By 2025, 85% of organizations will prioritize cloud computing for IT services. With this growing adoption of cloud infrastructure, Cloud Infrastructure Entitlement Management (CIEM) and Security Information and Event Management (SIEM) emerge as critical tools. CIEM helps organizations manage and secure access to cloud resources, while SIEM provides real-time analysis of cloud-security alerts generated by applications and network hardware.
This article will examine the differences between CIEM vs SIEM, how they work, and why they are essential for organizations.
 What is CIEM?
What is CIEM?
Cloud Infrastructure Entitlement Management (CIEM) (pronounced ‘Kim’), also known as Cloud Identity Governance (CIG), is an automated cloud security solution that helps IT teams and security professionals manage and reduce access risks in cloud environments. It identifies and analyzes permissions across cloud infrastructure, covering both hybrid and multi-cloud setups, ensuring that only the appropriate entities have access to resources.
Gartner coined the CIEM in 2020 in its Hype Cycle for Cloud Security report. The report provides deep insights into the evolving cloud computing scene. It also puts the spotlight on new security challenges and offers organizations advice on bolstering their defenses when they migrate to the cloud.
To better understand CIEM, let us first understand what entitlements are.
What are Entitlements?
An entitlement specifies the tasks a cloud identity is authorized to perform and the resources it can access within an organization’s cloud infrastructure.
These entitlements define a cloud identity’s permissions such as:
- A human user interacting with specific cloud applications or data
- A connected device, like IoT sensors or servers, with limited access to perform its functions
- An AI system acting on behalf of a user, executing tasks or analyzing data within the cloud network
What do CIEMs Actually do?
Before the advent of CIEM solutions, organizations struggled with visibility and control over cloud identities and their associated permissions. As cloud environments expanded, managing access rights became increasingly complex. Security professionals were facing issues around over-permission(ed) identities and security risks. The lack of granular control to enforce security policies and prevent unauthorized access left cloud infrastructures vulnerable.
CIEM effectively manages and safeguards access rights and permissions by enforcing the Principle of Least Privilege (PoLP) on cloud entitlements. CIEM ensures that identities— human users, connected devices, or AI systems—only have the access necessary to perform tasks specific to them. Given that even a single bad actor with excess account privileges can lead to a pulverizing breach (like in the case of this US-based health care provider), adopting CIEM significantly reduces the attack surface and limits potential misuse of permissions.
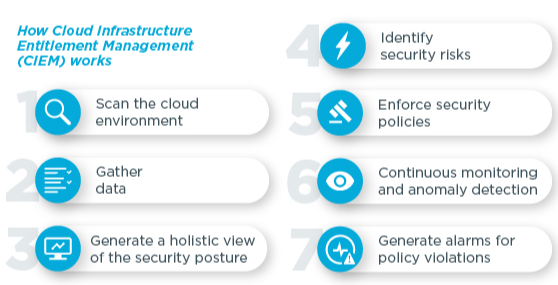
After entitlements define a cloud identity’s permissions, the system ensures that each identity—whether a user or AI—only has access to the specific resources needed for its role. This means that the cloud infrastructure is constantly monitoring who can access what and what not.
For example, if a user only needs access to a particular cloud application, they won’t be granted permission to sensitive databases or resources they don’t require. This minimizes the risk of accidental or intentional misuse of access.
From a user perspective, this structure improves security and simplifies users’ interaction with the system. Users only see and have access to the tools and data necessary for their work, reducing confusion and preventing policy breaches.
For the organization, this leads to a more streamlined, secure environment where roles and access levels are clearly defined. This makes it easier to manage permissions as roles change or users are added and removed from the system.
CIEM provides four essential capabilities:
- Visibility into entitlements
- The rightsizing of cloud permissions
- Advanced analytics
- Compliance automation
As part of a comprehensive modern cloud security strategy, CIEM works with other specialized solutions, such as Cloud Security Posture Management (CSPM) and Cloud Access Security Brokers (CASBs), to provide layered protection across cloud environments.
What are the Main Components of CIEM?
The six main components of CIEM include:
1. Cloud Identity Governance (CIG)
CIEM operates on the core principles of Identity and Access Management (IAM), but it elevates traditional IAM by defining access rights for users and applications in cloud environments. It specifies which cloud resources can be accessed and the actions that can be performed, such as reading, writing, or deleting data.
For example, a cloud-based AI system used for data analysis may be given read-only access to specific datasets required for processing, but it cannot modify or delete the data.
2. Entitlement Visibility
CIEM offers a centralized platform to view all user permissions and entitlements across various cloud environments. This visibility is essential for security teams, IT administrators, and compliance officers.
- Security teams rely on it to detect and remediate potential risks from unauthorized access.
- IT administrators use it to efficiently manage and streamline user permissions across multiple cloud environments, ensuring operational consistency
- Compliance officers benefit from this visibility by ensuring that the organization adheres to regulatory requirements and keeps access controls up to date.
Such visibility is imperative for tracking and understanding who has access to what. It allows organizations to quickly identify and address excessive or outdated permissions that could lead to security vulnerabilities.
