Enterprise businesses continue to undergo digital transformations, finding new ways to connect with their client base, embracing hybrid and work-from-home strategies, and scaling their operations through innovative technologies. Though cloud adoption has been a key driver for these transformations, the unique challenges of securing cloud environments remains a top concern amongst enterprise leaders and security professionals.
Most recently, Fortinet’s 2023 Cloud Security Report found that most global respondents across various industries expressed a moderate to high level of concern regarding cloud security. 43% of those surveyed believed that risks associated with using a public cloud far surpassed those tied to traditional, on-prem environments. One of the top risks identified highlighted the unique challenge of meeting cloud-specific compliance requirements.
This post provides an overview of the various regulations and requirements that impact cloud security and focuses on practical cyber best practices enterprises can implement to ensure compliance and continue benefiting from the cloud.

Changing Landscapes | How Cloud Security Needs Are Evolving
In a report covering data security in an era of hybrid work, ransomware, and accelerated cloud transformation, researchers examined the momentum that cloud adoption continues to see. Of those surveyed, a third of companies stated that they had 41% to 60% of all their corporate data stored in an external cloud. Another 22% of those participants indicated that over 60% of their business critical data was based in the cloud.
With so much of the world’s data now held in the cloud, enterprises are expected to meet set standards for cloud usage and security in accordance with industry-specific guidelines as well as local, state, federal, and international laws. Regulations and compliance controls serve to protect businesses and their clients; however, shifts in the greater threat landscape mean that they are frequently subject to change.
Even in terms of obtaining cyber liability insurance coverage, modern enterprises based in the cloud must be certain that their cloud infrastructure meets all applicable controls and regulations. Insurance carriers, particularly those that serve high risk industries like IT, finance, and healthcare, all require advanced cybersecurity measures in order to bind their insurance policies. Since the cloud surface is faced with many inherent risks, security strategies are now a hard requirement for any kind of coverage.
Addressing the Challenges of Securing Modern Clouds
Cloud computing has long evolved from just a means of storing data. The past decade has seen cloud bloom into a full-scale computing solution and enable an entire generation of organizations to share, optimize, manage, and scale information like never before.
Though powerful and very beneficial, the features that make cloud services so useful to enterprises are the same ones that make data in the cloud a challenge to regulate and secure. Security leaders defending their organization’s cloud environment take into consideration the following dimensions of cloud security:
- Data security – Cloud infrastructures and the use of multiple cloud services leave a wide surface for cyberattack. As vast amounts of sensitive data and workloads continue to be deployed to the cloud, the task to secure them all grows.
- Automated and continuous monitoring – Some security regulations and laws require cloud-based enterprises to monitor their cloud infrastructure. Depending on what solutions an enterprise uses for threat monitoring, this can create a large burden on small, in-house security teams or organizations that are still building up their security staff.
- Network visibility – For those who have deployed a hybrid network, establishing full network visibility can be daunting. Security teams working in hybrid networks face a more complex challenge since they need to keep eyes on a range of topologies, varying features, and data discrepancies.
- Fleet visibility – Similar to network visibility, cloud environments pose a unique challenge for asset and inventory monitoring. The different composition of cloud assets, from virtual machines to containerized workloads or the orchestration services that host them, are inherently more difficult to track than physical assets.
- Multi-cloud workflows – Multi-cloud architectures allow enterprises to stay agile, but they make workflow management more complex. The more workflows there are, the harder it is to ensure compliance across them all since there are many people making changes and accessing data.
How to Build a Stronger Cloud Security Compliance Posture
Cloud compliance describes the process and act of meeting regulatory standards, industry guidelines, and applicable legal requirements for using cloud technology. Compliance in cloud environments starts in the planning and initial deployment stage with the right settings, policies, and best practice frameworks in place to guide ongoing use.
Since many cyberattacks on the cloud surface are the result of poor implementation of cloud security measures, insider threats, and misconfigurations, focusing on cloud compliance management can help security leaders prioritize what needs to be done to achieve a stronger security posture.
1 – Get to Know the Compliance Security Frameworks
The following is a list of the most widely-used government and industry-specific security regulations that pertain to cloud-based organizations.
HIPAA (Health Insurance Portability & Accountability Act) federal standards seek to protect sensitive health information from being disclosed without the knowledge and consent of the patient it belongs to. The HIPAA Security Rule is a subset of requirements that supports these standards and covers all individually identifiable health information created, received, maintained, or transmitted in electronic form.
