Zero Trust Architecture (ZTA) is a modern cyber security architecture that is designed on one foundational principle: never trust anyone, and always verify. Unlike traditional security models where you grant privileges by default and treat the network perimeter as safe, Zero Trust follows zero trust principles. It trusts none and treats every device, user, and app, as untrusted, by default. It doesn't matter whether they are located inside or outside the network.
Every access request is authenticated, verified, and authorized. This helps reduce attack surfaces and prevent lateral movement.
Why Zero Trust Architecture is Crucial Today?
Zero trust matters more than now because we're shifting to cloud services. Here are some reasons why it's important:
- As we adopt remote and hybrid work models, perimeter-based network security becomes obsolete.
- Anyone can work from anywhere and many apps live across multi-cloud environments, and many of them are unmanaged.
- User access needs to be segmented to minimize damages. Blind trust is never enough and we need to replace it with dynamic, context-aware verification
- Zero-trust security is needed because it provides consistent security across multi-cloud, hybrid, and on-prem ecosystems.
Core Principles of Zero Trust Architecture
In a Zero Trust Architecture (ZTA), trust has to be always earned and it is never granted by default at a single point in time based on network locations. This is why zero trust architecture is important.
There are five core principles Zero Trust is based on:
Continuous Verification
Just like what it implies, every access request is vetted and verified based on multiple factors. No entity, workload, user, device, or external agent is granted access to any network or resource without verification.
Least-Privileged Access
Access must be granted only when an authorized user needs it. It's never granted without a reason and on a need-to-know or need-to-use basis only. After access is granted to the network and its connected resources, it may be automatically revoked once the job is done.
Contextual and Risk-Based Access Governance
The context behind every access request will be checked. Zero trust will use AI/ML to scrutinize contextual variables like device posture/health, geolocation, user behaviors, time of day, and other metrics. It will compute risk and govern access to said resources accordingly.
Continuous Monitoring and Risk Management
Zero trust will continuously monitor access requests and transactions in real-time. It will identify risks by doing dynamic analysis and is never static. Zero trust platforms adapt to threats and risks based on changing security contexts and also enforce different policies based on their changes.
No Public IPs
A Zero Trust Architecture will make sure that unauthorized devices and users can't discover data or services they don't have explicit permissions to. They shield apps and services from prying eyes and can eliminate public IPs. Zero Trust can exchange inbound connections for inside-out connections which can help reduce attack surfaces. They reduce complexity and provide better security for distributed environments.
What Does Zero Trust Mean?
Zero trust means you trust nobody. It’s not a product or service but rather, a security strategy which follows strict identity verification and validation.
It works on the model of assuming a breach and adapts to the complexities of modern threat environments and mobile workforces. Zero Trust verifies to protect every account, device, app, and data, no matter where they are located. It is an integrated security philosophy and can block unwanted events and security outcomes in organizations. If you want to know how zero trust architecture works, read below.
How Zero Trust Architecture Works
A Zero Trust Architecture is a unique framework where organizations provide secure connectivity to anyone and everyone. You can think of it turning the internet into a new corporate network. A Zero Trust Architecture platform will use technologies like endpoint detection and response (EDR) and identity management solutions.
At the high level, here is how it works:
- Start with verification when it comes to access requests: Zero Trust will provide least-privileged access. It will connect IT resources only after verifying identities for every user and entity.
- Zero Trust can connect entities directly to designated locations instead of just to networks. They can prevent lateral movement and can even verify the IT resource and service individuals are trying to access.
- Policies are enforced in real-time and on a per-session basis. The architecture can enforce several actions like: block, isolate, allow, deceive, and more. After granting access, it will continuously monitor and identify risks. It will also note policy changes and alter them as necessary.
- After policy enforcement is done, users will be allowed to connect directly to apps. Inbound connections are used for SaaS and the web. Private apps will use inside-out connections. All connections will use the same level of security and require verification.
