We are pleased to announce Ranger Pro, an available extension of Singularity Ranger®, which uses configurable job automation to conveniently and efficiently close agent deployment gaps. This exciting new option reduces stress and raises the productivity of an already overburdened Security team by offloading the ongoing and repetitive task of EPP/EDR agent installation. With peer-to-peer agent deployment, Ranger Pro finds and closes any agent deployment gaps, ensuring that no endpoint is left unsecured.

What Is An Agent Deployment Gap?
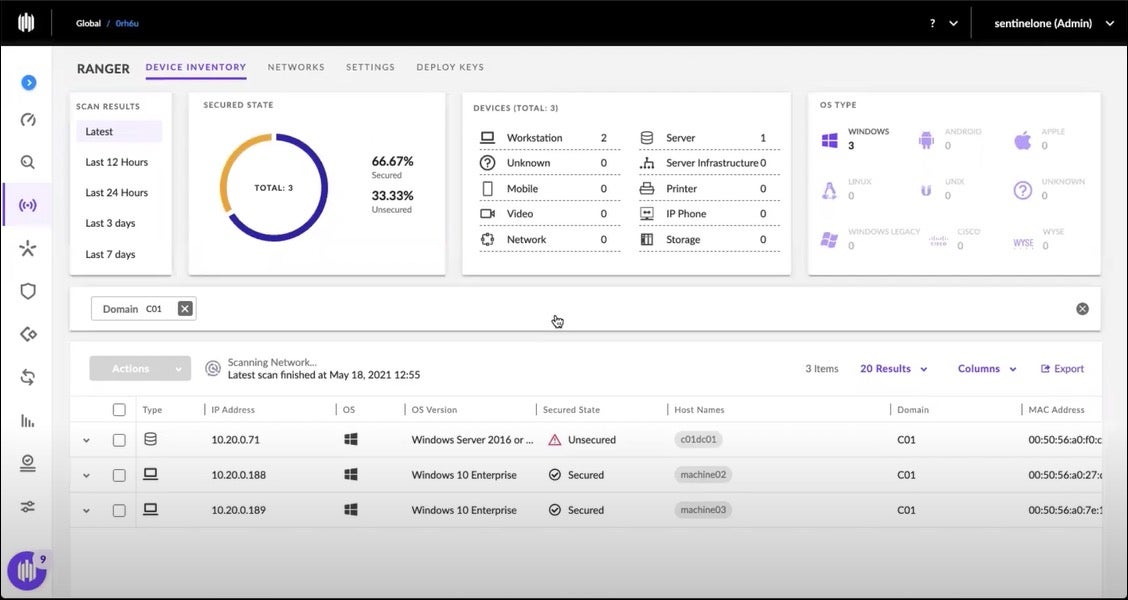
As SentinelOne customers already know, Singularity Ranger® is about proactive attack surface management. The first challenge that Ranger solves is visibility, showing you what is on your network.
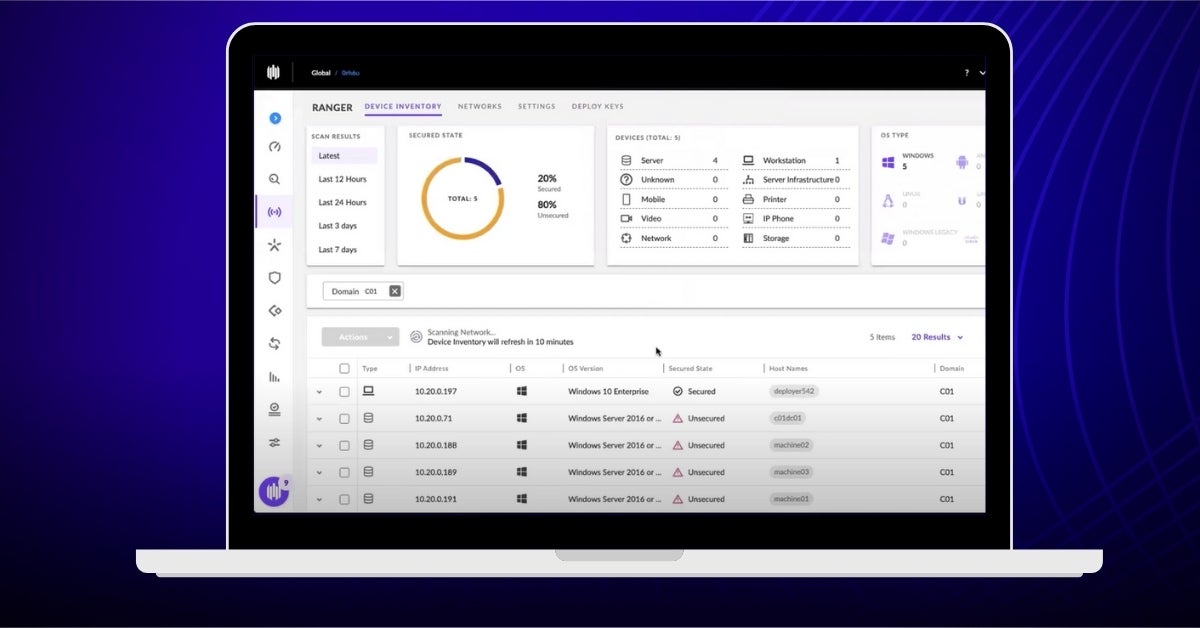
Ranger uses a proprietary ML device fingerprinting engine (FPE) to find any IP-enabled device connected to your network without any additional agents, hardware, or network changes. Ranger creates a device inventory in moments, organized by device function and by security state: Secured, Unsecured, Unsupported, and Unknown.
