Phishing continues to plague organizations, and many people don’t know how it works. Knowing how to avoid phishing is as essential as being aware of the latest scams. As attackers get crafty with their communications, users must educate themselves and get smarter.
This guide will break down how phishing attacks work. You will know how to report a phishing email, detect such schemes, and what you can do to counter them. Let’s get started.

What is Phishing?
Phishing is crafting a legitimate-looking email that convinces a reader that it comes from an official or verified source. Such email messages aim to persuade the victim to act urgently or carry out authorized actions. For example, imagine you are the hacker but pose as the CEO of a company.
You request an employee to send you their account details and want to reward them for doing a good job. Maybe even recognize them as ‘employee of the month.’ The employee, not knowing you are a scammer, because they are new, becomes gullible and shares their account details in response to your email. Then, you, the hacker, hijack his account by combining those credentials with any other sensitive info you harvested by reconfiguring the organization before targeting them.
This was spear phishing in action, but phishing emails are usually sent in bulk. You may email multiple employees and request their confidential information as a requirement for a survey or an upcoming campaign.
Why are Phishing Attacks So Effective?
Phishing attacks are effective because they are personalized, thought-provoking, and convincing. They are not limited to email; attackers put a new spin on their strategy. The idea behind phishing is that it uses bait or a hook. You, the victim, who is being phished (think of yourself as the fish), get pulled out and forced into revealing sensitive info, which is later used against you.
What does phishing mean? Another example of a phishing attack is a cloned website. The attacker could duplicate your organization’s platform by using AI to code the fake website. They can copy every detail, even design logos, but only change the domain name. For example, if your company is aramca.com, the attacker’s website would be something like aramca.co
So, any traffic directed to their official website would be misdirected to yours. If anyone clicks on links or submits information via forms on the fake website, the attacker will have direct access to all those details online.
How Do Phishing Scams Work?
Phishing scams work by making you think something is wrong and prompting you to take action to fix the problem. Or, in other times, they include offers that are too good to be true and make them simply irresistible to ignore. There’s no formula or strategy behind them, which makes these scams so scary. And they can be very unpredictable.
Usually, phishing scams are noted by suspicious login attempts. They might ask to share personal information or make some form of payment online. They can also issue free coupons to redeem or fake order confirmations. Most phishing scams are generic, but they are a social engineering threat.
Common Types of Phishing Attacks
One of the most recent reports from the Anti-Phishing Working Group (APWG) showed that phishing campaigns targeting brands have been steadily increasing. The report notes that phishing scams are increasingly hosted on HTTPS websites, with nearly half of all phishing sites now using the secure protocol. These will not trigger warnings from mechanisms like Chrome’s not secure tab, and their content is invisible to legacy AV solutions, which cannot read encrypted traffic.
Many phishing scams will attempt to impersonate a vendor the victim is familiar with, like this fake Spotify subscription message:

Then there’s homographic attacks in which scammers register sites with Unicode characters that are visually similar to the ASCII characters used in the name of a genuine site. Compare these two Unicode strings:
u0430u0440u0440u04CFu0435
u0061u0070u0070u006Cu0065
And their visual “printed” form, shown on the right in the image below:
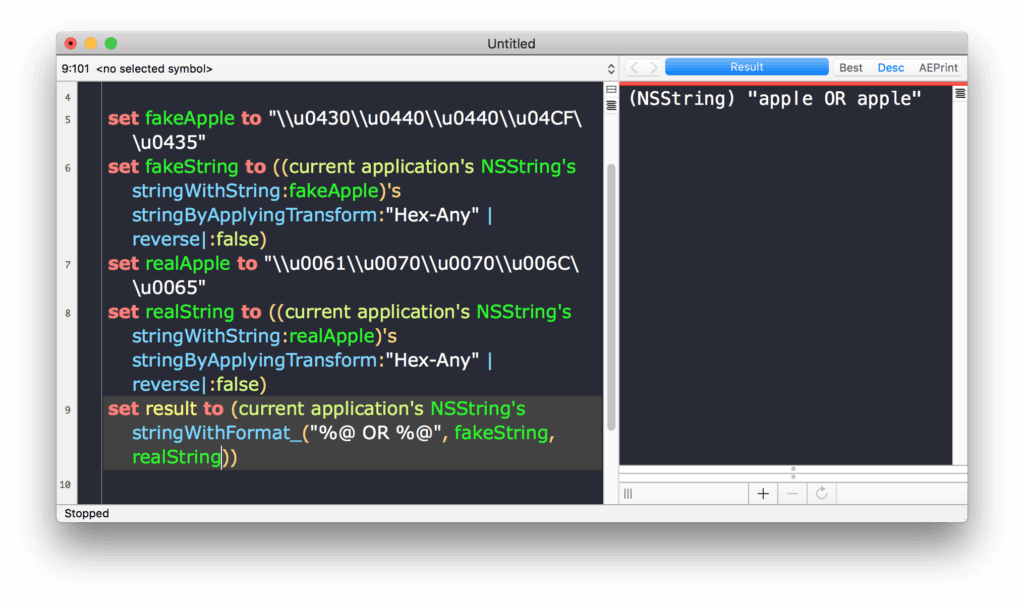
These two encodings may look similar to the human eye, but the computer reads them differently. If the first were used in a domain name registration, it would point to a completely different site than the second. Fortunately, most modern browsers can recognize this kind of attack, but vulnerabilities in Chrome, Firefox, and Opera as recently as last year could bypass those browsers’ homomorphic protection filters.
