Knight Ransomware: In-Depth Analysis, Detection, and Mitigation
What Is Knight Ransomware?
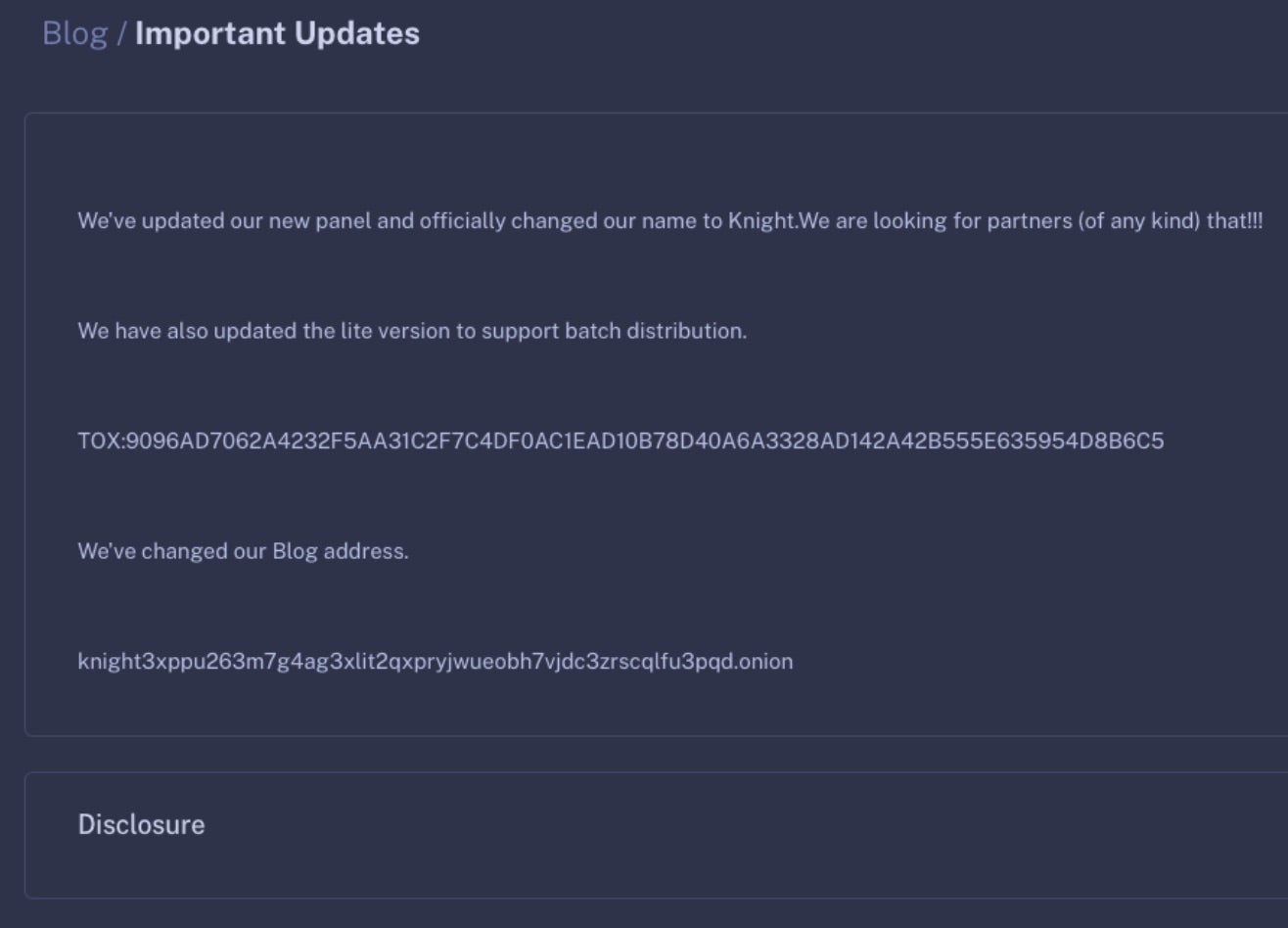
Knight ransomware operations emerged in August of 2023 as an evolution of Cyclops ransomware. The threat operator offers payloads in both normal and ‘lite’ versions. Knight ransomware operates as a multi-extortion group, hosting a TOR-based blog to list victim names along with any exfiltrated data. Victims are aggressively coerced into payment so as to avoid having their data leaked publicly. Knight has been actively advertised and sold on the RAMP forum.

