Microsoft released a Windows security update in May 2022, disclosing CVE-2022-26923 Active Directory Domain Services Elevation of privilege vulnerability. The CVE-2022-26923 allows a lower privileged user to acquire a certificate from Active Directory Certificate Services (AD CS) and escalate privileges to the domain controller. However, issues with the update may have prevented some organizations from updating at the time, while others may have been unable to update due to local dependency or compatibility reasons.
In this post, we discuss AD CS misconfigurations that allow attackers to exploit this flaw and describe how security teams can mitigate this vulnerability.

What Is CVE-2022-26923?
According to Microsoft’s advisory, CVE-2022-26923 is one of three CVEs relating to an elevation of privilege vulnerability that can occur when the Kerberos Distribution Center (KDC) services a certificate-based authentication request. On unpatched systems, certificate-based authentication fails to account for a dollar sign ($) at the end of a machine name, allowing related certificates to be spoofed in various ways.
What Is AD CS and Why Is It Important?
Before we dig deeper into the exposure, we will revise what Active Directory Certificate Services (AD CS) is and what it offers.
AD CS is an identity technology in Windows Server that offers Public Key Infrastructure (PKI) functionality to facilitate capabilities such as Encrypting File System (EFS), domain authentication, digital signatures, and email security. AD CS is the Server Role that allows an organization to build Public Key Infrastructure (PKI) and provide public key cryptography, digital certificates, and digital signature capabilities.
While organizations plan to implement PKI by deploying AD CS in an Active Directory environment, they must manage configurations properly for issuing and revoking certificates, including ensuring that appropriate certificate trusts are in place.
Windows Server administrators are responsible for designing the certification authority hierarchy, implementing it, and managing the process of issuing and revoking certificates. It is essential to ensure that appropriate certificate trusts are in place. Any misconfigurations in AD CS role services can expose them to cyber attacks such as privilege escalation, Golden Ticket Attacks, and AD Domain dominance.
How Do Attackers Abuse AD CS and Exploit CVE-2022-26923?
Several security risks exist with AD CS misconfigurations. Let us discuss a couple of them. After running the command certsrv.msc, right-click on the Certification Authority (CA) object, select Properties and navigate to the Security tab.
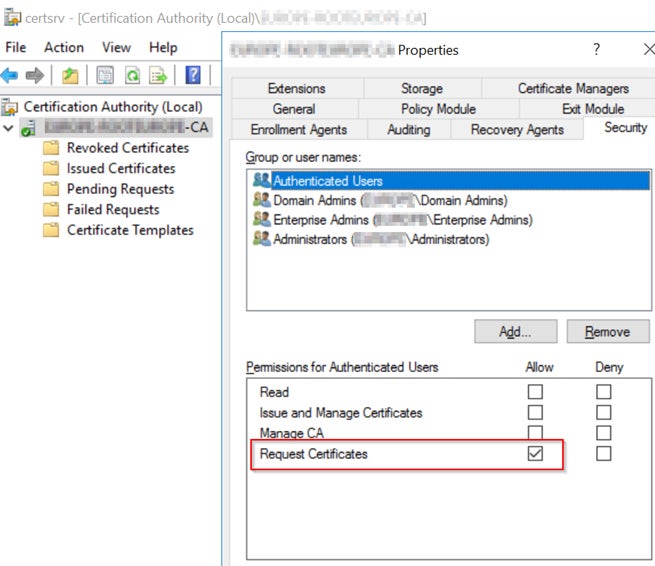
Note that the “Request Certificates” permission is enabled by default. This setting will allow an authenticated user to request certificates from the AD CS server. As with the CVE-2022-26923, an authenticated user could manipulate attributes on computer accounts they own or manage and acquire a certificate from AD CS that would allow elevation of privilege to Domain Controller.
Another vulnerable misconfiguration exists with enrollment permissions of certificate templates. In Windows environments, certificate templates are stored as objects in the Active Directory and used by Microsoft enterprise CAs. A certificate template defines the content and purpose of a digital certificate, including issuing certificate policies and enrollment permissions. Enrollment permissions define the rules by which a certification authority (CA) will issue or deny certificate requests.
