
The Good
The MAZE group actors found themselves lost in their own “maze” yesterday, Thursday, Jan 2, 2020. Their public shaming website was taken down along with the entire platform it was hosted on in Cork, Ireland at World Hosting Farm.
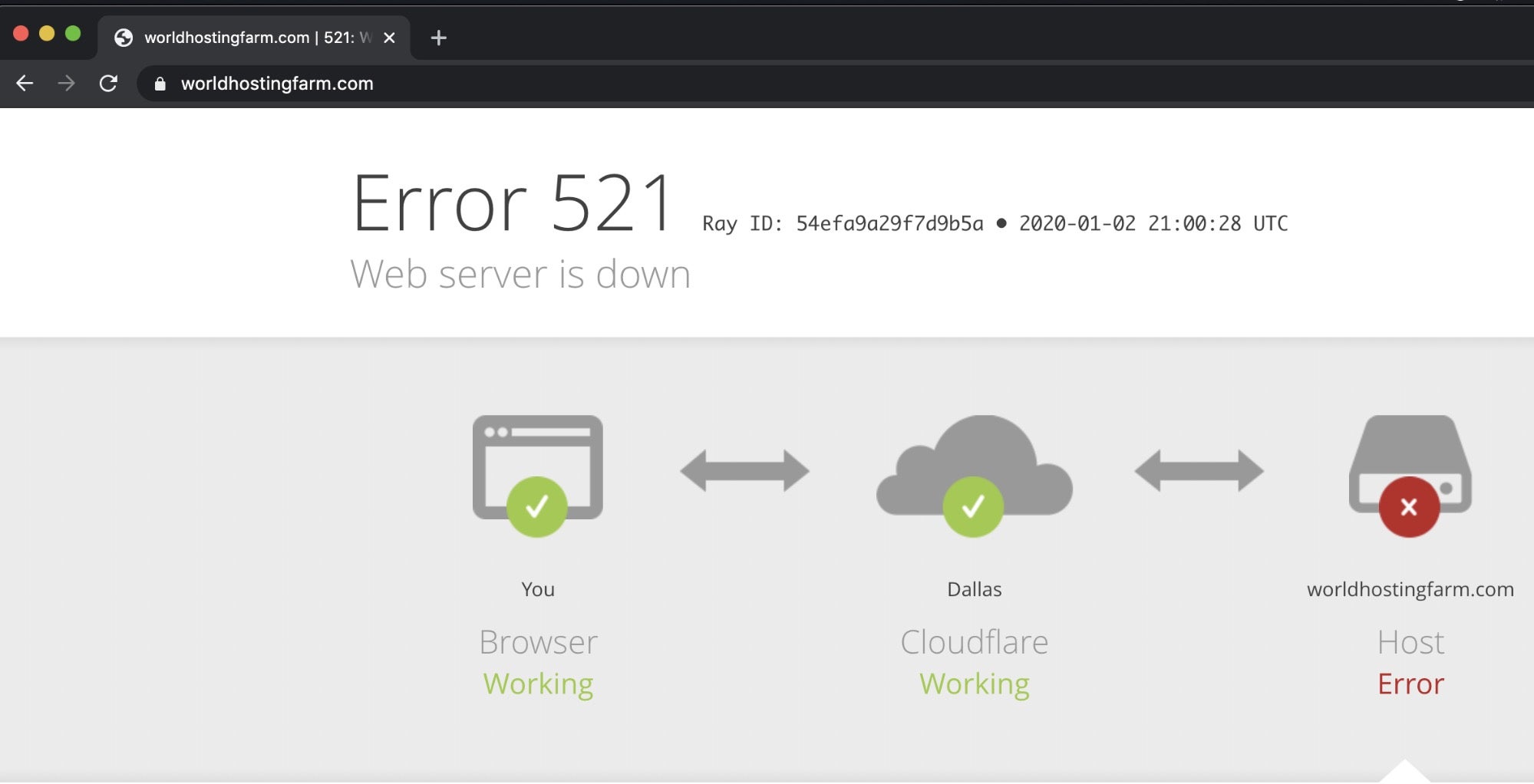
World Hosting Farm appears to have been a possible front for the bad guys (not a legitimate ISP in other words) and is host to many known malicious address ranges:
This comes on the heels of news from earlier in the week when one of Maze’s victims from several weeks ago, a US firm Southwire, was able to gain a secure emergency High Court injunction against two likely Polish nationals and the ISP front company that was just taken down. It is great to see a cross-border injunction granted, and even better to see the website and malicious ISP taken down. This development helps remove a portion of leverage the MAZE extortionists have upon past and future victims.
The Bad
The restaurant group, Landry’s (over 600 famous eateries like Morton’s, McCormick & Schmick’s, Mastro’s, and Joe’s Crab Shack, for example) had an awkward PCI breach this week. Even though their credit card POS systems used end-to-end encryption to prevent malware from being able to scrape card data, it turns out Landry’s Select Club reward card swipe systems did not, and employees were sometimes swiping customer’s credit cards with rewards readers instead. Malware found on reward card order entry systems was able to read the credit card data when employees swiped them!

Landry’s alerted their customers on their website, letting customers know the activity has been on-going for about a year. No word yet on how many credit cards were compromised.
