The Good | Authorities Target Two Nation State Threat Actors & Cybercriminals Linked to DragonForce Attacks
A Chinese national, Xu Zewei, was arrested in Milan under a warrant for alleged ties to the PRC-backed threat group known as Silk Typhoon, or Hafnium. Over the years, the group has been accused of targeting U.S. agencies, COVID-19 researchers, and healthcare organizations in 2020 to steal vaccine-related data. Italian media link Xu to these cyber espionage attacks and the more recent campaigns against OFAC and the U.S. Committee on Foreign Investment. Currently, Xu remains in custody as the U.S. seeks his extradition.

The U.S. Treasury has sanctioned a North Korean national, Song Kum Hyok, for running an IT worker scheme linked to APT45 (aka Andariel) threat group. Song used stolen U.S. identities to help DPRK nationals obtain remote jobs at American companies, funneling earnings back to the regime to support its weapons programs. Some of these workers also enabled cyberattacks and deployed malware onto their employers’ systems. The sanctions extend to five affiliated individuals and entities, closely following recent U.S. action against DPRK laptop farms that resulted in multiple indictments, seizures, and one arrest just earlier this month.
The UK’s National Crime Agency has detained four suspects – three British and one Latvian – reportedly linked to the cyberattacks on major UK retailers including Marks & Spencer and Harrods. The group, believed to be tied to DragonForce ransomware group, faces charges for blackmail and money laundering. The aftermath of the attacks caused major disruptions, with M&S suffering a $402M profit hit after ransomware deployment and data theft. Authorities were able to seize multiple devices for evidence, and investigations continue on as the broader collective remains active across retail, insurance, and transportation sectors.
The Bad | ZuRu Malware Uses Trojanized Termius.app & Modified Khepri C2 to Backdoor macOS Systems
A new write-up by SentinelOne researchers details new variants of a malware called macOS.ZuRu, a backdoor distributed via poisoned web results on Baidu search engine. In its latest iteration, ZuRu continues to spread by trojanizing legitimate apps used by developers and IT professionals.
In a new campaign, ZuRu masqueraded as the Termius SSH client, delivered through a malicious .dmg disk image. The fake app contains a modified version of Termius Helper, embedding a loader named .localized, which fetches a Khepri-based command and control (C2) beacon from download.termius[.]info, and writes it to /tmp/.fseventsd.
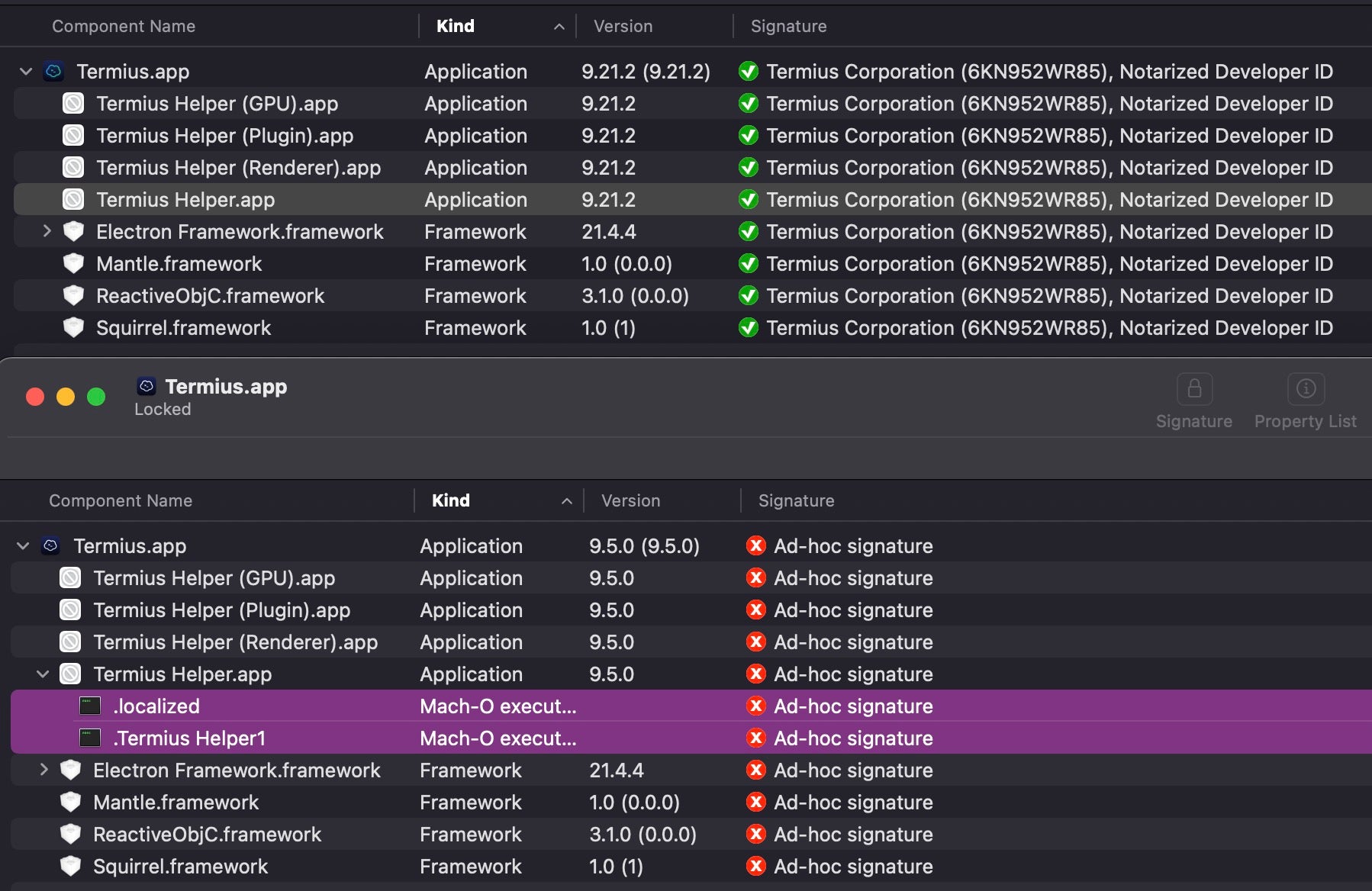