- Secured: These are endpoints that already have a Sentinel agent.
- Unsecured: These devices can support an agent, but do not yet have one.
- Unsupported: These devices, whether by hardware or software limitations, cannot support a Sentinel agent. Examples include OT (operational technology) devices, such as manufacturing process sensors.
- Unknown: These are devices that the FPE could not yet categorize. The fingerprinting engine gets ‘smarter’ the longer it observes device communication traffic.
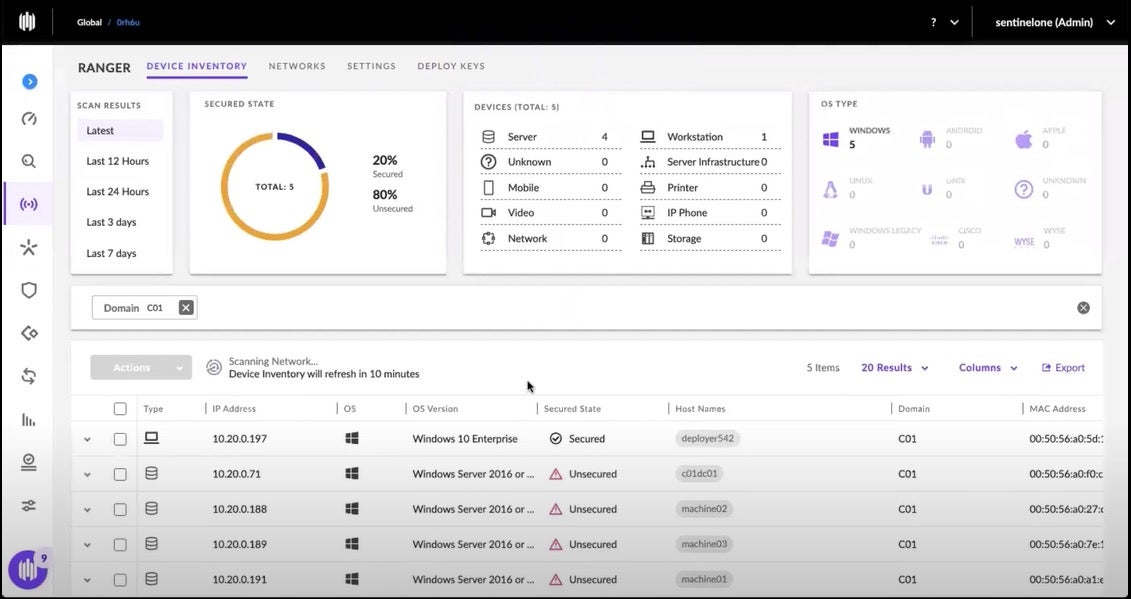
It is the so-called unsecured endpoints that are of particular interest to Ranger Pro. Any such device represents a gap in your agent deployment and a potential attack surface to be exploited. The security gap needs to be closed before malware or ransomware can exploit it.
How Do These Gaps Happen?
