In this Central Park blog post we will focus on the enhancements made to the Analyze View within the SentinelOne console.
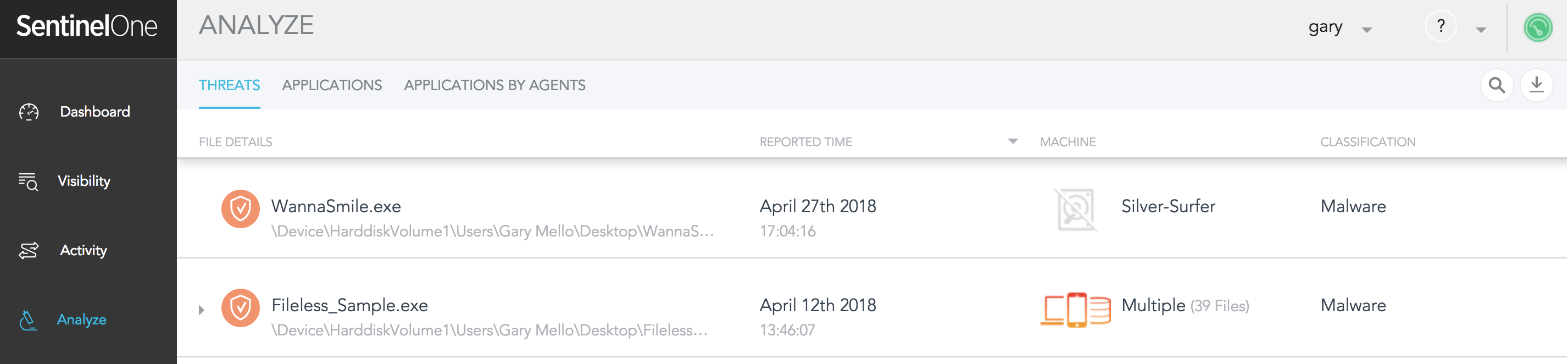
First, please let me provide a bit of background. If you are unfamiliar with the Analyze View in previous versions before Central Park, it was a tab within the Sentinelone console that provided the following functionality:
- Threats – A historical reference of all threats found within the environment
- Applications – A listing of all applications discovered within the environment
- Applications by Agents- A listing of applications discovered for a given endpoint
Below is a screenshot showing these details:
