The Good | Robbinhood Ransomware Operator Pleads Guilty & Cyber Scam Firm Sanctioned
U.S. authorities have taken actions against Robbinhood ransomware and Funnull Technology, two high-impact cybercriminal operations.
An Iranian national operating under Robbinhood has pleaded guilty to targeting U.S. cities and organizations, resulting in millions in loss between 2019 to 2024. Sina Gholinejad (aka Sina Ghaaf) and his conspirators infiltrated networks, often using admin credentials or exploiting vulnerabilities, to manually deploy ransomware to encrypt systems and demand Bitcoin payments. High-profile victims included the cities of Baltimore, Greenville, Gresham, and Yonkers, along with several healthcare and nonprofit organizations.
After an #FBI Charlotte investigation, an Iranian man plead guilty to his role in the use of Robbinhood Ransomware. Acting SAC James C. Barnacle Jr. highlights the reach of the FBI to cyber criminals no matter where they operate. @USAO_EDNChttps://t.co/Vx7WFBCMFI pic.twitter.com/lsYpF2WlQo
— FBI Charlotte (@FBICharlotte) May 27, 2025
Gholinejad used VPNs, cryptocurrency mixers, and European servers to mask his activity. He faces a maximum penalty of 30 years in prison for conspiracy to commit fraud, money laundering, extortion, and computer intrusion.
U.S. Treasury Department officials have sanctioned Funnull Technology, a Philippines-based company linked to over $200 million in American losses from virtual currency scams like romance baiting. Funnull enabled cybercriminals by selling IP addresses and hosting services that supported hundreds of thousands of malicious websites. Capitalizing on dating apps and social media to lure their victims, the scammers would convince victims into taking fake investments before stealing their funds.
Funnull also provided tools like domain generation algorithms, brand-impersonating web templates, and rapid domain/IP switching to avoid takedowns. The company’s administrator, Chinese national Liu Lizhi, was also sanctioned. In a report released by the FBI, the overall Funnull infrastructure supports over 332,000 domains, and IP migrations reveal coordinated cybercriminal activity. By increasing pressure on cybercriminal infrastructure and operators, law enforcement can continue to disrupt ransomware campaigns and online fraud both at scale and at their core.
The Bad | Go-Based Botnet ‘PumaBot’ Exploits Linux-Based IoT Devices via SSH Brute-Force
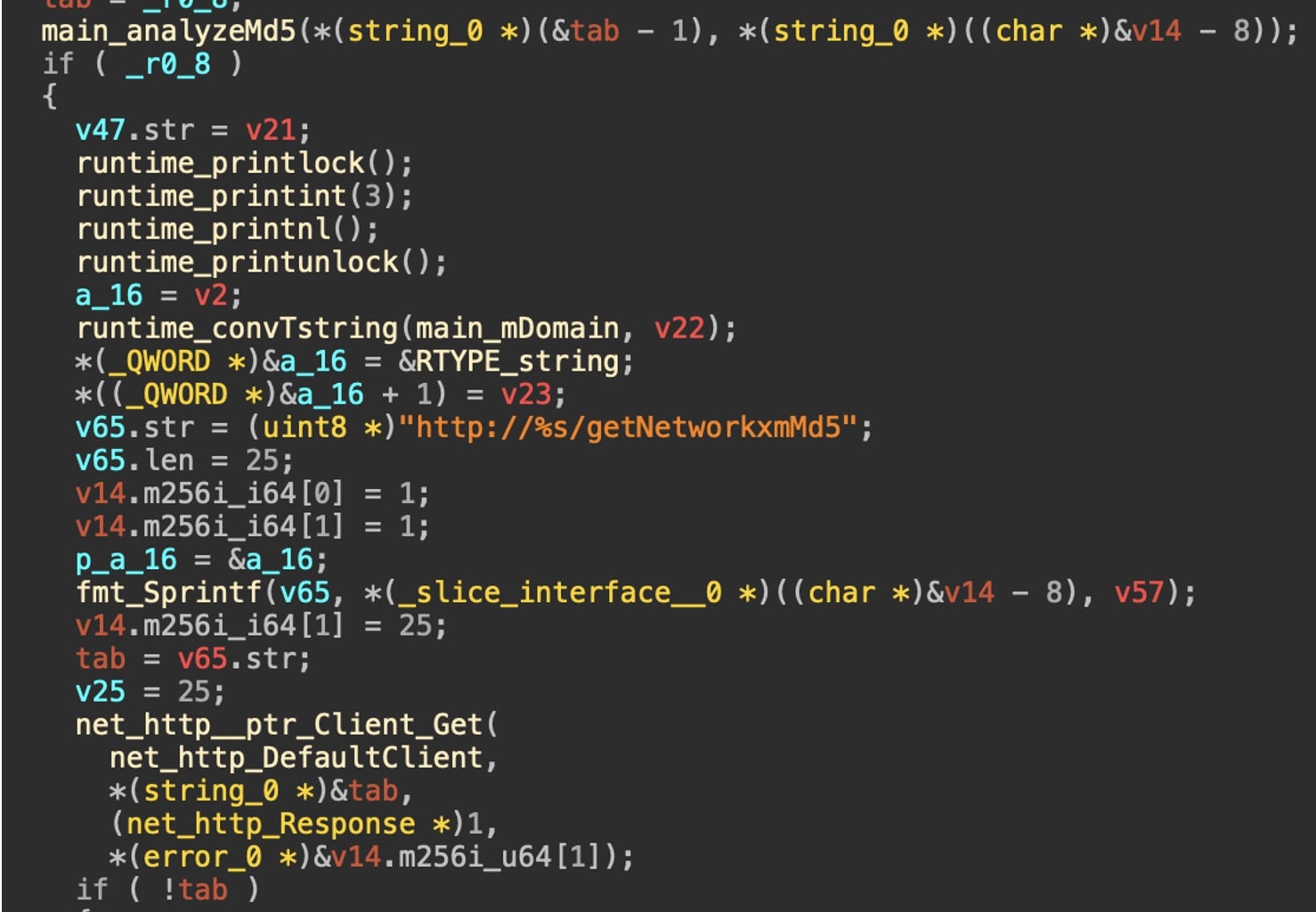
Threat actors are combining precision targeting with stealthy persistence with a newly uncovered Go-based malware named PumaBot. A Linux-based botnet, PumaBot attacks embedded IoT devices by brute-forcing SSH credentials on port 22. Unlike traditional botnets that perform broad scans of the internet, PumaBot pulls specific target IP lists from its command and control (C2) server (ssh.ddos-cc[.]org), pointing to a more strategic and selective infection method.
