The Good | Federal Courts Crack Down on BreachForums & UNC3944 Cybercrime Operators
Conor Brian Fitzpatrick, the 22-year-old operator of the notorious BreachForums hacking site, has been resentenced to three years in prison after a federal appeals court overturned his earlier punishment of time served and supervised release. Known online as “Pompompurin”, Fitzpatrick launched BreachForums in 2022 after the FBI dismantled RaidForums, quickly attracting more than 330,000 members.
The site was a major hub for trading data stolen from telecom providers, healthcare companies, social networks, investment firms, and U.S. government agencies. Fitzpatrick was first arrested in March 2023 and pleaded guilty to being the site’s administrator. Prosecutors sought more than 15 years due to his violations of pretrial conditions, which included secretly using VPNs and unmonitored devices, but the court ultimately imposed a three-year prison term.
Meanwhile, U.K. authorities have advanced their fight against hacking collectives. Two teenagers, 18-year-old Owen Flowers of Walsall and 19-year-old Thalha Jubair of East London, were arrested in connection with the August 2024 cyberattack on Transport for London (TfL). Both are believed to be members of the UNC3944 collective, known most recently for targeting large organizations across multiple verticals.

Flowers faces additional charges for conspiring to breach U.S. healthcare providers, while Jubair has been charged in the U.S. with computer fraud, wire fraud, and money laundering tied to more than 120 global breaches that netted $115 million in ransom. The TfL attack disrupted internal operations, delayed refunds, and exposed customer data including names, addresses, and contact details. Previous arrests in July linked UNC3944 to cyberattacks on major UK retailers such as Harrods and Marks & Spencer.
The Bad | China-Linked TA415 Uses U.S.-China Trade Lures in Targeted Espionage Campaigns
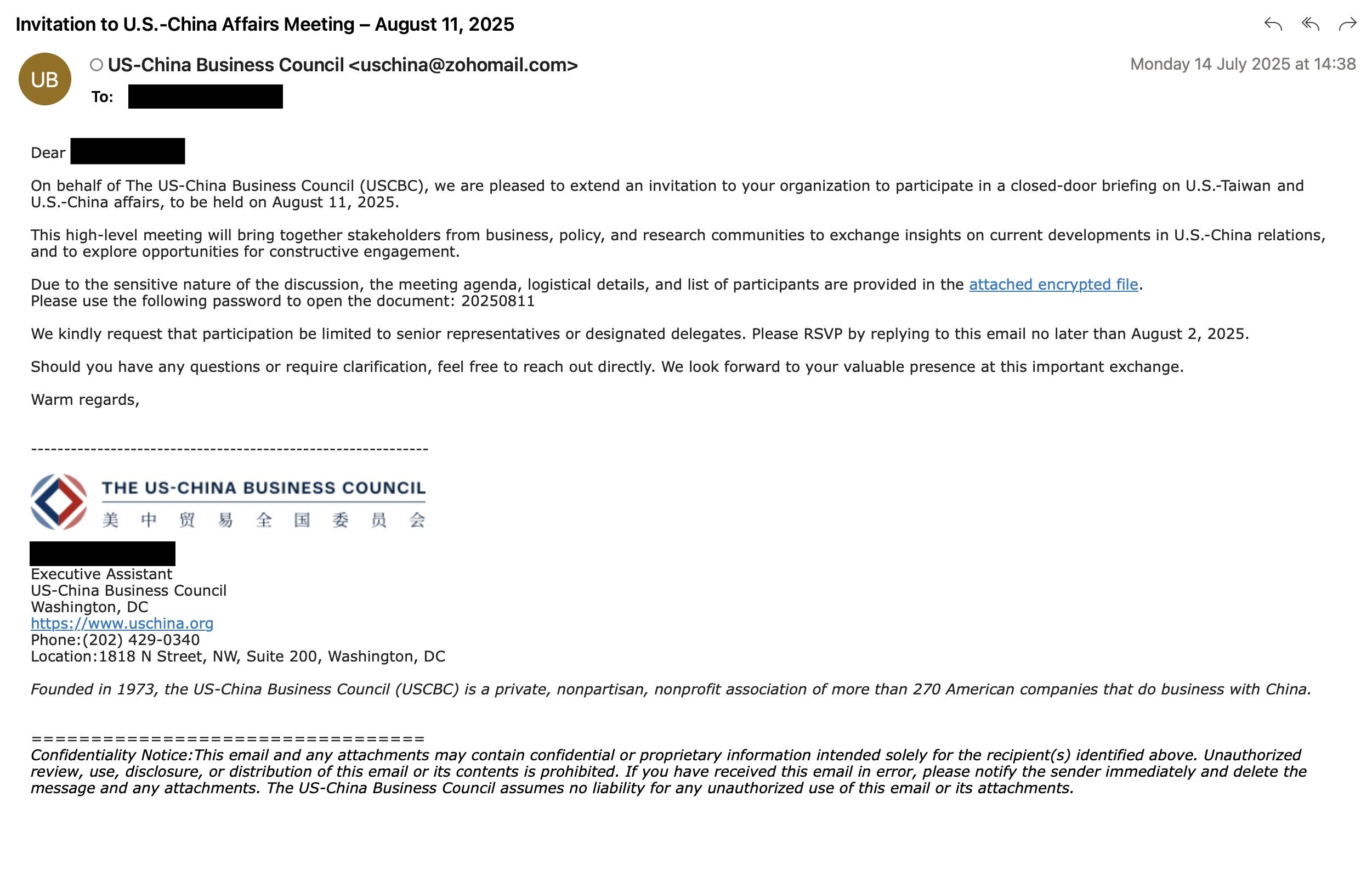
A Chinese state-sponsored threat actor known as TA415 has been linked to a string of spearphishing attacks against U.S. government entities, think tanks, and academic institutions in July and August. The campaign tailored its lures by using U.S.-China economic and trade topics, even impersonating the U.S.-China Business Council and the Chair of the House Select Committee on Strategic Competition to target individuals focused on relations and policy between the two nations.
