Katz Stealer is a feature-rich infostealer marketed and operated as Malware-as-a-Service (MaaS). It was launched in early 2025 and quickly garnered attention within the infostealer landscape.
The stealer includes robust credential and data discovery with theft capabilities as well as modern evasion and anti-analysis features. It is used to exfiltrate a broad range of personal or sensitive information including passwords, cryptocurrency keys, private messaging tokens, browser session data and more.
Katz Stealer is marketed through popular cybercrime forums as well as more broad networks (Telegram and Discord) and provides its subscribers with a web-based management panel. This interface is used to generate custom payloads, manage stolen data and logs, and perform other high-level campaign management. The turnkey nature of the Katz Stealer service, along with accessible pricing, have led to rapid adoption by threat actors across the spectrum of capability. In this post, we provide an overview of Katz Stealer’s general functionality and infrastructure.

Marketing & the MaaS Platform
Katz Stealer operates as a commercially distributed MaaS (Malware-as-a-Service) platform. Similar to RaaS operations, the developers of Katz Stealer offer the service to their “affiliates” or “customers” for an up front fee. Affiliates are provided with access to a web-based management panel, which they can use to generate and configure custom builds of the stealer payloads.
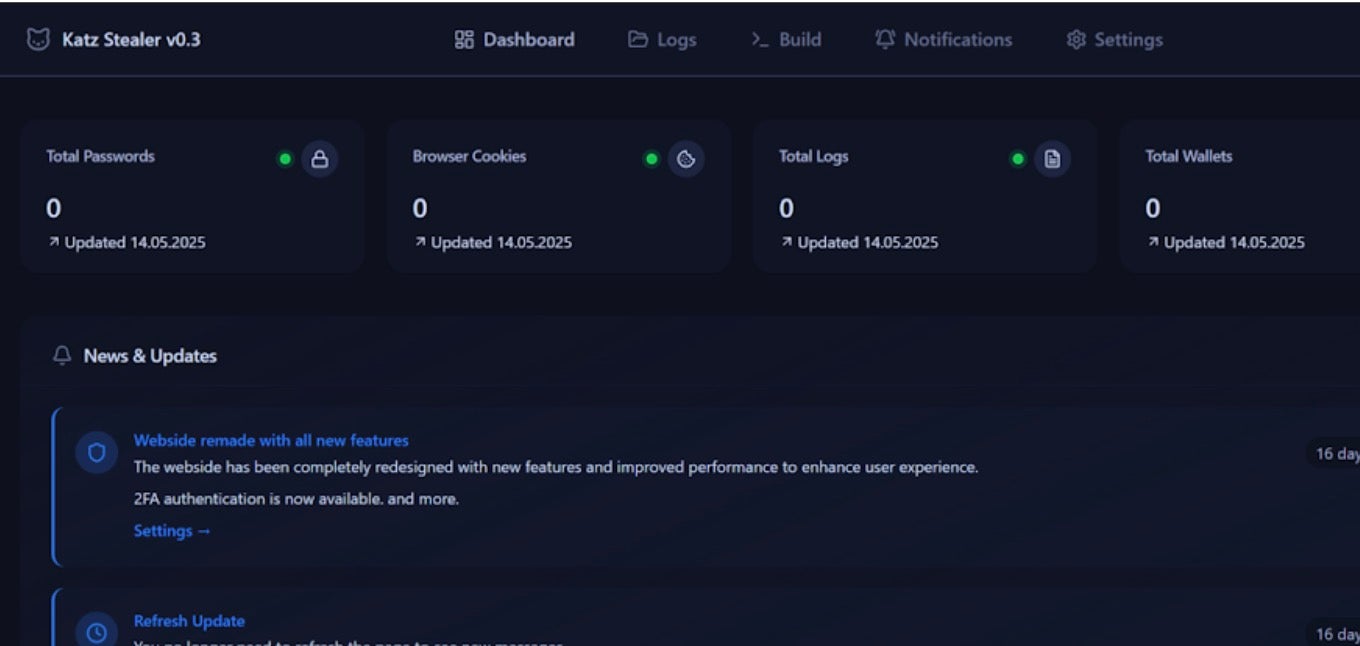
Various payload options can be toggled on or off during the build process, including checks for Virtual Machine hosts and different theft modules. The delivery format of the payload can be configured here as well. In addition, the panel functions as the data back-end for the stealer, allowing stolen victim data to be processed and searched. Attackers are also able to export and package stolen data in multiple ways, making it convenient for extortion purposes.
