The Good | FBI Seizes Chaos Ransomware Bitcoin as CISA Launches Thorium for Scalable Malware Analysis
Over 20 Bitcoins, worth more than $1.7 billion, are now in the possession of the FBI, following their seizure of a cryptocurrency wallet belonging to a Chaos ransomware affiliate named “Hors”. The funds have since been traced to ransomware payments, resulting in the U.S. Department of Justice filing a civil forfeiture complaint to permanently claim the assets.
Today, FBI Dallas made public the seizure of over $1.7 million worth of cryptocurrency as part of ongoing efforts to combat ransomware. The seized funds were traced to a cryptocurrency address allegedly associated with a member of the Chaos ransomware group, known as “Hors,” who… pic.twitter.com/uWeIMMGE9J
— FBI Dallas (@FBIDallas) July 28, 2025
Chaos ransomware is considered a rebrand of the BlackSuit group as well as a partial-successor to the defunct Conti gang, but unrelated to any older, low-tier Chaos variants. Security researchers have tied the new Chaos operation to BlackSuit based on its tools, encryption, and ransom notes. The FBI’s Bitcoin seizure follows law enforcement’s takedown of BlackSuit’s dark web infrastructure, which likely exposed the wallet connected to Hors.
From CISA this week, an open-source platform named “Thorium” was publicly released with the goal of helping government, private sector, and research teams automate malware and forensic investigations. Thorium was developed in conjunction with Sandia National Laboratories and can process over 10 million files per hour in addition to handling 1,700 tasks per second per permission group. This streamlines complex incident response and malware analysis workflows.
Thorium works by integrating commercial, open-source, and custom tools as Docker images, supports secure group-based permissions, and scales with Kubernetes and ScyllaDB to meet workload demands. Security teams can use it to tag and search results, share tools, and automate large-scale binary and digital artifact analysis.
The platform is available on CISA’s GitHub, joining recent public tools like the Eviction Strategies Tool and Malware Next-Gen, all furthering CISA’s mission to strengthen collective cyber defense capabilities.
The Bad | SentinelLABS Uncovers Patents Exposing Hafnium’s Expansive MSS-Linked Capabilities
SentinelLABS has identified more than ten patents for advanced forensics and data collection tools tied to the Chinese state-linked threat actor, Hafnium, highlighting the complexity of China’s cyber contracting ecosystem. Hafnium’s capabilities, many of which were previously unreported, include acquisition of encrypted endpoint data, mobile forensics, router and network traffic collection, and specialized software for decrypting hard drives.
The findings build on the DoJ’s indictment of two hackers: Xu Zewei and Zhang Yu, as well as the U.S. Treasury’s sanction of Yin Kecheng and Zhou Shuai. Xu and Zhang allegedly worked under the Shanghai State Security Bureau (SSSB) via Shanghai Powerock and Shanghai Firetech, while Yin and Zhou operated through Shanghai Heiying and the broker firm i-Soon. This tiered contractor model shows how the Ministry of State Security (MSS) leverages private firms for offensive cyber operations, sometimes spanning multiple regions beyond Shanghai.
