The Good
This week, it was announced that a joint effort between the French Border Police and the Spanish National Police, along with Europol, resulted in taking down an operation centered around counterfeit documents used, among other things, for human trafficking.
Forged identity documents are very big sellers on the Dark Web. Counterfeit documents available for purchase on the darknet include passports, birth certificates, drivers licenses, vehicle registration documents and other official identity cards.

While fake IDs can be used for a variety of nefarious purposes, the gang busted in this joint European law enforcement operation were said to be heavily involved in both human and drug trafficking, as well as property crimes. According to Europol, the organized crime group also charged upwards of €8000 per person for migrant smuggling operations.
Law enforcement agencies tracked distribution of forged ID documents across several jurisdictions, including France, Germany, Georgia, Italy, Lithuania, and Spain.
In the operation, seventeen suspects were arrested, six houses searched and a variety of electronic equipment seized. Police also recovered an unspecified amount of cash, as well as payment cards, counterfeit and genuine ID documents, and work permits. According to Europol, the gang’s network has been entirely dismantled and they have established multiple links between this case and other ongoing investigations.
The Bad
The Russian invasion of Ukraine has caused a significant rise in activity from Hacktivist groups, including website hacking and massive DDoS attacks aimed at Ukrainian entities. Researchers this week provided a fascinating look into one such threat actor and its connections across several countries, from Brazil to Sweden to Russia.
The self-styled “theMx0nday” group (The Monday Group) are based in Brazil and, the researchers claim, conduct operations in support of Russia. Most of their attacks are conducted through a Swedish ISP, Njalla, run by Pirate Bay co-founder, Peter Sunde, according to the researchers. They suggest that “theMx0nday” group may be using Njalla as a VPN exit node, although they haven’t ruled out the possibility that the attackers may have hacked another Njalla customer’s server or simply be Njalla customers themselves.
Aside from conducting massive DDoS campaigns against Ukrainian targets, the report says the Brazilian-based threat actor defaced multiple edu.ua (Ukrainian education) websites last week as Russia mounted its first incursions into Ukraine.