Katz Stealer is marketed on many web-based crime forums as well as on its own portal site.
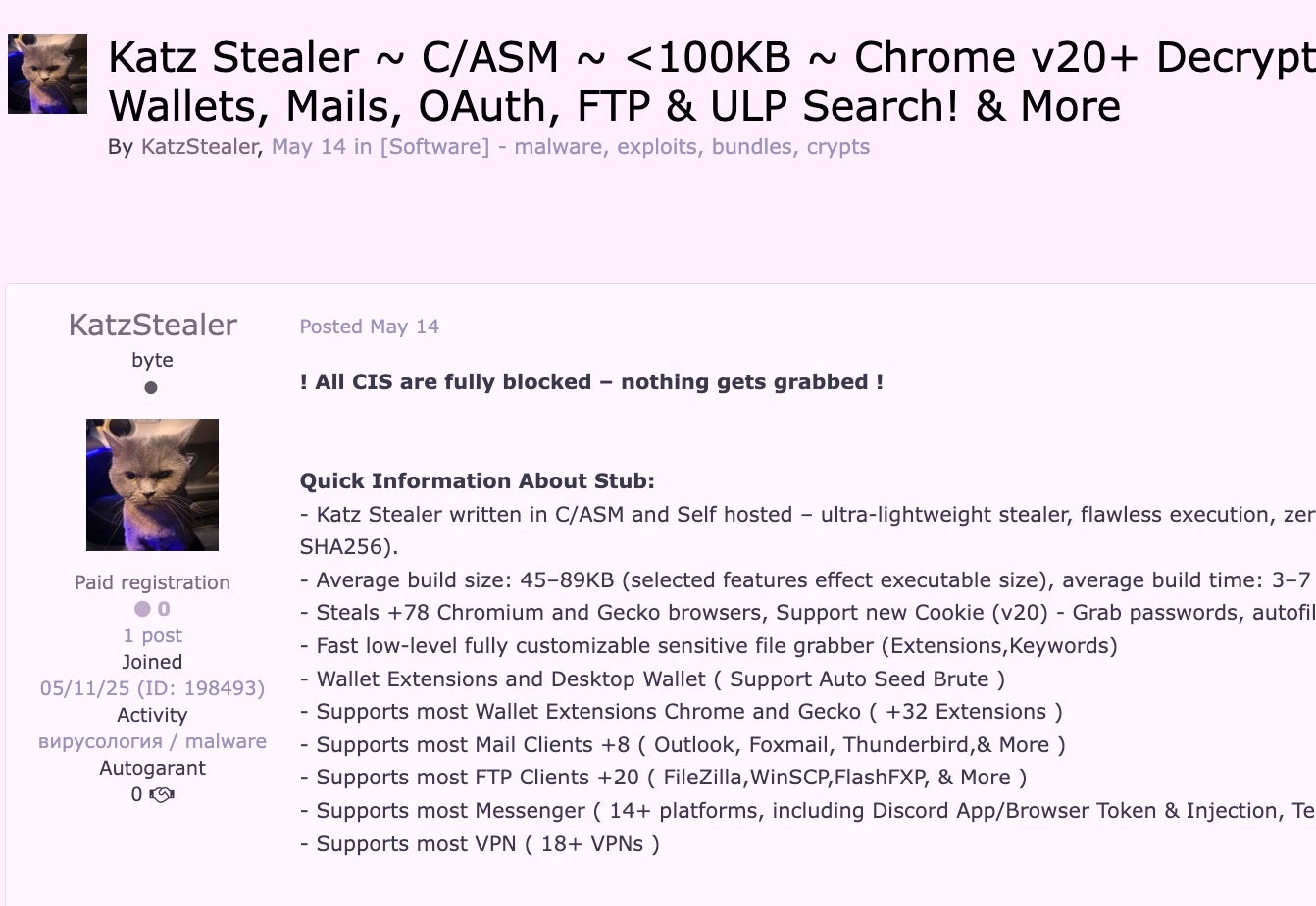
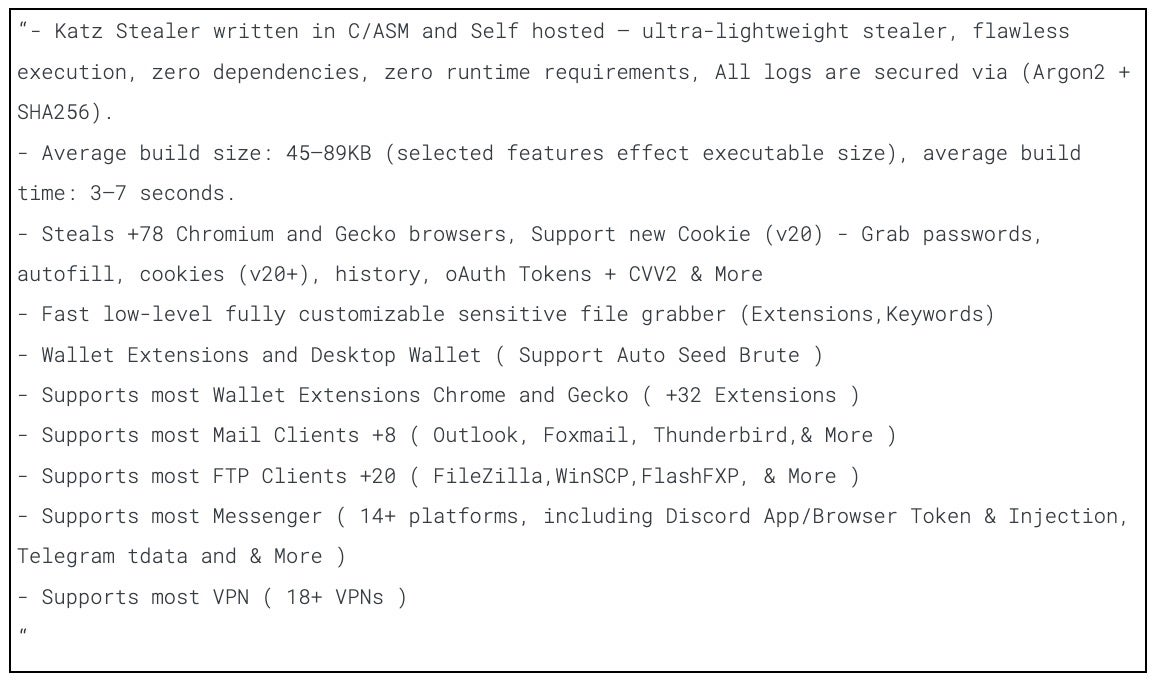
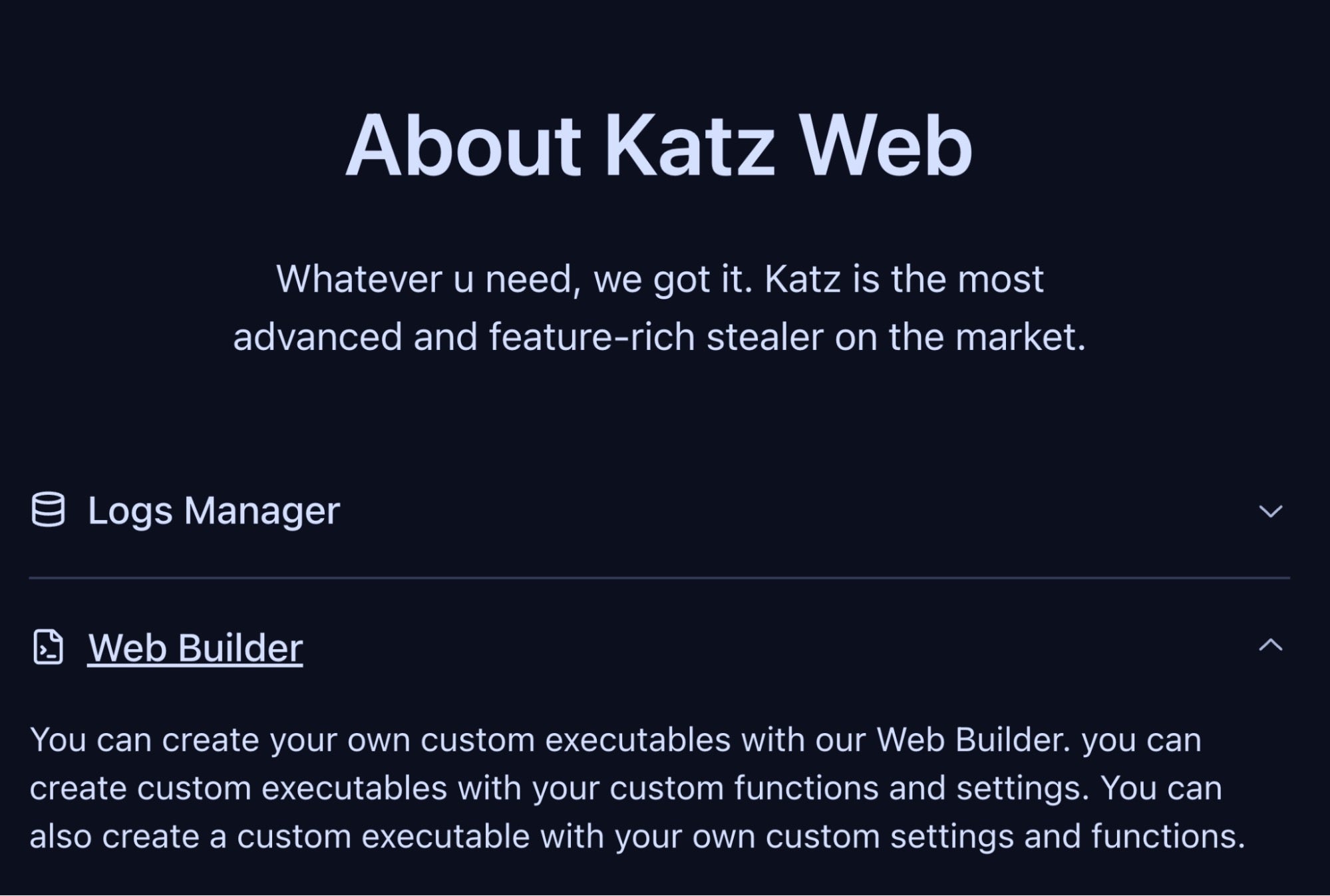
The sellers highlight the robustness of support that Katz has for stealing from numerous applications and data types. The following feature set is currently advertised for Katz Stealer:
The stealer is also heavily advertised across Telegram and Discord communities. The sellers accept payment in most stable cryptocurrencies (BTC, XMR). As of this writing, pricing for access to Katz Stealer were as follows:
6 Months – $480.00 USD
3 Months – $270.00 USD
1 Month – $100.00 USD
Infection & Evasion Tactics
Katz Stealer leverages a multi-stage infection chain. Katz campaigns most frequently start with malicious archive files (.gz) delivered to the victim via phishing email or trojanized downloads. These emails (or malicious downloads) contain an obfuscated JavaScript dropper. The JavaScript code is highly obfuscated and subjected to multiple transformations in an effort to evade static analysis.
When executed, the JavaScript dropper launches a PowerShell command, often with the -WindowStyle Hidden flag, to further evade user detection. This PowerShell script downloads what appears to be a harmless image file from a remote server. However, the image is weaponized using steganography. Analysis reveals the image contains a base64-encoded string embedded between specific markers. These markers can vary across samples.
