The Good | Russian National Linked to Ryuk Ransomware Laundering Schemes Sanctioned By US Authorities
One of Ryuk ransomware’s many affiliates just had a target placed on their back by the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC). Ekaterina Zhdanova was sanctioned this week after being identified as a key player in laundering millions of dollars in cryptocurrency. Zhdanova leveraged her expertise in cryptocurrency and blockchain networks to circumvent anti-money laundering controls.
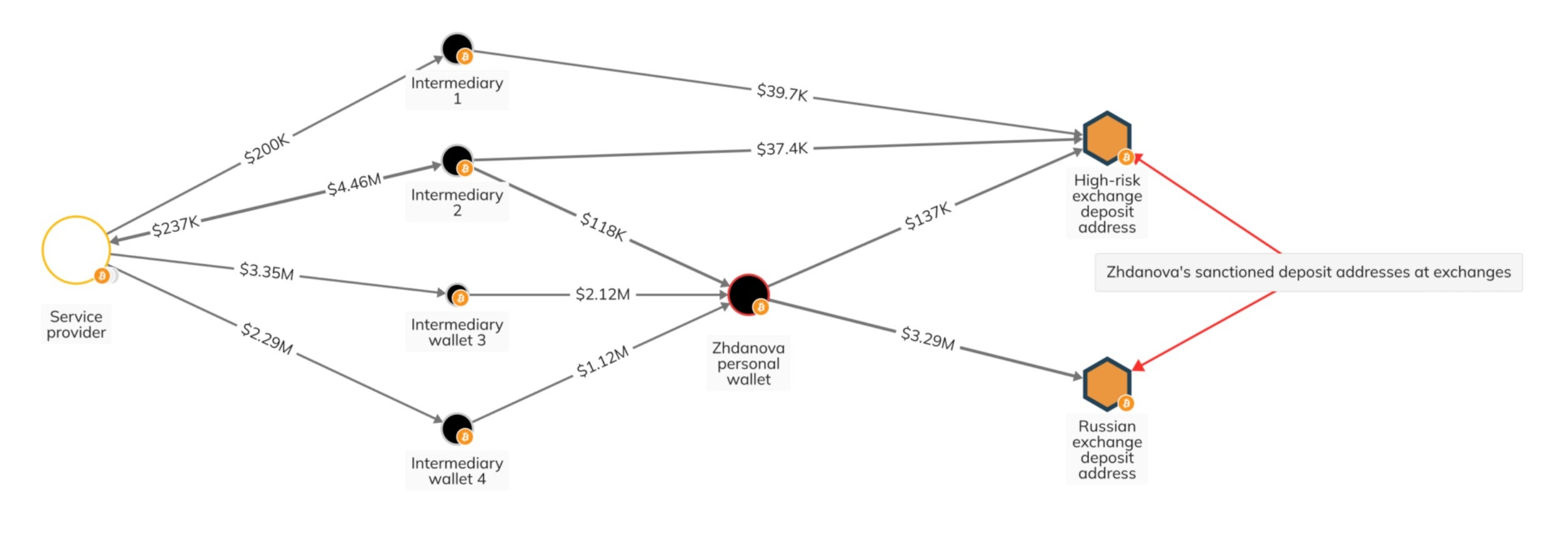
The OFAC and blockchain analysis experts highlight her use of a vast global network of money launderers to obscure her financial activities while expanding her clientele. Most notably, Zhdanova is believed to have aided the Ryuk ransomware operation, laundering over $2.3 million in suspected ransom payments for one of its known affiliates.
Ryuk ransomware operators made global headlines during the COVID-19 pandemic after extorting healthcare facilities for astronomical ransoms. Her work with the Ryuk affiliate involved the use of a fake investment account and real estate transactions to conceal the origins of the ransom payments.
A long list of malicious transactions follow Zhdanova. Authorities say that she has also been identified in helping Russian oligarchs evade Western sanctions set after Russia’s invasion of Ukraine. In addition, she facilitated the transfer of over $100 million for a Russian oligarch to the United Arab Emirates, orchestrating cases where her clients could obtain UAE tax residency, ID cards, and bank accounts.
Now, Zhdanova faces a freeze on all her U.S.-based assets, and U.S. individuals and entities are barred from transacting with her. This move underscores the U.S. government’s commitment to curbing money laundering activities, especially those linked to ransomware operations and the evasion of international sanctions.
The Bad | BlazeStealer Malware Hidden in Python Open-Source Packages Target Software Developers
Software developers are, once again, being targeted by threat actors through trojanized code libraries. Security research this week highlights at least eight developer tools published since January containing hidden payloads that are now reaching thousands of downloads.
So far, all eight in this series of packages have used Python programming language and are prefixed with the “pyobf” string to mimic genuine obfuscator tools like “pyobf2” and “pyobfuscator”. The latest in the string of malicious packages is called “pyobfgood”, which like its seven predecessors poses as a legitimate obfuscation tool for developers to defend against reverse engineering and code tampering.