So why the need for improvement? Although previous versions had captured all threat related data, the problem was that is was not easy to search through this data. With Central Park we have fixed that! We still capture all of the threat data that you need, but we have the ability to apply an array of filters to search through the data. The filters include both pre-built criteria and also free text search. This makes searching much easier and more robust, not to mention that it will also save you time. Below are a few examples of this exciting enhancement:
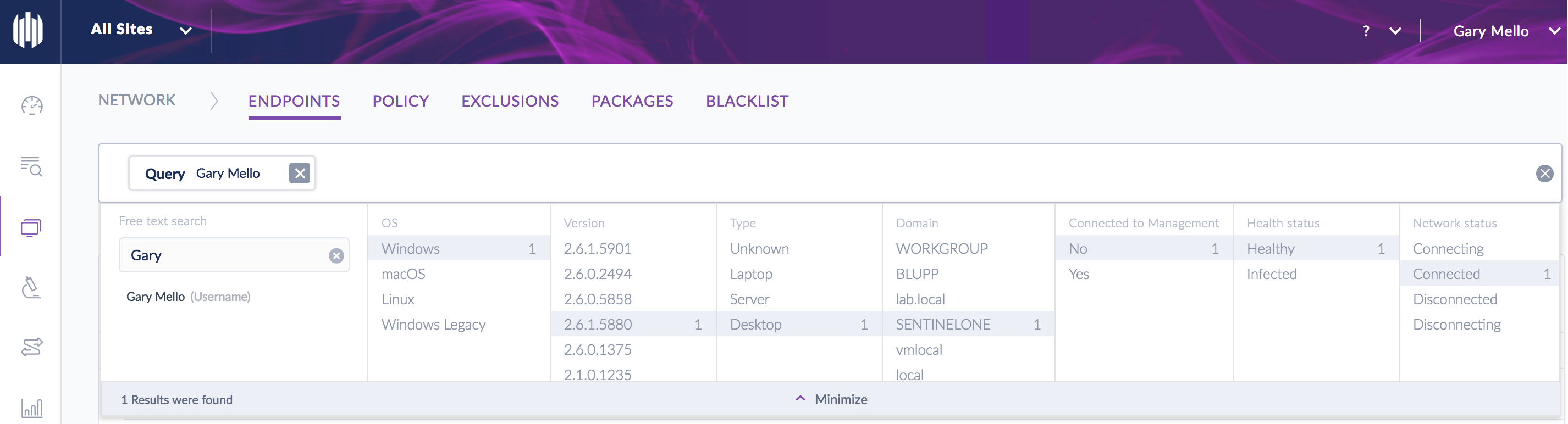
Example 1: Search across all endpoints for a given user login (i.e. which workstations did a user log into). In this example I generated a “Free Text Search” for the user “Gary”. Please keep in mind that Free Text Search can accommodate many other options such as IP Address, Machine Name, MAC Address, Domain, & etc.