Emails appeared to invite recipients to closed-door briefings and were sent from uschina@zohomail[.]com, with links to archives hosted on Zoho WorkDrive, Dropbox, and OpenDrive. These archives contained a decoy PDF and a Windows shortcut (LNK) file, which executed a batch script that deployed WhirlCoil, an obfuscated Python loader. The malware was able to establish persistence via scheduled tasks and open Visual Studio Code Remote Tunnels to grant attackers backdoor access and enable arbitrary command execution.
The collected data, including system information and user files, was exfiltrated through request logging services in base64-encoded HTTP POST requests. While early variants downloaded WhirlCoil components from Pastebin and Python.org, the infection chain has remained largely consistent since its first noted use in 2024 against aerospace, insurance, and manufacturing firms.
The continued abuse of Visual Studio Code Remote Tunnels highlights the challenge for defenders: since the feature is legitimate, it blends into normal developer workflows, and is hard to detect without specific monitoring. Analysts note that TA415, which overlaps with APT41, has gradually refined this technique over the past year, ramping up activity in recent months as U.S.-China trade negotiations intensify.
The Ugly | Chaos Mesh Vulnerabilities Put Kubernetes at Risk of Full Cluster Takeovers
Researchers have revealed multiple critical flaws in Chaos Mesh, an open-source Chaos Engineering platform for Kubernetes designed to simulate, test, and identify potential weak spots in pods, networks, and other components. If exploited, the four vulnerabilities, collectively named Chaotic Deputy, could allow attackers to take over entire clusters.
The report warned that attackers need only minimal in-cluster network access to exploit the vulnerabilities, enabling them to run fault injections, shut down pods, disrupt communications, and even steal privileged tokens for further attacks.
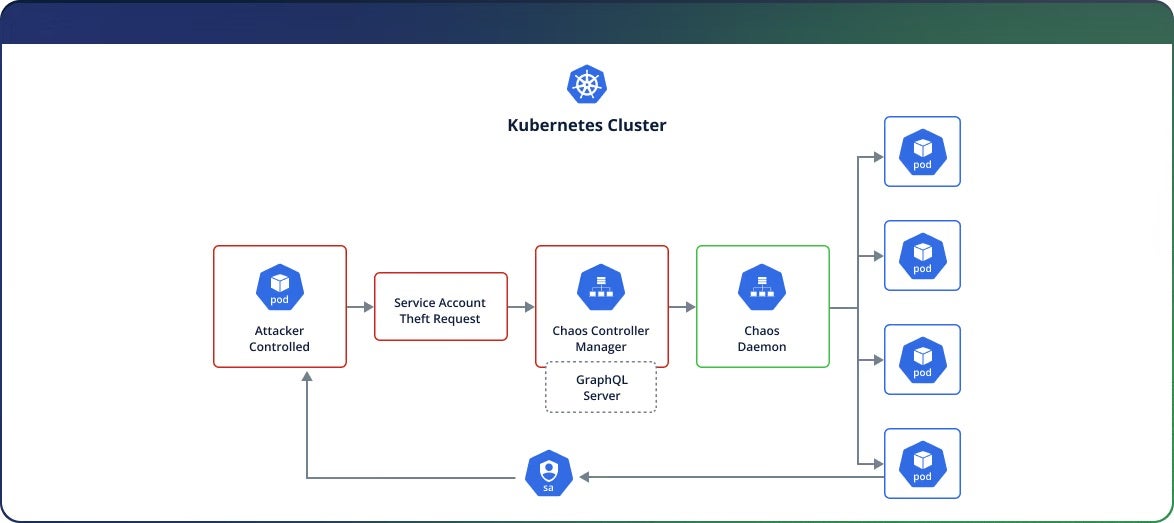
CVE-2025-59358 (CVSS 7.5) exposes an unauthenticated GraphQL debugging server that lets attackers kill arbitrary processes in any Kubernetes pod, which could lead to cluster-wide denial-of-service. CVE-2025-59359, CVE-2025-59360, CVE-2025-59361 (all, categorized as CVSS 9.8) are command injection flaws in the Chaos Controller Manager’s GraphQL mutations (cleanTcs, killProcesses, and cleanIptables, respectively) that allow remote code execution (RCE).
Chaotic Deputy stems from insufficient authentication in the Chaos Controller Manager’s GraphQL server. An in-cluster attacker with initial access to a network could chain the four vulnerabilities to execute arbitrary commands on the Chaos Daemon, achieving full cluster compromise. The result could mean data theft, service disruption, and lateral movement across Kubernetes environments.
The flaws were responsibly disclosed in early May and patched in Chaos Mesh version 2.7.3, released August 21. Users are strongly urged to upgrade immediately, and if patching isn’t possible, mitigations include restricting network traffic to the Chaos Mesh daemon and API server as well as avoiding deployments in open or weakly secured environments.
Researchers stressed that while Chaos Engineering platforms offer the ability to test resilience, their deep cluster access and flexibility makes them a high-value target and vulnerabilities like Chaotic Deputy can be especially risky if left unpatched.


