NoEscape Ransomware: In-Depth Analysis, Detection, and Mitigation
What Is NoEscape Ransomware?
NoEscape ransomware emerged in May of 2023 and functions as a Ransomware-as-a-Service (RaaS). The developers of NoEscape claim to have built the malware and its supporting infrastructure from scratch; notably opting not to incorporate source code or leaks from other known ransomware families. Currently, NoEscape RaaS operators provide affiliates with a platform to build and manage payloads for both Windows and Linux.
NoEscape is also a known multi-extortion operation, hosting a TOR-based blog to list victims, and host exfiltrated data of victims that fail to comply with their demands.
What Does NoEscape Ransomware Target?
Since NoEscape operates as a RaaS, its targets vary depending on the affiliate and the buyer. From what is known, NoEscape operators seemingly avoid targeting entities in the Commonwealth of Independent States (CIS).
How Does NoEscape Ransomware Work?
NoEscape RaaS payouts are engineered on a shared-profit model similar to many of the contemporary operations. Any collected ransom over $3 million dollars USD results in a 90/10 split in favor of the affiliates. The number changes with lower ransom amounts. For example, a one million dollar payout would result in a 80/20 split for the operator and affiliate respectively.
Prospective NoEscape affiliates are offered a full-feature management panel to monitor and manipulate their ransomware campaigns. The panel offers ‘full automation’ within the TOR network, automated updates to the TOR-based leak blog, a private victim chat, and several communication channels. The NoEscape group also offers their affiliates 24/7 support and other ‘prime’ features that come with a sizeable ‘software license purchase’.
NoEscape ransomware payloads support multiple encryption modes, including full, fast, or strong, along with leveraging RSA and ChaCHA20 for the specific file encryption. Other features include process termination, safe-mode operation, spreading and encryption over SMB or DFS, and the use of the Windows Restart Manager to work around any processes which may inhibit the encryption process. A shared encryption feature allows for a single encryption key to be shared across all infected files in a network as opposed to each host having a unique key. This option is available to allow for efficient encryption and rapid decryption should the victim pay.
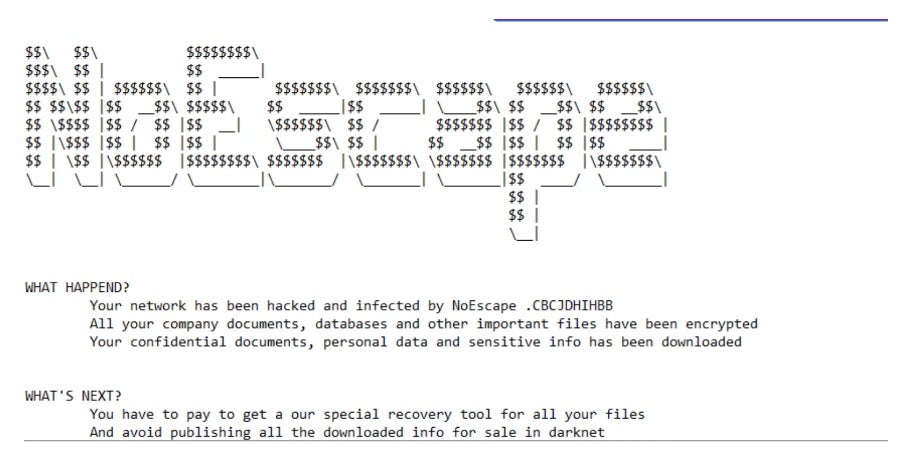
NoEscape ransom notes are written as “HOW_TO_RECOVER_FILES.TXT” to each folder containing encrypted files. All encrypted files will have a ten-character identifying extension appended to them. Examples of observed extensions include “.CCBDFHCHFD” and “.CBCJDHIHBB”.
How to Detect NoEscape Ransomware
The SentinelOne Singularity XDR Platform can identify and stop any malicious activities and items related to NoEscape ransomware.
In case you do not have SentinelOne deployed, detecting NoEscape ransomware requires a combination of technical and operational measures designed to identify and flag suspicious activity on the network. This allows the organization to take appropriate action, and to prevent or mitigate the impact of the ransomware attack.
To detect NoEscape ransomware without SentinelOne deployed, it is important to take a multi-layered approach, which includes the following steps:
- Use anti-malware software or other security tools capable of detecting and blocking known ransomware variants. These tools may use signatures, heuristics, or machine learning algorithms, to identify and block suspicious files or activities.
- Monitor network traffic and look for indicators of compromise, such as unusual network traffic patterns or communication with known command-and-control servers.
- Conduct regular security audits and assessments to identify network and system vulnerabilities and ensure that all security controls are in place and functioning properly.
- Educate and train employees on cybersecurity best practices, including identifying and reporting suspicious emails or other threats.
