The last twelve months have been unprecedented in cybersecurity. Multiple state-sponsored hacktivist groups marched to the forefront of concerns as 2023 saw the Russian invasion of Ukraine continue into its second year and a new cyber battlefront open up due to the kinetic war between Israel and Hamas.
Meanwhile, despite new government initiatives and international cooperation to combat cybercrime, ransomware continues to be a top challenge for enterprises, in an environment where cloud assets represent new targets and LLMs offer both defenders and attackers new tools and new opportunities. Throughout the year, SentinelLabs has been tracking, identifying and disclosing information on these and other issues to help organizations and defenders stay ahead of the threats to their business operations.
All our research and threat intelligence posts can be found on the SentinelLabs home page, but for a quick recap of the year’s main cybersecurity events, take a scroll through the 2023 timeline below.

January
In January, we reported on pro-Russia hacktivist group NoName057(16), describing its attacks on Ukraine and NATO organizations as well as its targeting of the 2023 Czech presidential election. We identified a volunteer-fueled DDoS progam operating over public Telegram channels and described in detail their DDosia malware. We also revealed how the group, previously reported on for tageting both the Polish government and the Danish financial sector, abused GitHub to host its toolkit and offered payments to its most impactful contributors.
In January 2023, we also reported on DragonSpark, a cluster of opportunistic attacks against organizations in East Asia. The threat actors used Golang malware that implemented an uncommon technique to hinder static analysis and evade detection: Golang source code interpretation.
February
SentinelLabs observed the first ELF variant of Clop ransomware and reported on its flawed encryption method, allowing us to develop and publish a decryptor for the malware.
In February, we also exposed a cluster of virtualized .NET malware loaders being distributed through malvertising attacks. Dubbed MalVirt, the loaders were seen distributing the Formbook family of malware and disguising C2 traffic by beaconing to random decoy servers hosted on providers such as Azure and Namecheap.
In other research published this month, SentinelLabs in collaboration with QGroup GmbH identified a new threat cluster tracked as WIP26 engaging in targeted espionage activities against telecommunications businesses. WIP26 also relies heavily on public cloud infrastructure to disguise malicious traffic, abusing Microsoft 365 Mail and Google Firebase services for C2 purposes.
March
Telcos were also the targets of Operation Tainted Love, this time in the Middle East. Believed to be an operation conducted by Chinese cyberespionage actors, we disclosed how the campaign was an evolution of Operation Soft Cell. The initial attack phase involved infiltrating Internet-facing Microsoft Exchange servers to deploy webshells for command execution. Once a foothold had been established, the attackers deployed custom credential theft malware.

Also in March we reported on the evolution of AlienFox, a comprehensive, modular toolset for credentials harvesting against multiple cloud service providers.
April
Transparent Tribe (aka APT36) is a suspected Pakistan-based threat group active since at least 2013. In April, SentinelLabs observed this long-running threat actor expand its interest into the Indian education sector through a cluster of malicious documents staging Crimson RAT. Previously focused on Indian military and government personnel, the threat actor was observed distributing malicious education-themed content hosted on known APT36 infrastructure. The malicious documents stage Crimson RAT using Microsoft Office macros or OLE embedding.

In addition, some Crimson RAT variants were identified using a cracked versions of a commercial tool Eazfuscator to obfuscate code. This represents a change in tactics from earlier versions which relied on the Crypto Obfuscator tool for such functionality.
May
The leak of Babuk source code back in 2021 has led to multiple ransomware variants and contributed to a widely expanded crimeware ecosystem. In May 2023, SentinelLabs revealed how this same source code was behind 10 different ransomware families targeting VMware ESXi, potentially enabling new threat actors who might otherwise lack the technical skills to target Linux systems. Due to the prevalence of ESXi in on-prem and hybrid enterprise networks, these hypervisors are valuable targets for ransomware.

