Our teams have been busy lately, increasing our release frequency and providing value to our customers with another release. This time, our focus was on making the deployment flow smooth, by supporting Windows Agent installation without an immediate reboot. Let’s go over the most significant changes.
Smooth deployment
SentinelOne is growing rapidly, and so our customer base. We see more and more large customers who want to replace their existing AV solutions, EDR, visibility, and incident response products. In the past, our Windows agent was asking for a reboot on initial installation, but no more (macOS and Linux never needed that). Starting this release, you can just deploy without the need to interrupt your users. You will immediately get Static AI protection, reputation engine, Ransomware prevention features and we will also kick off scan, to ensure no dormant malware is on disk.
For servers who must be always on – no other steps are necessary. For workstations and laptops, once the device reboots, it will get additional features.
More controls on policy
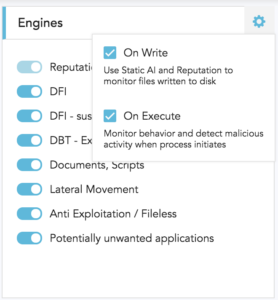 On our last 2.0 release, we exposed our engines on the policy, and our customers loved it. Starting on this release, you can also control more aspects of the policy as “on write” and “on execute”. This came as a request from some of our customers who are running SentinelOne agents on thin devices, ATMs, and Servers with special configuration.
On our last 2.0 release, we exposed our engines on the policy, and our customers loved it. Starting on this release, you can also control more aspects of the policy as “on write” and “on execute”. This came as a request from some of our customers who are running SentinelOne agents on thin devices, ATMs, and Servers with special configuration.
Agent configuration
Agent configuration is now part of the policy, configured easily in the Management Console. We looked at some of the most common needs of our customers and you can now control things like logging options, snapshot creation, automate the scan upon install, agent UI and more, straight from your SentinelOne policy.
More visibility on why we detected a malware
Our Behavioral AI was always rich in details – what was running, what it tried to do, including URLs, child processes and more, but since we introduced our Static AI capabilities, the detections did not carry the full story. Our Static AI prevents malicious files and variants from ever being executed on your devices, so these detections did not carry the full story. Since we know your security analysts’ and incident responders’ time is valuable and they need simplified workflows, we added more intelligence to our Static AI in order to tell you exactly why something was detected. 
Automated Prevention, Detection, and Response
There were many other improvements in this release, to highlight a few:
- Our Lateral Movement engine now introduces extra forensics data like the source IP and the associated user of the attacker.
- New Static AI version
- Additional behaviors including anti-VM detection.
- Backdoor factory: A pre-execution prevention of files that encapsulates malicious capabilities within, evading traditional solutions in a glance.
New device details view
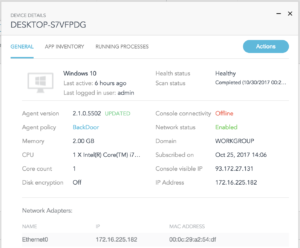
Like every release, we are looking to improve our administrator experience and this time we’ve focused on the device details. Starting this release, you can get all the information on a device, perform more actions and have more visibility on each device.
More improvements
- Performance improvements (cross-platform)
- Added SuSe Linux to our already existing Linux distributions we support
- SSO support for our knowledge base, help and community
- More support and visibility into High Sierra upgrade, which may require some user intervention.
- Added search for users on the network page.
What’s next?
Our team is already working on the next release, planned for later this year. This time we will focus on better reporting, and expand upon our multi-tenancy and RBAC features. These are features some of our major accounts were asking for and it will allow more MSSPs to protect their users and devices using our innovative solution.
Stay tuned!