We often hear the question, “How do these gaps happen?” There are a number of possibilities. First, you may not have completed your initial agent rollout, but thought you did. Limited visibility is a real challenge facing IT security, and our solution tackles that challenge head-on. As previously mentioned, Ranger will spotlight any unsecured devices. In this way, it helps Security confidently answer the question, “Have I completed my agent rollout?” And if that answer is no, you will know exactly where to look. (And please, hold that thought for two paragraphs more…)
Another likely scenario is a hardware replacement cycle: new user endpoints or servers were purchased and put into service by IT, perhaps without a Sentinel agent installed to protect against known and unknown threats. Similarly, new employees are onboarded, often with new laptops or desktops which need autonomous cybersecurity protection, detection, and response.
In all of these cases, Ranger would show when an endpoint needs a Sentinel agent. Security teams can configure the solution to alert anytime such an unsecured endpoint is found.
Why Did We Create Ranger Pro?
After finding the coverage gap, the inevitable next step facing the security team is closing the gap. Security administrators can indeed choose to do so manually via the SentinelOne Management Console, but such repetitive tasks are begging to be automated.
No one suggests that installing an agent is not a necessary cause worthy of Security’s attention, only that such a task comes at the opportunity cost of a SOC analyst’s valuable time. Security teams are often stretched way too thin and need sensible automation to help them do their job more effectively.
Moreover, how long would the endpoint remain in the wild without a Sentinel agent keeping watch? After all, SOC analysts are on the front lines of a high-stakes battle for the security of the organization against all threats. Much like nurses and physicians in a hospital emergency room, security staff are often forced to triage events, giving their time and focus to the most pressing matters of the day. SentinelOne created Ranger Pro to solve this pain.
An available add-on, Ranger Pro includes all of the Ranger capabilities available for your chosen functionality level – Singularity Core, Control, or Complete – with the added convenience and repeatability of automated deployment. Inevitably, the next question is, “How does it work?”
How Does Ranger Pro Work?
The following sequence walks you through the process.
First, by using the networked device inventory capability, an administrator notices a few unsecured endpoints. In this example site, there are five endpoints, four of which are unsecured. The admin selects 2 of those 4 endpoints – she could have just as easily selected all 4, but perhaps this is her first experience with Ranger Pro’s automated agent deployment and so wants to test it on a subset.
Under the Actions pull-down, she selects Deploy Agent.
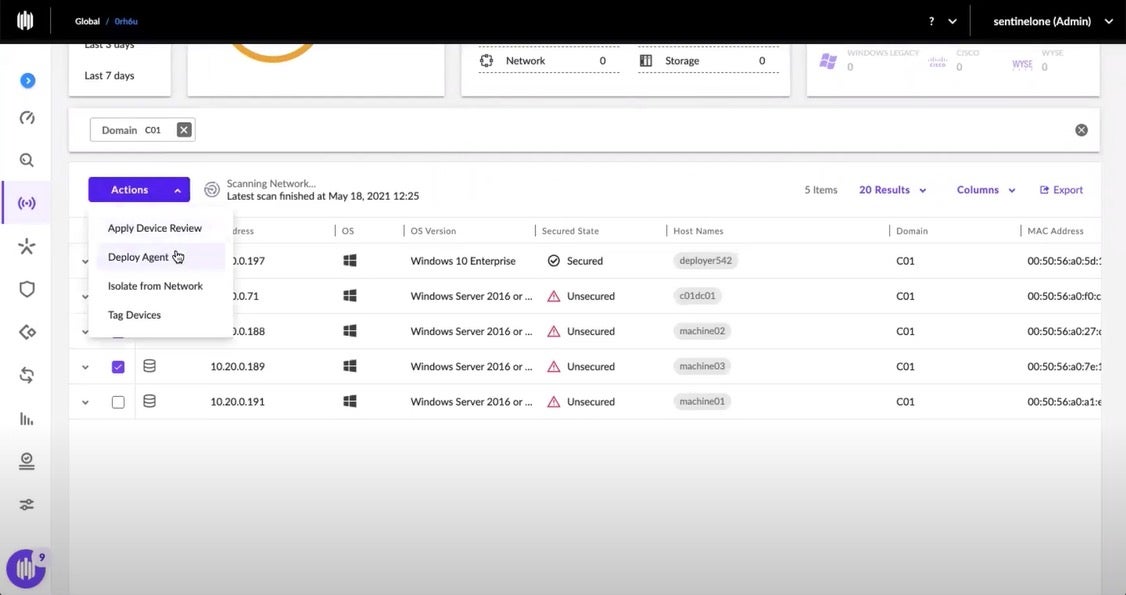
The Auto Deploy pop-up window is opened, and the administrator selects the appropriate Agent deployment package.