In May, the SentinelLabs team also disclosed Operation Magalenha, a long running campaign by a Brazilian threat actor targeting Portuguese financial institutions for credentials and PII theft.
June
Across May and June, SentinelLabs released reports on DPRK-aligned threat actor Kimsuky. In collaboration with NK News, we disclosed a targeted social engineering campaign against experts in North Korean affairs from the NGO sector. The campaign focused on theft of email credentials, delivery of reconnaissance malware, and theft of NK News subscription credentials.
A hallmark of the activity was establishing initial contact and developing a rapport with their targets prior via impersonation of industry figures before initiating malicious activities, a tactic also seen in DPRK-aligned cybercrime activity aimed at cryptocurrency exchanges.
If the target engages in the conversation, Kimsuky uses the opportunity to deliver a spoofed URL to a Google document, which redirects to a malicious website specifically crafted to capture Google credentials. Kimsuky has also been seen delivering weaponized Office documents that execute the ReconShark malware.
July
Cloud security came to the fore in July through both crimeware and APT intrusions. We reported on a cloud credentials stealing campaign that had expanded from targeting AWS cloud instances to include both Azure and Google Cloud. Primarily seeking out exposed Docker instances, crimeware actors looked to deploy a worm-like propagation module via script-based and UPX-packed Golang-based ELF binaries.

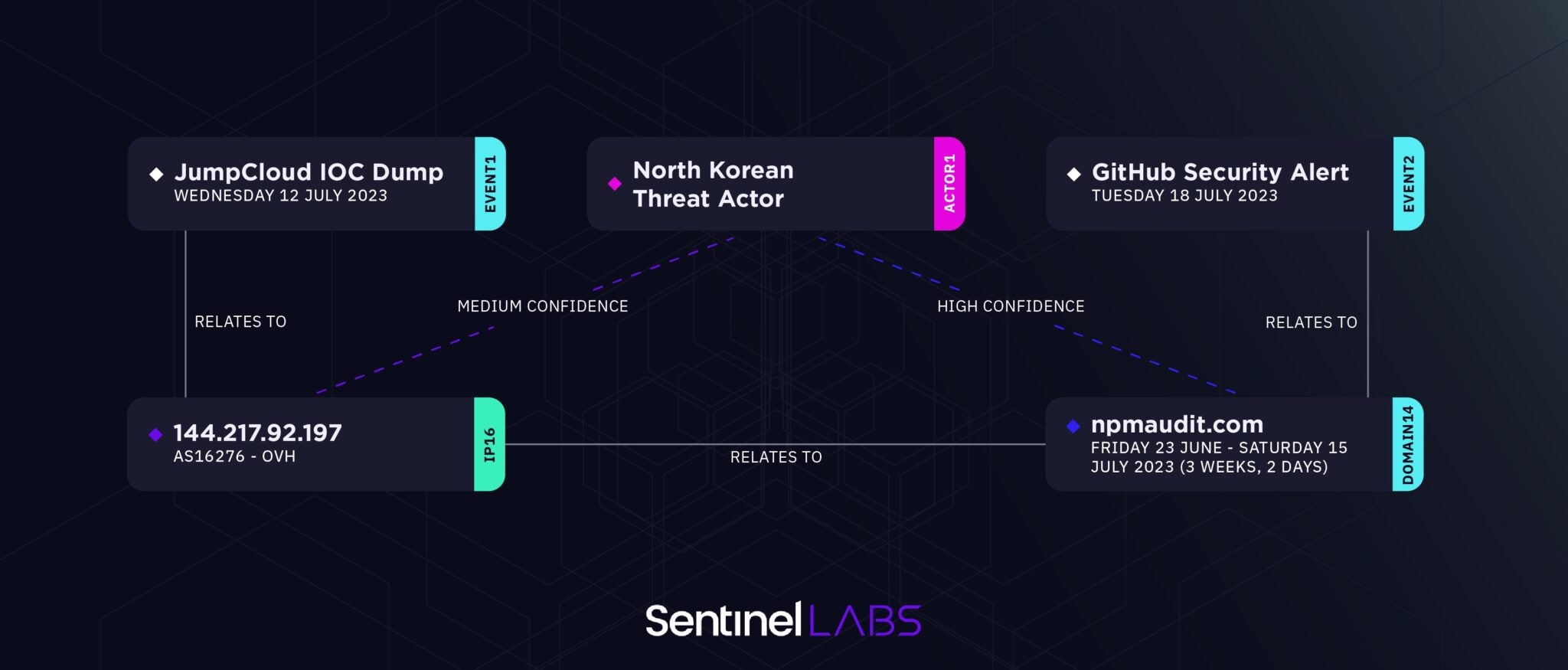
Elsewhere, an intrusion at cloud-based IT management service company JumpCloud turned out to have infrastructure connections DPRK-aligned threat activity, SentinelLabs reported. The intrusion bore links to the earlier 3CX SmoothOperator campaign we reported on in March.
August
North Korean-aligned threat actors were having a busy year throughout 2023, but not all their targets were in the west. In August, we identified intrusions into the Russian missile engineering organization NPO Mashinostroyeniya, a sanctioned entity that possesses highly confidential intellectual property on sensitive missile technology currently in use or under development for the Russian military.
Our investigation uncovered an email trove leaked from the victim organization that revealed two separate sets of activity. We were able to establish a connection between each cluster of activity and reveal that a more significant network intrusion had occurred that the victim organization realized.

