The Good
Nigerian authorities have arrested a 37-year-old man alleged to be the leader of the SilverTerrier (Team TMT) business email compromise gang.
Interpol announced the arrest on Wednesday, and detailed how Interpol’s Africa Desk, AFJOC (African Joint Operation against Cybercrime), Nigerian law enforcement, and other private sector partners successfully tracked and apprehended the suspect.
Interpol and Group-IB announce the arrest of a 37yo Nigerian man, leader of the SilverTerrier (Team TMT) BEC ganghttps://t.co/mDGcCCcpUhhttps://t.co/lOPAXUXQBD pic.twitter.com/Soa4iAwP5p
— Catalin Cimpanu (@campuscodi) May 25, 2022
According to the statement, Operation Delilah began in May 2021, led by Nigerian police with three Interpol partners offering intelligence to the AFJOC.
Public and industrial analysts from Interpol’s Cyber Fusion Centre enriched the intelligence before referring it to the Nigerian police. Australian, Canadian and American law enforcement also supported the investigation by participating in several case-coordinating meetings.
With support from a private sector firm, investigators mapped out and tracked the suspect’s online activities and physical travel before police made the arrest at Murtala Mohammed International Airport in Lagos.
In their statements, Interpol officials expressed their hope that the operation would “stand as a reminder to cyber criminals across the world that law enforcement will continue to pursue them, and that this arrest will bring comfort to victims of the suspect’s alleged campaigns.”
This operation offers encouraging signs that governments and law enforcement officials across the world are taking notice of escalating cyber crime and proactively taking action to investigate and neutralize major threats. While the road ahead is a long one, the international investment displayed here, and the cooperation of major vendors in the private sector, is a great first step towards a safer cybersecurity landscape.
The Bad
This week, details emerged of an attack chain against Zoom clients that potentially left all Zoom users exposed to a zero-click vulnerability. Several bugs were discovered by a security researcher in February and Zoom released a patch in late April. All Zoom users are urged to ensure they update to version 5.10.0 if they have not already done so.
According to Zoom’s advisory, CVE-2022-22784 could allow an attacker to break out of the current XMPP message context and force a user’s client to perform a variety of malicious actions.
The same researcher also identified CVE-2022-22785, a vulnerability that allows threat actors to send user session cookies to a domain outside of Zoom, which leaves users open to spoofing attacks, and CVE-2022-22786, which allows an attacker to trick a user into downgrading their Zoom client to a less secure version.
Chaining the vulnerabilities together could allow an attacker to achieve remote code execution (RCE) without any user interaction.

Explaining the attack chain, Ivan Fratric, the Google Project Zero researcher responsible for discovering the bugs, said “The only ability an attacker needs is to be able to send messages to the victim over Zoom chat over XMPP protocol”.
He went on to explain that a threat actor could trick a targeted Zoom client into connecting into a man-in-the-middle server that downgrades a target’s Zoom client to a version from 2019.
These RCE attacks are possible because Zoom’s clients and servers use different XML parsing libraries, which means they also parse XMPP messages differently.
Although Zoom patched its servers against these vulnerabilities when they were first discovered in February, the client patch was only recently released. Zoom users that haven’t updated yet should patch their clients immediately to mitigate the risk.
The Ugly
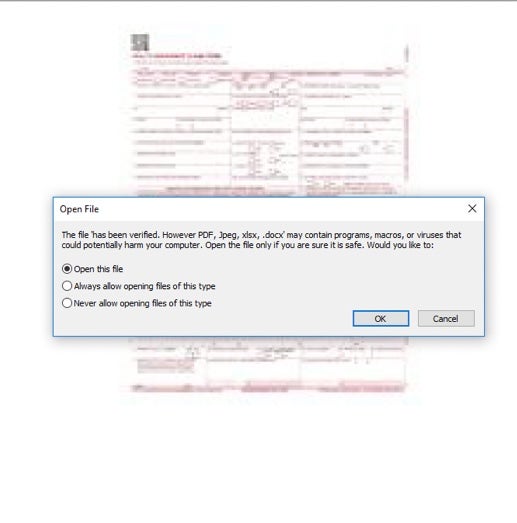
HP’s security researchers are observing a malware campaign that leverages malicious PDFs to target Window PCs with malware through a code-execution vulnerability in MS Office that was discovered four years ago.
According to HP’s threat intelligence, threat actors trick targets into opening malicious emails and a PDF document labelled as a remittance invoice. Once the victim opens the document, the PDF file will load a fake Adobe Reader prompt designed to look legitimate and prompt users to open a malicious Word document.
Ultimately, this attack chain is designed to deliver an executable from the Snake keylogger family, which steals information from targeted users.
While malicious PDFs are hardly new, in recent years cyber criminals have primarily exploited Word documents or Excel sheets to infect machines with malware. However, researchers believe that the PDF format’s relative scarcity in today’s threat landscape is not only due to widespread awareness of Microsoft Office files but also to the belief that other document formats serve as better social engineering lures.
The existence of malicious documents like these is truly disruptive to vulnerable users and reminds us that not every emerging threat is cutting edge—older threats can still wreak just as serious damage.