The Good | Courts Prosecute DPRK Fraud, Ransomware Hosting & Crypto Mixer Ops
Five people have pleaded guilty to helping the DPRK run illicit revenue schemes involving remote IT worker fraud and cryptocurrency theft. The group enabled North Korean operatives to obtain U.S. jobs using false or stolen identities, generating over $2.2 million while impacting 136 companies. The DOJ is also seeking forfeiture of $15 million tied to APT38 cyber-heists. The defendants, Oleksandr Didenko, Erick Prince, Audricus Phagnasay, Jason Salazar, and Alexander Travis, admitted to stealing U.S. identities for overseas workers and laundering stolen funds.
In the U.S., U.K., and Australia, authorities have issued a coordinated sanction against Russian bulletproof hosting (BPH) providers that enable ransomware groups by leasing servers to support malware delivery, phishing attacks, and illicit content hosting. To help cybercriminals evade capture, BPH services ignore abuse reports and law enforcement takedowns. OFAC has sanctioned Media Land, its sister companies, and three executives all tied to LockBit, BlackSuit, Play, and other threat groups. Five Eyes agencies also released guidance to help ISPs detect and block malicious infrastructure used by BPH services.
Our 🆕 joint guidance on bulletproof hosting providers highlights best practices to mitigate potential cybercriminal activity, including recommended actions that ISPs can implement to decrease the usefulness of BPH infrastructure. Learn more 👉 https://t.co/cGQpuLpBPP pic.twitter.com/tM55acfuQv
— CISA Cyber (@CISACyber) November 19, 2025
The founders of Samourai Wallet, a cryptocurrency mixing service, have been sentenced to prison for laundering over $237 million. Operating since 2015, Samourai used its ‘Whirlpool’ mixing system and ‘Ricochet’ multi-hop transactions to obscure Bitcoin flows. These features made tracing more difficult and enabled criminals involved in darknet markets, drug trafficking, and cybercrime to launder more than $2 billion. Authorities seized the platform, including its servers, domains, and mobile app, while the founders agreed to forfeit all traceable proceeds. CEO Keonne Rodriguez has received five years, while CTO William Lonergan Hill received four along with supervised release. The pair were ordered to pay fines of $250,000 each.
The Bad | DPRK Actors Build Fake Job Platform to Lure AI Talent & Push Malware
As part of their ongoing and evolving Contagious Interview campaign, DPRK-based threat actors have created a fake job platform designed to compromise legitimate job seekers, particularly in the AI research, software development, and cryptocurrency verticals. While earlier fraudulent IT-worker schemes relied on targeting individuals through phishing on social media platforms, the latest tactic weaponizes a fully functional hiring pipeline.
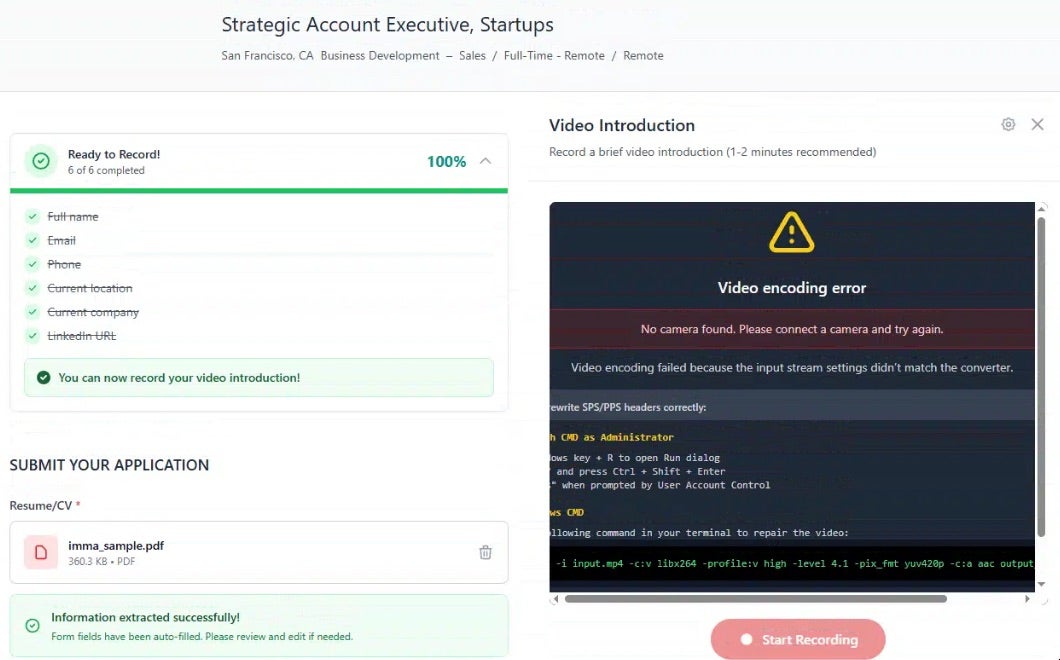
Researchers discovered the latest lure – a Next.js-based job portal hosted at lenvny[.]com, complete with dozens of fabricated AI and crypto-industry job listings. The listings mimic branding from major tech companies and feature a polished UI and full recruitment workflow that mirrors modern hiring systems, encouraging applicants to submit resumes and professional links before prompting them to record a video introduction.