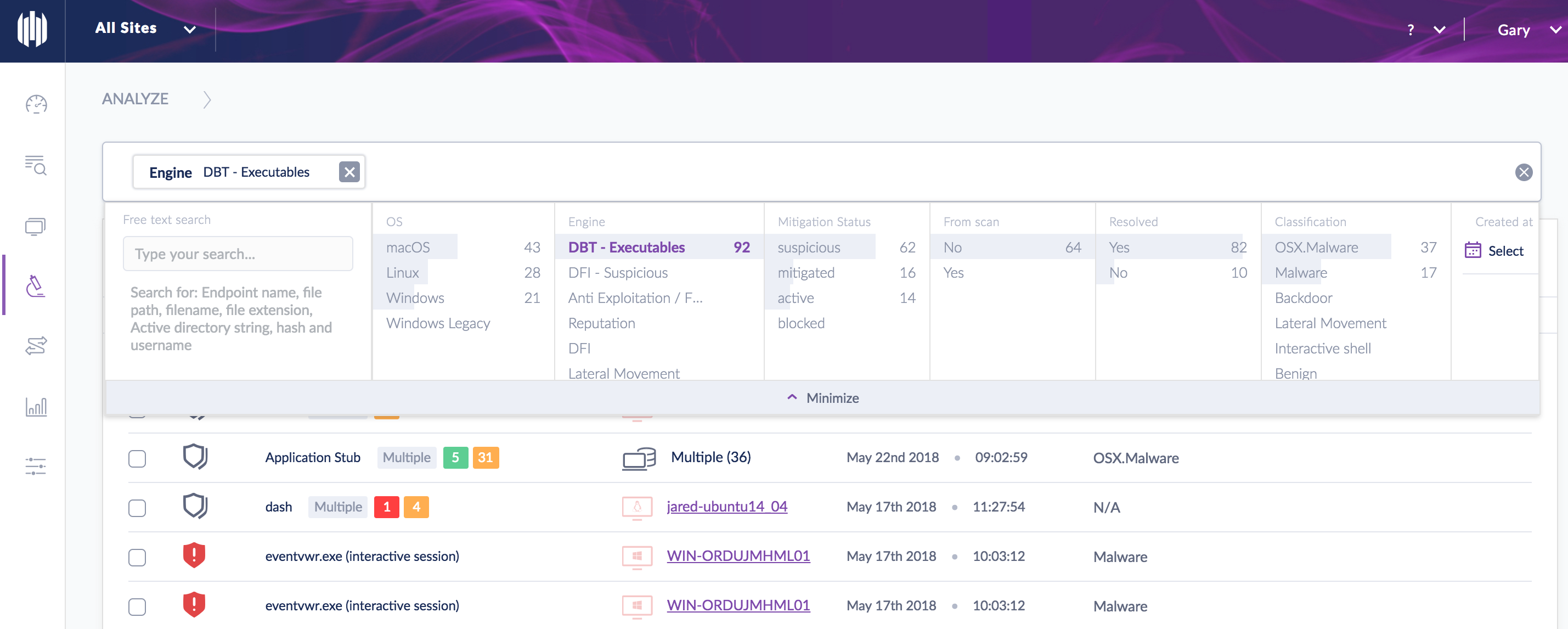
Example 2: Search for all threats that were convicted by a specific engine. In this example I am conducting a search that will show all threats that were convicted via our Behavioral-AI engine (DBT-Executables)
Example 3: Search for all threats that were classified as “Exploit”. Please keep in mind that there are over 25 different classifications we are now assigning to threats
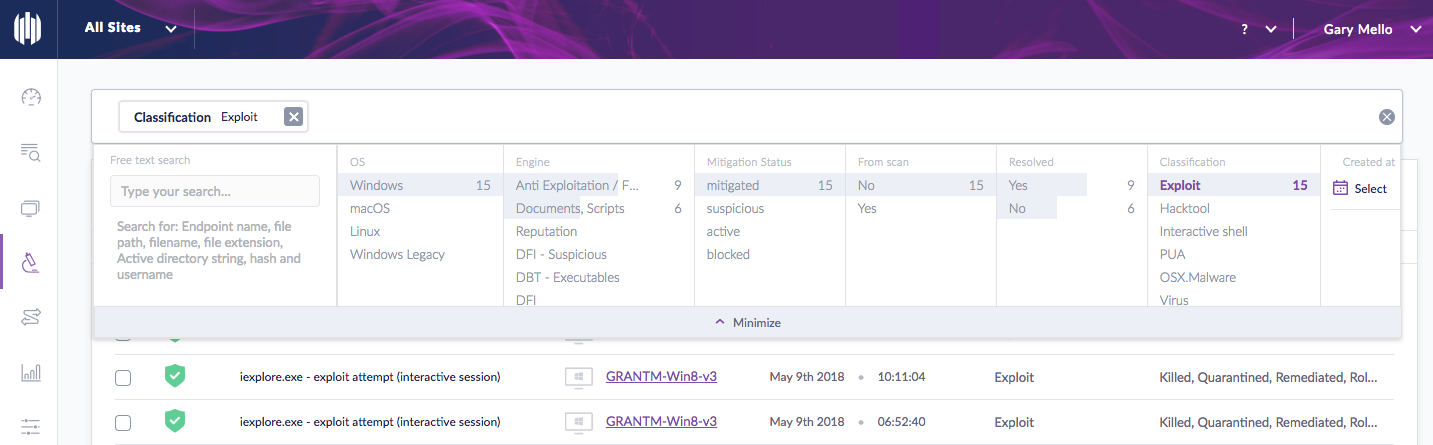
On top of making our search abilities much more robust, we have taken things a step further and made our searches actionable. In other words, once you have generated a search you can do something with the results directly from within the search interface.