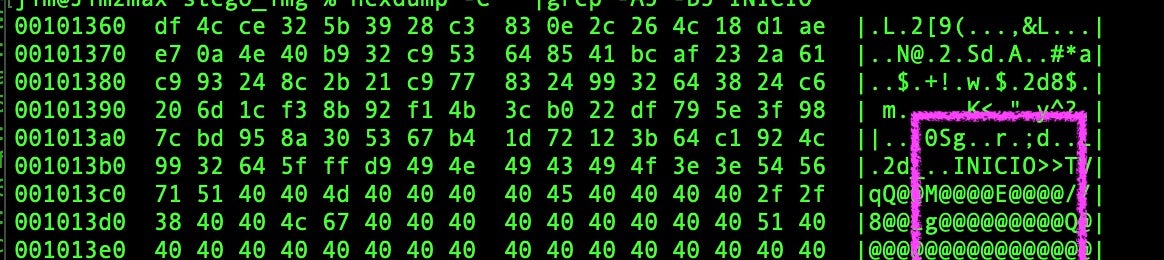
The image below shows an example of a Katz Stealer ‘stego image’ “new_image.jpg”. The markers delineating the base64-encoded sections in this sample (0fad38ab91d5676378265405b4f42d98e475c44c) are <<INICIO>> and <<FIM>>. The script scans the image for these markers, extracts the string, and decodes it entirely in memory, ensuring that no malicious payload is written to disk at this stage.
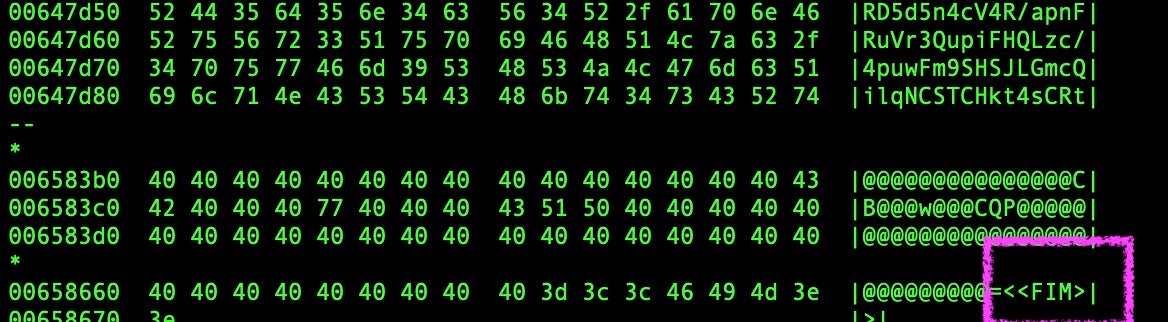
Once the payload is decoded, Katz Stealer leverages a User Account Control (UAC) bypass by abusing cmstp.exe, a legitimate Windows utility, to gain elevated privileges. It then establishes persistence by creating a scheduled task, ensuring that the malware survives system reboots.
The third stage Katz Stealer payload is the .NET loader responsible for final geofencing and anti-analysis checks prior to further execution. Katz Stealer checks the local system’s locale settings, keyboard layout and default language settings in an effort to exclude use within the CIS (Commonwealth of Independent States) such as Russia, Belarus and other former Soviet Union states.
Additionally, the malware performs a series of checks to determine if it is being executed within a virtual or sandbox/analysis environment. It reads various BIOS identifiers from the Windows registry looking for strings related to common VM platforms (e.g., VirtualBox, VMWare). Default resolution and system uptime are also checked as these are valuable for indicating analyst or researcher environments.
The next stage of the infection spawns the main Katz Stealer module, via process hollowing, within MSBuild.exe (Microsoft Build Engine). First, Katz Stealer drops a dummy INF file, then invokes cmstp.exe to execute. This is a well-established UAC bypass technique, and it allows attackers to fully bypass UAC while avoiding prompts of additional user interaction.
The malware also establishes persistence at this time by creating a scheduled task. The task is set to trigger upon every system restart. The main module is executed within MSBuild.exe via process hollowing. The prior-stage loader spawns an instance of MSBuild.exe, reserving a section of memory to implant and execute the main Katz Stealer module. Running in this context, elevated and within the privileged memory space of MSBuild.exe, the malware is able to operate with SYSTEM-level access hidden from surface-level detection tools.
Once active, Katz Stealer injects itself into target processes to begin harvesting data. Katz is heavily focused on browser data, and multiple browsers are supported. Rather than intercepting existing user browser sessions, Katz launches the targeted browser processes in headless mode, which ensures it remains hidden from the user. A specialized DLL (written to disk by the dropper in %temp%) is injected into the headless browser process, allowing the malware to fully access sensitive browser data in an elevated context.
