The era of evaluating AI on its potential is over. For CISOs, the only conversation about AI worth having in cybersecurity is about proven performance. The executive mandate is clear – every leader is being asked how they are using AI to get better, faster, and more profitable. For CISOs, this pressure transforms the conversation from if they should adopt AI to how to do it right. The right AI investment is one that strengthens the business by delivering faster threat containment, creating more efficient security teams, and providing a quantifiable reduction in overall risk.
In a landscape where every vendor claims AI supremacy, the measure of a platform’s worth is not its model size or an arbitrary LLM benchmark, but its ability to deliver on those business imperatives. It’s time to move beyond the hype and focus on the results of implementing AI for security operations.
Security teams face unprecedented pressure from a growing volume, complexity, and speed of cyberattacks – it’s more noise, more work, more risk. Tried-and-true security methods and manual workflows are struggling to keep pace, resulting in overwhelmed analysts, overlooked alerts, and greater organizational risk. In response, security teams not only need new tools, but also a fundamental shift in how they approach security.
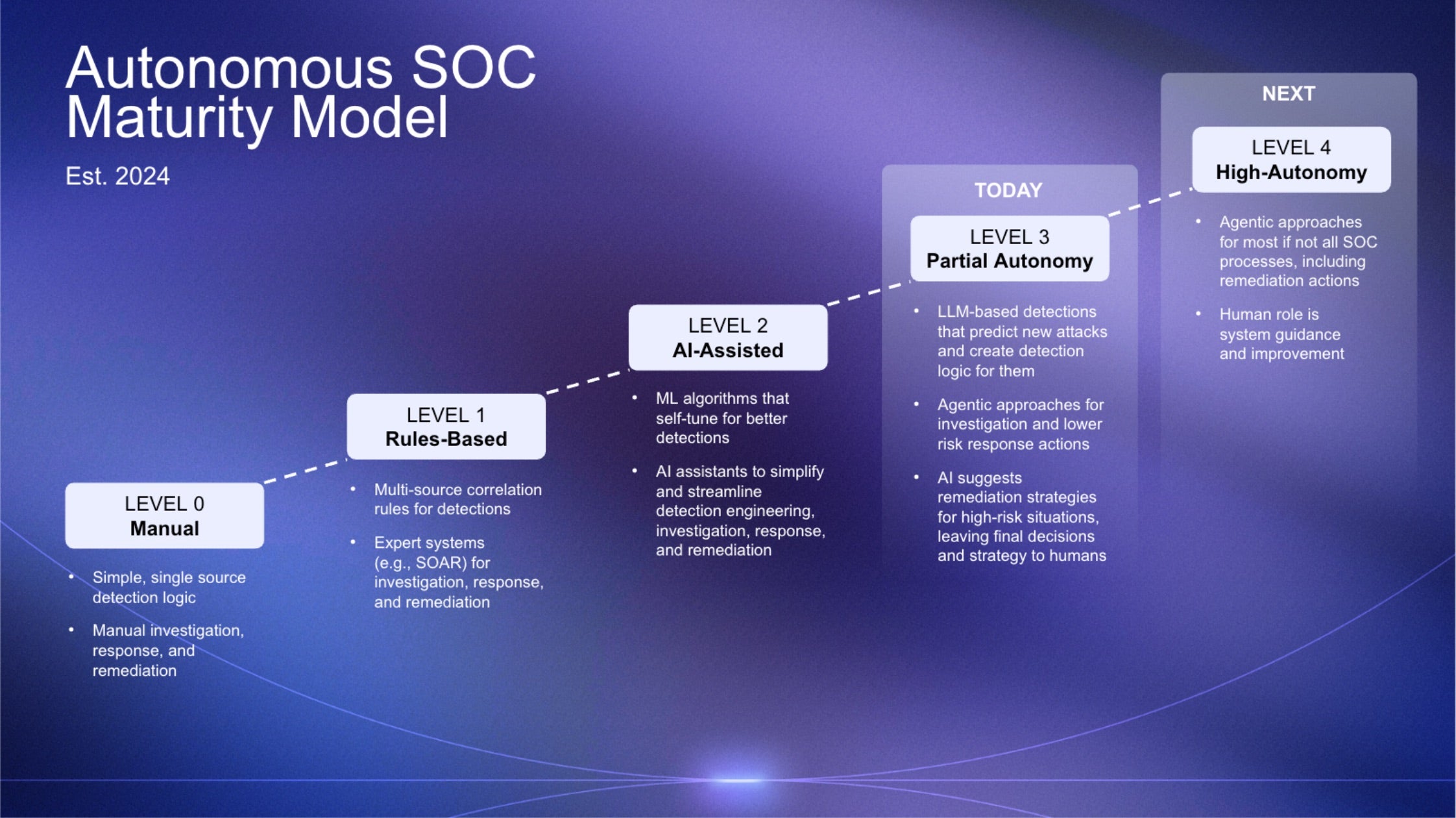
To guide this transformation, SentinelOne created the Autonomous SOC Maturity Model, a framework showing how advanced generative and agentic AI are essential to augment human expertise, analyze data, and automate workflows to counter threats at machine speed.
Discerning Genuine AI Value from Market Noise
For CISOs, the challenge lies in cutting through the deafening market noise to identify actual AI-driven value. True AI value manifests when organizations can accelerate their threat detection and response times while reducing critical metrics such as MTTD and MTTR. By automating routine and repetitive tasks, AI enables experienced analysts to focus their expertise on proactive threat hunting and deeper investigation.
Organizations implementing AI in their security programs aim for substantial gains in efficiency, demonstrably lower risk, and a reduction in the probability and severity of security incidents. Tools driven by AI become essential to security teams when they improve the analyst workflow and provide security professionals of all levels with amplified capabilities. Most people are now familiar with generative AI: tools that help assist you with work.
