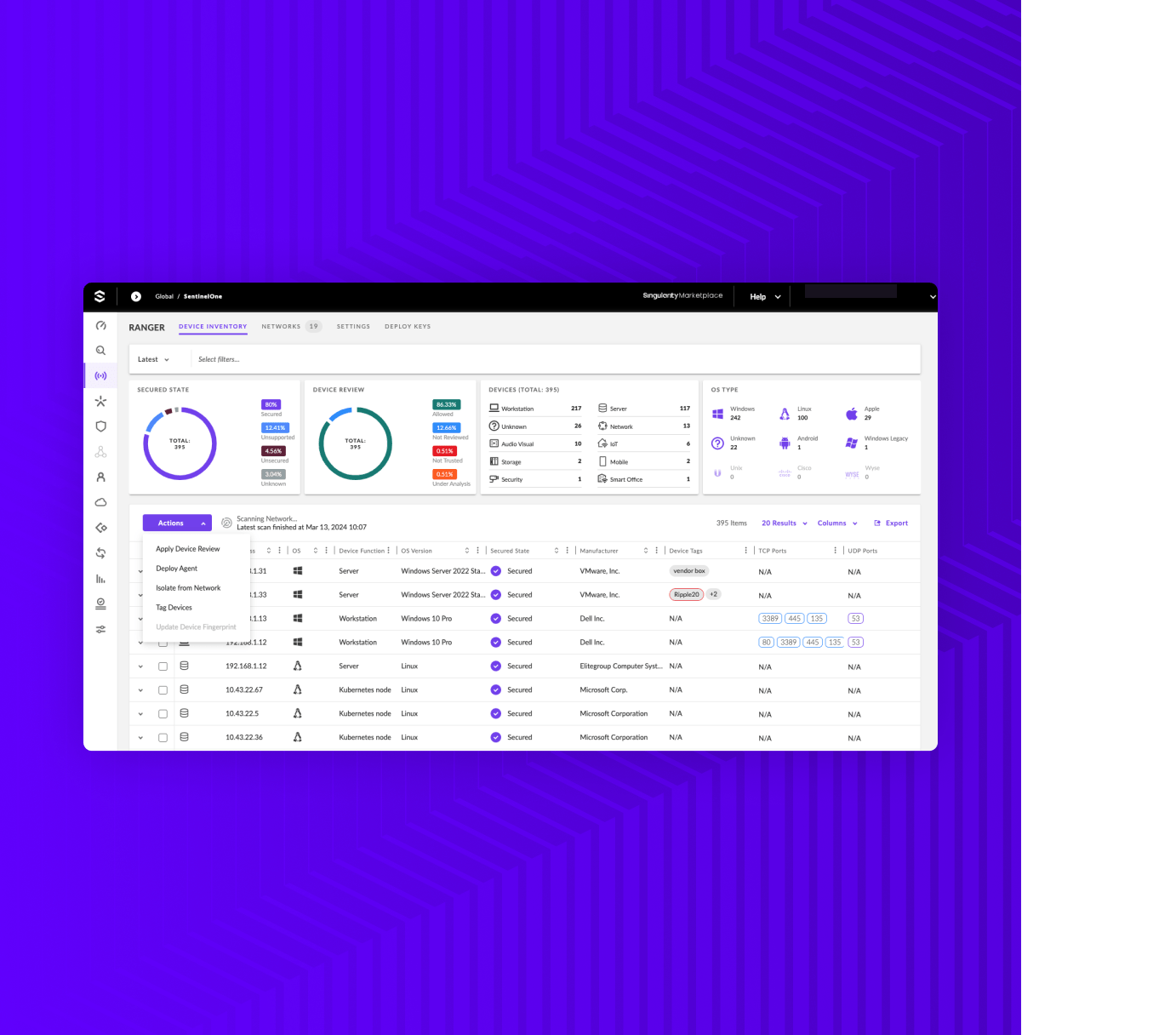
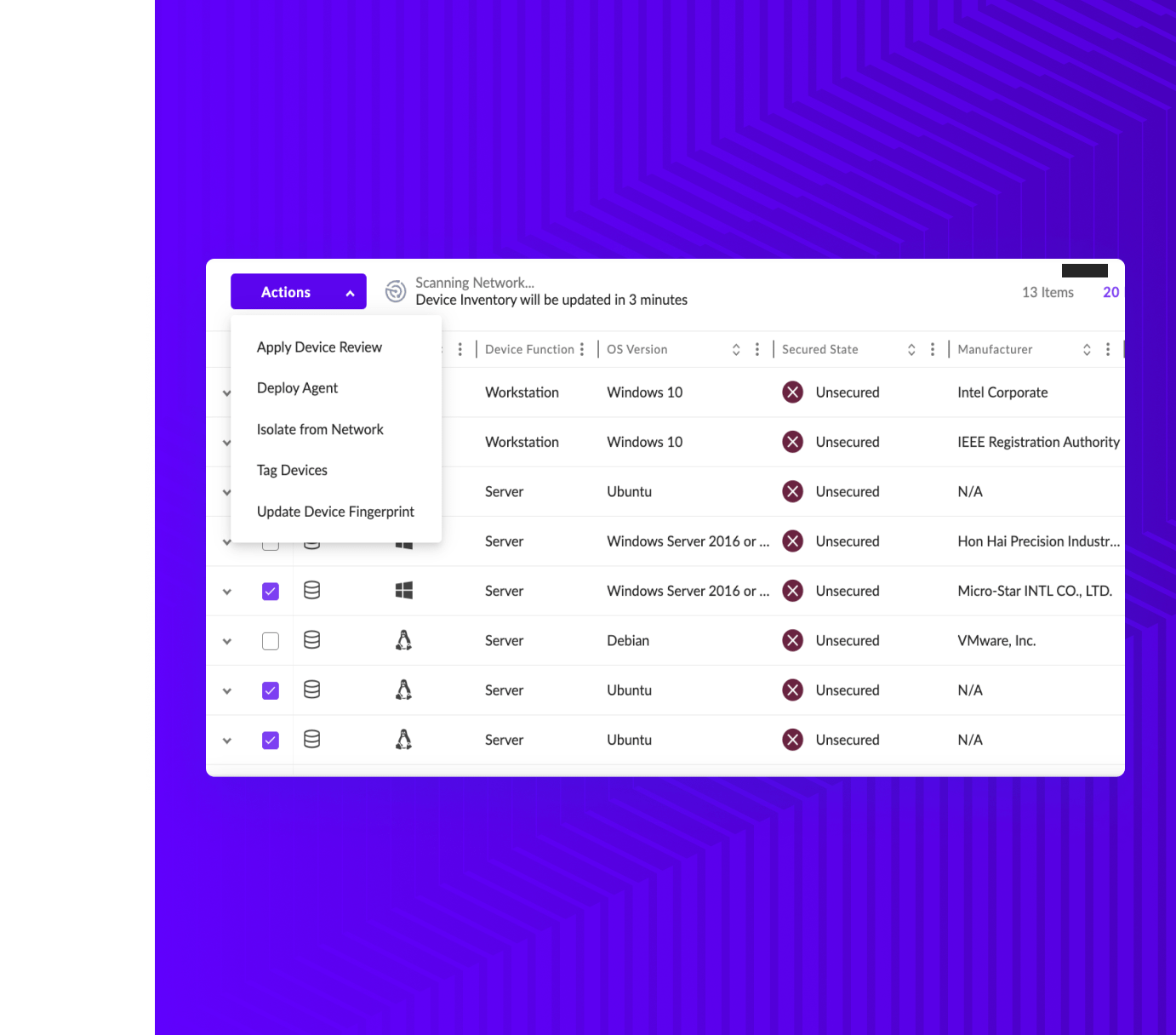
Can I prevent Network Discovery from scanning home, coffee shop, and customer networks when my employees are on the road?
Absolutely yes! Network Discovery policies have several settings to maintain administrative control over what is and is not scanned. A few examples…. You can set a minimum number of Sentinel agents that must be on a subnet before the system event considers it as a possibility. If you set the number at, say 5, small home networks and coffee shops are unlikely to be scanned because you probably will never have 5 managed devices on those networks at any one time. Further, administrators can require an explicit “yes, scan this network” from within the SentinelOne Singularity console to further control what is analyzed.