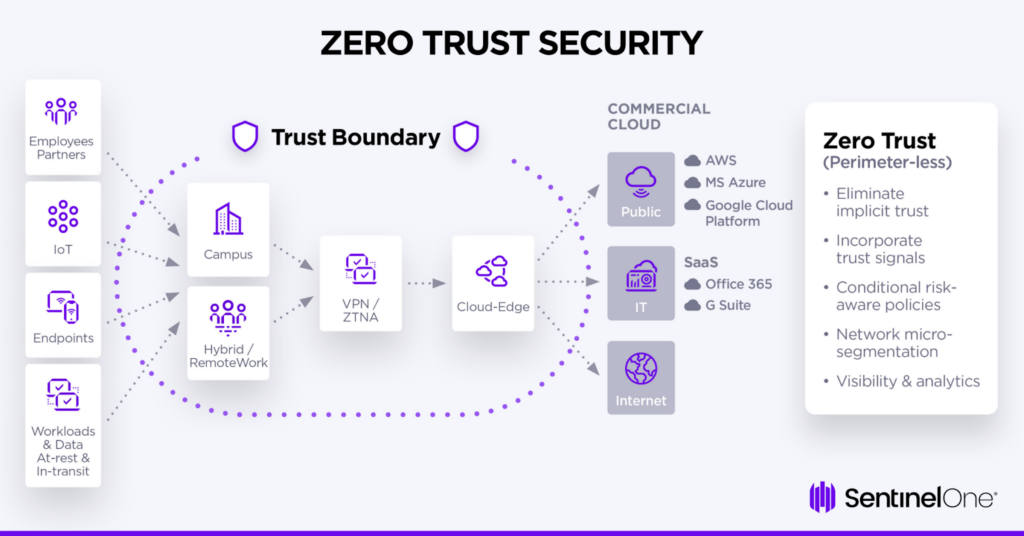
Benefits of Zero Trust Architecture
Adopting a zero-trust architecture confers a number of benefits that an entity can gain, greatly improving the security posture. Understanding these advantages gives businesses an idea about the advantages of investing in zero-trust architecture and continuing with its implementation.
- Improved security posture: The zero trust architecture secures organizations against cyber threats through constant checking of all attempts to access data, hence minimizing unauthorized access that eventually leads to data breaches. This gives rise to the benefits of the zero-trust architecture with regard to security and resilience.
- Zero trust architecture minimizes the attack surface: Through the use of micro-segmentation, zero trust enforces least-privilege access. This makes for an effective containment strategy in the case of an attack, whereby the potential impact of compromised accounts or systems is massively reduced, making it hard for the attacker to obtain his objectives.
- Regulatory compliance: Adhering to zero trust architecture principles helps organizations meet regulatory requirements such as GDPR, HIPAA, and PCI DSS. The emphasis on data protection, strict access control, and comprehensive auditing supports compliance efforts and reduces the risk of costly fines and reputational damage.
- Improved visibility and control: Continuous monitoring and analytics provide detailed insights into network activity. It means that the organizations can identify the irregularities in the systems and act promptly as well as make wiser security choices. Enhanced control over users and devices is a significant zero-trust architecture benefit.
- Secures access to enterprise resources: Zero trust architecture secures access to enterprise resources from any user location and device, be it on-premise or in the cloud, which is very supportive of modern work environments. It goes a step further to cement its importance in securing cloud environments against modern threats, as more than 90% of organizations migrating workloads into the cloud have adopted or intend to adopt zero-trust architecture. Such flexibility underpins business operations without compromising one of today’s essential security requisites: increasingly mobile and distributed workforces.
- Cost savings over time: Although a bit costly to implement at the beginning, the zero trust architecture cuts down on other costs that relate to security incidents and breaches or downtimes. By implementing a zero-trust architecture, it is possible for businesses to save an average amount of $1 million in terms of the cost of a data breach. It decreases financial loss amongst other legal liabilities and damage to brand reputation, hence bringing long-term financial benefits.