Infostealer Features
Katz Stealer is capable of stealing files, tokens and credentials from nearly every common application or service that a typical user might have. The infostealer can harvest data from all commonly used web browsers (Chrome, Edge, Brave, Firefox and various Chromium/Gecko-offshoots). Saved passwords, login session cookies, saved session tokens, autofill data (including stored credit card CVV data) are all targeted. Katz also has the ability to decode encrypted browser data in some cases, as detailed in the next section.
Messaging and gaming platforms are also targeted, including the harvesting of gaming session tokens and user account data from secure messenger platforms (e.g., Discord, Telegram), along with credentials for well-known gaming sites and communities like Steam.
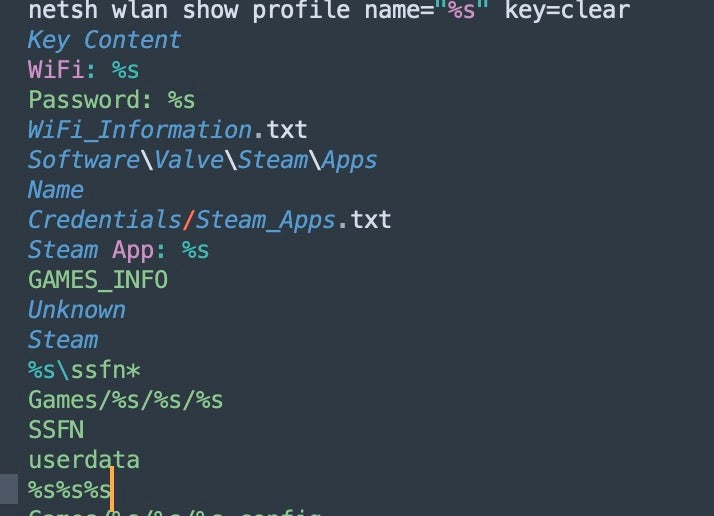
In addition, Katz Stealer targets a wide range of Email, FTP, and VPN clients. The malware parses and extracts stored messages and credentials from Outlook, Windows Live Mail, Foxmail, Eudora and other mail clients. Katz extracts and logs any configuration files and stored credentials related to VPN clients, FTP Software and known WiFi networks.
Katz Stealer also has the ability to capture screenshots (scheduled or ad-hoc), audio and video. It monitors clipboard activity for strings that resemble passwords, passkeys and cryptocurrency wallet addresses. Attackers often combine these features to capture one-time passcodes or other time-sensitive info displayed on the screen of the targeted system(s). Finally, Katz Stealer is heavily focused on cryptocurrency wallets. Private keys, wallet files, and discovered seed phrases are all captured for a wide array of cryptocurrency wallets.
Browser Injection Process and Encryption Bypass
Data stored by web browsers (passwords, autofill data, cookies) are a primary target for Katz Stealer. The malware is able to bypass some modern browser security measures. Once the Katz Stealer DLL is injected into a browser process, the infostealer can extract sensitive data using the browser’s own security context and available APIs.
This allows Katz Stealer to bypass some encryption barriers that attempt to obfuscate sensitive data. For Chromium-based browsers, Google has introduced (in 2024) ABE (Application Bound Encryption), which ties the decryption of stored passwords and cookies to the logged-in OS user. Katz Stealer is able to defeat this by programmatically masquerading as the browser once injected. The malware locates the browser’s “Local State” file (which is responsible for storing the master encryption key for the logged-in user’s browser session data) and uses the Windows cryptography API to decrypt that key.
With the plaintext master key now available, the malware can subsequently decrypt all saved passwords and cookies from the browser’s SQLite databases. These extracted keys are saved to disk as text files (e.g., decrypted_chrome_key.txt) in the current user’s %APPDATA% folder.
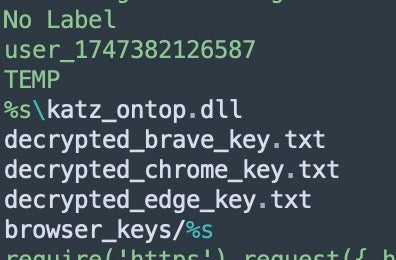
These stored files can be called upon for later use should the infostealer need to decrypt further or new browser session data. This technique appears to be borrowed (at least partially) from the open-source project ChromeKatz, which allows the dumping of Chrome credentials via similar methods of impersonation within the browser.