What Does Knight Ransomware Target?
Knight operates as a RaaS (Ransomware-as-a-Service). Individual ransomware operators do not discriminate when it comes to victimology outside of targeting enterprise and SMB environments. The same holds true for the previous iteration of this ransomware, Cyclops.
How Does Knight Ransomware Work?
Knight ransomware is delivered primarily through phishing and spear phishing campaigns. Some early examples include those masquerading as messages from TripAdvisor. Individual threat actors (affiliates) have multiple options available through the Knight RaaS program. Encryptor payloads are available for Windows as well as Linux/ESXi and macOS.
In July of 2023, it was formally announced that Cyclops was changing their name and branding to “Knight”. Requisite updates to their available encryptors were made as well. This includes the continuation of the specialized stealer tools developed during the Cyclops era. The ‘lite’ version or “Knight Lite” is also available to affiliates and is meant for more broader, non-targeted spam-based attacks. The administration panel also offers Knight affiliates control over the financial side of the attacks. The portal can be used as a bank of sorts for attackers to efficiently access and withdraw their funds at will.
Knight affiliates are provided with a builder, extended toolsets, and panel access to create payloads and manage campaigns. Generated Knight payloads support multiple command line options. These include:
| Parameter | Function |
| .exe (with no parameters) | Encrypt all local and SMB-attached drive volumes. |
| -m local | Mode: Local disk only mode |
| -m net | Mode: network (SMB) volumes only mode |
| -p (path) | Path: path of files to encrypt |
| -h (host.txt) | Remote hosts: Text file input for hosts to infect |
Knight ransomware notes are written to each folder containing encrypted items. The notes are named “How to Restore Your Files.txt”. Ransom notes for Knight campaigns may include specific ransom demands as well as BTC (Bitcoin) addresses for payment.