Difference Between Zero Trust Architecture and Zero Trust Network Access (ZTNA)
While zero trust architecture and Zero Trust Network Access both derive from the philosophy of zero trust, each fits into different cybersecurity strategies. Understanding their differences is thus key to effective organizations in light of better security posturing. Below is a comparison table which presents the comparison between the both based on some factors:
Comparison Table
| Aspect | Zero Trust Architecture (ZTA) | Zero Trust Network Access (ZTNA) |
|---|---|---|
| Scope | Comprehensive security framework for the entire organization | Specific solution for secure remote access |
| Focus | Policies, principles, and technologies across all assets | Granting access to applications without exposing the network |
| Implementation | Involves identity, device, network, application, and data layers | Operates primarily at the network and application access layers |
| Access Control | Continuous verification of all users and devices | Provides granular access to specific applications |
| Use Cases | Enhancing overall security posture | Facilitating secure remote work and third-party access |
As we have learned from the above table, zero-trust architecture involves an overall security strategy that implements zero-trust architecture components in an organization from end to end. Further, it includes a broad range of policies and technologies that independently check each and every access by assuring whether the users and devices have actually been authenticated and authorized and their activities are continuously validated. In this approach, the areas of concern include identity management, device security, network segmentation, application control, and data protection.
On the other hand, Zero Trust Network Access is a focused application of zero trust principles that is mainly aimed at providing secure remote access to applications. While ZTNA may actually embody zero trust principles, it is primarily technology-focused and not strategic. By design, solutions of ZTNA allow users to connect to applications without exposing the entire network, making them very effective for companies having remote workforces or in need of providing secure access to third-party vendors.
Understanding such a difference implies that an organization can draw on proper remedies to make the cybersecurity of an organization effective. In other words, zero trust architecture is the basic framework, while ZTNA is more practical. Now that we have discussed the differences, let’s move on to discuss the principles of zero-trust architecture.
Zero Trust in Cloud, Hybrid, and Multi-Cloud Environments
Here is how Zero trust works and applies to cloud, hybrid, and multi-cloud environments:
Extending Zero Trust to SaaS, IaaS, and Hybrid Workloads
SaaS applications and Infrastructure-as-a-Service platforms are part of most organizations now. Your team uses cloud apps for email, collaboration, and storage. You also run virtual machines and containers in the cloud. With Zero Trust, you check every connection to these services. When an employee accesses a SaaS app, the system verifies who they are and what device they're using. If they're accessing from somewhere unusual, you can require extra verification steps.
Hybrid workloads mix apps running on-site with apps running in the cloud. Some data might be stored on your servers, and some in the cloud. Zero Trust connects all of these pieces together. It treats a request to your on-site database the same way it treats a request to a cloud service. This means you get consistent security across everything, not just in one place.
Managing Identities Across Cloud Platforms
When you use multiple cloud providers, you have identities spread across different systems. One person might have an account in AWS, Azure, and Google Cloud. Managing these can get messy. Zero Trust solves this by creating a central place to verify identities. When someone tries to access anything, the system checks their identity in one place, not three different places.
You can link all these cloud identities together. When you add a new user or remove someone who left, you only do it once. The change flows across all your cloud systems automatically. This also helps prevent people from accessing things they shouldn't. If someone changes jobs, you can quickly remove their old access and give them new access for their new role, all in one step.
Network Segmentation and Access Policies in Hybrid Environments
Hybrid environments need clear boundaries for what can talk to what. With Zero Trust, you create rules that say which apps can talk to which databases, and which users can access what. These rules work the same way whether the app is on-site or in the cloud.
You can break your systems into small segments. Each segment only allows specific traffic. If someone tries to access something they're not supposed to, the network stops them. This prevents hackers from moving around freely if they get into one part of your system. The rules update in real-time, so if a threat is spotted, you can shut down access immediately without waiting for a manual process.
