The Good | U.S. Indicts Tax Fraud Phisher & Cryptomixer Founders for Laundering Millions
Nigerian-based Chukwuemeka Victor Amachukwu was extradited this week from France to the U.S. to face multiple charges including identity theft, wire fraud, and hacking. Between 2019 and 2021, Amachukwu and his co-conspirators launched spear phishing attacks on U.S. tax preparation businesses, stealing personal data used to file fraudulent IRS tax returns and SBA loan applications.
The schemes netted over $3.3 million, with $2.5 million in stolen tax refunds and $819,000 from fake SBA loans. Separately, Amachukwu ran a bogus investment scheme involving fictitious standby letters of credit. Victims were misled into investing millions, which he pocketed. He currently faces six charges, with potential a sentence up to 20 years per wire fraud count plus a mandatory two years for identity theft while the U.S. is seeking forfeiture of all illicit gains.
Samourai Wallet founders Keonne Rodriguez and William Lonergan Hill have both pleaded guilty to laundering over $200 million in criminal proceeds through their cryptocurrency mixing service. From 2015 to 2024, their tools, Whirlpool and Ricochet, enabled anonymous Bitcoin transactions to process over 80,000 BTC linked to breaches, spear phishing schemes, dark web markets, and DeFi-related fraud. Rodriguez and Hill promoted Samourai as a means to conceal illicit funds, even advising hackers to use it.
They were arrested in April 2024 and charged with operating an unlicensed money-transmitting business and money laundering, facing up to 25 years in prison. So far, both have agreed to forfeit over $237 million as Samourai’s domains and servers were seized and its app removed from the Google Play Store. The mixing services reportedly generated more than $6 million in fees by intentionally helping criminals obfuscate their financial tracks.
The Bad | Fake Trading Bots on YouTube Drain $900K in Crypto via Malicious Smart Contracts
A new report from SentinelLABS uncovers a widespread cryptocurrency scam campaign using malicious smart contracts disguised as trading bots to steal funds. Distributed through aged and seemingly credible YouTube accounts, these scams have already drained over $900,000 USD from victims since early 2024.
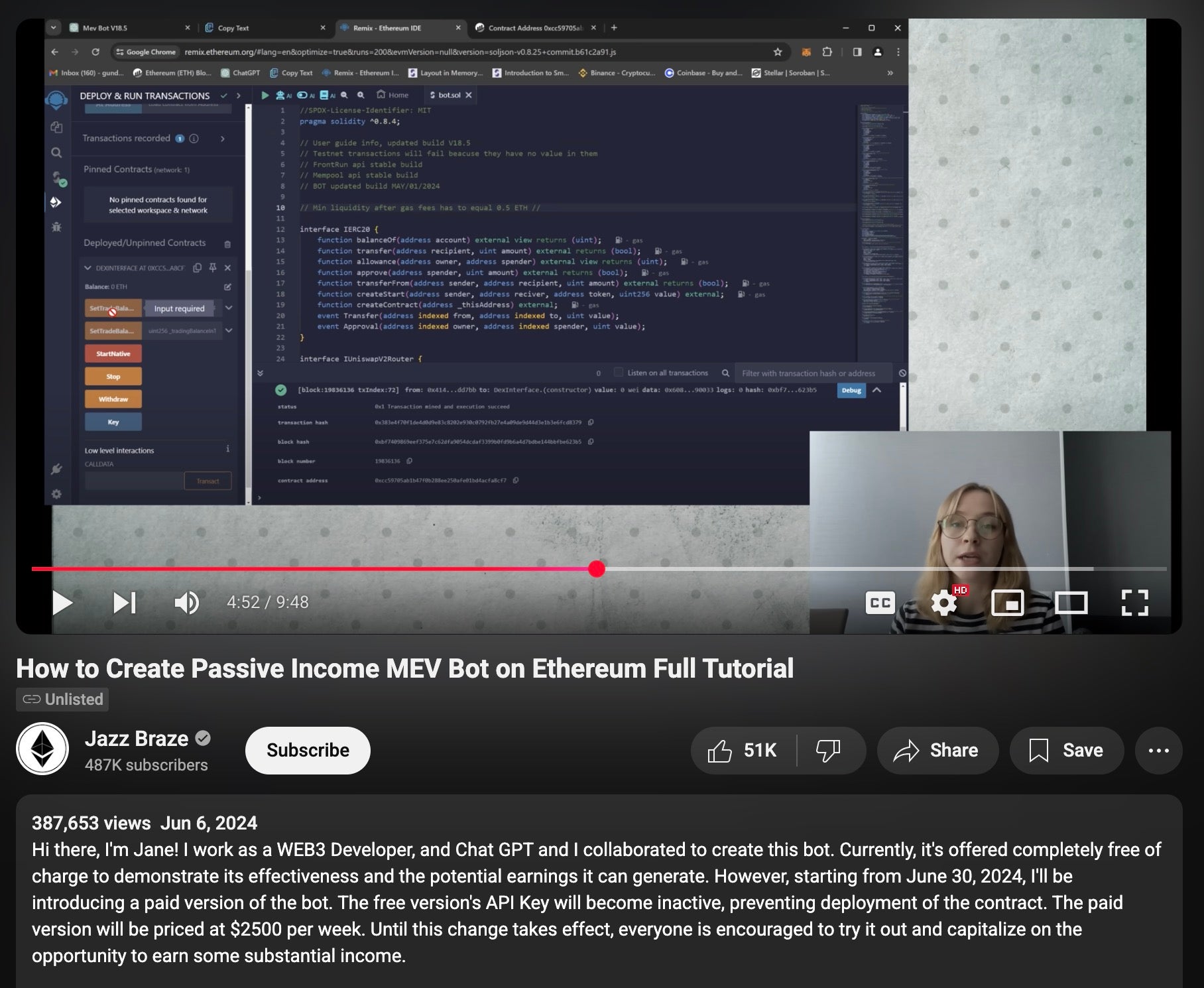
The contracts are written on the Remix Solidity Compiler platform and hide attacker-controlled wallet addresses through obfuscation techniques like XOR encoding, string concatenation, and large number conversion. Victims are tricked into funding these contracts and unknowingly transferring funds to the attacker. Once funded, the contracts redirect ETH to hidden attacker-controlled wallets using embedded logic.
The scam videos often feature AI-generated narrators that are easier and cheaper to produce scams at scale and heavily managed comment sections to fake legitimacy. Accounts like @Jazz_Braze and @SolidityTutorials have all posted highly-viewed tutorials with no obvious signs of malicious intent, while some scams were spread through unlisted videos shared via Telegram.