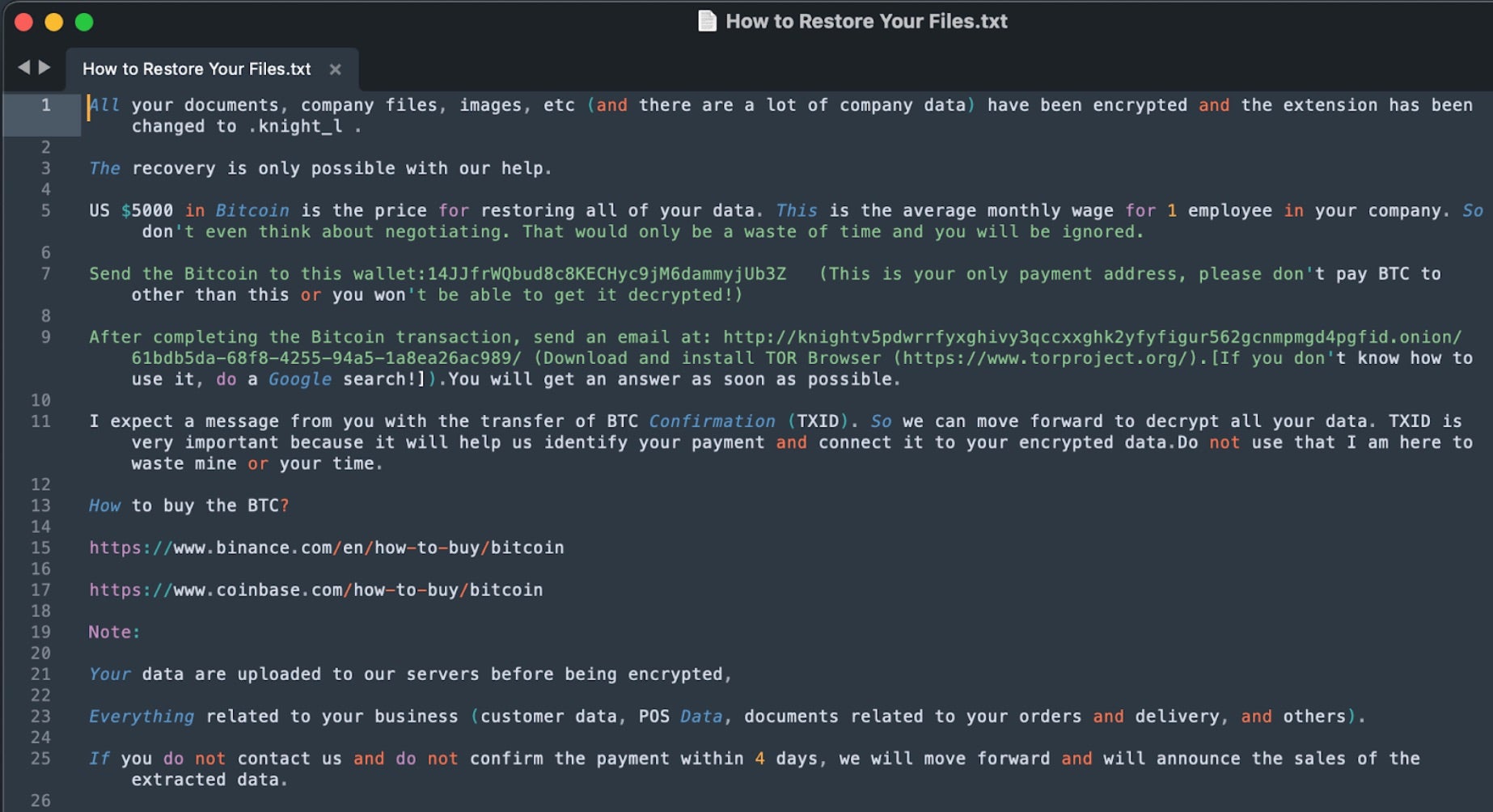
Victims are required to visit a unique TOR-based URL to receive an email address. That address is then used to obtain further instructions and carry out any additional communications between the victim and attacker. Upon encryption, files will have a “.knight”, “.knightl”, or “.knight_l” extension. The “l” character is appended when infected by “Knight Lite” payloads.
How to Detect Knight Ransomware
The SentinelOne Singularity XDR Platform can identify and stop any malicious activities and items related to Knight ransomware.
In case you do not have SentinelOne deployed, detecting Knight ransomware requires a combination of technical and operational measures designed to identify and flag suspicious activity on the network. This allows the organization to take appropriate action, and to prevent or mitigate the impact of the ransomware attack.
To detect Knight ransomware without SentinelOne deployed, it is important to take a multi-layered approach, which includes the following steps:
- Use anti-malware software or other security tools capable of detecting and blocking known ransomware variants. These tools may use signatures, heuristics, or machine learning algorithms, to identify and block suspicious files or activities.
- Monitor network traffic and look for indicators of compromise, such as unusual network traffic patterns or communication with known command-and-control servers.
- Conduct regular security audits and assessments to identify network and system vulnerabilities and ensure that all security controls are in place and functioning properly.
- Educate and train employees on cybersecurity best practices, including identifying and reporting suspicious emails or other threats.
- Implement a robust backup and recovery plan to ensure that the organization has a copy of its data and can restore it in case of an attack.
How to Mitigate Knight Ransomware
The SentinelOne Singularity XDR Platform can return systems to their original state using either the Quarantine or Repair.