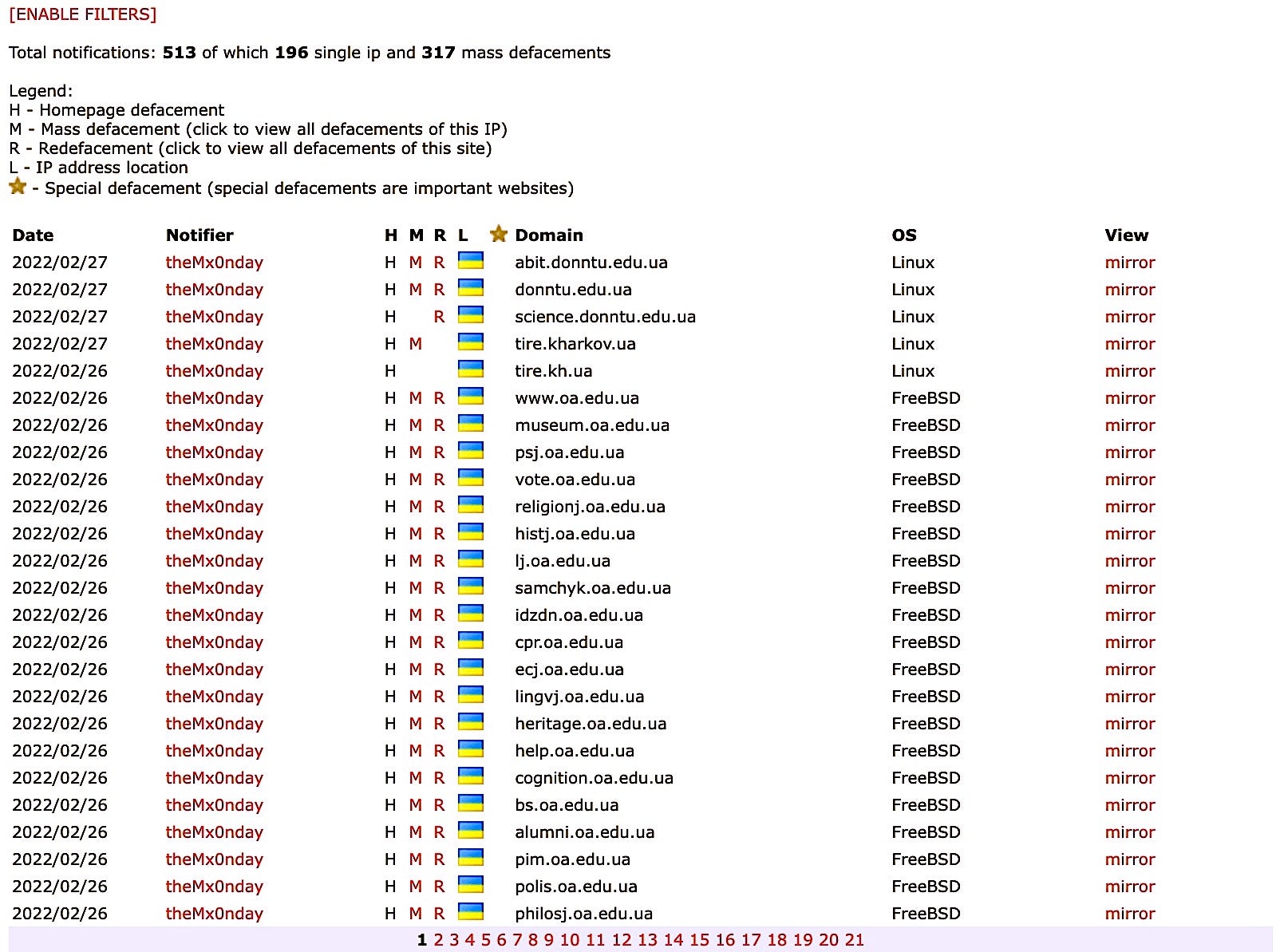
Prior to Russia’s military operation against Ukraine, the Monday group had primarily focused its attacks on Brazilian websites. Precisely what motivated it to support Russia’s invasion of Ukraine is at this time unknown, though it could be as simple as DDoS for hire. Since the story went viral, the group’s self-proclaimed “founder” deleted a tweet stating the hackers supported Russia’s invasion of Ukraine, claiming it was all for “the lulz”.
The Ugly
This week, a number of IoT vulnerabilities specific to healthcare have emerged, prompting CISA to release advisories in relation to two of them and researchers to call on healthcare providers to take medical device security more seriously in light of others.
Automated medication dispensing systems help clinicians to dispense medications to patients at the right time. Alas, it turns out that multiple products made by one vendor in use worldwide contain hard-coded credentials that can allow threat actors access to protected health information on the devices’ underlying file system. CISA reports that the vulnerabilities, CVE-2022-22766, CVE-2022-22765, have low-attack complexity.
While implementing hard-coded credentials in IoT or any internet-facing devices is fraught with dangers, credit goes to the device manufacturer who self-reported these issues upon discovery and is working to strengthen credential management in future devices. Meanwhile, mitigation steps can be found in CISAs advisories noted above.

In other health-related vulnerability news, researchers this week discovered that over 75% of 200,000 network-connected “smart” infusion pumps suffer from multiple vulnerabilities, previously reported and patched against various CVEs between 2016 and 2020. Infusion pumps and “Smart IV drips” serve to administer fluids and medication to patients through a controlled and programmable flow.
The vulnerabilities make it possible for attackers to gain access to sensitive information, but more worryingly in some cases unauthenticated users could send network traffic in a certain pattern that may cause the pump to become unresponsive or operate in unexpected ways.
Researchers have urged health providers to identify at-risk devices and to retire or repair them to avoid putting patients’ lives or sensitive information at risk.