This latest version marks a shift in tactics. While older samples relied on dynamic library (Dylib) injection to load the Khepri backdoor, this variant embeds the loader directly in the application’s bundle.. Once deployed, the malware checks for existing installations, compares MD5 hashes, and updates itself if needed, pointing to a built-in self-update mechanism. ZuRu uses the open-source Khepri toolkit to give attackers remote control, enabling file transfers, system recon, process control, and command execution. SentinelOne notes the C2 beacon communicates with ctl01.termius[.]fun.
The malware installs a persistence module that attempts to masquerade as a system component by using the fake label com.apple.xssooxxagent. The malicious LaunchDaemon executes a copy of the .localized binary every hour from /Users/Shared/com.apple.xssooxxagent.
SentinelOne warns that ZuRu’s evolving tactics suggest it remains effective in environments lacking strong macOS endpoint protection. Singularity customers are protected against macOS.ZuRu.
The Ugly | DoNot Team Expands Targeting with LoptikMod RAT Through European Espionage Campaign
An Indian-linked threat actor known as DoNot Team (aka APT-C-35, SectorE02, Mint Tempest, Viceroy Tiger, or Origami Elephant) has been seen targeting a European foreign affairs ministry in a cyber espionage campaign. Active since at least 2016, the group is known for its use of custom malware such as YTY and GEdit backdoors.
Most recently, DoNot Team added a malware to their arsenal dubbed LoptikMod, delivered via spear phishing emails. In this new campaign, attackers worked by impersonating defense officials using Gmail and lured victims with emails referencing an Italian Defense Attaché’s visit to Dhaka, Bangladesh. The emails linked to a Google Drive-hosted RAR archive containing a malicious executable disguised as a PDF. Once opened, the file deployed LoptikMod, a remote access trojan (RAT) capable of establishing persistence, exfiltrating data, executing commands, and downloading additional payloads.
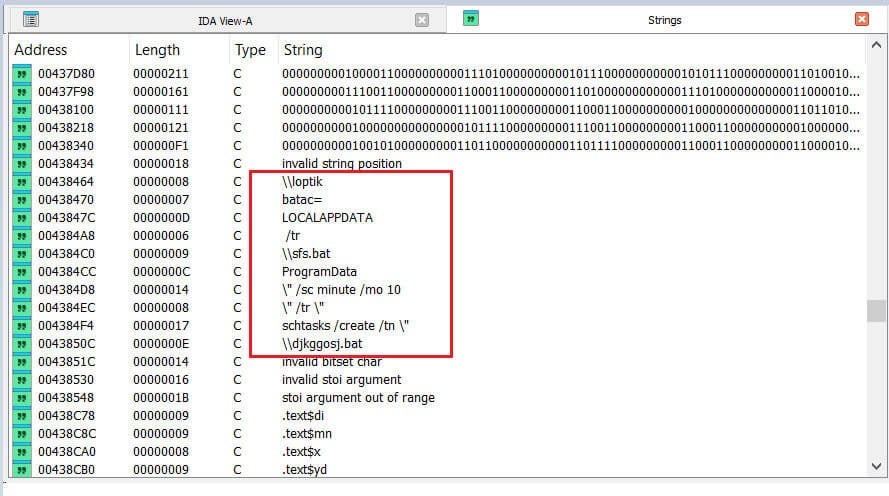
The malware evades detection through anti-VM checks, ASCII obfuscation, and by ensuring only one active instance runs on the system. Security researchers tracking the campaign note the command and control (C2) server used in the campaign is currently inactive, leaving details of its full capabilities unknown. DoNot Team typically targets government and defense sectors, NGOs and foreign ministries across South Asia, but this marks the first documented use of LoptikMod against South Asian embassies in Europe.
While there have been previous incidents where DoNot Team has attacked European organizations in the UK and Norway, researchers believe that this campaign is a strategic shift for the group, signaling enhanced capabilities and broader intelligence-gathering priorities. The attack reflects a growing interest in European diplomatic data, possibly to keep tabs on Western relations with South Asia and collect sensitive information on regional policy for the group’s likely state-aligned sponsors.