In security, that means generating readable content from raw data (incident summaries, queries, investigative insights) to help an analyst understand what’s happening faster. It’s about speeding up comprehension. Agentic AI goes further. This isn’t about just providing assistance, it’s about systems that can do the work. Advanced AI systems, particularly those that leverage agentic capabilities, can now handle data recall and correlation, and even initiate decision-making steps with precision, enabling teams to respond faster and more accurately.
The most effective AI complements and amplifies human expertise and vice versa, driving towards a more resilient security posture. Ultimately, the goal of a well-designed AI system is where the human role is elevated to strategic oversight and supervision of AI actions, applying their expertise and deep institutional knowledge of tools and processes in a more effective way. The role of the analyst shifts from manually triaging and investigating a queue of alerts to applying their expertise for the supervision of an autonomous system. AI agents can reason through multi-step tasks, decide on next actions, prioritize what matters most, and move workflows forward autonomously, while maintaining transparency and keeping a human in the loop.
Navigating the AI Maze: What CISOs Should Look For In AI Tools
Navigating the AI vendor landscape is challenging. Use this checklist to prioritize solutions that deliver smarter, faster, and more integrated security, ensuring you invest in true value, not just hype.
✔️ 1. Does It Deliver Unified, Actionable Visibility?
- Can the AI break down data silos by ingesting and correlating intelligence from my entire security landscape, including endpoints, cloud workloads, identities, firewall, SASE, and threat intelligence feeds?
- Does it provide a single, unified view to turn disparate data points into actionable insights?
✔️ 2. Does It Support Open Standards for Better Detection?
- Does the platform adopt open standards for data normalization, like the Open Cybersecurity Schema Framework (OCSF)?
- Will this result in more accurate, context-rich threat detection by ensuring all my security tools speak the same language?
✔️ 3. Does It Drive Action and Containment?
- Does the AI move beyond simply identifying issues to actively helping my team contain them?