Common Challenges in Cloud Zero Trust Adoption
Moving to Zero Trust in a cloud environment takes work. Many organizations have apps that were built a long time ago, and they don't work well with Zero Trust policies. These legacy apps might expect to see other apps without verification, which goes against Zero Trust principles.
Another challenge is that cloud providers have different ways of managing access and security. Azure has different tools than AWS, and Google Cloud is different again. Getting these to work together smoothly takes time and planning. You also need to train your team on how Zero Trust works. People might get frustrated if they're asked to verify their identity more often, even though it makes your company safer. Getting the balance right between security and usability takes thought and testing.
Zero Trust for Remote Work, IoT, and Edge Devices
Here is how Zero trust works for remote work, IoT, and edge devices:
Protecting remote endpoints
Zero Trust treats every remote access request as potentially untrusted, regardless of previous authentication history. Every connection from remote endpoints—whether laptops, mobile devices, or home networks—undergoes rigorous verification before accessing corporate resources. It evaluates multiple signals in real-time, including device health status, user identity confirmation, location anomalies, and behavioral patterns. If a remote employee's device shows signs of compromise, Zero Trust can immediately revoke access or downgrade permissions without requiring manual intervention.
Managing IoT and OT security
IoT devices present unique security challenges because they often operate with limited processing power, cannot receive regular security updates, and frequently run proprietary firmware that lacks standard security controls. Zero Trust addresses these constraints by treating every IoT device as untrusted and verifying each interaction it attempts. Rather than securing the device itself (often impossible), the architecture secures what the device can access and how it communicates with other systems.
In industrial IoT environments, Zero Trust enforces strict segmentation between operational technology networks and IT infrastructure. Each sensor, controller, or gateway must authenticate before sending data, and the system validates that only legitimate, expected traffic flows.
Edge computing considerations
Zero Trust secures edge environments by verifying every computation request, application access, and data transfer at the edge layer itself. It ensures that edge nodes and endpoints authenticate to each other and to centralized policy systems. It verifies service-to-service communications and prevents unauthorized lateral movement between containerized workloads. Data flowing between edge devices and cloud infrastructure may need cryptographic verification,
AI-based continuous authentication
Zero Trust uses AI to check on users all the time, not just when they log in. It can watch user behaviors and how they interact with AI tools, apps, and services. AI-based continuous authentication can also run in the background and are great for monitoring remote work sessions. If any account is active but the user is not present, it can catch and prevent malicious activity in real-time. Since AI-based authentication works 24/7, it can catch problems early before any big security issues arise.
Zero Trust Maturity Model & Adoption Roadmap
Most global agencies refer to the CISA's Zero Trust Maturity Model Version 2.0 and consider it a roadmap or blueprint to follow. It has 5 pillars and each of them provide specific zero-trust architecture examples, including advice on how to optimize them.
The essential components of the CISA model are as follows:
- Identity and Access Management
- Device Security
- Network Security
- Data Security
- Visibility and Analytics
- Application Security
- Automation and Orchestration
- Governance
How to Implement this Roadmap
Knowing how to implement zero trust architecture models like the CISA's is just as important as learning everything about these models themselves. Implementation is strategic, phased, and ongoing. It won't happen all at once but rather in incremental and manageable stages.
Here is how you implement it:
- Apply least-privileged access and integrate it with major Identity Providers (dPs).
- Next, ensure that only secure and managed devices can connect to your services. Do device compliance checks and apply microsegmentation to limit access to apps instead of just networks to minimize lateral threat movement.
- You'll also want to start using real-time monitoring and analytics solutions like to identify and respond to anomalous activity. Data protection tools will help with preventing data losses and ensure encryption both at rest and in transit.
Other things you want to do to ensure a smooth zero trust architecture implementation are:
- Enforce multi-factor authentication and use role-based access controls for continuous and real-time user verification
- Mandate security compliance for users, devices, and resources, before granting access of any sort. It should align with standards like the NIST SP 800-207, and you should also incorporate governance and assessment frameworks.
