It’s not enough to see the malware that’s coming for you—you have to be able to stop it. For Next Generation Endpoint Security solutions, that statement is doubly true. As stated in one of our previous blogs on the subject, SentinelOne relies on a behavioral detection engine in order to detect the activity of viruses that haven’t been seen before in the wild. In order to recognize viral behavior, SentinelOne actually needs to let malware run for a short amount of time—which means it’s highly important that we perform effective mitigation.
The good news is this: SentinelOne can effectively mitigate malware instants after detecting malicious behavior. Here’s the bad news: other endpoint security solutions can allow a gap between detection and response—and this represents a major problem that can allow malware to thrive.
The Gap Between Detection and Mitigation in Endpoint Security

If you’re reading this blog you’re probably at least familiar with Star Trek. You may remember that at least once an episode, the Enterprise (or the Voyager) will encounter some form of crisis and enter a “red alert.” The lights dim, red lights start to flash, and klaxons begin blaring throughout the vessel. It makes for some extremely dramatic television, but in real life it would be nearly impossible to solve problems with those kinds of distractions going on. As it turns out, however, information security professionals go through most of their working lives in “red alert” mode.
A Ponemon Institute survey from 2016 indicates that most IT security practitioners experience nearly seventeen thousand malware alerts per week. That’s clearly an overwhelming number—if security personnel were to spend just one minute investigating each alert they receive per week, they’d be at it for seventy days. Obviously, that figure can be whittled down a bit due to false positives, but out of the remaining 3,218 alerts deemed actionable, only an average of 700 alerts are investigated.
To summarize, there are far too many alerts for IT security to investigate, and by looking only at the ones deemed most severe, they run the risk of passing over low-risk alerts which are actually hiding malware. As a matter of fact, this is exactly what happened during the Target breach.

The Detection Gap Favors Long, Stealthy Malware Infections
Once a malware alert slips through the cracks, there’s actually not much else that standard endpoint protection can do about it. As we’ve emphasized, standard endpoint protection is built on recognizing the characteristics of malware, and not its behavior. That means it might not be able to detect malicious activity once a system is infected. For this reason, the average length of a malware infection is now 98 days, from infection to mitigation.
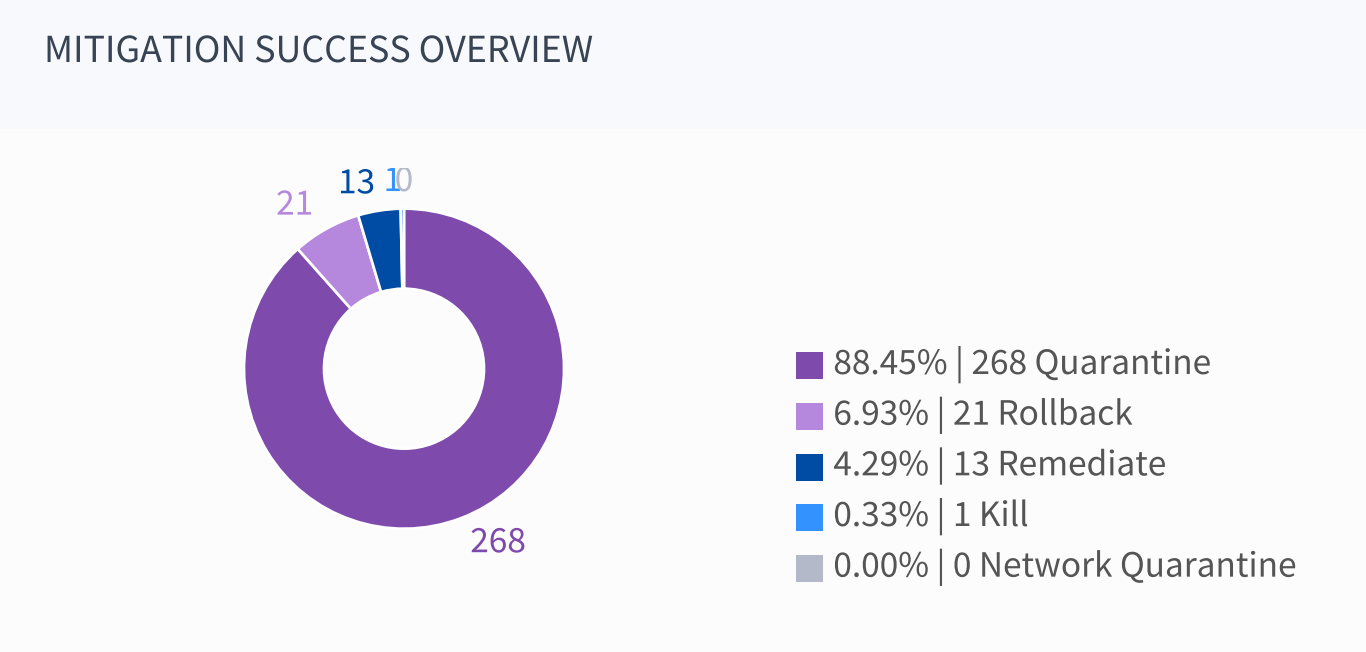
SentinelOne is different. By interrogating all of an endpoint’s running processes, it can detect actions that are likely to be malicious. That means there’s zero detection gap. Additionally, mitigation is automatic—upon sensing malicious actions, SentinelOne will automatically quarantine the machine from the rest of the network, kill the responsible processes, or even shut down the infected endpoint. These actions are based upon pre-set policies that can be set for the entire organization or for individual groups, and can be modified or re-written at the administrator’s whim.
Reinforcing Mitigation with SentinelOne
With SentinelOne, you won’t have to worry about malware going behind your back. Our solution can cut down false positives, so you won’t find yourself drowning in red alerts. In our future blogs, we’ll also talk about remediation and forensics, which can help you roll back damage from malware and get a better picture of what’s going on in your network. If you need more information right away, check out our Next Generation Endpoint Protection Buyer’s Guide.