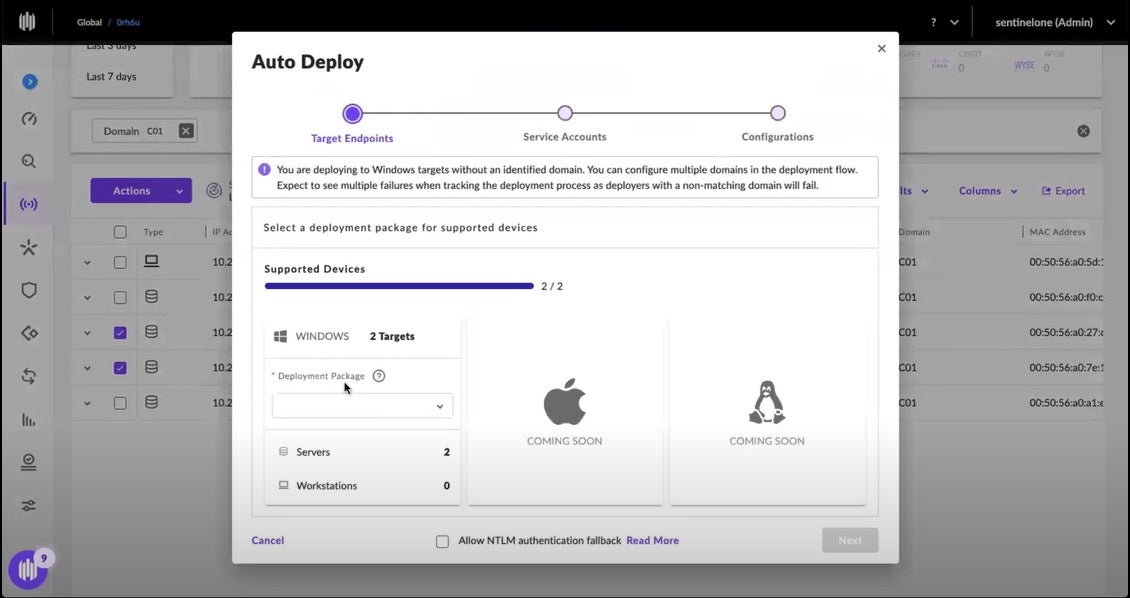
Once the package is chosen, the administrator enters the master passphrase credentials for her secure credential vault. SentinelOne does not have access to the credentials.
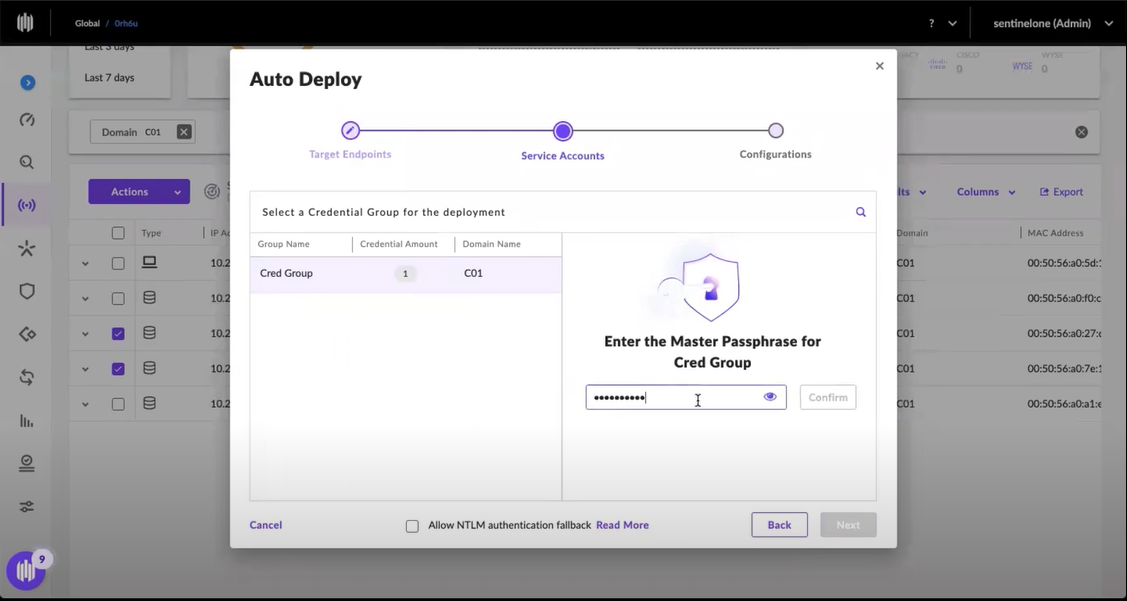
Then the admin selects the appropriate site to assign the endpoints.