In case you do not have SentinelOne deployed, there are several steps that organizations can take to mitigate the risk of Knight ransomware attacks:
- Educate employees: Employees should be educated on the risks of ransomware, and on how to identify and avoid phishing emails, malicious attachments, and other threats. They should be encouraged to report suspicious emails or attachments, and to avoid opening them, or clicking on links or buttons in them.
- Implement strong passwords: Organizations should implement strong, unique passwords for all user accounts, and should regularly update and rotate these passwords. Passwords should be at least 8 characters long, and should include a combination of uppercase and lowercase letters, numbers, and special characters.
- Enable multi-factor authentication: Organizations should enable multi-factor authentication (MFA) for all user accounts, to provide an additional layer of security. This can be done through the use of mobile apps, such as Google Authenticator or Microsoft Authenticator, or through the use of physical tokens or smart cards.
- Update and patch systems: Organizations should regularly update and patch their systems, to fix any known vulnerabilities, and to prevent attackers from exploiting them. This includes updating the operating system, applications, and firmware on all devices, as well as disabling any unnecessary or unused services or protocols.
- Implement backup and disaster recovery: Organizations should implement regular backup and disaster recovery (BDR) processes, to ensure that they can recover from ransomware attacks, or other disasters. This includes creating regular backups of all data and systems, and storing these backups in a secure, offsite location. The backups should be tested regularly, to ensure that they are working, and that they can be restored quickly and easily.
Knight Ransomware FAQs
What is Knight ransomware?
Knight is a continuous ransomware-as-a-service (RaaS) campaign active since 2024. It encrypts files and appends the .knight extension. Its ransom message is named HOW_TO_DECRYPT.html. The attackers will ask for the payment in Monero or Bitcoin. Knight operators will scatter through phishing and exploit kits.
What encryption methods are used by Knight ransomware?
Knight uses ChaCha20 for file encryption and Curve25519 for key exchange. They encrypt files in place to avoid detection. Your decryption key is stored on attacker-controlled servers.
What file extension does Knight ransomware append to encrypted files?
Knight adds the .knight extension to encrypted files. For example, “report.pdf” becomes “report.pdf.knight”. They will also replace desktop wallpapers with ransom instructions. You will also notice the altered file icons.
How does Knight ransomware gain initial access to a system or network?
Knight exploits vulnerabilities in WordPress plugins and unpatched Exchange servers. They will use phishing emails disguised as invoices or shipping notices. You can also get infected via malicious adware bundles. Compromised RDP credentials are another common entry point.
What tools and techniques does Knight ransomware use for lateral movement?
Knight uses Cobalt Strike beacons for lateral movement. They will exploit SMB protocol weaknesses to spread. Your domain admin accounts are targeted for credential dumping. The ransomware will also use scheduled tasks to deploy payloads across networks.
What are the indicators of compromise (IOCs) for Knight ransomware?
IOCs include files with .knight extensions and ransom notes in HTML format. They will create registry keys under HKEY_CURRENT_USER\Software\Knight. Monitor for unusual PowerShell scripts accessing lsass.exe. Network traffic to 185.153.192.7 is a known C2 server.
How can organisations detect a Knight ransomware infection early?
You can detect Knight by monitoring for abnormal file-locking patterns. There are alerts for Cobalt Strike beacon activity. They will leave traces in Windows Event Logs (ID 4688). Use SIEM tools to flag unauthorised registry modifications.
What security controls help prevent Knight ransomware attacks?
You should turn off unnecessary SMBv1 protocols and patch web-facing applications within 48 hours. There are intrusion detection systems (IDS) that block exploit kit traffic. Restrict PowerShell execution in non-admin accounts. Regular backups stored offline are good.
Can endpoint detection and response (EDR) tools identify Knight ransomware activity?
Yes, EDR tools can flag Knight’s file encryption behavior. They will detect malicious PowerShell scripts and Cobalt Strike artifacts. You can use SentinelOne Singularity XDR Platform to block unsigned binaries from running. It can help you identify and fight against this ransomware strain and stop its encryption.