The Good | Cybercriminals Face Disruptions Across Ransom, DDoS & Extortion Campaigns
Cameron John Wagenius, a 21-year-old former U.S. Army soldier, has pleaded guilty to attacking and extorting at least ten U.S. telecom and tech companies, including AT&T and Verizon. Operating under aliases like “kiberphant0m” and “’cyb3rph4nt0m”, he used tools like SSH Brute and SIM-swapping techniques to steal credentials and demand ransoms of up to $1 million from the breached firms.

Active on forums such as BreachForums and XSS, Wagenius conspired with other actors between 2023 and 2024, including the Snowflake cyberattacks and even while serving in the military. In one instance, he threatened to leak over 358GB of stolen data and, in another, sought $500,000 in cryptocurrency from a victim company. Wagneius was arrested in December 2024 and indicted this week, and now faces up to 27 years in prison with sentencing scheduled for October 6.
Europol-led “Operation Elicius” has dismantled a Romanian-based ransomware gang called “Diskstation” that recently targeted Synology Network-Attached Storage (NAS) devices, encrypting data and disrupting businesses, including NGOs and media firms, in Italy’s Lombardy region. The group, active since 2021 under multiple aliases, demanded ransoms from $10,000 to hundreds of thousands in cryptocurrency. One man, suspected to be the primary operator of the attacks, was also arrested in Bucharest following international raids.
In another global operation dubbed “Eastwood”, law enforcement came together to target pro-Russian hacktivist group “NoName057(16)”, responsible for widespread DDoS attacks across Europe, Israel, and Ukraine. As part of the collaborative effort, authorities seized over 100 servers, issued seven arrest warrants, and detained two suspects. The operation was successful in disrupting the group’s infrastructure, but key members remain in Russia, and future attacks on European entities by the gang are still expected to persist.
The Bad | Katz Stealer MaaS Gains Traction, Stealing Sensitive Info Via Multi-Stage Infection Chains
A new report from SentinelLABS this week breaks down Katz Stealer, a sophisticated infostealer operating as Malware-as-a-Service (MaaS), launched in early 2025 and widely adopted by cybercriminals due to its ease of use, customizable features, and powerful capabilities. Marketed on Telegram, Discord, and web forums, it offers a web-based panel for affiliates to create custom payloads, manage stolen data, and configure attacks.

Katz employs a stealthy multi-stage infection chain that begins with phishing emails or trojanized downloads. A JavaScript dropper launches PowerShell commands to retrieve a steganographically embedded payload from a decoy image. It uses UAC bypasses, process hollowing, and scheduled tasks to achieve persistence and execute with elevated privileges, often hiding in legitimate processes like MSBuild.exe.
Once active, Katz Stealer focuses on harvesting data from browsers, messaging platforms, gaming services, email clients, VPNs, and cryptocurrency wallets. It bypasses modern browser protections such as Google’s Application Bound Encryption (ABE) by extracting master decryption keys and decrypting sensitive data in memory.
The malware also targets wallet extensions, clipboard data, and system files, sending stolen information back to hardcoded command-and-control (C2) servers via HTTP. The C2 infrastructure is IP-based, and Katz maintains persistence for ongoing data exfiltration. Attackers can also remotely wipe traces after data theft is complete.
Despite its advanced capabilities, Katz Stealer still relies heavily on user interaction, making training and awareness on social engineering and detection critical for prevention. SentinelOne Singularity detects and blocks Katz Stealer through real-time analysis of malicious behaviors, process injections, and network activity, ensuring systems remain protected from this evolving infostealer threat.
The Ugly | DPRK-Based Actors Expand On Contagious Interview npm Malware Campaign
North Korean threat actors behind the ongoing Contagious Interview campaign have published 67 new malicious packages to the npm registry, continuing their efforts to compromise the software supply chain. Cyber researchers observed that these packages – downloaded over 17,000 times – feature a new malware loader dubbed “XORIndex”, which builds on earlier campaigns distributing another loader called HexEval.
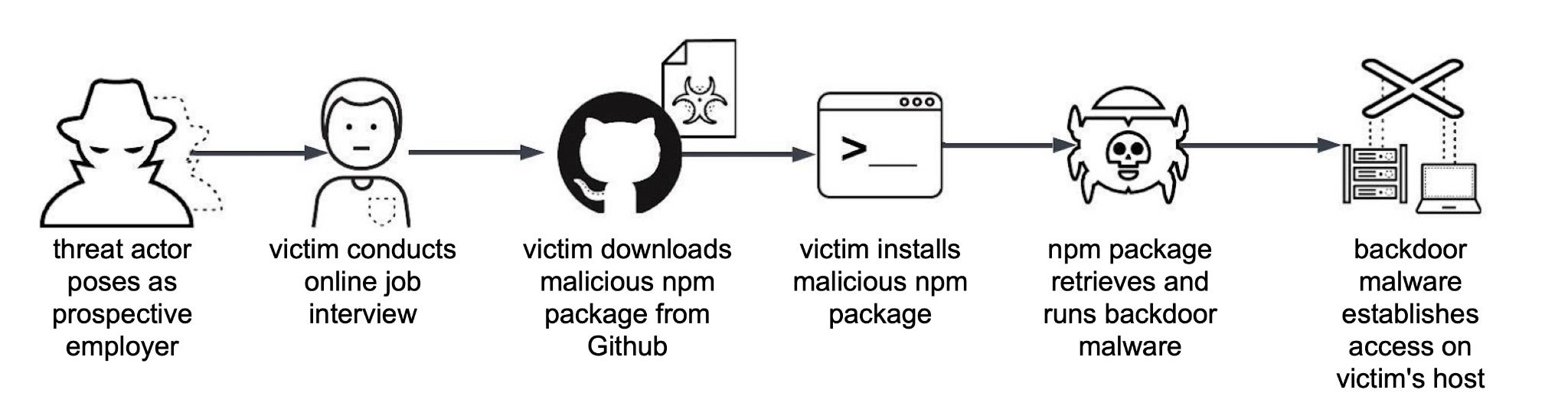
Contagious Interview is known for targeting software developers through fake coding assignments or poisoned open-source packages. The goal is to infect machines and extract sensitive data, particularly from developers at organizations of interest. This campaign aligns with North Korea’s broader strategy of exploiting remote IT roles to gain unauthorized access to global networks.
These npm packages serve as initial access vectors for BeaverTail, a JavaScript-based infostealer that targets web browsers and cryptocurrency wallets, and may also deploy the Python backdoor InvisibleFerret. XORIndex, like HexEval, profiles the victim’s machine and communicates with hardcoded C2 servers to exfiltrate system information and launch follow-on payloads.
Researchers observed that XORIndex has evolved from a simple loader into a more advanced tool with basic system reconnaissance capabilities. Meanwhile, attackers are rotating aliases and package names to evade detection, creating a “whack-a-mole” scenario for defenders.
The campaign continues to rotate npm maintainer aliases and reuse core malware components, making detection difficult. XORIndex alone has seen over 9,000 downloads since June 2025. Despite ongoing takedown efforts, the attackers adapt quickly with new variants. The malware is deployed using a consistent playbook with small variations, allowing the threat actors to maintain persistence despite ongoing takedown efforts, highlighting the growing need for vigilance across developer ecosystems.