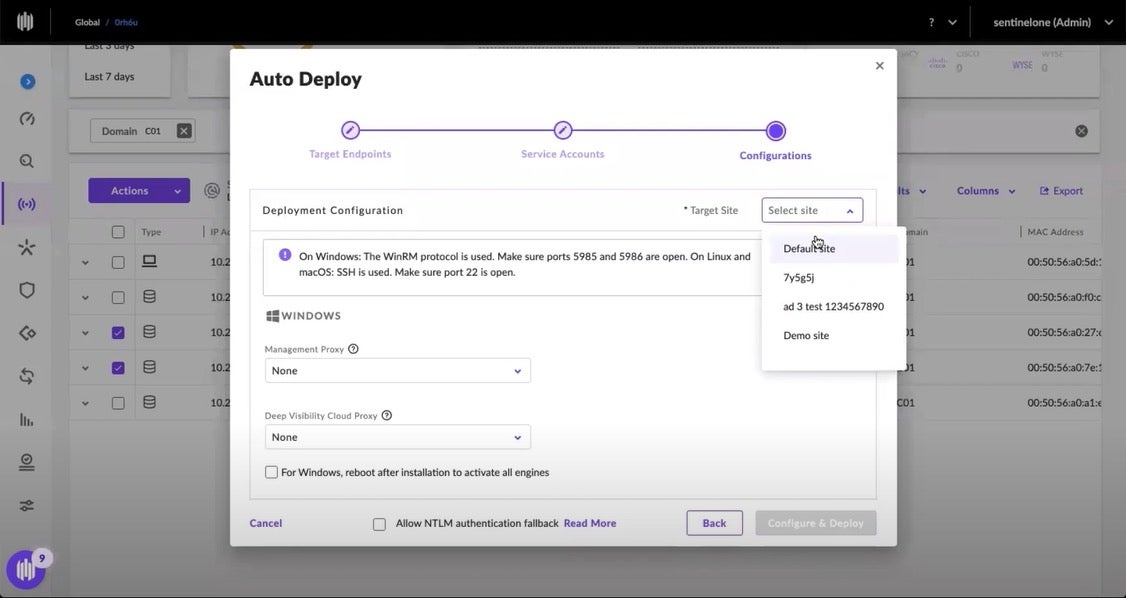
And then Ranger Pro is off to the races, handling the details of Agent installation.
Switching to the Task Management context, the administrator can check the job status as it moves from “Pending” to “In Progress” to “Completed.”
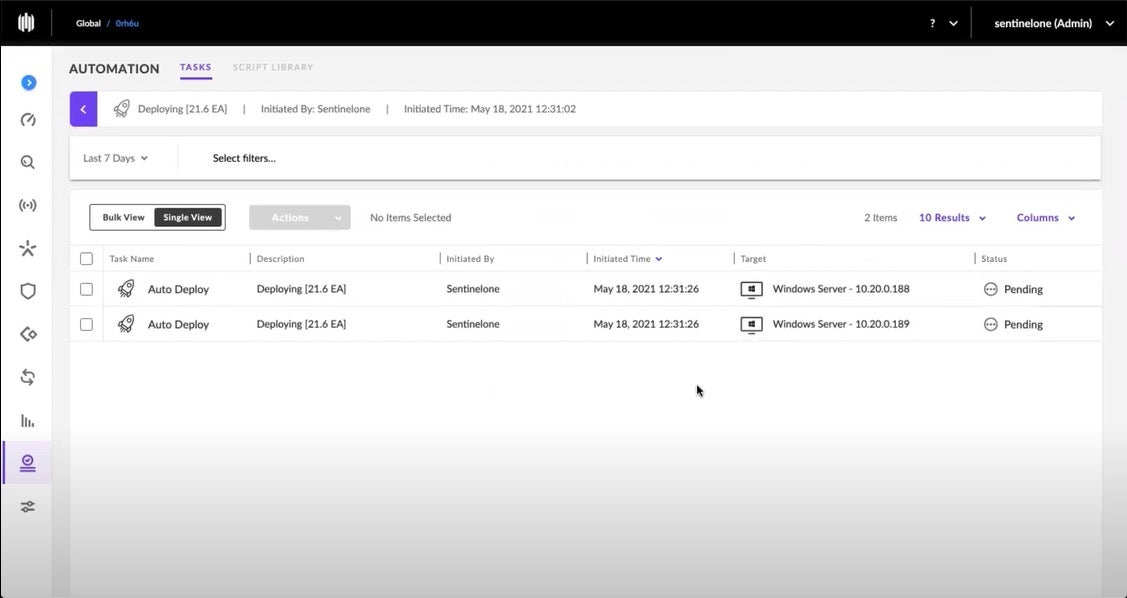
Ranger Pro examines nearby secured endpoints and selects the one which can most efficiently install the Agent via the peer-to-peer deployment mechanism. Here the first Agent installation is completed.