The Ugly
The City of New Orleans gave an update on it’s recovery status on the heels of their December 14th ransomware attack. The attack took out all 3,400 systems which were connected to the network. 2,658 systems have been restored over the last two and a half weeks, however, eight of the city’s agencies have yet to be restored from backup.
Manual processes are still being used and restoring Public Safety systems, including the NOPD’s EPP and body camera footage, remains the top priority. These systems should be restored by next Monday, January 6th, after three weeks of downtime. Meanwhile, the city hopes to be able to allow property taxes to be paid no later than January 31, a month and a half after the attack began. To give an idea on the level of effort it’s taken so far, over 75 people have been working full time since December 14th on the breach. This represents over 10,000 hours for just the additional 75 people involved. Additionally, up to 20% of the city’s computing assets will not be usable on the newly-restored network, though the reason for this was not mentioned. Perhaps this is the percentage of assets for which data could not be recovered
While the city has turned over relevant data to the FBI, it was not willing to name the type of ransomware used in the attack or speculate who (or what nation state, perhaps) is behind the attack. Earlier reports based on files that were uploaded to VirusTotal pointed to Ryuk:
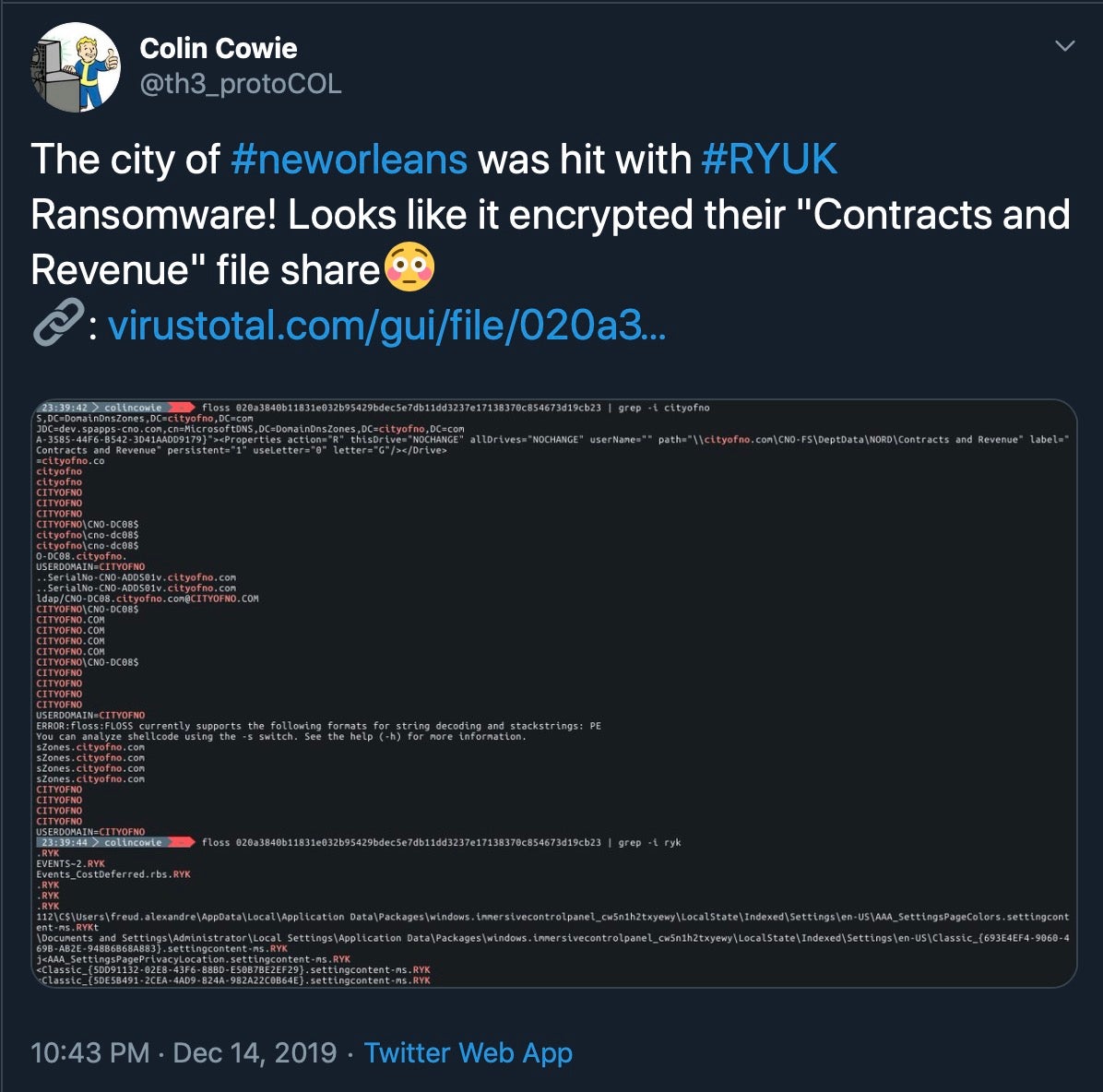
based on strings from this sample, it was seemingly taken from the computer owned by the city’s IT Security Manager:
So there you have it, this week’s UGLY: cities, counties, and schools keep getting debilitated from ransomware, and it’s taking weeks and months to recover.