- Can it transform raw telemetry into clear intelligence that drives automated response actions or provides prioritized, guided pathways to remediation?
✔️ 4. Does It Empower Analysts and Foster Autonomy?
- Is the AI designed to simplify complexity and empower analysts of all skill levels, reducing alert fatigue and freeing up human talent for the most critical threats?
- Does it help my team move towards a more autonomous operational model?
✔️ 5. Does It Act as a True Force Multiplier?
- Does the platform leverage both generative AI (for insights and understanding) and agentic AI (for autonomous actions and decision-making)?
- Is there clear evidence that the AI continuously learns, adapts, and enhances the capabilities and efficiency of my security team?
From Anecdote to Evidence: Outcomes of AI Deployments
Confronted with these challenges and choices, how can security leaders separate credible AI solutions from the hype? The answer lies in data-driven evaluations and an honest look at real-world implementations. Security leaders should evaluate solutions that demonstrate how advanced AI capabilities translate into measurable security and business outcomes.
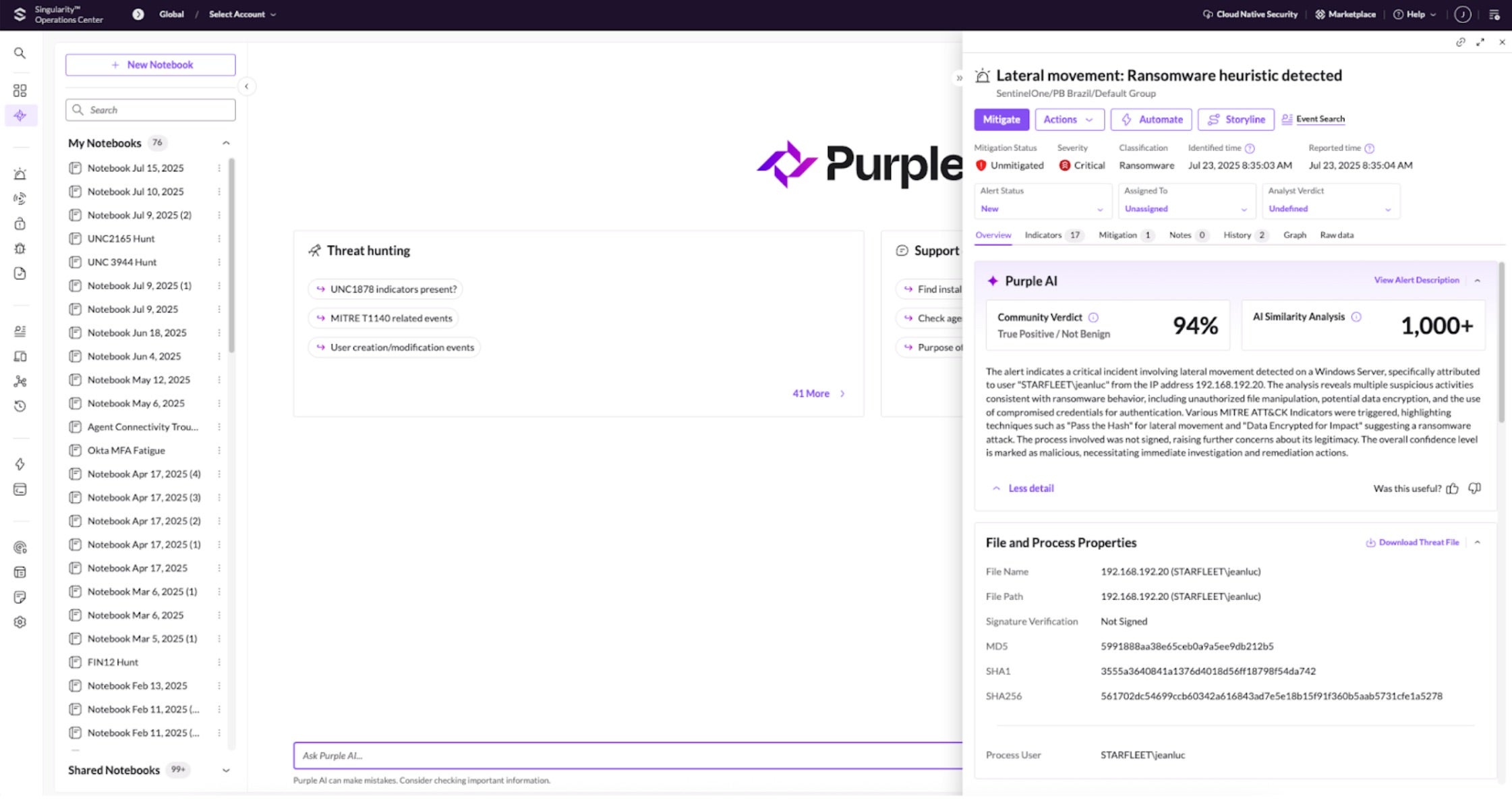
A recent IDC white paper, “The Business Value of SentinelOne Purple AI” [1] offers precisely this kind of quantitative evaluation. IDC conducted in-depth interviews with organizations using SentinelOne’s Purple AI, a solution that leverages cutting-edge generative AI and agentic AI to accelerate workflows like investigation, hunting, triage, and response.
The findings from these real-world deployments provide compelling insights into the tangible benefits AI can deliver when aligned with the needs of security leaders for speed, efficiency, and risk reduction. With the Singularity Platform and Purple AI, customers experienced significant improvements:
- 63% faster to identify and 55% faster to resolve security threats, meaning incidents are contained in minutes, not hours.
- Security teams became 38% more efficient, allowing them to support 61% more endpoints per team member.
- A 338% three-year ROI with a payback period of just four months.