Chinese adversaries also came to our attention this month after we identified malware and infrastructure directed at the Southeast Asia gambling sector. We observed indicators that pointed to China-alinged BRONZE STARLIGHT group: a suspected Chinese ‘ransomware’ group whose main goal appears to be espionage rather than financial gain, using ransomware as means for distraction or misattribution. However, exact attribution remains unclear due to the complex interconnections between various Chinese APT groups.
September
Transparent Tribe came to our attention for a second time in 2023 via distribution of its CapraRAT malware in a novel YouTube-like Android application we dubbed CapraTube. We identified three Android application packages mimicking the appearance of YouTube but which also requested spyware-like permissions.
In September, SentinelLabs also hosted its second LABScon event, featuring talks from leaders across the cybersecurity industry. Among the keynotes were Tom Hegel’s presentation on how China uses strategic intrusions in under monitored regions such as Africa to further and to strengthen its regional goals.
SentinelLabs’ Aleksandar Milenkoski, in collaboration with QGroup, reported on yet another adversary targeting telcos. Dubbed Sandman, the previously unreported threat actor has targeted organizations across the Middle East, Western Europe and the South Asian subcontinent with a novel modular backdoor that utilized the LuaJIT platform.

October
The shocking events in Israel in October 2023 and their aftermath may yet come to define much of the headlines to come in 2024, but in terms of cyber activity there is still a lack of clarity as different hacktivist groups pursue various goals in support of one side or another.
Our initial reporting on state-sponsored activity emerging from events on the ground aimed to highlight adversaries-of-interest to the cybersecurity community at large in an effort to better coordinate reporting and help to understand the threat model facing organizations.

November
Continuing on from October’s activity, we reported on Arid Viper‘s SpyC23 malware and the group’s espionage campaign targeting Android devices.
This long-running campaign through 2022 and 2023 involves weaponized apps posing as the Telegram messeging app or a romance-themed messaging app called ‘Skipped Messenger’. Our report highlighted how Arid Viper had developer several newer SpyC23 versions delivered via social engineering. The spyware, once installed, gained a high degree of control over the victim’s device including being able to make calls without user interaction, capture microphone and audio input, and collect sensitive data, including the phone’s contacts list.

Of course, 2023 has also been the breakout year for AI, and threat actors have not been slow to jump on the bandwagon either. In November, we reported on Predator AI, a new Python-based infostealer and hacktool designed to target cloud services. Advertised through Telegram channels related to hacking, the main purpose of Predator is to facilitate web application attacks against various commonly used technologies, including content management systems (CMS) like WordPress, as well as cloud email services like AWS SES.
December
We rounded out the year with two reports on earlier themes. In joint research between SentinelLabs, PwC and MS Threat Intelligence, we published further intelligence on the Sandman APT we reported at September’s LABScon, noting that Sandman and STORM-0866/Red Dev 40 share infrastructure control and management practices. Importantly, we described commonalities between two distinct malware strains: the LuaDream malware and the KEYPLUG backdoor.
In our final report of the year, we turned to activity attributed to Gaza Cybergang, a long-running cluster of Hamas-aligned threat activity known since 2012. Tracking activity spanning from late 2022 until late 2023, we observed that the group introduced a new backdoor to their malware arsenal, Pierogi++, used in targeting primarily Palestinian entities.

These activities are likely aligned with the tensions between the Hamas and Fatah factions, whose reconciliation attempts had been stagnating before and after the outbreak of the Israel–Hamas war. We describe the development of Pierogi++ and highlight overlaps in targeting that suggest the Gaza Cybergang sub-groups have likely been consolidating.
Conclusion
This year as last, SentinelLabs has continued its mission to keep defenders abreast of the latest developments and trends across crimeware, APT and other cyber threat activity. Aside from the research highlighted here, there’s more to be found across our From the Front Lines series of posts and our published and forthcoming videos of talks from LABScon 2023.
You can also meet the SentinelLabs team in our quarterly threat briefings.
We’ll be back in 2024 with more security research and threat intelligence reporting. In the meantine, we wish all a happy, secure and peaceful New Year and 2024.