- Use secure app development practices to protect apps from vulnerabilities
- Integrate security orchestration and automation (SOAR) workflows for efficient incident response and policy enforcement. Create clear and granular policies to ensure that all zero trust architecture principles are enforced consistently.
Zero Trust Implementation Checklist
Here is your zero trust architecture implementation checklist’s action items:
- First, start off by forming a dedicated Zero Trust team. You will need team members who have expertise in network, identity, app and data security. You will also have to secure executive sponsorship and gain the support of leaders.
- Find out what services need zero trust protection and classify them. These can be services, physical assets, critical data, apps and other things in your organization.
- Do an asset inventory and map transaction flows. All your workflows and services to understand your current security implementation carefully and make it a phased incremental rollout. Start with a low risk pilot environment, just to see how it kicks off and works.
- Phase 2 of your Zero Trust Implementation Checklist is implementing multi-factor authentication, centralizing identity management, and establishing least privilege access. You will need to implement identity governance and enforce device validation.
- For your networks, you will have to encrypt all traffic and add micro-segmentation. Secure APIs, manage permissions, and apply security checks throughout the CI/CD pipeline.
- When it comes to monitoring and ongoing management, it will make up phase 3 of your zero trust implementation checklist. You will have to use security information and event management and analytics solutions to monitor all user behaviors and network activities in real time. Integrate identity and endpoint controls as well.
- You will also have to develop and test plans to respond quickly to security incidents. Always take an assumed breach principle and use automation to collect solid data from various sources. You will need to trigger immediate actions whenever you detect any anomalies.
- Conduct regular security assessments, testing, and do periodic audits of your access stocks. Review your security policies and run vulnerability scans to identify and address gaps.
- You'll also need to educate and train your employees and provide ongoing training. They need to be aware of your zero trust principles, policies, and implement the best zero trust architecture practices.
- After you roll out your plan, you'll have to extend the scope of your Zero Trust access, assess how your Zero Trust security architecture is working, find areas of improvement, and continuously optimize the process based on feedback and new threats that emerge.
Challenges of Adopting Zero Trust Architecture
Implementing zero-trust architecture is indeed having its challenges. Recognizing as well as focusing on these would be critical to a successful transition with maximum return on investment.
- Implementation Complexity: Implementation of zero trust architecture is actually based on overhauling the existing systems and processes. Integration of new technologies and redefinition of workflows further increase the complexity, demanding strained resources and calling for careful planning/project management, which might necessitate phased implementation.
- Cultural Resistance: Cultural resistance to approaches that will change how employees gain access to systems and data can be expected while adopting ZTA. The resistance will be overcome only through effective communication, training, and leadership support. Communications of the importance of security and how zero trust architecture benefits the organization will help gain buy-in with staff.
- Existing Legacy Systems Integration: Integrating with existing legacy systems is difficult because older systems do not easily collaborate with new security technologies invoked by zero trust. Upgrading or replacing such legacy infrastructure could grow so high in cost and time that it becomes prohibitive; however, it is usually a necessity to achieve complete realization of the principles of zero trust architecture. An organization shall look at the existing systems and plan accordingly for upgrades.
- Resource and Budget Constraints: The zero trust architecture requires new investments in different tools, technologies, and people with particular skill sets. This requirement is going to be balanced along with other budget priorities that might constrain the scope or speed at which it will be implemented. To secure the necessary funding, organizations must engage executive sponsors who can advocate for strategic initiatives while demonstrating potential ROI to decision-makers.
- Complexity of Policy: Zero Trust Support policies are complex to develop and manage in detail. It is tough to create comprehensive security policies for Zero Trust, apply them consistently, and keep them updated concerning continuously evolving threats. In this regard, policy management through automation tools would help make life easier since every zero-trust architecture shall be supported by best practices.