Organizations that create, receive, maintain, and or transmit electronic protected health information (e-PHI) through a cloud platform must:
- Ensure the confidentiality, integrity, and availability of all e-PHI
- Detect and safeguard against anticipated threats to the security of the information
- Protect against anticipated impermissible uses or disclosures that are not allowed by the rule
- Certify compliance by their workforce
- Use PHI-compliant vendors for services that may expose PHI
SOX (Sarbanes-Oxley Act) is a federal law enforcing auditing and financial regulations upon public companies to improve the reliability of their financial reporting and foster investor confidence in the age of high-profile corporate crime. To comply with SOX, companies are required to:
- Implement strong digital safeguards in place to prevent data tampering
- Have verifiable controls to monitor all data access
- Establish policies to disclose data breaches to SOX auditors and other applicable parties
Public companies adhering to SOX guidelines are only permitted to work with cloud service providers that themselves follow the Statement on Auditing Standards No. 70 or the Statement on Standards for Attestation Engagements No. 16 auditing guidelines.
PCI DSS (Payment Card Industry Data Security Standard) was developed to protect all payment account data throughout the payment lifecycle. Any organization, merchant, service provider, or institution that processes card payment transactions are required to abide by PCI DSS controls. These controls focus on building and maintaining a secure network and system to protect cardholder data through robust access controls.
Cloud-specific PCI DSS controls to be followed include:
- Physical firewalls and network segmentation at the infrastructure level
- Firewalls at the hypervisor and VM level
- VLAN tagging or zoning in addition to firewalls
- Intrusion-prevention systems at the hypervisor and/or VM level to detect and block unwanted traffic
- Data-loss-prevention tools at the hypervisor and/or VM level
- Controls to prevent out-of-band communications occurring via the underlying infrastructure
- Isolation of shared processes and resources from client environments
- Segmented data stores for each client
- Strong, two-factor authentication (MFA/2FA)
- Separation of duties and administrative oversight
- Continuous logging and monitoring of perimeter traffic, and real-time response
The NIST (National Institute of Standards & Technology) framework is a risk-based approach to managing cybersecurity risks through a repeatable and measurable process. NIST Special Publication 800-144 (“Guidelines on Security and Privacy in Public Cloud Computing) outlines recommendations organizations can follow when outsourcing data, applications, and infrastructure to a public cloud environment. Other special publications geared specifically towards cloud computing include:
- NIST SP 500-291 – Compiles available cloud computing standards and identifies gaps.
- NIST SP 500-293 – Provides a detailed cloud infrastructure security framework for government use.
- NIST SP 800-53 Rev. 5 (2020) – A commonly used information system security standard, also relevant to cloud environments.
- NIST SP-800-210 (2020) – Details cloud security and access controls, providing guidance to help secure Paas and IaaS services.
ISO 27001 is recognized internationally as an information security standard for establishing, implementing, operating, monitoring, reviewing, maintaining, and improving Information Security Management Systems (ISMS).
Under this main umbrella of standards, ISO 27017 is a set of security controls specific to cloud computing and ISO 27018 set of privacy controls for managing personal data in cloud environments.
FedRAMP (Federal Risk & Authorization Management Program) is a federally recognized and government-wide compliance program promoting the adoption of secure cloud services. It standardizes the security assessment and authorization of any cloud products and services used by U.S. federal agencies.
2 – Understand Roles & Responsibilities of Cloud Service Providers
The responsibility of securing a cloud environment is not shifted from an enterprise to their cloud service provider (CSP) – rather, it is shared. This starts with an understanding between all associated parties with access to the cloud through frameworks such as the Cloud Shared Responsibility Model.
The model clearly defines the areas of control and protection that each party must handle to ensure a secure and reliable cloud environment. In this model, the CSP is responsible for securing the underlying cloud infrastructure, including servers, networks, and physical facilities. On the other hand, the enterprise is accountable for managing their data, applications, user access, and configurations.
The significance of the Cloud Shared Responsibility Model lies in establishing clear boundaries and expectations for both CSPs and customers. It helps organizations understand the division of responsibilities and assists in making informed decisions about implementing additional security measures to protect their data and applications. By clarifying the shared responsibilities, the model promotes collaboration, risk mitigation, and effective security management in the cloud.
3 – Lay Down Corporate Cloud Policies & Cloud Governance
Developing cloud security policies that make sense for a unique business begins with assessing risks. Since there are inherent risks to consider, security leaders will need to look at what information is shared to the cloud, how it is being stored, and what requires business-critical levels of control and access.
Post risk assessment, design policies and controls around the cloud risks and then establish cloud governance to disseminate and manage those policies to the rest of the organization. Having a formal governance model in place reduces friction between various teams when the new cloud policies are implemented and refined. Both cloud adoption and governance champions should be in regular contact to evaluate and adjust corporate cloud policies to fit the evolving needs of the business.