New findings on PumaBot note how it gains access by checking system identifiers like “Pumatronix”, likely targeting traffic and surveillance camera vendors, and executes uname -a to ensure the device isn’t a honeypot. After validation, it writes a binary to /lib/redis and creates a persistent systemd service such as redis.service or a misnamed mysqI.service to survive any reboots. It also inserts its SSH key into the authorized_keys file to retain access even if the main malware is removed.
PumaBot can receive C2 commands to install additional payloads, exfiltrate data, and support lateral movement. Payloads observed include custom scripts, PAM rootkits that harvest credentials by replacing pam_unix.so, and daemons that monitor and exfiltrate captured login credentials from /usr/bin/con.txt, wiping evidence afterward. Other components found that are thought to be part of a larger campaign include a Go backdoor, an SSH brute-force tool called networkxm, and shell scripts that further establish the malware.
Currently, PumaBot appears focused on deeper network infiltration and credential harvesting rather than traditional DDoS activity. To defend against such threats, organizations should update IoT firmware, eliminate default credentials, segment networks, limit SSH access, and monitor for abnormal login attempts and rogue system services.
The Ugly | DragonForce Ransomware Targets MSPs via RMM Exploits in Expanding Affiliate Model
Less than a month after DragonForce targeted major retailers across the U.K., the ransomware group has been observed exploiting three vulnerabilities in the SimpleHelp remote monitoring and management (RMM) platform to steal data and perform reconnaissance on downstream customer environments.
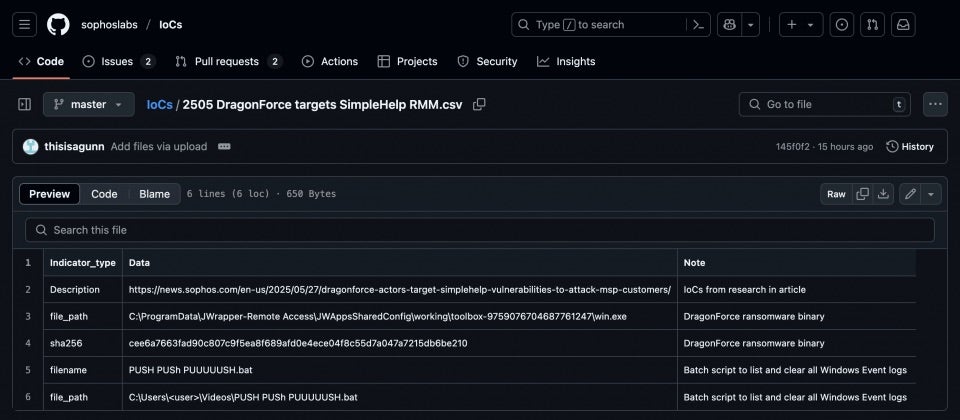
Researchers tracking this latest campaign observed DragonForce attackers leveraging CVE-2024-57726, CVE-2024-57727, CVE-2024-57728 to breach an MSP. They collected sensitive network, user, and configuration data before deploying encryptors on the service provider’s customer systems to enable double extortion schemes later on.
DragonForce has adopted a ‘white-label’ ransomware-as-a-service (RaaS) model, allowing affiliates to deploy customized versions of its encryptor under their own names. After openly recruiting on underground forums last year, its leak site listed 136 victims by March 2025. This affiliate-centric model, along with efforts to build a broader ‘cartel’, reflects the group’s ambition to dominate the post-LockBit ransomware ecosystem. Affiliates can leverage DragonForce’s infrastructure, including encryption tools, negotiation panels, Tor-based leak sites, and support services. The flexibility lowers the barrier for less sophisticated actors while appealing to advanced threat groups looking to avoid the overhead of managing their own platforms.
This recent attack reiterates just how high-value MSPs are as targets. To threat actors, gaining access to one means cascading into multiple downstream victims. As seen in cases with SimpleHelp, ConnectWise, ScreenConnect, and Kaseya, which are all widely used in MSP environments, actors continue to focus on breaching MSPs to maximize the scale and impact of each of their campaigns. With growing abuse of AI in malware development, an increased decentralization and competition among threat actors, the threat landscape remains volatile.