- Implement a robust backup and recovery plan to ensure that the organization has a copy of its data and can restore it in case of an attack.
How to Mitigate NoEscape Ransomware
The SentinelOne Singularity XDR Platform can return systems to their original state using either the Repair or Rollback feature.
In case you do not have SentinelOne deployed, there are several steps that organizations can take to mitigate the risk of NoEscape ransomware attacks:
Educate employees: Employees should be educated on the risks of ransomware, and on how to identify and avoid phishing emails, malicious attachments, and other threats. They should be encouraged to report suspicious emails or attachments, and to avoid opening them, or clicking on links or buttons in them.
Implement strong passwords: Organizations should implement strong, unique passwords for all user accounts, and should regularly update and rotate these passwords. Passwords should be at least 8 characters long, and should include a combination of uppercase and lowercase letters, numbers, and special characters.
Enable multi-factor authentication: Organizations should enable multi-factor authentication (MFA) for all user accounts, to provide an additional layer of security. This can be done through the use of mobile apps, such as Google Authenticator or Microsoft Authenticator, or through the use of physical tokens or smart cards.
Update and patch systems: Organizations should regularly update and patch their systems, to fix any known vulnerabilities, and to prevent attackers from exploiting them. This includes updating the operating system, applications, and firmware on all devices, as well as disabling any unnecessary or unused services or protocols.
Implement backup and disaster recovery: Organizations should implement regular backup and disaster recovery (BDR) processes, to ensure that they can recover from ransomware attacks, or other disasters. This includes creating regular backups of all data and systems, and storing these backups in a secure, offsite location. The backups should be tested regularly, to ensure that they are working, and that they can be restored quickly and easily.
NoEscape Ransomware FAQs
What is NoEscape ransomware?
NoEscape is a ransomware-as-a-service operation first seen in May 2023. It encrypts files and demands payment for decryption. The attackers threaten to publish stolen data if not paid. When possible, they target both files and backups. The ransomware communicates with command servers during encryption. You can identify it by its distinct ransom wallpaper.
Which sectors and regions have been targeted by NoEscape ransomware?
NoEscape will focus on healthcare, manufacturing, and educational organisations. They will primarily target businesses in North America and Europe. Small and mid-sized companies face the most attacks due to limited security resources. The ransomware will target organisations with valuable data. You can see they prefer victims who can’t afford downtime.
What encryption algorithms does NoEscape ransomware utilise?
NoEscape uses ChaCha20 and RSA-2048 to lock files. It will create unique encryption keys for each victim. The ransomware will encrypt files with a hybrid approach for speed and security. Files will be processed quickly with strong ciphers. You can’t decrypt files without the attackers’ private key. The encryption makes recovery impossible without the decryption tool.
How does NoEscape ransomware propagate within networks?
NoEscape exploits flaws in remote access tools and moves through network shares once inside. The attackers use stolen credentials to gain admin rights and deploy them through group policies in domain environments. If you have connected systems, it will spread to maximise damage. The malware maps network drives before starting encryption.
What file extension does NoEscape append to encrypted files?
NoEscape will add the .noescape extension to all encrypted files. The ransomware will keep the original file names but add this extension at the end. Original extensions remain visible after the added marker. It will create a unique ID for each infection. You can quickly identify encrypted files by this pattern. The ransomware targets over 200 different file types.
What indicators of compromise (IOCs) are associated with NoEscape ransomware?
You can identify NoEscape through specific registry changes in the HKCU hive. The ransomware will create files named “README_TO_RESTORE.txt” in each folder. Connections to a Tor-based command server will be made. Look for deleted shadow copies and stopped security services. If you check logs, you’ll find data leaving the network before encryption starts.
How can organisations detect an ongoing NoEscape ransomware attack?
You can detect NoEscape by watching for mass file renaming operations. Monitor for suspicious PowerShell commands and security shutdowns. Look for unexpected admin account usage. The ransomware will cause high disk activity during encryption. Network traffic will show data exfiltration patterns. If you see these signs, disconnect systems from the network immediately.
What preventive measures can be implemented to protect against NoEscape ransomware?
You can prevent NoEscape attacks by using multi-factor authentication for all remote access, keeping systems patched and updated, training employees to spot phishing attempts, and setting up network segmentation to limit movement. If you have critical data, keep offline backups that NoEscape can’t reach, and block macros in documents from untrusted sources.
What steps should be taken immediately after a NoEscape ransomware infection?
Disconnect all infected systems from networks right away. You can contain the outbreak by isolating affected network segments—document which files were encrypted. Contact security experts and law enforcement. If you have clean backups, prepare them for restoration. Don’t contact attackers before getting professional advice. Start your incident response plan immediately.