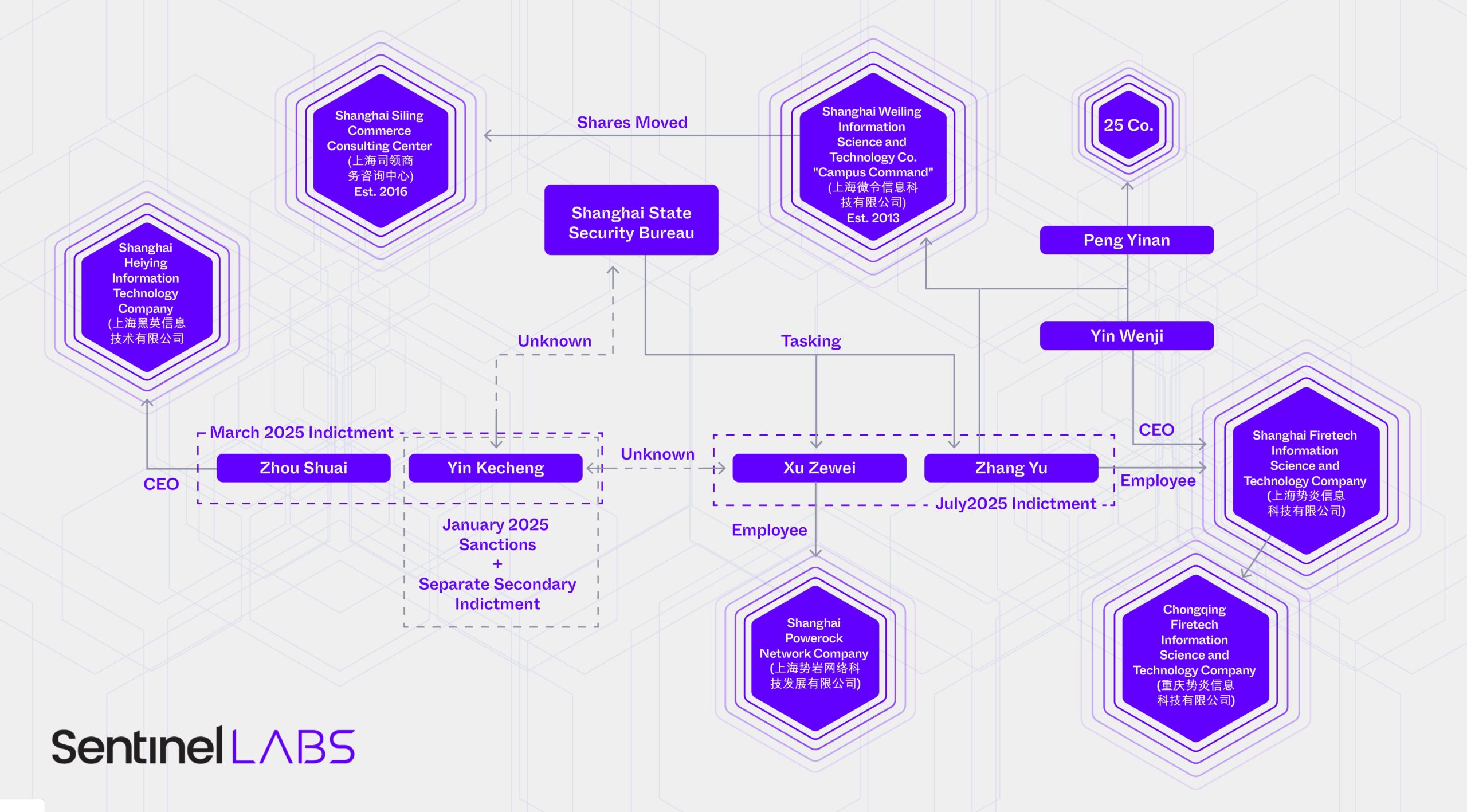
Hafnium (aka Silk Typhoon) first rose to prominence in 2021 for exploiting Microsoft Exchange Server (MES) zero-days, which led to opportunistic attacks by other Chinese groups and the first ever joint statement from the U.S., U.K., and E.U. Subsequent research and leaked i-Soon chats revealed a layered ecosystem with low-tier contractors like i-Soon, mid-tier firms like Chengdu 404, and elite outfits like Firetech that are trusted with direct MSS tasks.
The 10+ patents filed by Shanghai Firetech suggest the company possesses far broader capabilities than publicly attributed to Hafnium. These tools may support human intelligence (HUMINT)-style close access operations and could have been provided to other MSS regional offices, complicating attribution. The findings, as a whole, show that threat actor labels track activity clusters, while true attribution requires tracing operations back to the people and companies executing them.
The Ugly | Secret Blizzard Exploits ISP-Level Access & SORM to Spy on Moscow Diplomatic Missions
Secret Blizzard (aka Turla or Waterbug) is conducting cyber-espionage operations against diplomatic missions in Moscow. Researchers note that the Russian Federal Security Service (FSB)-linked group is exploiting an adversary-in-the-middle (AiTM) position at the internet service provider (ISP) level in order to leverage Russia’s SORM surveillance system to intercept traffic and deploy custom ApolloShadow malware.

Attackers have been observed redirecting victims to captive portals where they are prompted to download a malware-laced antivirus installer. Once executed, ApolloShadow installs a forged trusted root certificate masquerading as Kaspersky anti-virus, enabling the compromise of encrypted connections and the long-term monitoring of diplomatic networks. This allows Secret Blizzard to spoof legitimate sites, decrypt traffic, and maintain persistent access to diplomatic and governmental networks. Researchers found this to be the first observed instance of Secret Blizzard conducting ISP-level espionage with special focus on targeting foreign embassies, diplomatic entities, and sensitive organizations in Moscow that rely on local providers.
While discovered in February 2025, the campaign has been active since at least 2024. It also represents a high-risk threat to embassies and sensitive organizations in Moscow. By combining network-level interception, certificate forgery, and custom malware delivery, Secret Blizzard achieves long-term surveillance and intelligence collection without relying on traditional spear-phishing or direct network intrusion.
Secret Blizzard, linked to Russia’s FSB Center 16, is one of the longest-operating advanced persistent threats (APTs), active since the 1990s, and responsible for global campaigns targeting embassies, defense organizations, and research institutions. This latest campaign demonstrates the group’s adaptability and sophistication, using local ISP-level access and Russia’s domestic surveillance ecosystem to maintain covert, long-term access for intelligence gathering against high-profile diplomatic targets.