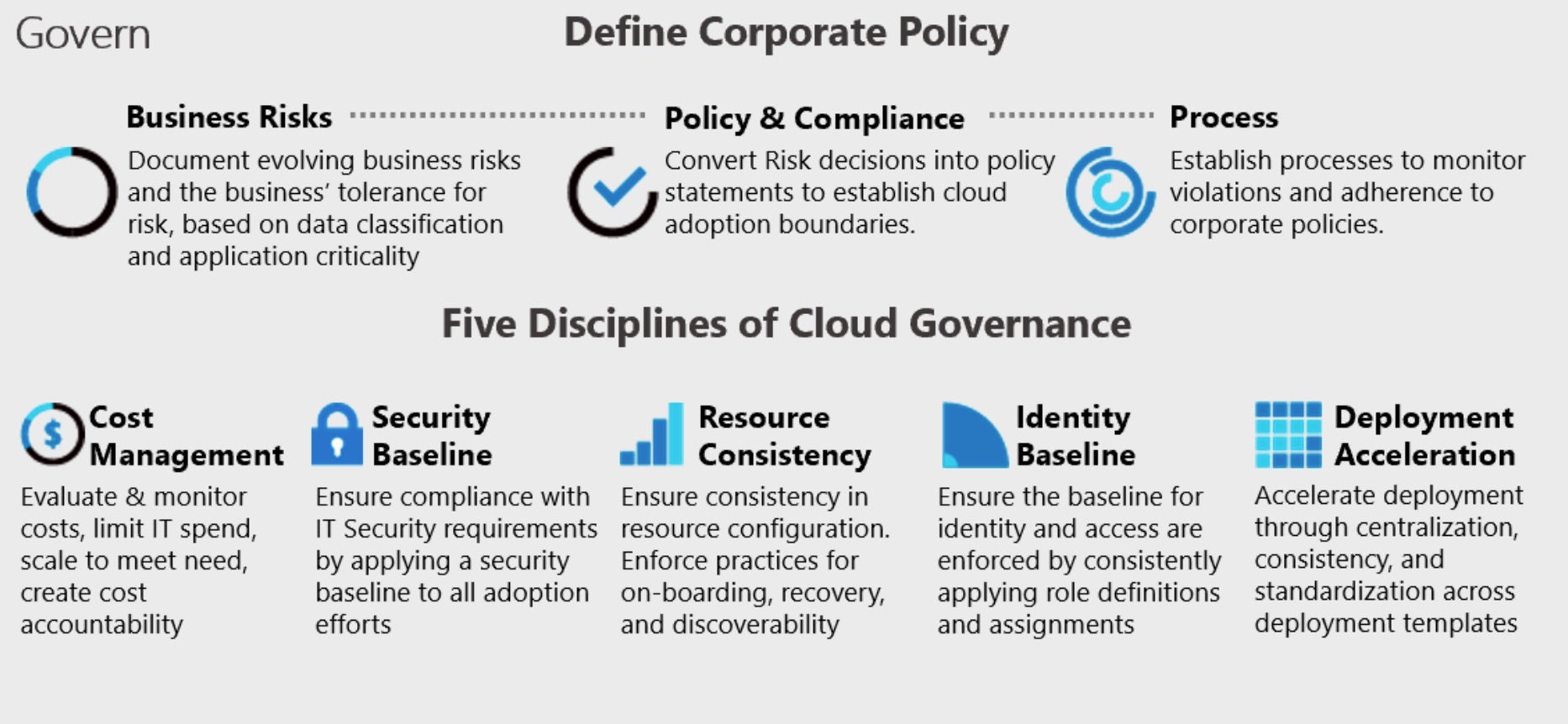
4 – Establish Cloud-Related Change Management
In cloud computing, changes to the systems, services, or configurations will need to be tightly controlled involving workflows to review, approve, and even document any modifications and updates made to any part of the cloud infrastructure or applications.
While cloud solutions and services enable flexibility and speed, these benefits can also make managing change a challenge for security teams. Improperly established change control can result in misconfigurations early on in the cloud deployment process, leaving the environment exposed to opportunistic threat actors.
To establish proper change management processes for cloud:
- Continuously monitor any administrator and root accounts for indications of unauthorized access.
- Implement role-based access and group-level privileges. Only grant access based on an individual’s tasks and workflows and work off of a least privilege principle for all users in the cloud.
- Offboard dormant or obsolete accounts to remove the changes of account takeover by threat actors.
- Enable logging on critical resources held in the cloud and protect logs through encryption.
Conclusion
Growing cloud adoption rates reaffirm its popularity amongst organizations of all sizes. Used to increase scalability, flexibility, and operational efficiency, cloud computing has risen as a driving force behind many modern businesses. As more businesses migrate to cloud as part of their ongoing digital transformations, cloud compliance will remain a keystone within the overarching cybersecurity strategy.
Building a strong cloud strategy focused on achieving compliance means understanding what legal and regulatory requirements are required for specific industries and locations of operation. Also, taking time to perform a detailed risk assessment allows security teams to design policies and governance models that are streamlined to the business and support the ongoing use of innovative cloud technologies.
Learn about how SentinelOne’s Singularity™ Cloud solution protects the cloud surface from advanced cyberattacks, allowing business leaders to focus on their operations and clients. Improve your cloud security strategy through a combination of endpoint detection and response (EDR) capability, autonomous threat hunting, and runtime solutions that can defeat cloud-based threats without compromising agility or availability. Contact us today or book a demo for more details.