For Firefox and other Mozilla/Gecko-based browsers, Katz Stealer locates Firefox’s profile directories and harvests the core files that contain all the browser user and session information. This includes saved usernames and passwords (logins.json) along with the databases that hold decryption keys for all the local logins (key4.db). By collecting all the raw logins, keys, and session data, the attacker can crack or decrypt the passwords offline.
Cryptocurrency Theft Features
Katz Stealer searches the victim’s filesystem for any files related to modern desktop cryptocurrency wallet applications. The malware targets data from multi-coin wallets like Exodus and Coinomi, as well as specific wallet data pertaining to Dash, Dogecoin, Litecoin, Monero (XMR), Bitcoin and Ethereum. The stealer uses a combination of known file paths, folder names, and extensions to locate relevant data. Once identified, the malware copies wallet files, private keys, and backed-up seed phrases to its own temporary folder.
Katz Stealer is also capable of stealing data from individual crypto-based browser extensions. Katz Stealer contains over 150 specific browser extension “IDs” which correspond to cryptocurrency wallet extensions (e.g., MetaMask, Phantom, Binance). The malware scans the browser’s extension data for these IDs, and when found, gathers all relevant files and data such as extension logs, wallet vault files, and any cached seed phrases. For more hardened browsers like Brave, Katz contains tailored code which can locate Brave’s wallet data as well, and process it directly.
C2 and Network Behavior
Once a victim is successfully infected, Katz Stealer establishes an active and persistent C2 channel. Each instance of the stealer contains a hardcoded C2 IP address. Upon infection, the malware calls out to the C2 and identifies itself via a campaign-unique ID.
The malware continues to beacon out to the C2 server to ensure a consistent and available connection. In the event the C2 is unreachable, the implant continues to beacon to the C2 until connectivity can be established, or some sort of termination command is received. Most analyzed Katz stealer samples contain hardcoded C2 IP addresses as opposed to more ‘resilient’ options like DNS-centric C2 communications.
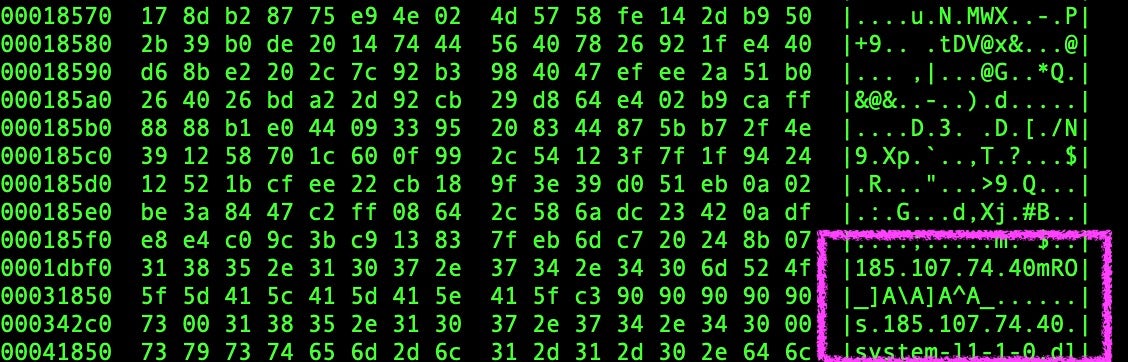
The bulk of C2 communications within Katz Stealer are IP-based with the use of HTTP/HTTPs for the primary functions. There are multiple attacker-controlled domains used to control the main malware infrastructure and host the MaaS components with the management panels.
Katz Stealer is not a ‘one shot’ infostealer; it is designed to continually exfiltrate the victim’s data. The malware not only extracts data found on a targeted system at the point of infection but also as data updated, changed, or freshly introduced. Credentials, tokens, and plain text data may be sent line-by-line via HTTP Post to the C2 servers. Larger data blocks like screenshots, audio-visual data and cryptocurrency wallets are transferred via similar methods, but broken up into chunks which are then reconstructed on the server side.
Once the malware operators have determined that the stealer has harvested all targeted and desired data, they are able to invoke steps to remove traces of the incident. The malware removes all temporary files and folders used to store locally harvested data; any output logs or temporary data files are wiped and all injected processes are terminated, removing the malicious code from memory.
