CSPM
Cloud Security Posture
Management
- Agentless deployment in minutes
- Eliminate misconfigurations
- Easily assess compliance
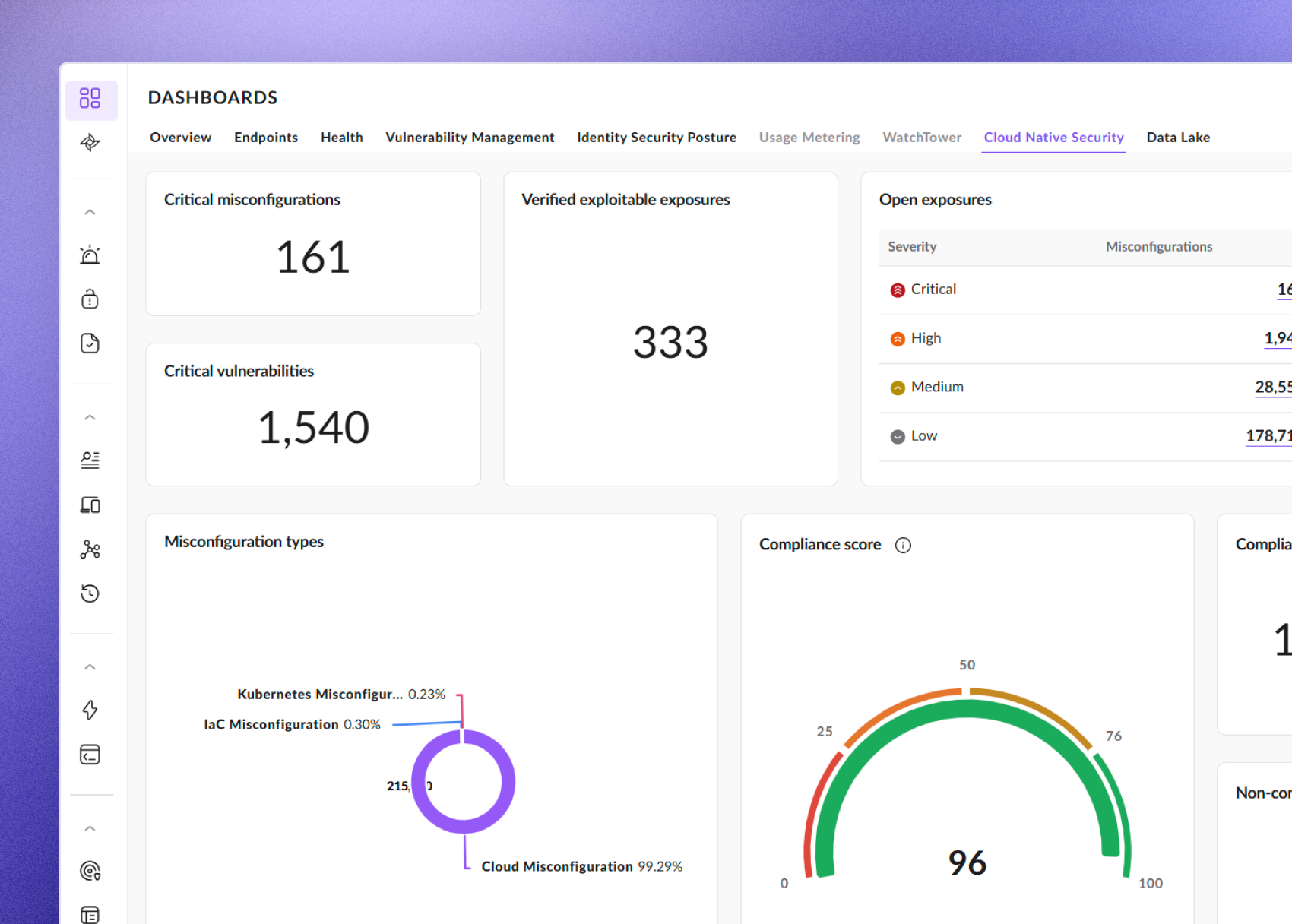
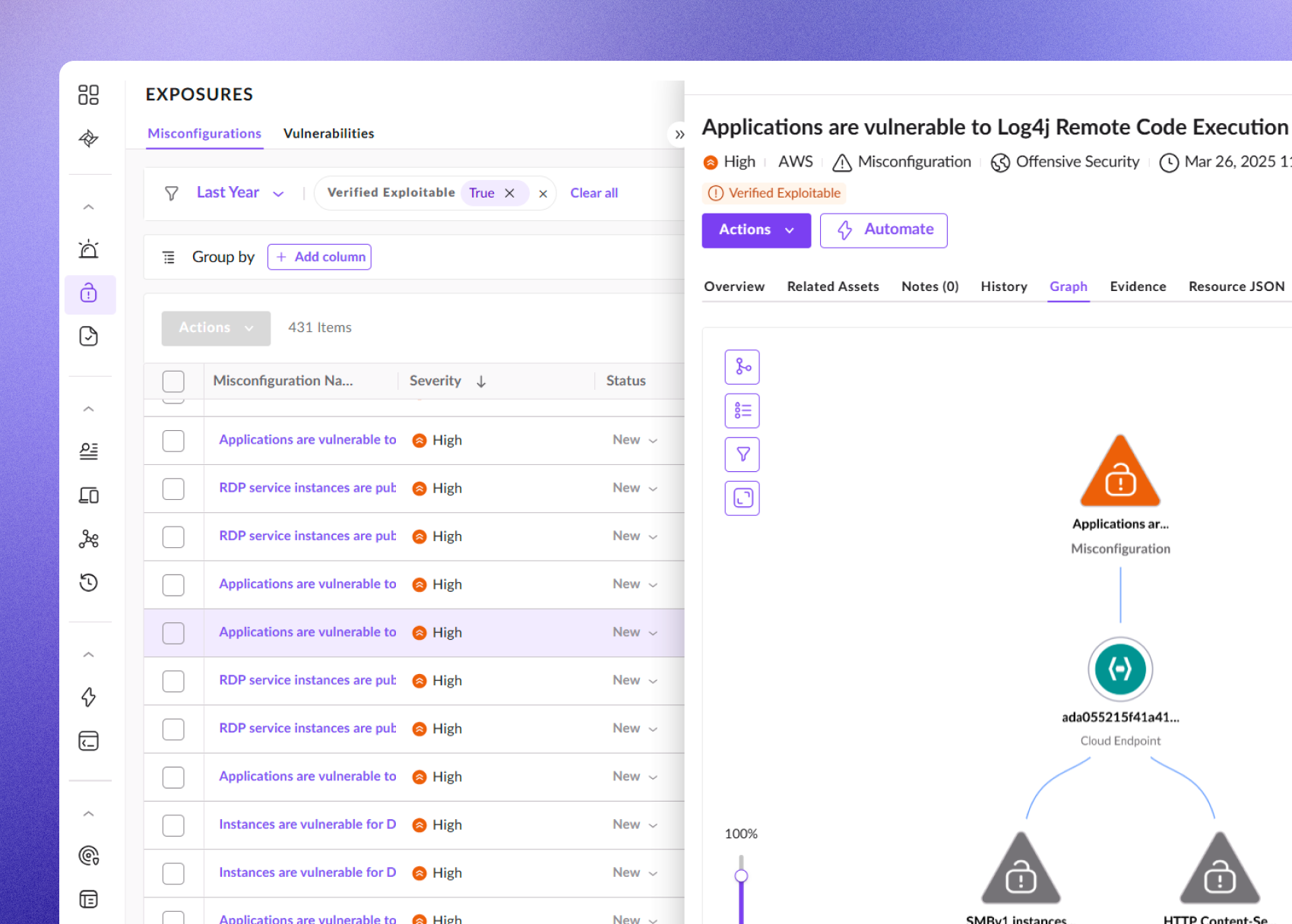
Singularity™ Cloud Security from SentinelOne is the most comprehensive and integrated CNAPP solution available. See what a flexible, cost-effective, and resilient cloud security platform can do for your organization.
Cloud-Native Application Protection Platform
Cloud Security Posture
Management
#1 Ranked Cloud Workload
Protection Platform*
Cloud Detection
& Response
AI Security Posture
Management
Cloud Infrastructure Entitlement
Management
External Attack Surface
& Management
Graph-Based
Asset Inventory
Shift-Left
Security Testing
Container & Kubernetes Security Posture Management
The only CNAPP product to earn a 4.9 out of 5 rating.