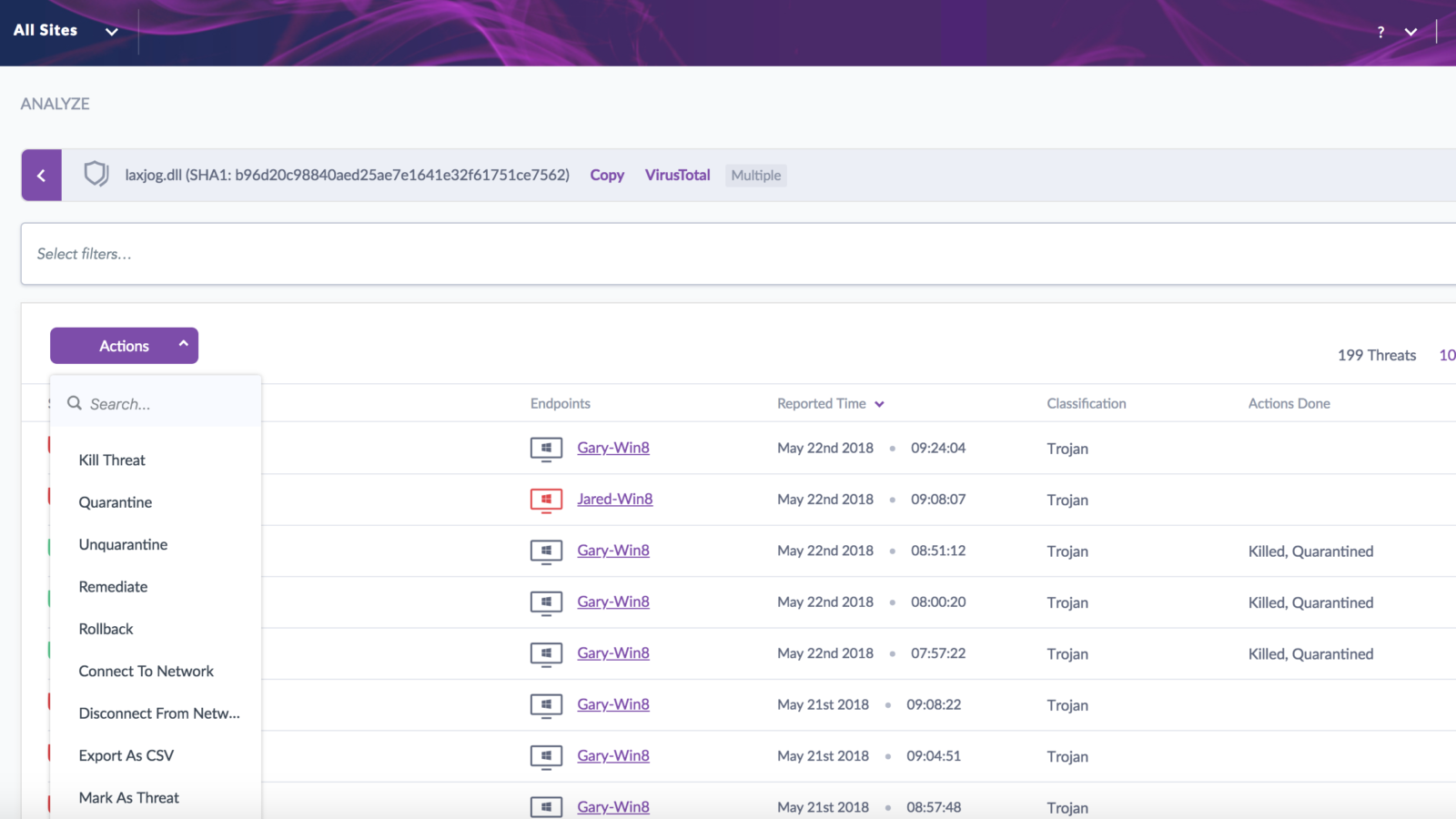
Here is an example of a search for a given threat and the actions available. In this case you could take a bulk action for a given threat such as Disconnect from Network, Remediation (Kill, Quarantine, Rollback), Mark as Resolved, etc. Additionally with Central Park, similar threats have now been consolidated into a single view. This is also reflected in the example below.
