The Good
International crime rings are responsible for the worst type of criminal activities. Perhaps the most hideous of these is Child Sexual Exploitation and Abuse. The internet in general, and the dark web in particular, has allowed the “consumers” (pedophiles, sex offenders) and the “producers” to interact in a stealthy manner, and to escape the long hand of law enforcement agencies. Moreover, since these crimes involve multiple geographies it was assumed that the chances of perpetrators being caught and brought to justice were slim. That’s why we are so pleased to hear that member states of the “Five Eyes” (Australia, Canada, New Zealand, the UK, and the US ) and six major tech firms (Facebook, Google, Microsoft, Roblox, Snap and Twitter) are working together to combat online child exploitation and abuse. This week, the tech firms signed up to implementing a new framework, published in the document “Voluntary Principles to Counter Online Child Sexual Exploitation and Abuse”, across all their platforms.
The framework consists of 11 principles grouped into seven categories; together, they aim to reduce the potential malicious use of social media and internet technologies to search for and distribute such materials. Cooperation between tech giants and law enforcement agencies is not trivial, and we hope it will foster an atmosphere of trust and information sharing that will have a substantial impact on reducing if not eliminating the very worst kind of all cyber crimes.

Indeed, while international cooperation is imperative for fighting global criminal activities in general, alone it’s not enough. When it comes to battling cyber crime and offensive cyber activities, speed and knowledge sharing are of the essence. This is why Estonia, Lithuania, Croatia, Poland, the Netherlands and Romania have joined forces and agreed to create European Union Cyber Rapid Response Teams (CRRTs), led by Lithuania. The CRRT teams will be ready to intervene in the “neutralization and investigation of dangerous cyber incidents virtually or, if necessary, physically,” the Lithuanian Defense Ministry said in a press release. A great week for the good guys.
The Bad
It is almost two years since the introduction of GDPR (May 2018), but it seems that some companies have yet to grasp the full damage resulting from data breaches. The regulation was intended to improve the state of data security and privacy, but judging by recent events, it seems that companies still need more time to implement the right safeguards or that they have chosen to simply pay the associated fines instead of achieving high levels of security to prevent such breaches. Carrier T-Mobile has announced a data breach that exposed personal and financial information of some of its customers. The breach was caused by an email vendor being hacked, and the data leak contained social security numbers, financial information, government ID numbers, billing information, and rate plans. Affected customers were informed via text message.
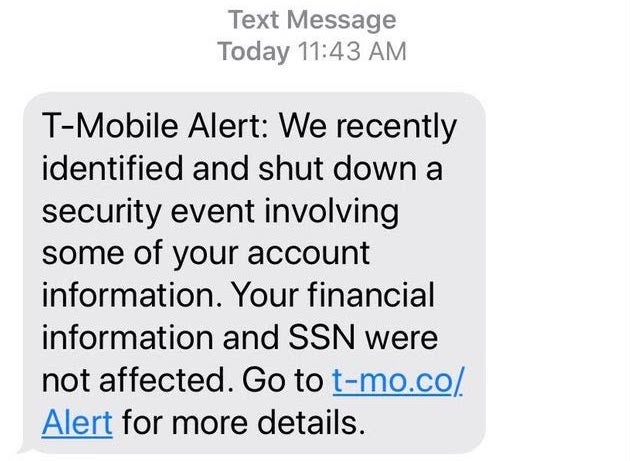
This is not the first time T-Mobile has suffered such an incident. The previous one happened less than 2 years ago. Not to be outdone, the British media giant Virgin Media has announced that a massive database, containing the personal details of 900,000 people, was left unsecured and accessible online for 10 months. During this time, it was accessed at least once. Not that it took any hacking skills to do it; the company admits that the database was not protected due to human error which led to “misconfiguration”. It was compiled for marketing purposes and contained phone numbers, home and email addresses.
The Ugly
The world seems to be in turmoil nowadays, with more and more countries entering the “Corona Impact Zone”. As if that wasn’t bad enough, there will always be people who try to capitalize from the situation. And where best to test and gain from this epidemic than in Italy, the country hit the hardest (so far) outside of Asia.
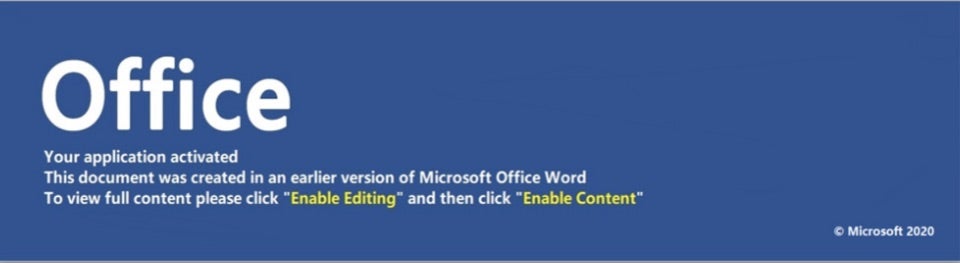
A recent malware campaign reached about 10% of all the organizations in Italy by disguising a malicious attachment as an official document by the World Health Organization containing all the necessary precautions to take against coronavirus infection.
Opening the document results in a request to “Enable Editing” and “Enable Content”. If granted, the TrickBot banking trojan installs itself on the user’s machine. It is yet another example of how cybercriminals will cynically exploit whatever opportunity comes their way. The good news is that unlike the actual virus, this pest can easily be avoided by practicing good cyber hygiene.