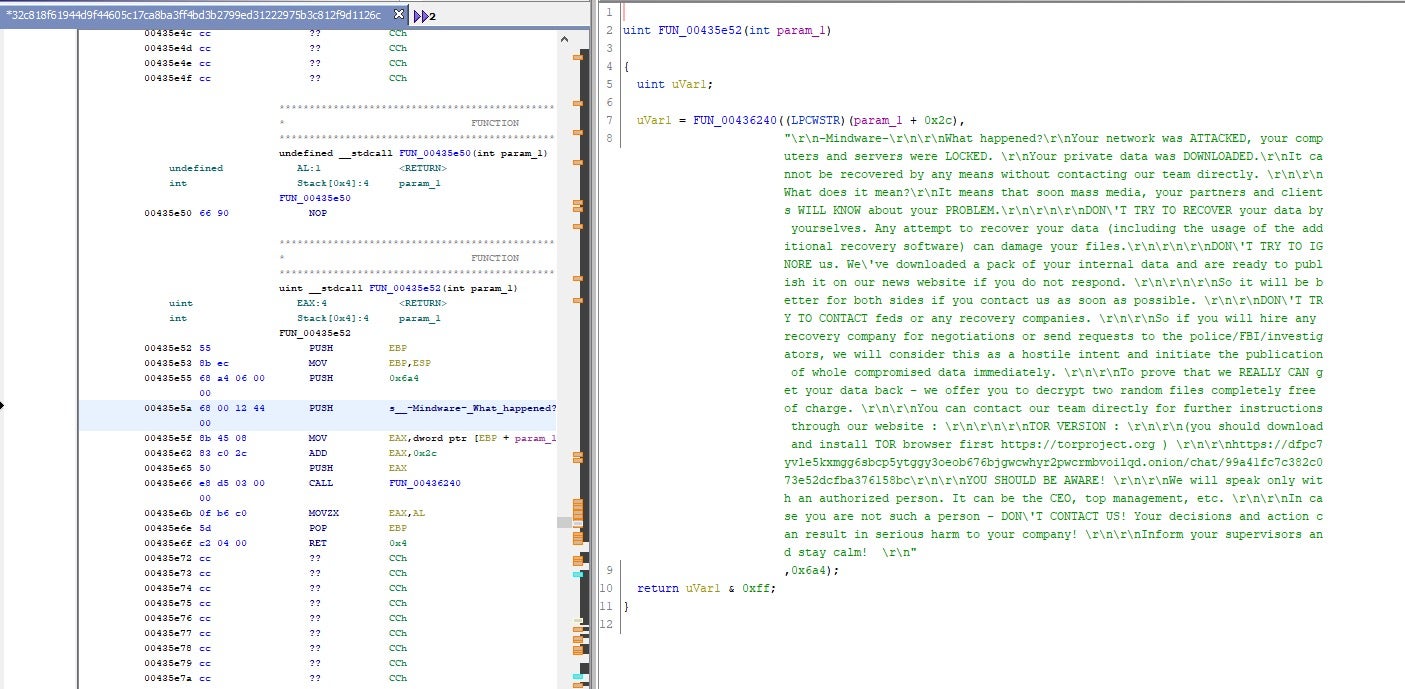
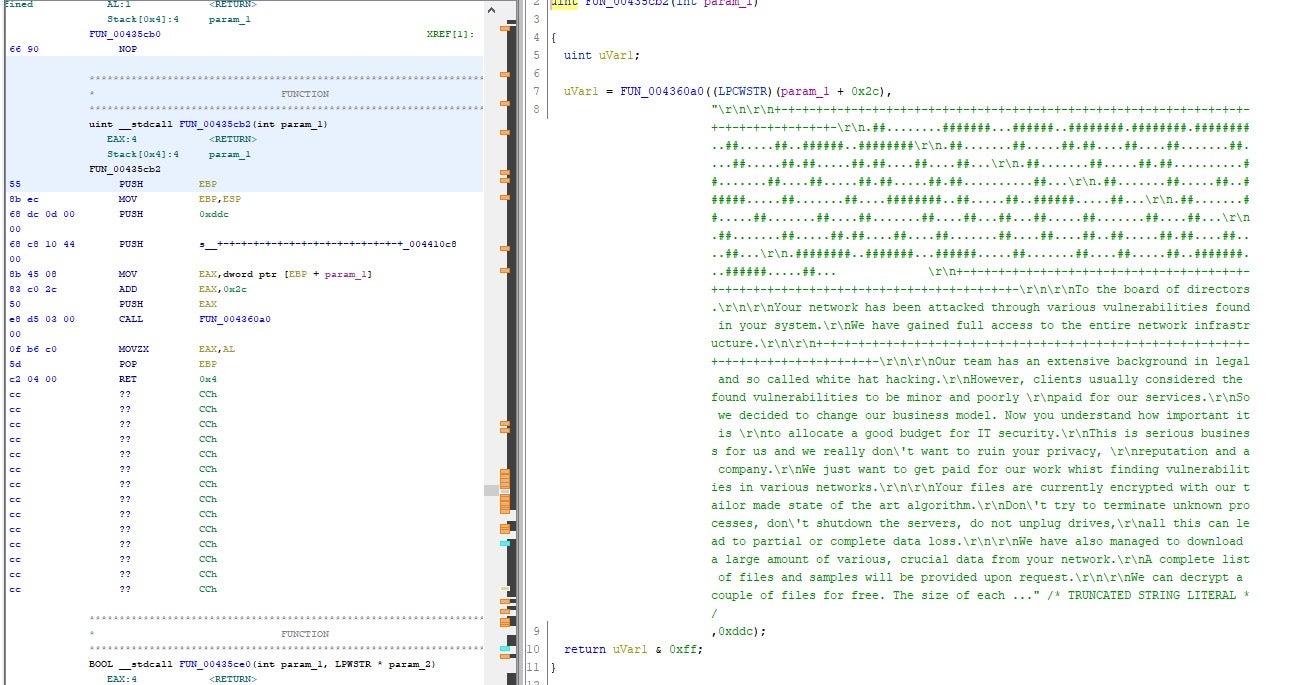
MetaEncryptor Strings and Artifacts
LostTrust, like SFile and Mindware, contains known references and functions around encryption staging.