A standard User Certificate template may grant the Domain Users group with “Enroll“ permissions, as shown below.
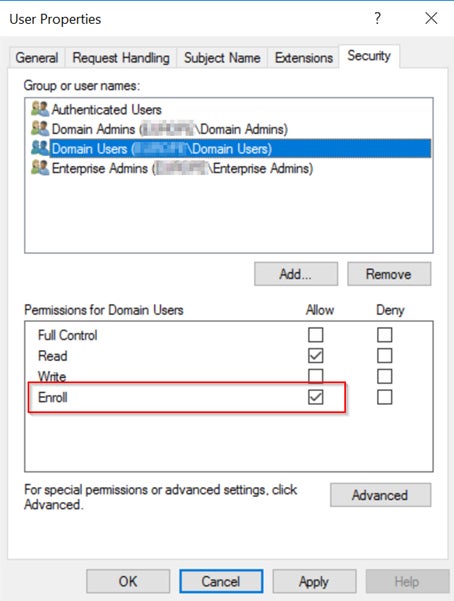
Also, there are Enroll and Autoenroll permissions that are specific to certificate template objects, for example, the Workstation Authentication certificate template, as shown in the next image.
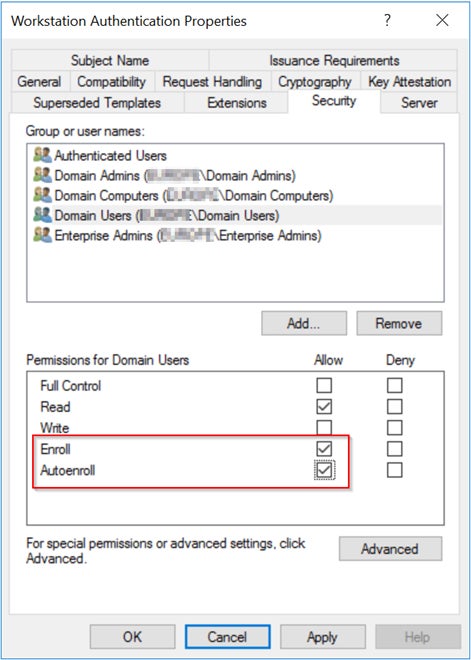
An attacker can abuse these permissions on objects. If an attacker gains access to any template, it can be reconfigured to issue certificates and compromise the entire domain.
Attackers abuse misconfigurations in AD Certificate Services using various tools such as Certify, Mimikatz, Rubeus, and others, which can lead to elevation of privileges and advanced identity-based attacks.
Detection and Mitigation Factors for CVE-2022-26923
Singularity™ Ranger® AD continuously monitors risks associated with misconfigurations, weak policies, credential harvesting, and privilege escalations at the domain, user, and device levels. The solution prevents attacks that attempt to exploit CVE-2022-26923 by detecting and remediating Active Directory Certificate Services exposures. As a mitigation strategy, the following best practices outline how to protect AD CS services from the exploitation of CVE-2022-26923.
Exposure #1: Dangerous Access Rights That Expose Certificate Templates
Misconfigured permissions on certificate templates can allow an attacker to modify or request a certificate, and an attacker could use the certificate to elevate privileges.
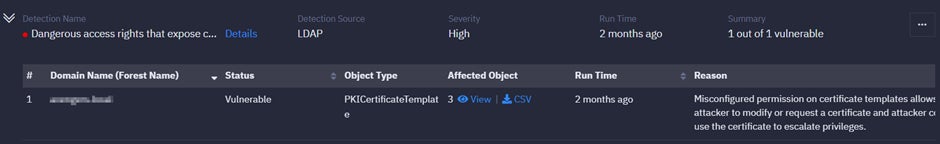
To mitigate this:
- Open the Certificate Authority Manager MMC from “Administrative Tools” or run the command “certsrv.msc”.
- Expand the Certificate Authority.
- Right Click “Certificate Templates” and Click “Manage”.
- Select the Certificate Template listed in the Exposure.
- Right Click on the Certificate Template and select “Properties”.
- Select the “Security” tab.
- Verify and remove the permissions listed in the exposure by Singularity™ Ranger® AD.
