Active Directory misconfigurations can lead to total domain compromise of an organization. Once an attacker gets a foothold on a compromised network, it can discover AD misconfigurations and gain higher-level privileges to access the domain.
A typical Kerberos authentication attack scenario originates from an unconstrained delegation, where attackers identify misconfigurations and steal authentication information, such as password hashes, Kerberos tickets, and application access tokens. Attackers can escalate higher privileges and move laterally within an organization’s IT infrastructure to target high-value assets.
This post discusses what a delegation is, how attackers escalate unconstrained delegation exposure, and what security measures every organization should implement to protect itself.

What is Active Directory Delegation?
Delegation is an Active Directory feature for when a user or computer account needs to impersonate another account. For example, when a user calls a web application hosted on the web server, the application can impersonate the user credentials to access resources hosted on a different server, such as a database server. Any domain computers with unconstrained delegation enabled can impersonate user credentials to any service in the domain.
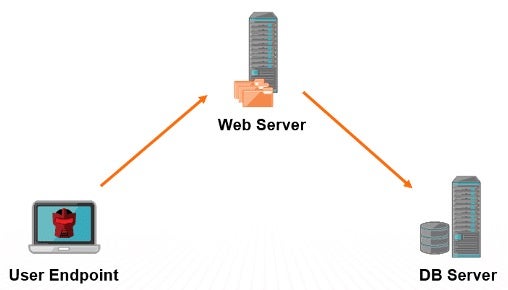
How Attackers Escalate Higher Privileges With Unconstrained Delegation
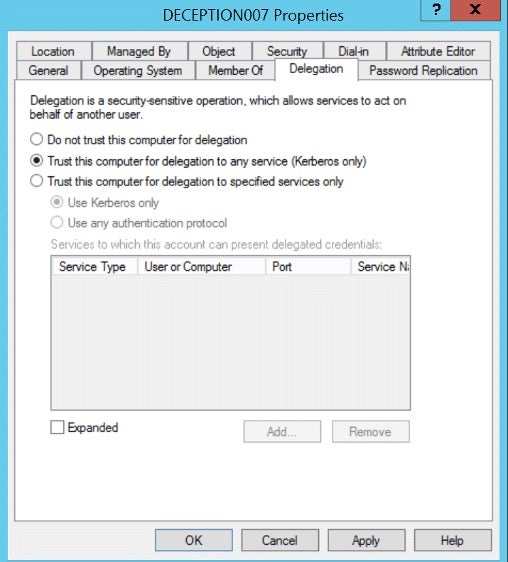
Unconstrained delegation is a privilege that domain administrators can assign to a domain computer or a user. They can enable this privilege from the Delegation tab settings within the object properties.
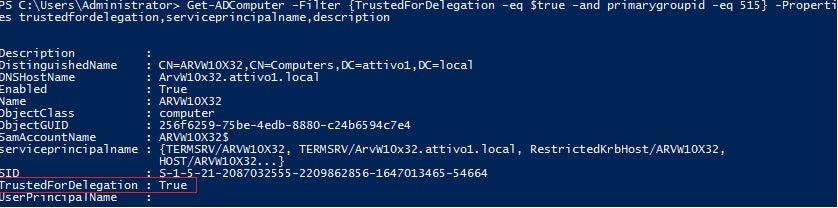
Attackers can discover computers on a domain with an unconstrained delegation property set using the Active Directory PowerShell module cmdlet, Get-ADComputer:
Get-ADComputer -Filter {TrustedForDelegation -eq $true -and primarygroupid -eq 515} -Properties trustedfordelegation,serviceprincipalname,description
When a user authenticates to a computer with unconstrained Kerberos delegation enabled, the authenticated user’s TGT (ticket-granting ticket) gets saved to that computer’s memory. Caching the TGT allows the system to verify that the user has already authenticated without requesting re-authentication and can impersonate the authenticated user to access any other services. Attackers can steal this cached information through Credential Access techniques.
Attackers can then advance their attacks against unconstrained delegation using PowerShell and Mimikatz commands. They can
- Dump and reuse credentials out of LSASS.
- Export all private certificates.
- Escalate privileges to have debug rights on the remote computer.
Detecting Unconstrained Delegation Exposures
Unconstrained delegation configuration poses a serious security risk to an organization where attackers who compromise a single server can compromise the entire domain. The Attivo networks ADAssessor solution offers continuous monitoring for AD vulnerabilities and detects misconfigured dangerous delegation exposures that can lead to credential theft.
Mitigation Steps
- Identify all the servers that have delegation configured. Disable unconstrained Kerberos delegation and configure constrained delegation for servers that require it.
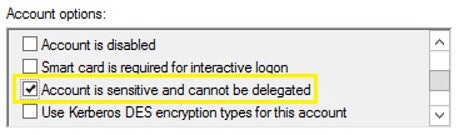
- Enable the “Account is sensitive and cannot be delegated” setting for high privileged accounts.
- Security admins should be more cautious of granting privileged permissions to users who can enable unconstrained Kerberos delegation. The option “Enable computer and user accounts to be trusted for delegation” is available under Security Settings >> Local Policies >> User Rights Assignment.
- Adding user accounts to the Protected Users Security Group, available starting with Windows Server 2012 R2, can also mitigate unconstrained delegation exposure.
Conclusion
Detecting Active Directory exposures at an early stage can massively reduce the impact of an attack. The Ranger® AD solution can enhance visibility and remediate unconstrained delegation exposures, preventing further AD attacks.
For more information, please visit Singularity Ranger AD.