In a more recent attack, scammers used a real subdomain of Google.com, sites.google.com, to host webpages that then redirected victims to malicious sites.
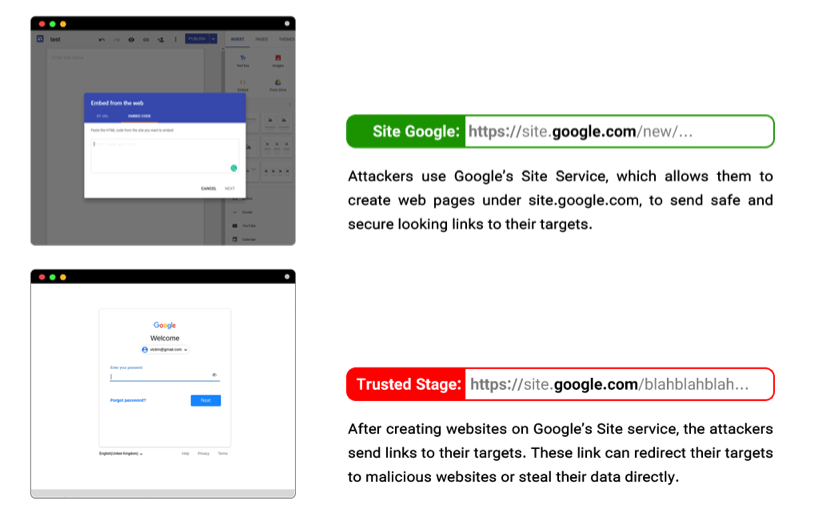
Once the victim has been hooked, the scam could involve any number of ruses, from fraudulent tech support scams to fake email sign-in pages. A common tactic is to tell the victim that they need to update their email account and then provide a reasonably convincing spoof site:
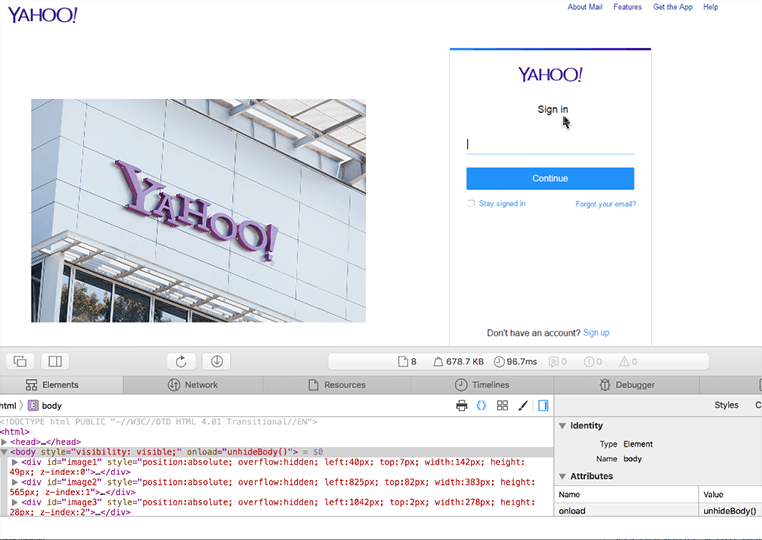
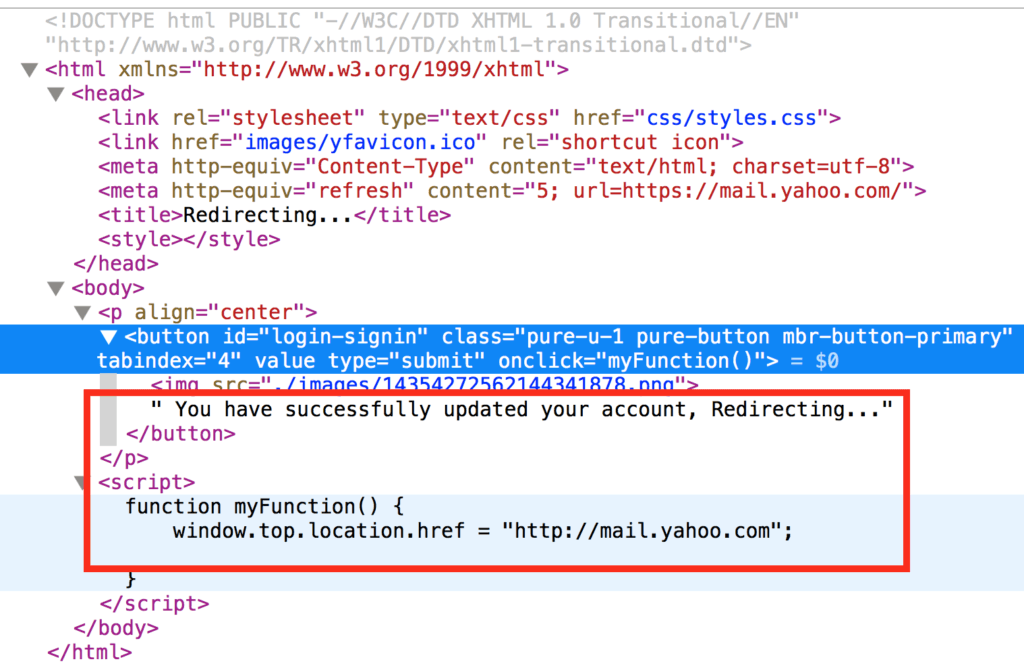
However, examining the code behind the site will show it for what it is: an attempt to steal the user’s login credentials. After the user enters their credentials in the fake site, the code redirects them to the real site.
Spear-phishing campaigns targeting the enterprise may seek intellectual property for industrial or nation-state espionage. A UK engineering company, for example, was recently targeted in a spear-phishing campaign designed to steal secrets about its maritime technology, possibly for a Chinese-backed APT group. These are some of the most common types of phishing attacks.
 Enhance Your Threat Intelligence
Enhance Your Threat Intelligence
See how the SentinelOne threat-hunting service WatchTower can surface greater insights and help you outpace attacks.
Learn MoreSigns You’re Being Targeted by a Phishing Attack
So, how do you know that phishing attacks are targeting you? Here’s how:
- Someone unknown in the organization initiates a request for sharing sensitive information.