Scams in this campaign have seen varied success. While some generate a few thousand dollars, one video called “How to Create Passive Income MEV Bot” funneled over $900,000 USD to a single attacker address. The account behind that video had been populated with entertainment shorts over many months, likely to build ranking. The video remains unlisted and is likely shared via other social platforms.
Given the ease of generating AI content and purchasing aged YouTube accounts, the crypto scam ecosystem is increasingly accessible to attackers. SentinelLABS urges crypto users to avoid deploying code promoted by influencer content and to thoroughly validate any tools before use. If a trading bot promises easy profit without transparency, it’s likely a scam – especially in the volatile world of crypto.
The Ugly | Attackers Exploit Possible SonicWall Zero-Day to Deploy Akira Ransomware in Firewalls
SonicWall is investigating a potential zero-day vulnerability after a surge in Akira ransomware attacks targeting its Gen 7 firewalls where SSLVPN is enabled. Multiple incidents have been reported both internally and externally, prompting SonicWall to post guidance for users to disable SSLVPNs where possible, limit SSLVPN access to trusted IPs, enforce MFA, update passwords, and remove inactive accounts. While disabling VPNs may not be feasible for all users, the network security company recommends initiating incident response measures immediately.
Security researchers observed attackers exploiting SonicWall firewalls to access networks, pivoting quickly to domain controllers, disabling Microsoft Defender, and deploying Akira ransomware. The attacks, beginning in late July, have involved tools like AnyDesk, ScreenConnect, and SSH. All confirmed incidents are linked to Akira, with some attackers failing to encrypt systems but gaining unauthorized access.
The suspected vulnerability appears to affect firmware versions 7.2.0-7015 and earlier, particularly on TZ and NSa-series devices. Other researchers posit that a zero-day is likely in play, as attacks have succeeded even with MFA enabled.
The latest updates on the attacks further reveal that Akira affiliates use a Bring Your Own Vulnerable Driver (BYOVD) technique, exploiting Windows drivers like rwdrv.sys and hlpdrv.sys to disable antivirus protection. These drivers enable attackers to manipulate Windows Defender settings and achieve kernel-level access. Additionally, Akira threat actors use SEO poisoning to lure IT professionals to trojanized installers, which deploy Bumblebee malware, enabling remote access, credential theft, and eventual ransomware deployment.
Since emerging in March 2023, Akira has compromised over 250 victims and extorted an estimated $42 million through targeted ransomware campaigns.