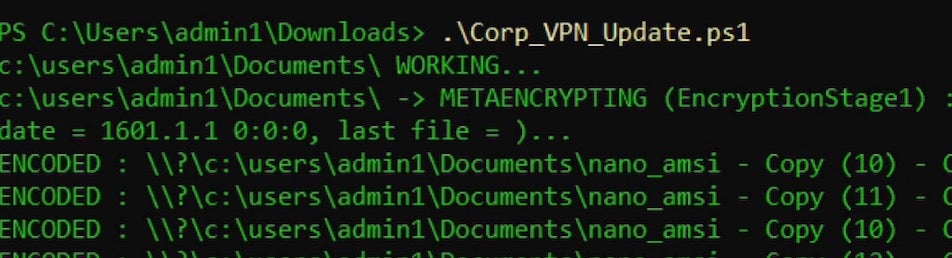
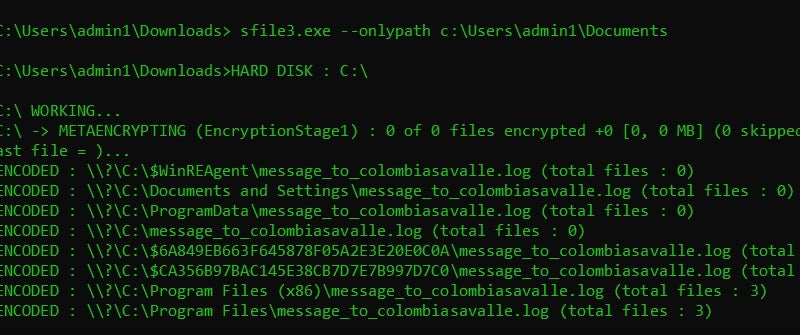
The cross-references to MetaEncryptor encryption stage can be viewed within the LostTrust payload binaries as well.