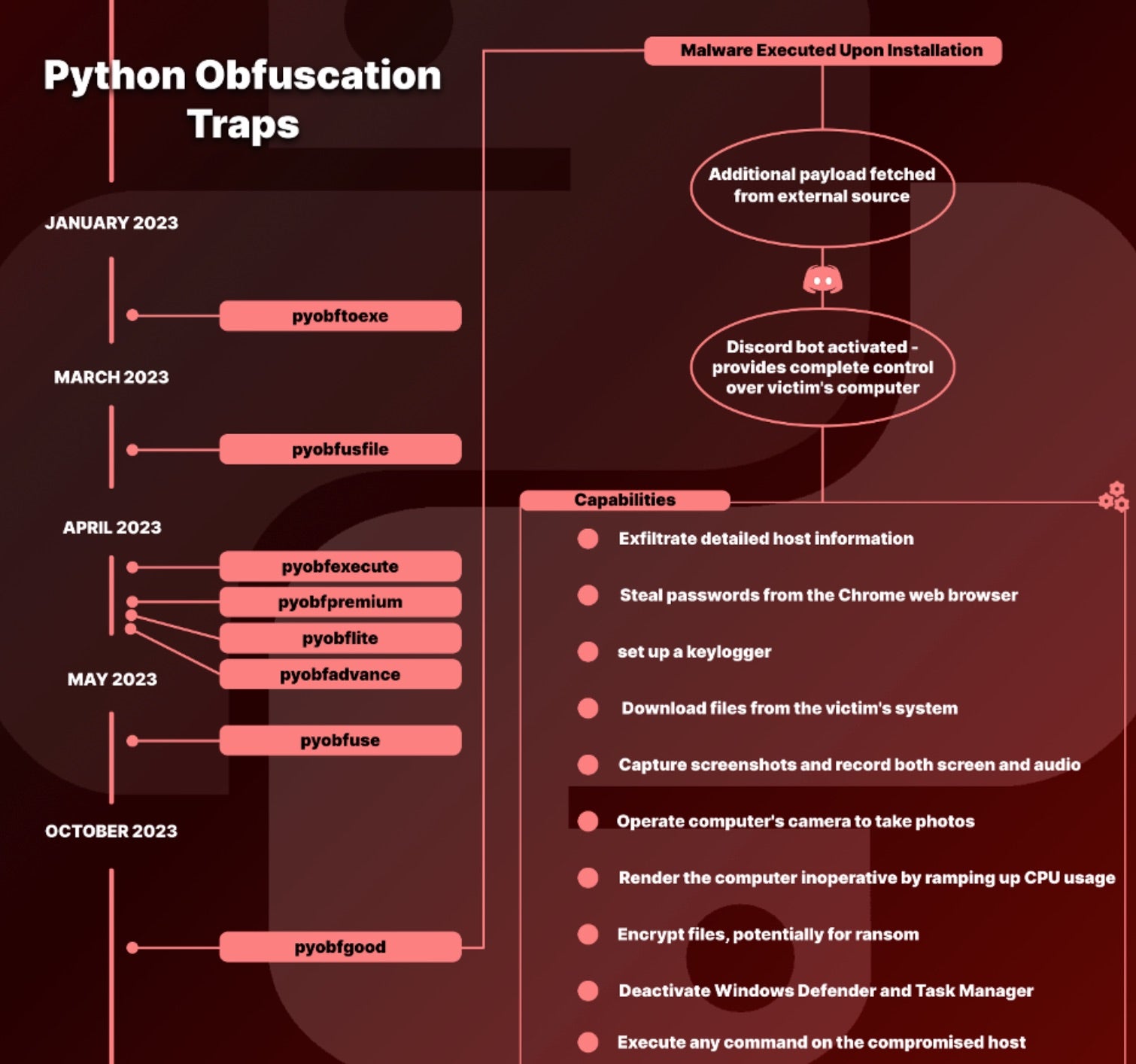
In the case of the “pyobfgood” package, malware called BlazeStealer is installed as soon as the unsuspecting developer runs the code, giving the threat actor capabilities such as exfiltrating detailed host information, setting up keyloggers, stealing passwords from web browsers, downloading sensitive files, recording both screen and audio, and encrypting files for potential ransom. A list of the malicious package names and indicators of compromise may be found here.
Developers remain a lucrative target for threat actors, given their work with both sensitive and valuable information. Open-source libraries also continue to draw attention. In late September, a 10.0-level vulnerability in the LibWebP image library was exploited in the wild, and just last month a flaw found in curl, a widely-used open-source command-line tool, was described as one of the most serious bugs found in the tool for some time.
For now, the Biden administration and CISA have placed an open call out for support in securing the nation’s open-source software and have several ongoing security initiatives for the broader open-source ecosystem.
The Ugly | SaaS Analytics Firm Advise API Key Resets After AWS Account is Compromised
After evidence of a breach surfaced last Friday, Sumo Logic officially disclosed the incident this week, notifying users that its Amazon Web Services (AWS) account was compromised using stolen credentials. The Californian data analytics firm has confirmed that its systems, networks, and customer data remain unaffected.

Upon detection, Sumo Logic was able to lock down the exposed infrastructure and rotate all potentially compromised credentials. So far, the company has implemented additional security measures such as enhanced monitoring and vulnerability scanning to help prevent similar occurrences in the future. Continuous monitoring of network and system logs is also ongoing to identify any signs of additional malicious activity.
In response to the breach, Sumo Logic has advised its customers to rotate credentials used for accessing its services as well as those shared with the company for accessing other systems. Specifically, customers were urged to reset API access keys, Sumo Logic-installed collector credentials, third-party credentials stored for data collection purposes, and user passwords to Sumo Logic accounts.
While an investigation is ongoing, regular updates are being posted in the company’s Security Response Center. Sumo Logic has also pushed out a playbook instructing customers on how to update their API keys. Known for its cloud-native SaaS analytics platform, the firm offers log analytics, infrastructure monitoring, and cloud infrastructure security to over 2000 customers including 23andMe, GoFundMe, Mattel, and SEGA.
Threat actors continue to keep AWS accounts in their sights due to the wealth of sensitive data and critical services hosted on the platform. As a major cloud service provider, it is seen as a springboard into a vast number of businesses, government agencies, and high-profile organizations.