For example, an organization uses CIEM to monitor permissions across its cloud platforms, such as AWS, Azure, and Google Cloud. Through the centralized dashboard, the IT administrator can control active access permissions for a former employee. With this visibility, the security team can immediately revoke the outdated permissions, preventing any potential unauthorized access.
3. Least Privilege Enforcement
CIEM rigorously applies the principle of least privilege by constantly monitoring and adjusting user permissions and access rights. Systems and applications are configured to grant minimal initial access, with additional privileges provided only after thorough review and authorization.
Primarily, IT administrators and cloud security teams are responsible for configuring least privilege enforcement within CIEM. They set up systems and applications to provide minimal initial access to users, ensuring that only the essential permissions are granted. This is done by defining specific role-based access controls (RBAC) or policy-based access management rules for each user or system entity.
Once these configurations are in place, the CIEM system continuously monitors user activity and access requests. When a user requires additional privileges, the request is thoroughly reviewed by the security team or an automated policy system, ensuring that access is necessary before approval.
This ongoing monitoring and review process helps maintain strict control over access rights and reduces the risk of over-permission.
The key mechanisms include:
- Role-based access allocation: CIEM enforces strict role-based access controls, assigning permissions based on a user’s job duties. For example, in a healthcare setting, a nurse is given access to patient medical records, while a billing clerk only accesses financial data.
- Temporary privilege elevation: Through Just-In-Time (JIT) controls, CIEM temporarily raises a user’s privileges for specific tasks and then reverts them once the task is completed. For example, a developer may get temporary access to the production environment to fix an issue. Once done, CIEM’s JIT controls automatically revert the privileges to the standard level.
- Fine-grained access controls: CIEM divides cloud resources into smaller segments, allowing for precise permission settings. For example, CIEM segments resources so that HR staff can access only HR data, while Finance is limited to financial records, ensuring needful and precise permissions only.
4. Advanced Analytics
CIEM solutions equip cyber security teams with advanced analytics, such as machine learning and User Entity Behavior Analytics (UEBA), to evaluate entitlements and detect unusual or suspicious access patterns. For example, CIEM uses machine learning and UEBA to flag unusual behavior, such as a sales employee trying to access financial data and alerting security teams to investigate potential threats.
5. Access Policy Implementation
CIEM, when integrated with Identity Governance and Administration (IGA) systems, enables the detailed definition and enforcement of access policies tailored to an organization’s specific requirements. For example, a contractor only has access to project-specific resources for a limited time. Once the project ends, the system automatically revokes access based on predefined policies.
These policies can be designed based on various criteria, such as:
- Role-specific permissions: Permissions are linked to specific job roles. This ensures users are granted access rights that align with their responsibilities.
- Location-based access controls: CIEM can restrict access based on user’s geographical locations, aiding compliance with regional data protection regulations.
- Time-based access controls: Permissions can be restricted during non-operational hours or sensitive periods.
- Device-specific access: Access can be limited to authorized devices, reducing the risks associated with potentially compromised hardware.
6. Privileged Account Monitoring and Control
CIEM works in tandem with Privileged Access Management (PAM) and Just-In-Time (JIT) systems to secure accounts with elevated access levels. By providing insights into cloud entitlements, CIEM helps these systems detect anomalous behavior and mitigate potential breaches.
What is SIEM?
Security Information and Event Management (SIEM) (pronounced ‘Sim’) is a technology that combines Security Information Management (SIM) and Security Event Management (SEM) to monitor real-time security threats and analyze data across networks, servers, and applications.
It helps identify abnormal activities, such as unauthorized access attempts or unusual network traffic. Additionally, SIEM offers tools for managing incidents and conducting post-attack analysis, aiding businesses in maintaining their overall security posture.
The term SIEM was introduced by Gartner in 2005, signifying the formal acknowledgment of a technology that merges Security Information Management (SIM) and Security Event Management (SEM) into a unified solution for comprehensive security management.
SIEM effectively monitors and analyzes security events across an organization’s IT infrastructure by aggregating and correlating log data from various sources. These sources can include:
- User activity logs
- Network devices
- Applications
- Security Hardware
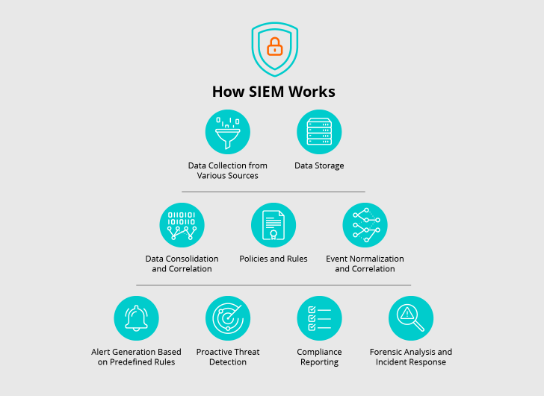
SIEM systems gather and analyze logs from a diverse array of sources, including:
- Endpoint security tools
- Intrusion detection (IDS) and intrusion prevention (IPS) systems
- Firewalls and Unified Threat Management (UTM) systems
- Web filtering solutions
- Application servers
- Wireless access points
- Routers
- Databases
- Switches
- Cloud service providers
- Honeypots
- Identity and access management (IAM) systems
What are the Main Components of SIEM?