- Employees ask for a special request outside their usual work timings or schedule at any odd hour of the day. You get invited to perform activities that fall beyond the scope of your work, or need to do “additional work.”
- Don’t read the email you receive. Look at the sender’s address. It appears to come from a different or unfamiliar domain.
- An attacker asks you to verify your account again when you’ve clearly verified it before as part of your onboarding process. They may hide malicious links behind the verification button in the email or message.
- The email contains many spelling or grammatical mistakes that are too obvious (in this case, the attacker is a foreigner).
- The attacker may ask you to complete a survey or share your opinion by visiting another website and sharing a link. They may also ask you to call a number to engage personally with them off-record.
How to Detect Phishing Attempts Early?
One of the dead giveaways of a phishing attempt is the use of emotional triggers or overly sensitive language.
Here are some questions you should ask yourself to know if it’s a phishing attack incoming and how to detect it early:
- Is the sender sending a message in a format you are not familiar with or outside the norm of the organization?
- Does the email ask you to download malicious files? When you hover over links, do the links look different than what’s displayed in the text?
- Does the email contain typos or reference any individuals you don’t recognize?
- Does the email come from a public domain (like Gmail), but the attacker claims it’s an official company email?
- Is the email filled with threats or consequences, or does it ask you to act immediately before the situation could potentially escalate?