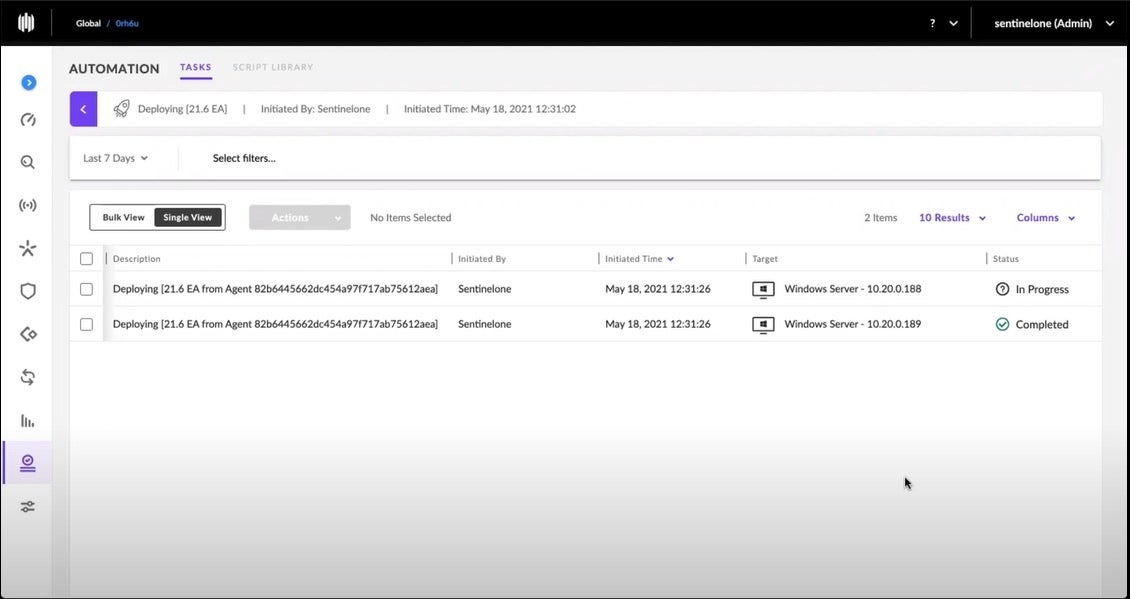
Once Ranger Pro completes the installation and the next device inventory scan is done, the updated inventory reflects the newly secured endpoints. In this example, we installed an agent on two endpoints. In practice, a security administrator is just as likely to have configured the agent installation for all unsecured endpoints on this site. Or, perhaps this was the first attempt using Ranger Pro and the admin just wanted to explore the process on a subset of endpoints.
Once the admin is comfortable and confident with the auto-deploy capability, she can easily tackle the remaining endpoints’ agent installation with a few simple clicks.
Summary
Ranger Pro provides a convenient means of quickly and reliably installing a SentinelOne endpoint security agent on unsecured endpoints. The best part? Ranger does not need extra agents to manage your network attack surface; its AI is woven into the Sentinel agent itself. Using peer-to-peer agent deployment, Ranger Pro conveniently finds and closes any agent deployment gaps, providing security administrators with yet another way of proactively reducing their attack surface.
To explore Ranger and Ranger Pro, visit our solution page, read the datasheet, and when you are ready, contact us to discuss how SentinelOne can help your team do more.