Over 240 awards—and counting.
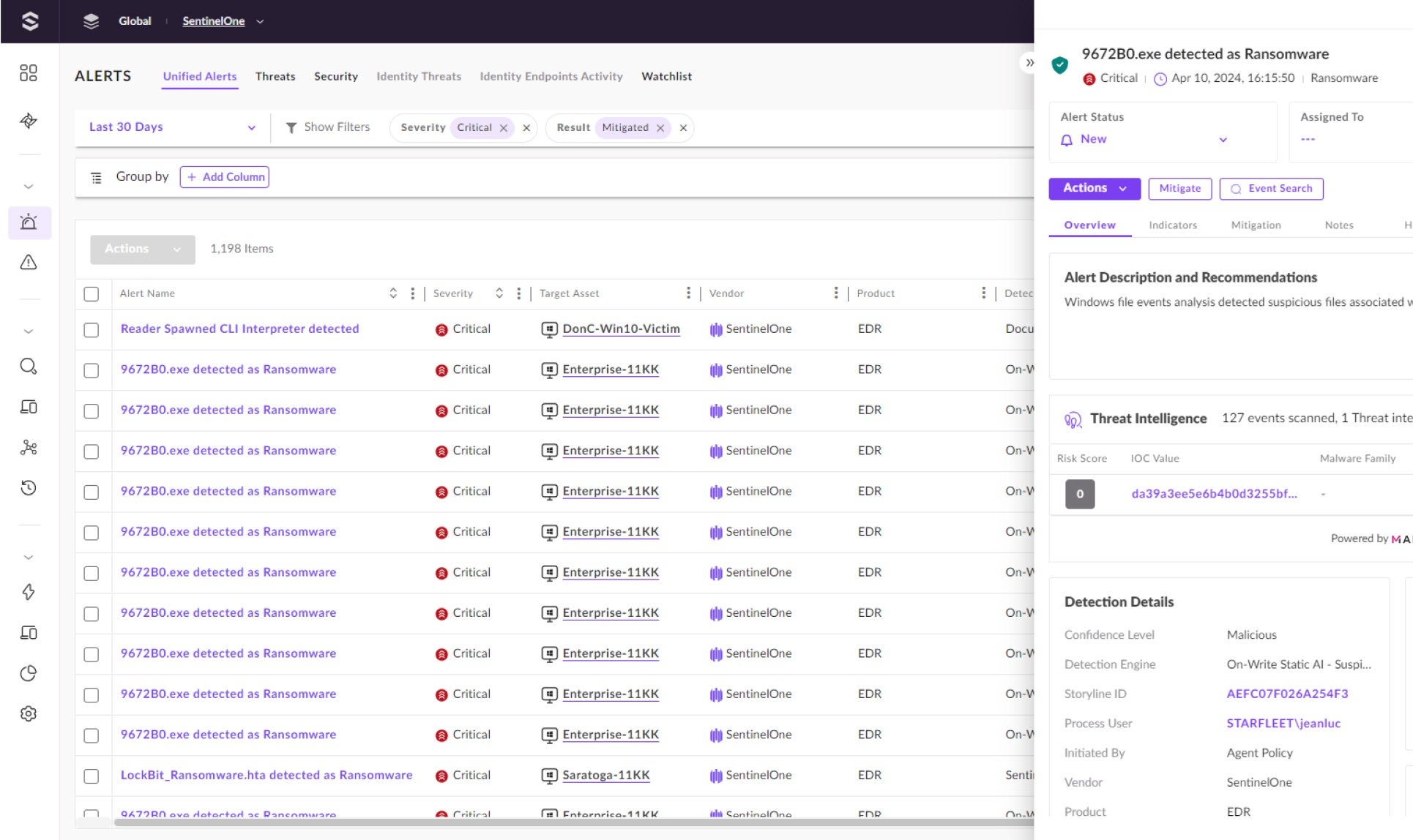
Connect with a SentinelOne expert to see how our AI-powered CNAPP can help you protect your entire cloud estate from build time to runtime.