FireEye recently published a report about a cyber attack that resulted in attackers stealing their Red Team tools. FireEye has also released countermeasures (IOCs, YARA rules) to detect the use of these stolen tools against organizations. https://github.com/fireeye/red_team_tool_countermeasures
Initial analysis of the above countermeasures reveals Red Team techniques to assess an organization’s security.
The below lists a few of the techniques used:
- Active Directory reconnaissance and exploitation
- Credential dumping and stealing, etc.
- SMB, WMI enumeration
- MITM LLMNR/NBNS/mDNS/DNS/DHCPv6 man-in-the-middle attacks
- Exploiting known vulnerabilities across internal and public-facing systems
- Security evasions techniques
- Kerberos abuse, Kerberoasting exploitation
- Process injection
Although FireEye has not released what the tools do, our research team has analyzed and found many variants of open source tools used for Red Team assessment.
The below lists Open Sources tools that are part of the FireEye Red Team toolset:
- SharpHound (https://github.com/BloodHoundAD/SharpHound)
- PuppyHound (Modified Version of Sharphound)
- Seatbelt (https://github.com/GhostPack/Seatbelt)
- SharpSploit (https://github.com/cobbr/SharpSploit)
- ADPassHunt (Powershell scripts to extract passwords)
- SharpZeroLogon (https://github.com/nccgroup/nccfsas/tree/main/Tools/SharpZeroLogon)
- Collection of Impacket tools (https://github.com/SecureAuthCorp/impacket)
- SafetyKatz (https://github.com/GhostPack/SafetyKatz)
- InveighZero (https://github.com/Kevin-Robertson/InveighZero)
- Rubeus (https://github.com/GhostPack/Rubeus)
- AndrewSpecial (https://github.com/hoangprod/AndrewSpecial)
- KeeFarce (https://github.com/denandz/KeeFarce)
- G2JS (https://github.com/med0x2e/GadgetToJScript)
The Attivo ThreatDefend® platform can detect attackers inside the network by providing early visibility into the attacker’s lateral movement without the need for deploying any signatures, YARA rules, or IOCs, including detecting activity from the tools listed above.
The following is a list of recommendations for preventing and detecting the use of stolen tools and exploits using the ThreatDefend® platform.
Active Directory Reconnaissance and Exploitation
SharpHound:
SharpHound is the data collector for BloodHound. SharpHound uses native Windows API functions and LDAP functions to collect data from domain controllers and domain-joined Windows systems. Attackers use SharpHound to discover:
- Security group memberships
- Domain trusts
- Discover computers, groups, and user objects in AD
- Members of the local administrators, remote desktop, privilege groups, etc.
PuppyHound
PuppyHound appears to be a modified version of the open-source tool SharpHound and provides the same functionality.
ADPassHunt
This tool hunts for AD credentials via execute-assembly that looks for passwords in GPP, Autoruns, and AD objects. This activity is associated with the MITRE ATT&CK® Tactic for Credential Access, with specific Techniques T1003.003 and T1552.006
SharpZeroLogon
This tool exploits CVE-2020-1472, a.k.a. Zerologon – a cryptographic vulnerability in Netlogon – to achieve authentication bypass. Ultimately, this allows for an attacker to reset the machine account of a target Domain Controller, leading to Domain Admin compromise.
Customers can deploy the Attivo EDN® suite’s ADSecure and ThreatPath® components to discover and protect from attackers enumerating and discovering privileges in Active Directory using tools such as those listed above.
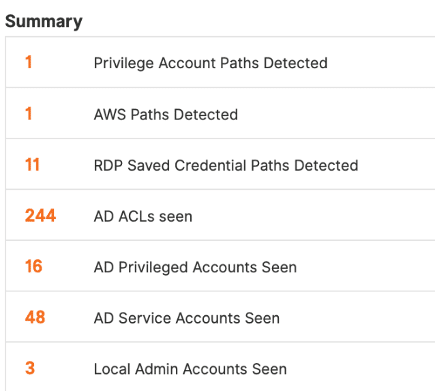
The ThreatPath® component will continuously learn from Active Directory and discover privilege accounts, service accounts, and AD ACL accounts, which are AD accounts with elevated privileges that attackers can target.
- Deploy the AD Secure® component to protect against attackers discovering permissions for these critical accounts in Active Directory.
- Deploy deceptive credentials and policies in GPO for attackers to target.
- Enable SIEM integration to discover usage of deceptive credentials on production systems
Please see the blog “Protection against targeted Active Directory Ransomware” for further reference.
MITM
InveighZero is a C# LLMNR/NBNS/mDNS/DNS/DHCPv6 spoofer and man-in-the-middle tool designed to steal credentials. The protocols broadcast traffic at the network subnet level and hard to detect by traditional security solutions.
ThreatDefend platform users can implement the following best practices:
- Enable MITM policies
- Turn on manual MITM detection
- Configure deceptive domain names to entice attackers to target
Please see the blog “Detecting Man-in-the-Middle Attacks” for further information
SMB, WMI enumeration
Impacket
Impacket is a collection of Python classes for working with network protocols. Attackers can use the Impacketlibrary to perform reconnaissance and exploitation.
WMIRunner, WMISharp, WMISpy
These tools perform WMI enumeration and run WMI commands to move laterally in the network.
WMISpy uses several WMI classes to perform reconnaissance
- MSFT_NetNeighbor
- Win32_NetworkLoginProfile
- Win32_IP4RouteTable
- Win32_DCOMApplication
- Win32_SystemDriver
- Win32_Share
- Win32_Process
MITRE ATT&CK categorizes these under Technique T1135, Network Share Discovery Win32_Share WMI class, and Technique T1057, Process Discovery Win32_Process WMI class, which are popular methods used by many malware.
Customers can implement the following ThreatDefend platform best practices:
- Deploy deceptive mapped shares on endpoints to lure attackers into targeting deceptive shares
- Enable the EDN data cloak function, which prevents attacks from discovering production network shares
- Deploy BOTsink® Windows decoys and ThreatDirect forwarders to engage attackers performing WMI and SMB enumeration.
- Protect against SMB session enumeration by deploying the EDN ADSecure component
Please see the blog “Lateral Movement Using SMB Session Enumeration” for further information.
Credential Dumping
There are multiple variants of memory and credential dumping tools in the stolen Red Team toolset.
SafetyKatz
SafetyKatz is a slightly modified version of @gentilkiwi’s Mimikatz project to steal credentials.
AndrewSpecial
AndrewSpecial is a tool that dumps LSASS memory and steals credentials.
Rubeus
Rubeus is an open-source C# toolset that performs Kerberos interaction and abuses. Rubeus also performs Kerberoasting attacks and ticket extraction.
Customers can implement the following ThreatDefend platform best practices:
- Deploy deceptive mapped shares, deceptive lures (credentials, browser artifacts, etc., to decoy systems).
- Deploy AD Secure to protect service accounts in AD against Kerberoasting attacks.
Please see the following blogs for more information:
The FireEye news generated a great deal of discussion and concern in information security circles. Attivo customers should implement the listed best practices to defend against these and other tools with similar functions.