Conclusion
Katz Stealer represents a potent combination of credential theft and modern malware design. It has multi-faceted stealing abilities across browsers, messaging systems and cryptodata, along with stealthy delivery methods (in memory staging, pseudo-steganography, process injection and hollowing). This feature set, and low barrier of entry are resulting in a notable increase in Katz Stealer use and an overall rise in the adoption of this tool as a viable infostealing platform.
However, Katz Stealer still relies on social engineering and user interaction to enable a successful compromise. This is a malicious mix of old and new. The SentinelOne Singularity is capable of detecting and preventing malicious behaviors and artifacts associated with Katz Stealer.
Indicators of Compromise
Files SHA-1
0076795b220fa48c92b57994b015119aae8242ca
0c1f2ee0328e0ed7e4ec84ef452bffa1749f5602
17ce22264551bd32959790c4c2f57bec8304e2ce
1976a1a05a6a47ac33eb1cfc4e5a0eb11863f6eb
1b6b072df8f69a47fd481fa9be850c0063fd5b93
1d5ef46357eb2298b1c3c4faccbaafa729137613
1ee406eb68ab92bad77cf53df50c4ce6963e75fd
26e089bed61c0d89e5078f387bd55dd5895d4fc0
29daa866c85fc1e302c40a73bc2a0772aa285295
2f2ced67e87101f4d1275456f0861209809492fc
3cf4f3ababa912e0e6bb71ab5abb43681d8e7ecc
47ea1c41f79f775f0631191ee72852c1bfb61a7e
4e69cb16a3768733d94bb1b5d8f1556d0bddd09b
4eeda02db01cdf83948a83235c82e801522efa54
5179dbf5e9fd708f6e6df8b4913f21c3b78d5529
5492947d2b85a57f40201cd7d1351c3d4b92ae88
571b3681f7564236b7527d5b6fe14117f9d4de6d
5de014856702b9f1570944e8562ce283f7cd0a64
6351b5505dc671d143d5970eb08050d2f7344149
680984e43b76aa7a58ed9b617efe6afcb1f04bb7
6d88a5f0021278c2c3a56c177f39f4a31f286032
76bb7ffe523f594308ecd482db4f32047905c461
80f1b8b27833db614d3f7c2a389aceb033b8ce80
82dc7c0ca39f114c333caae9a6931a2a1c487ee5
8c2422ebab77a0de81d2e46e1326d8912b099018
9becb041aedc7c6aafeb412b4b91788e1df65b38
9c60a2b4764b7b5e3a6c7f20036490a539996d8a
a0717a486b4e037871c4657cf353cd298f13601f
b3d574dfb561f5439930e2a6d10917f3aa58c341
b40e56439d4dcdc238b8254adbd8862c73ca34bc
b61f92613dc911609b78a1e83c5baadc7e289dbc
b744179d3304d1e977e680502d201b7df49cb188
bbf2a5fdb039366b3f9eca603bf08ae92c43c0ef
cc800e4977d76c38656f3f60c5ed5f02df6a2f7b
ce19aa5eb7fce50dd94b5f740d162f8d9b057fde
da5ed6b939f51370709f66cbf0d8201ec8cd58b0
dffc1167399631ed779b5698d0ac2d9ea74af6c8
dffddd2fb7b139d2066284c5e0d16909f9188dc2
e26d65d8c25b0be7379e4322f6ebcadecbb02286
e78f942ca088c4965fcc5c8011cf6f9ee5c2a130
fb4792306f2cf514e56bc86485920b8134954433
Network Communications
172.67.146[.]103
185.107.74[.]40
195.182.25[.]71
31.177.109[.]39
80.64.18[.]219
katz-panel[.]com
katz-stealer[.]com
katzstealer[.]com
pub-ce02802067934e0eb072f69bf6427bf6.r2[.]dev
twist2katz[.]com
Zxczxczxczxc.twist2katz[.]com
OSINT
Usernames:
- Katzadmin
- KatzStealer
- @katzst
- @katzcontact
- @katzadmin
qTOX ID:
375AB62BD333F80905E612DB71BEE06660C40F00AAF393FD7F8605DF5761E47670B6578C9410