- Selection of Vendors and Technology: Appropriate choices regarding vendors and technologies are very crucial in terms of interoperability and functionality. With numerous solutions available, organizations are very likely to face problems in choosing components that best fit zero-trust architecture and are seamlessly integrated. Due diligence with detailed evaluations is supposed to be carried out here.
Best Practices for a Successful Zero Trust Strategy
An ideal zero-trust architecture can be observed where an organization follows best practices for the implementation and management of the system continuously. This ensures that the security framework remains solid, effective, and aligned with organizational objectives.
So, here are some key best practices:
- Create a Well-Defined Roadmap: There has to be a detailed roadmap or plan entailing organizational goals, time frames, and achievements. A gradual approach allows for the smooth implementation of zero-trust architecture components and may also be less intrusive into operations. You should also periodically reassess the roadmap for necessary readjustments.
- Execute Asset Discovery: Identify network assets, including devices, applications, data repositories, and user accounts. It becomes important to understand what needs protection in order to apply zero-trust architecture principles effectively. Asset discovery tools can automate this task and enable the inventory to stay updated.
- Strong Authentication: This is a zero trust architecture best practice where the implementation of multi-factor authentication, biometric verification, and even risk-based authentication falls under. Securing identity assurance is one of the best practices for zero-trust architecture, meaning only authorized users shall have access, even in the case of credential compromise.
- Apply the Principle of Least Privilege: Design a policy where there is an assignment of minimum permission for users concerning their role. Periodically review and adjust permissions with regard to changes in responsibility. Employ automation tools to manage the rights of access with a view to maintaining compliance with zero-trust principles.
- Segment the Network Strategically: With micro-segmentation, isolate critical assets and systems from the rest. For each of these smaller-sized segments, draw a clear definition and enforcement of security policy to reduce the possibility of wide-scale breaches. Segmentation of the network should be performed with a good understanding of data flows and communication patterns.
- Leverage Automation and Orchestration: Automating the more mundane jobs of security-enforcing policies and incident response can go a long way in reducing human errors. This would be further helped through orchestration tools, which can integrate actions from zero-trust architecture components for fast, consistent responses against threats.
- Train and raise awareness: Educate employees about zero trust architecture, the role of zero trust, and their role in security maintenance. Regular training sessions, simulations, and knowledge updates of emerging threats enable a culture of security awareness. Employee awareness is one of the key success factors among all the best practices we discussed when it comes to zero-trust architecture implementation.
Adopting best practices such as continuous monitoring and segmentation is crucial. Singularity Endpoint Protection enables these practices through autonomous endpoint protection.
Measuring Success: Metrics, KPIs, and Continuous Improvement
Here is how you can measure the success rate of your zero trust security strategy:
- Security posture metrics will measure your Zero Trust effectiveness. You can track MFA adoption rates to ensure proper authentication. Policy compliance shows how well teams follow access rules. Access violations provide insight into gaps needing attention. These indicators give a clear picture of security health.
- Operational metrics evaluate how efficiently your team detects and responds to threats. Mean time to detect measures how quickly systems identify suspicious activities. Mean time to respond tracks duration from detection to resolution. These metrics will help you optimize incident response and minimize exposure windows.
- Continuous feedback and maturity tracking will let you strategically evolve your zero trust security strategy over time. You can assess progress against maturity models with traditional, initial, advanced, and optimal stages. Regular audits and tests can help you validate controls and identify weaknesses before they can be exploited by threat actors.
- User experience measurements can help you balance security and efficiency. Monitor login latency to ensure your measurements don't hinder workflows. User feedback and helpdesk tickets can provide insights for improving policies and maintaining protection.
Zero Trust Architecture Use Cases in Different Industries
Zero trust architecture is used by organizations in various industries, each with its own unique challenges in information security. So, let’s explore how companies in each industry use zero trust architecture and check out some zero trust architecture examples:
- Healthcare: Zero trust architecture secures sensitive patient data, protects EHRs, and maintains compliance with HIPAA while preventing unauthorized access to critical data. Continuous verification and micro-segmentation are some of the approaches commonly used here that denote keeping sensitive information confidential and accessed by authorized persons only.