- Click “Apply” and “Ok”.
- Repeat the steps from 4 to 8 until all the templates are corrected.
- Delete the template from the “Certificate Templates” Container and Re-Publish the certificate to Issue.
- To publish the Certificate, right-click “Certificate Templates” and Click “New”.
- Click “Certificate Template to Issue”.
- Select all the required Certificate Templates and Click “Ok”.
- Re-Run the assessment to check exposure is remediated.
Exposure #2: Dangerous Access Rights Delegation on Critical Objects
Attackers can compromise user accounts with access rights on critical AD objects and take complete AD domain compromise.
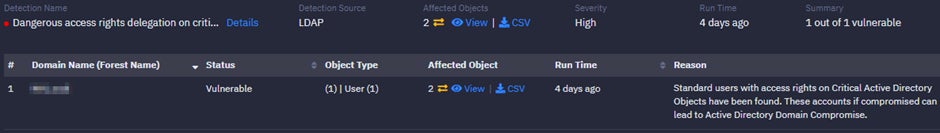
To mitigate this:
- Remove all standard & non-privileged users from the Critical Objects listed in the detection.
- View the assigned permissions on an Organizational Unit (OU) in the graphical user interface. You can also use the Active Directory Users and Computers console with Advanced Features enabled in the View menu.
- After enabling, right-click on OU (for example, OU=NewYork) and select Properties.
- Select the Security tab, then click the “Advanced” button. You can see ACE lists in the Permissions tab (alternate name – “Discretionary Access Control List – DACL”).
- Select the ACE you want to remove and click “Remove”.
Exposure #3: Regular users can add new computers into AD domain
Attackers can also compromise endpoints and attempt to add new computers to the Active Directory Domain without Administrative access.
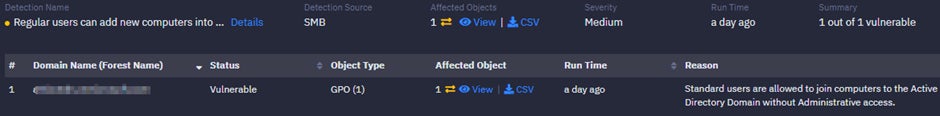
To mitigate this:
- Open Group Policy Management Console ( Start -> Run -> gpmc.msc).
- Locate Domain Controllers OU and find Default Domain Controllers Policy.
- Edit Default Domain Controllers Policy.
- Expand Computer Configuration-> Policies -> Windows Settings -> Security Settings -> Local Policies -> User Rights Assignment.
- From the right pane, right-click on Add workstations to domain ->Properties ->Remove Authenticated Users and Add the User or Group that you are delegating domain joining permissions.
- Click Apply and then OK to close the Properties window.
Other services offered by AD CS such as “Certificate Authority Web Enrollment” and “Certificate Enrollment Web Service” are also potentially vulnerable. Attackers can exploit these settings to perform a classic NTLM Relay Attack called PetitPotam. It allows an attacker to take over Windows domain controllers or other Windows servers.
Patching CVE-2022-26923
As CVE-2022-26923 carries the highest Common Vulnerability Scoring System (CVSSv3) base score of 8.8, it is highly recommended that organizations prioritize the deployment of a patch for CVE-2022-26923 to reduce the possibility of an attacker exploiting this vulnerability.
If certificate-based authentication relies on a weak mapping that cannot be moved from the environment, admins can place domain controllers in Disabled mode using a registry key setting. According to the Microsoft’s documentation, KB5014754—Certificate-based authentication changes on Windows domain controllers, Enablement Phase starts with the February 14, 2023 updates for Windows, which will ignore the Disabled mode registry key setting.
Conclusion
It is of paramount importance that administrators implement all mitigation factors to protect their AD CS servers from such attacks. Organizations deploying Singularity Ranger® AD can remediate the AD CS exposures discussed that will no longer allow attackers to exploit CVE-2022-26923. In addition, Singularity Ranger® AD offers other differentiating exposures that indicate possible malicious activity targeting Active Directory Domain Services and Active Directory Certificate Services.
For more information, please visit Singularity Ranger AD.