This final step triggers the DPRK-favored ClickFix technique: When applicants copy the fake interview instructions, a hidden clipboard hijacker swaps their text with a multi-stage malware command. When pasted into a terminal, it downloads and executes staged payloads under the guise of a “driver update”, ultimately launching a VBScript-based loader. This design blends seamlessly with typical remote-work interview processes and dramatically increases the likelihood of accidental execution.
The platform also performs strategic filtering, attracting AI and crypto professionals specifically as their skills, network access, and workstation devices tend to align with DPRK’s intelligence and financial priorities including model-training infrastructure to crypto exchange systems. The campaign reflects significant maturation in DPRK social engineering tradecraft, pairing high-fidelity UI design with covert malware delivery. Job seekers are advised to verify domains, avoid off-platform hiring systems, and execute any requested code only in sandboxed environments.
The Ugly | Iran-Backed Actors Weaponize Cyber Recon to Power Real-World Attacks
Iranian-linked threat actors are using cyber operations to support real-world military activity, a pattern described by researchers as “cyber-enabled kinetic targeting”.
In the past, conventional security models separated cyber and physical domains – delineations that are proving artificial in today’s socioeconomic and political climate. Now, these are not just cyber incidents that cause physical impact, but rather coordinated campaigns upon which digital operations are built to advance military objectives.
One example involves Crimson Sandstorm (aka Tortoiseshell and TA456), a group tied to Iran’s Islamic Revolutionary Guard Corps (IRGC). Between December 2021 and January 2024, the group probed a ship’s Automatic Identification System (AIS) before expanding their operations to other maritime platforms. On January 27, 2024, the group searched for AIS location data on one particular shipping vessel. Days later, that same ship was targeted in an unsuccessful missile strike by Iranian-backed Houthi forces, which have mounted repeated missile attacks on commercial shipping in the Red Sea amid the Israel–Hamas conflict.
A second case highlights Mango Sandstorm (aka Seedworm and TA450), a group affiliated with Iran’s Ministry of Intelligence and Security (MOIS). In May, the group set up infrastructure for cyber operations and gained access to compromised CCTV feeds in Jerusalem to gather real-time visual intelligence. Just a month later, the Israel National Cyber Directorate confirmed Iranian attempts to access cameras during large-scale attacks, reportedly to get feedback on where the missiles hit and improve precision. Both highlighted cases show the attackers’ reliance on routing traffic through anonymizing VPNs to prevent attribution.
The divide between digital intrusions and physical warfare continues to blur. With nation state groups leveraging cyber reconnaissance as a precursor for physical attacks, it is likely we will continue to see significant developments in this kind of hybrid warfare.