- Financial Services: Banks and financial organizations make use of zero trust architecture when it comes to the security of a transaction, customer data, and proprietary systems. With the increase in online banking along with fintech solutions, the implementation of zero trust architecture components such as strong authentication and advanced analytics helps in fraud prevention, detection of suspicious activities, and compliance with regulatory norms like PCI DSS.
- Manufacturing: Zero trust architecture principles help safeguard the intellectual property, control systems, and supply chain integrity of the manufacturers. Security remains very crucial for the Industrial Internet of Things (IIoT) devices and manufacturing systems. In this regard, micro-segmentation with rigid access controls ensures minimal breakdowns along production lines and other industrial espionage.
- Education: Learning facilities like schools and universities are at constant risk of falling victim to cyber-attacks. This is because the networks are accessed via various devices by students, faculties, and staff members. With zero-trust, academic records, research data, and administrative systems can be kept safe in schools and universities. Furthermore, zero trust architecture best practices imply permissions granted to access sensitive resources only to genuine users, even in environments that are dynamic and open.
- Government Agencies: Government agencies are attempting to adopt zero trust architecture in order to protect national security information, citizen data, and critical infrastructure. By assuming breaches and implementing continuous verification, they enhance resilience against sophisticated cyber threats and state-sponsored attacks. Compliance with frameworks like NIST’s zero trust architecture guidelines is often required.
Future of Zero Trust: AI, Automation & Continuous Trust
We can expect Zero trust to be the new normal from 2025 onward. Organizations are realizing that legacy perimeter-based models are not a good match for the challenges of cloud adoption, hybrid work, and emerging insider threats.
- SASE will see a major shift as organizations consolidate security and networking vendors. They'll opt for unified and cloud-native platforms to gt a single-pane-of-glass view into their security posture.
- AI and automation will drastically change cyberthreat detection and response capabilities. Organizations will use AI-enabled threat detection to fight against rising malware and phishing campaigns. They will better defend against anomalies, detect zero-days, and get accurate context for efficient and automated incident response.
- We can also expect identity-driven security to redefine zero trust access controls. Organizations will manage identities, enforce MFA, and provision access. They will defend against threats like credential theft and misuse. We can also expect tighter integrations with third-party vendors and reductions in attack surfaces.
- Cloud-native agentless CNAPP solutions will offer AI-driven analytics, and integrate with identity fabrics. We’ll see a shift towards better behavioral risk scoring and the use of multiple detection engines in these solutions to detect configuration drifts and ensure better zero trust security compliance.
- Businesses will also integrate Cloud Security Posture Management (CSPM) solutions and use strong endpoint detection and response (EDR) solutions to improve zero trust security.
How SentinelOne Can Help?
SentinelOne for Zero Trust can extend visibility, analytics, and response capabilities across endpoint, identity, cloud, and network. It enables the rapid adoption of a Zero Trust security model.
SentinelOne can reduce open attack surfaces and enhance security capabilities beyond perimeter defenses. It treats every user, endpoint, app, workload, and data flow as untrusted. The platform operates with the assumption that an adversary already has a presence within the environment, so it follows an "assume breach" philosophy.
You can verify explicitly and dictate access in a consistent manner using multiple trust signals for contextual access decisions. SentinelOne’s approach to Zero Trust provides the means for security teams to continuously monitor and manage the hygiene, risk, and hardening of their entire estate as part of a Zero Trust strategy.
SentinelOne Singularity™ XDR provides visibility, analytics, and autonomous response capabilities that help organizations move to a Zero Trust security model. To help organizations successfully adopt a Zero Trust security model, SentinelOne has partnered with leading identity and network vendors like Zscaler, Microsoft, CloudFlare, Guardicore, and others, to deliver validated Zero Trust capabilities.