If you answered yes to any of these questions, then your answer is to detect it early. When detecting these threats, your best friend is your intuition and personal sense of judgment.
How to Prevent Phishing Attacks and Scams?
Here’s how you can prevent them:
- Block phishing with sophisticated email filtering software that blocks malicious senders and real-time scanning of links.
- Activate SPF, DKIM, and DMARC protocols to authenticate email and limit spoofing.
- Install endpoint protection platforms such as SentinelOne’s Singularity XDR to identify malicious processes before they are executed.
- Educate employees to recognize misspelled words, mismatched sender domains, and unwanted attachments. Installing an application allows listing to prevent unauthorized software from running.
- Manage user privileges regularly to block sensitive system access.
- Multi-factor authentication (MFA) provides a vital layer of protection on all accounts, particularly admin accounts.
- Monitor network traffic for abnormal activity such as unexpected outbound connections, which might represent data exfiltration attempts.
How to Mitigate the Impact of a Phishing Attack?
If a successful phishing attack occurs, remove infected devices immediately to prevent malware from spreading. Use pre-configured incident response playbooks to lock down the affected accounts and remove access tokens.
Perform forensic analysis to discover attack vectors, map out scheduled tasks, and any other registry modifications. You should also alert affected users to reset passwords and turn on MFA across the organization. Report the incident to organizations such as CISA or the FBI’s IC3 to assist with investigations. Update your security policies to remedy gaps, such as enforcing stricter email attachment policies and disabling macro execution by default.
Challenges in Defending Against Phishing Attacks
Phishing is tricky to defend against since attackers keep changing their tactics. You don’t know how much research the attacker has done on you or the team before they craft and send personal messages for active engagement. Polymorphic malware bypasses signature-based detection, and AI-generated content can help them match corporate tone. Limited IT resources cause patch delays and unforeseen vulnerabilities. Attackers can spread false information and interfere with communications by misleading or misdirecting others. Phishing campaigns follow no predictable patterns.
Best Practices to Protect Against Phishing
Here are the best practices to defend against phishing:
- Use email phishing filters and install the best anti-virus and anti-spam software. Pop-up blockers can also help. These are basic security measures that should be kept in place.
- Build a Zero Trust security architecture and authenticate all access requests, regardless of their source. Partition networks to restrict lateral movement attackers breach one segment, they cannot pivot to high-value assets.
- Incorporate deception technology like honeytokens to notify when attackers interact with fake credentials.
- Use threat intelligence feeds to block known bad IPs and domains ahead of time.
- Automate vulnerability scans to identify unpatched applications and misconfigured services.
- Encrypt sensitive data at rest and in transit to render stolen data unusable.
- Use SentinelOne’s managed detection and response (MDR) services for 24/7 monitoring and rapid containment.
Phishing Awareness Training for Employees
One of the best ways you can test your team’s knowledge is to send out fake invoices. See who can spot the difference. Reward those who can successfully identify phishing invoices and phony payment requests. Conduct regular simulated phishing campaigns with SentinelOne solutions to measure employee awareness. Update scenarios from time to time to reflect current threats. Engage your employees by trying phony IT support emails or invoice impersonation.
Integrate training with your SIEM to correlate phishing with login anomalies-for example, flag logins from new sources after an opened phishing email. Train personnel to verify requests through alternative sources, i.e., call a confirmed number before transferring money. Change training modules quarterly to cover new tactics, i.e., QR code phishing (quishing) or voice deepfakes. Conduct regular simulated phishing campaigns with SentinelOne solutions to measure employee awareness.
Real-World Examples of Phishing Scams
In the latest news, cybercriminals used digital twins to scam crypto users. They infiltrated online communities and impersonated several users by creating synthetic identities. They then manipulated digital systems and users online for financial gain.
Indiana has been ranked #2 as one of the top phishing victims. Phishers lure victims and scam them by sending notifications about fake packaging issues and delivery delays. They impersonated UPS and U.S. Postal Service officials. Japan also had an explosion of phishing scams and lost USD 700 million in trade. Rakuten Securities Inc. reported multiple fraudulent transactions as of late March 2025.
How can SentinelOne help?
SentinelOne’s endpoint agents use application allowlisting, preventing unauthorized payloads from executing. Real-time forensics provides attack timelines to IR teams, and automated scripts quarantine endpoints and reinstate tokens. To offer a layered defense, you can integrate with email management gateways like Mimecast to quarantine phishing emails containing malicious links.