These customer outcomes are attributed to Purple AI’s capabilities, including natural language querying, automated event summarization, suggested next investigation steps, and the automation provided by its agentic AI features like Auto-Triage. Organizations found that Purple AI enabled them to enhance their security operations, become more operationally efficient, and improve overall security outcomes, reducing operational risk and increasing business confidence.
Don’t just take our word for it – hear from existing Purple AI customers featured in the report about how they:
- Enhanced Security Operations: “Being able to ask a native question with SentinelOne Purple AI without needing to know specific keywords or learn new syntax is a massive force multiplier, saving us a lot of time.”
- Improved Operational Efficiency: “With Purple AI, we don’t have to scale our security expert team. At this point, we are avoiding hiring and we’ll be able to leverage our existing application teams.”
- Realized Risk Reduction: “Having Purple AI has been instrumental in improving our operational maturity. It allows us to conduct investigations with specificity, making informed decisions around security posture and ensuring nothing sneaks into our environment.”
- Increased Business Confidence: “In terms of innovation, I think it will potentially help us take more risks in the future because we’ll have more confidence.”
Beyond the Buzz: Judge for Yourself
When AI – incorporating both generative and agentic strengths – is thoughtfully implemented to address the demands of security teams, it moves the needle for security operations in a very real and measurable way. The key is to look past the marketing slogans and focus on validated outcomes. Generative and agentic AI will undoubtedly shape the future of the security operations center, and CISOs must move from cautious curiosity to strategic adoption.
Is AI a distraction or your next competitive advantage? Get the definitive answer in our on-demand webinar, Beyond the Buzz: Separating AI Hype from Security Outcomes. We present IDC’s quantitative evaluation of real AI implementations and feature insights from current Purple AI customers, IDC Research Vice President Chris Kissel, and SentinelOne’s Senior Director of Product Management Adriana Corona.
To learn more about how to transform security operations with Purple AI’s revolutionary approach to the Autonomous SOC, visit our web page or request a demo from a product expert.
[1] IDC Business Value White Paper, sponsored by SentinelOne, The Business Value of SentinelOne’s Purple AI, #US53337725, July 2025