The Good
This week’s good news: attackers tossed lemons, and their victim made lemonade. First, the embarrassing bit: The august cybersecurity training body SANS Institute announced that it had been breached when an employee fell for a phishing attack.
On Tuesday, SANS said that the attackers got access to the worker’s Office 365 account and planted a suspicious email forwarding rule—one that was flagged during a systematic review of email configuration and rules. SANS said that the hackers forwarded 513 emails, some with personally identifiable information (PII) such as name, email, work title, company name and address, to a “suspicious” external email address. In total, about 28,000 PII records were exfiltrated.
Bad? Yes. But by week’s end, SANS had plans to turn it into a teachable moment by creating a webinar and training material based on the lessons it learned from the breach, CTO James Lyne explained: “We use any bump in the road as an opportunity to ask ourselves questions in retrospect of what we should have done differently. That’s exactly the process that we’re in the middle of now, because, clearly, if things had been better, we would not be in this situation. And you can always improve.”
Though SANS hasn’t released the name or job role of the responsible employee, it did say that they a) didn’t have access to sensitive or financial data and b) don’t teach at the institute.
In other good news this week, a U.S. Immigration and Customs Enforcement (ICE) investigation has led to the shutdown of thousands of fraudulent COVID-19 websites—the type that target people through financial fraud, import counterfeit pharmaceuticals and medical supplies, and that promise to sell in-demand products like hand sanitizer and disinfectant wipes, taking people’s money for things with no intention of delivering. Feds have seized over $3.2 million in illicit proceeds and made 11 arrests.
The Department of Justice has tips on avoiding these scams. Here’s more on Operation Stolen Promise and how to report COVID-19 fraud.
The Bad
A ReVoLTE-ing development: the mobile voice standard known as Long Term Evolution (LTE) was supposed to give us far better sound quality than previous generations, with up to three times the capacity of the earlier 3G standard and an extra layer of security, to boot. But researchers say that due to an implementation glitch in the LTE protocol, Voice over LTE (VoLTE) lets hackers eavesdrop on calls with only $7,000 worth of gear.
As described in a paper presented by the researchers at USENIX, the problem is usually found at the level of base stations, which in most cases either reuse the same stream cipher as encrypted calls or use predictable algorithms to generate the encryption key for voice calls. Due to this common, flawed implementation of VoLTE, attackers can convert cryptographically scrambled data into unencrypted sound. It’s easy: using a software radio, an attacker sniffs the encrypted radio traffic between, say, Alice and Bob, within the same, vulnerable base station. After the first call ends, the attacker calls Alice and talks with her—the longer, the better. For that second call, the attacker sniffs the encrypted radio traffic of Alice and records the unencrypted sound (known plaintext).
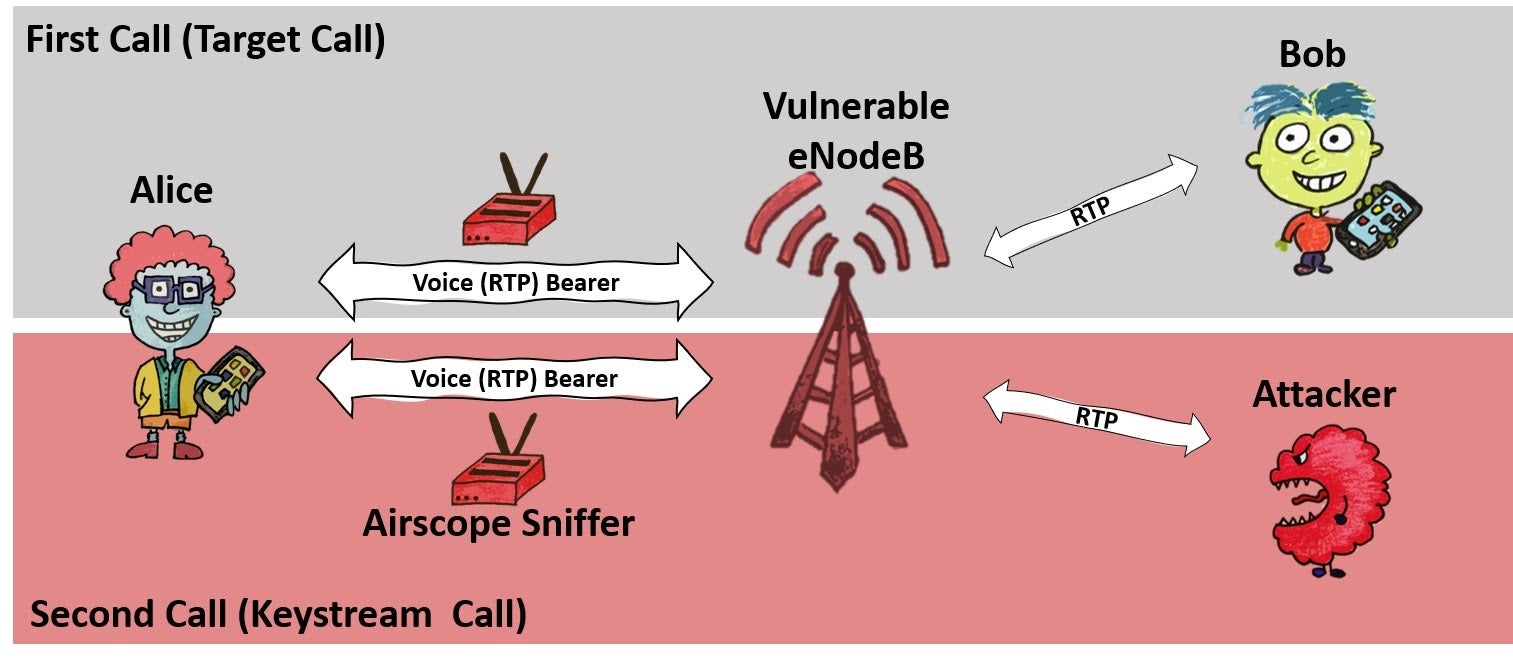
Here’s a demo of the attack, and here’s a site explaining it in detail, along with mitigation. Long story short: Germany’s fixed it, but it’s likely a problem everywhere else. On Wednesday, the researchers released an Android app that mobile operators can use to test their networks and base stations for the vulnerability. It’s open-source, and you can get it on GitHub.
The Ugly
Mozilla announced it’s slashing 250 jobs: about a quarter of its workforce. This won’t be good for development of its privacy-first Firefox browser, it says. CEO Mitchell Baker blamed the pandemic: “Economic conditions resulting from the global pandemic have significantly impacted our revenue,” he wrote. “As a result, our pre-COVID plan was no longer workable.”
In a memo sent to employees, Baker said that it will shutter its operations in Taipei, Taiwan. The workforce will also shrink in Canada, the US, Europe, Australia and New Zealand.
A slew of browser development is going to suffer, Baker wrote: “In order to refocus the Firefox organization on core browser growth through differentiated user experiences, we are reducing investment in some areas such as developer tools, internal tooling, and platform feature development, and transitioning adjacent security/privacy products to our New Products and Operations team.”
Those security/privacy products do a lot: the browser blocks a mess of undesirable online crud, including social-media trackers, cross-site tracking cookies, tracking code, fingerprinters and cryptominers.
Shortly after this news broke, Mozilla and Google announced a deal worth “mega-millions” that would keep Google as the default search engine on the browser.

Hopefully the deal will help keep the wolves from the door. Meanwhile, all we can do is wish Mozilla’s New Products and Operations team the best of luck in doing more with less. May security and privacy in this popular browser not slip in these trying times.