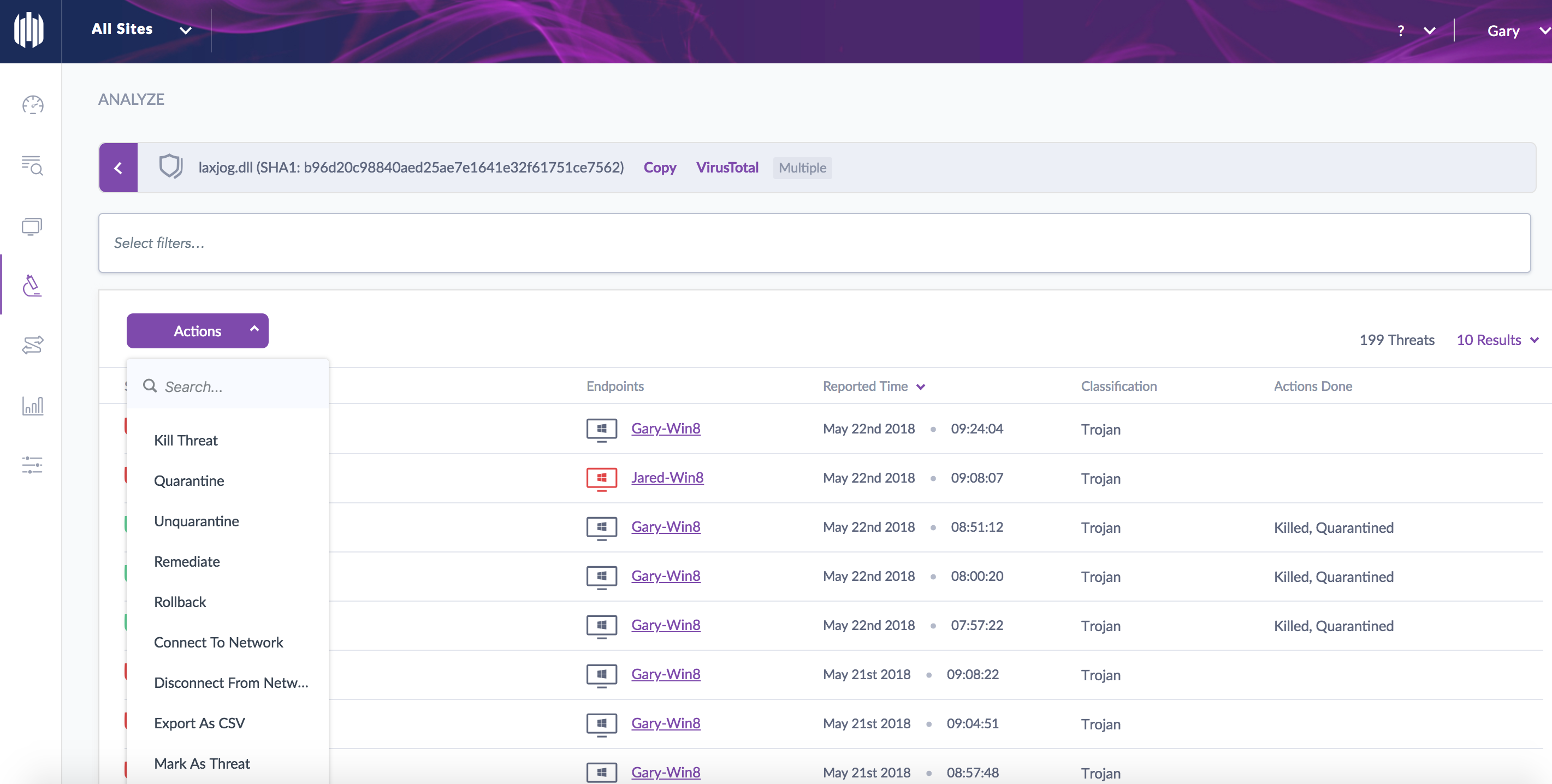
In summary, this enhancement not only makes searching much more robust, but taking action is much more simplified. All of which will save you time!
In our next Central Park blog we will focus on our enhanced reporting capabilities.