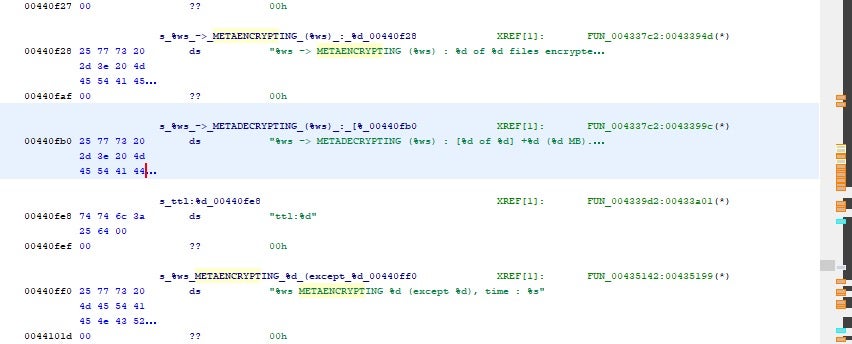
Debug Paths & String Artifacts
Throughout the timeline of SFile to LostTrust, we see some commonalities with regards to the included debug paths and string artifacts.
| SFile | Mindware | LostTrust |
| C:\fake_exe.pdb | D:\fake.pdb | C:\fake_exe.pdb |
| D:\fake.pdb | C:\fake_exe.pdb | |
| D:\code\ransomware_win\bin\decoder.pdb |
There is some variance among the email addresses provided in the ransom notes across these families as well. For example:
SFile
| clark.rotband[@]mailfence[.]com | finbdodscokpd[@]privatemail[.]com |
| gnidhyg[@]protonmail[.]com | greemsy.jj[@]protonmail[.]ch |
| jj.greemsy[@]mailfence[.]com | johny1cashusa[@]protonmail[.]ch |
| johny2[@]mailfence[.]com | johny2recoveryusa[@]protonmail[.]com |
| johny3[@]mailfence[.]com | jorge.smith[@]mailfence[.]com |
| mally[@]mailfence[.]com | mallyrecovery[@]protonmail[.]ch |
| mandysales[@]mailfence[.]com | primethetime[@]protonmail[.]com |
| recoverfiles[@]ctemplar[.]com | recoverfilesquickly[@]ctemplar[.]com |
| salesmandy[@]protonmail[.]com |
Mindware
| cacaoocacaooohusl[@]onionmail[.]org | corpovigiligiurati[@]onionmail[.]org |
| corpovigiligiuratiii[@]mailfence[.]com | lifespire[@]mailfence[.]com |
| lifespire[@]onionmail[.]org | niss.brandon[@]mailfence[.]com |
| niss.brook[@]onionmail[.]org | pationatiforsa[@]mailfence[.]com |
MetaEncryptor
| hamfrelors[@]proton[.]me | hermond.glass[@]mailfence[.]com |
SentinelOne Detects and Protects Against LostTrust Ransomware
SentinelOne Singularity detects and prevents malicious behaviors and artifacts associated with LostTrust ransomware.
Conclusion
In this analysis we have provided a technical outline of where these ransomware families and operations overlap. When LostTrust’s blog emerged in September 2023, many eyebrows were raised given the immediate similarities noticed between the LostTrust and MetaEncryptor sites. Our current observations and analysis indicate that “LostTrust” is an evolution of SFile and Mindware.
Organizations without SentinelOne are recommended to review the indicators provided below and throughout this post.
Indicators of Compromise
SFile
0f20e5ccdbbed4cc3668577286ca66039c410f95
14e4557ea8d69d289c2432066d860b60a6698548
28f73b38ace67b48e525d165e7a16f3b51cec0c0
5ffac9dff916d69cd66e91ec6228d8d92c5e6b37
665572b84702c4c77f59868c5fe4d0b621f2e62a
6960beedbf4c927b75747ba08fe4e2fa418d4d9b
8c507d26c2fec90707320ffb721ae626139bbf11
a67686b5ce1d970a7920b47097d20dee927f0a4d
bdb0c0282b303843e971fbcd6d2888d834da204c
Mindware
46ca0c5ad4911d125a245adb059dc0103f93019d
9bc1972a75bb88501d92901efc9970824e6ee3f5
ae974e5c37936ac8f25cfea0225850be61666874
e9b52a4934b4a7194bcbbe27ddc5b723113f11fe
f91d3c1c2b85727bd4d1b249cd93a30897c44caa
MetaEncryptor
e04760f670fab000c5ff01da39d4f4994011e581
LostTrust
09170b8fd03258b0deaa7b881c46180818b88381