SentinelOne's agentless CNAPP solution offers AI Security Posture Management (AI-SPM) that can configure checks on AI models and discover new AI pipelines and services. Prompt Security by SentinelOne helps organizations adopt zero trust security for AI tools and services. It can fight against shadow AI usage, prevent denial of service and wallet attacks, mitigate unauthorized agentic AI actions, and prevent LLMs from generating harmful responses to users. Prompt Security can defend against prompt injection attacks, malicious prompts, and prevent AI model misdirects and biases. It applies the strictest guardrails and ensures the safe and ethical use of AI tools and services.
You can also check out SentinelOne's AI-SIEM solution, Singularity™ Endpoint, Singularity™ Cloud Security Posture Management, Singularity™ Cloud-Native Security, and Singularity™ Identity offerings for adopting a Zero Trust security architecture in your organization.
Reduce Identity Risk Across Your Organization
Detect and respond to attacks in real-time with holistic solutions for Active Directory and Entra ID.
Get a DemoConclusion
A Zero Trust architecture integrates advanced security with strict access controls and ongoing education to defend against the latest threats. For businesses, this means adopting a proactive and more resilient cloud and cyber security posture. If you're ready to start your Zero Trust journey, be sure to reach out to the SentinelOne team today. We can help! :)
FAQs
Zero trust is a security model based on the principle of not trusting a user or device by default, whether insider or outsider, of the network perimeter. No request for access should be granted without constant verification of its authenticity to make sure only authenticated and authorized users will have access. It will lead to conformance with the principles of zero-trust architecture and will result in enhancing the security of minimum assumptions of trust.
Major steps in implementing zero trust security include:
- Asset Discovery: This is the identification of all the assets, which include devices, users, applications, and data.
- Strong Authentication: Enable multi-factor authentication and strong identity verification processes.
- Principle of Least Privilege Access: Establish and enforce appropriate access policies and procedures that provide a user with the least amount of privileges or access necessary.
- Micro-Segmentation: Segment the network, isolating resources and bounding lateral movement.
- Continuous Monitoring: Monitor network activity through various tools and spot anomalies as they happen.
- Policy Enforcement: Automate the application of security policies across all components in a zero-trust architecture.
Integrating zero-trust architecture with existing systems is challenging due to several reasons. For example, the existing infrastructure is not compatible with the newer security technologies needed for the zero-trust approach, and integration is challenging. Furthermore, the process of deploying zero trust in the existing framework is a bit costly for SMBs and also takes a lot of time. There are also resource limitations that organizations experience because implementing new technologies is pressure on the financial and human capital. Also, cultural resistance is often cited as a problem, as people continue using the familiar ways of working and getting the necessary resources.
The six pillars of zero trust architecture, often referred to as zero trust architecture components, include:
- Continuous Verification: Continuous user and device authentication and authorization.
- Least Privilege Access: Limiting the authorities of the user to the basic level of functionality.
- Assume Breach: Assuming that breaches can happen anywhere while implementing the controls.
- Micro-Segmentation: Using subnetworks that are separate and secure from one another.
- Strong Authentication: By applying Multi-factor and Advanced authentication techniques.
- Visibility and Analytics: Supervising the network traffic to identify threats and act upon them.
No, they're not the same thing. Zero Trust is a broader security approach where you don't trust anyone by default, whether they're inside or outside your network. You verify everything and everyone all the time. Zero Trust Network Access is a specific part of that strategy. It focuses on controlling who gets access to your network resources. You can have Zero Trust Network Access without implementing the full Zero Trust model across your entire organization, but it's a good first step if you're starting out.
Yes, small organizations can adopt Zero Trust, but you need to approach it differently than large enterprises do. You don't have to deploy everything at once. Start by enabling multi-factor authentication and monitoring your network traffic. You should also set up access controls so employees only get what they need to do their jobs. If you have limited resources, you can use cloud-based security tools and solutions instead of building your own infrastructure. The key is to start somewhere and build from there rather than waiting until you have a bigger budget.