SentinelOne’s behavioral engine tracks all system activities across environments, detecting techniques and tactics that indicate malicious behavior and automatically correlates related activity into unified alerts. With SentinelOne DeepVisibility, you can see how users are affected and even scan through encrypted traffic. It will allow your team to understand the security incidents better, monitor phishing attempts on your users, identify data leakage, and ensure cross-protection. These simple interfaces will enable you to automate and connect them to other products in your portfolio.
Conclusion
You know what a phishing attack is. You have also learned how to prevent phishing attacks, so now you are better prepared to face the challenges of tomorrow. Remember that combating phishing scams means proactively approaching your email and site security. Attackers can phish you through apps, social media channels, and any other online platform or opportunity they can identify and exploit. Think outside the box, expand your security coverage, and stay protected with SentinelOne. Contact us for further assistance.
FAQs
A phishing scam is a type of cyberattack where criminals send fraudulent emails, text messages, or set up fake websites that look legitimate. They try to trick you into sharing sensitive information like passwords, credit card numbers, or installing malware. These attacks use social engineering to manipulate you into taking harmful actions. If you receive unexpected requests for personal data, you should be suspicious immediately. Phishing is currently the most common type of cybercrime reported to the FBI.
Phishing is a social engineering attack that tricks people into revealing sensitive information or downloading malware. Attackers pretend to be trustworthy sources like banks, companies, or colleagues. They will send you messages with urgent requests, fake deals, or alarming notifications to make you act quickly without thinking. You can spot phishing by checking sender details and suspicious links. Phishing got its name in 1995 and has become the leading method for cybercriminals to steal information.
Anyone can be a target of phishing attacks. Cybercriminals go after individuals, businesses, and organizations of all sizes. They will specifically target employees with access to sensitive data, C-level executives (whale phishing), and system administrators. You might be targeted based on where you work or what access you have. Phishers also launch widespread campaigns against customers of popular services like Amazon, especially during sales events like Prime Day.
You can spot phishing emails by looking for these telltale signs: They ask for sensitive information like passwords or credit card details. The sender’s email domain doesn’t match the company they claim to be from. Links in the email go to suspicious websites – hover over them to check. They contain unsolicited attachments. The message isn’t personalized and uses poor grammar. They create fake urgency to panic you into action.
There are several types of phishing attacks you need to watch out for. Email phishing uses fake emails to trick large groups of people, while spear phishing targets specific individuals with personalized messages. Whaling focuses on executives and high-value targets. Business Email Compromise (BEC) tricks employees into transferring money or data. Smishing uses SMS text messages, and vishing happens over phone calls.
Organizations can prevent phishing by implementing multi-factor authentication using apps like Microsoft Authenticator or physical tokens. They should also regularly update and patch all systems to fix vulnerabilities, train their employees to identify and report suspicious emails, and set up regular security audits to find network weaknesses. They must create and test backup plans and store data in secure off-site locations. Regular monitoring of network traffic will help them spot unusual activities.
Antivirus software alone cannot stop all phishing attacks. There’s been a decline in antivirus effectiveness against modern threats like fileless attacks. If you rely only on antivirus, you miss half of all threats. Many attackers change malware signatures frequently or use zero-day exploits, bypassing traditional security tools.
Yes, phishing attacks are increasing significantly. During the COVID-19 pandemic, phishing incidents rose, and they have gone up year-on-year since then. Criminals adapt their tactics to current events and trends. They increasingly use encryption on phishing sites, with a majority using valid HTTPS certificates to look legitimate and trick you into trusting them.
If you’ve clicked a phishing link, don’t provide any information when prompted. Disconnect your device from the internet immediately to stop malware from spreading or data transmission. You should run a full system scan with security software. Change your passwords for all accounts, especially if you entered credentials. Report the phishing attempt to your IT department if at work. You must monitor your accounts for unusual activity and consider freezing your credit if financial information was compromised.
You can avoid phishing by checking email sender addresses carefully before clicking links. Never give out personal information through email or unexpected pop-ups. If you get an urgent message, verify it by calling the company directly using their official number. You should keep your devices updated with security patches. Use multi-factor authentication for all critical accounts. Before clicking, hover over links to see their proper destination. Check for HTTPS in the website address and look for spelling errors on sites.