Since SIEM solutions rose from the amalgamation of SIM and SEM technologies, they encompass capabilities, such as:
- Data aggregation and normalization
- Event correlation
- Real-time monitoring and alerting
- Incident response and management
Let us discuss this in detail.
1. Log Management
Log management is a cornerstone of SIEM. It encompasses collecting, storing, and analyzing log data from various sources within an organization’s network.
This data includes:
- User activities
- System operations
- Error messages, creating a detailed timeline of events
Effective log management standardizes and organizes diverse log data into a consistent format, facilitating precise analysis and threat detection.
For example, using SIEM’s log management capabilities, a network admin monitors user login logs to detect unusual activity, such as multiple failed login attempts from a single IP address.
2. Real-time Security Event Monitoring (SEM)
SEM consolidates, and correlates log data to detect suspicious traffic patterns and anomalies in real time. For example, SEM detects a spike in outbound traffic from a server, triggering an alert that prompts the security team to investigate and stop a potential data exfiltration attempt.
SEM tools generate alerts based on predefined criteria such as– failed login attempts, unusual network traffic spikes, unauthorized access to sensitive files, or port scanning activities. This enables security teams to respond quickly to such threats.
3. Security Information Management (SIM)
SIM focuses on the long-term storage, analysis, and reporting of security-related data. It provides historical context for security events, allowing organizations to perform forensic investigations and meet compliance requirements.
For users, the benefit of SIM lies in ensuring their data remains secure, as historical analysis helps identify and address long-term threats while maintaining regulatory compliance. For security teams and IT managers, SIM provides valuable insights into past security events, enabling forensic investigations to uncover attack patterns.
An example of SIM as a solution is– how a security analyst uses SIM to review logs from six months ago to trace the source of a data breach, providing critical information for forensic analysis.
4. Event Correlation
Event correlation links related log entries to identify patterns indicative of security incidents.
For example, SIEM correlates related log entries such as multiple failed login attempts from different IP addresses and an unexpected file download from a sensitive database, uncovering a coordinated attack aimed at breaching the system. Security teams link these events using SIEM and detect and respond to threats early.
By analyzing data from multiple sources, SIEM systems can correlate events to uncover complex attack vectors and offer actionable insights for incident response. This capability helps security managers detect threat detection by revealing connections between seemingly unrelated events.
5. Alerting and Notification
SIEM systems include alert mechanisms that inform security teams of detected incidents based on correlated events. For instance, SIEM generates a high-priority alert for the security team when it detects suspicious activity, such as an unauthorized user accessing sensitive data. These alerts are prioritized by severity, helping teams focus on the most critical threats. Automated notifications ensure a prompt response, minimizing the window of opportunity for attackers.
6. Incident Response and Management
This component involves the processes and workflows for handling security incidents. For instance, after receiving an alert, the SIEM system opens an incident ticket and assigns it to the security team, automatically tracking the investigation and ensuring all response steps are documented.
SIEM systems streamline:
- Incident tracking
- Ticketing
- Coordination among security teams
Automating routine tasks and documenting responses improves incident management efficiency and promotes collaboration, ensuring a cohesive approach to addressing threats.
7. Integration of Threat Intelligence
SIEM solutions can incorporate threat intelligence feeds to enhance detection capabilities. For example, it integrates a feed reporting a new phishing campaign, allowing the system to detect and block similar attacks targeting the organization’s email servers.
By integrating external data on known threats, vulnerabilities, and attack patterns, SIEM systems improve their ability to identify and respond to emerging risks. This integration provides a richer context for security events, leading to more informed analysis and decision-making.
The Industry’s Leading AI SIEM
Target threats in real time and streamline day-to-day operations with the world’s most advanced AI SIEM from SentinelOne.
Get a DemoCIEM vs SIEM: What is the Difference?
Here’s a comparative table highlighting the differences between SIEM vs CIEM.
| Features | CIEM | SIEM |
|---|---|---|
| Primary Focus | Managing and securing cloud permissions and entitlements | Monitoring, analyzing, and responding to security events and incidents across IT environments |
| Scope | Primarily focused on cloud environments, particularly multi-cloud and hybrid setups. | Broad scope covering on-premise, cloud, and hybrid IT infrastructures. |
| Core Functionality | Ensuring the principle of least privilege by managing user and application access rights. | Correlating and analyzing security events from various sources to detect potential threats. |
| Data Management | Manages access controls, user entitlements, and permissions across cloud services. | Aggregates normalizes, and analyzes log data from applications, networks, servers, etc. |
| Threat Detection | Focuses on identifying misconfigurations, excessive privileges, and unauthorized access in the cloud. | Detects and alerts on a wide range of security threats, including network intrusions, malware, and insider threats. |
| Incident Response | Adjusts entitlements and permissions to mitigate potential security risks in cloud environments. | Generates alerts and supports incident response workflows, including automated responses. |
| Integration | Integrates with identity governance, PAM, and cloud security tools. | Integrates with threat intelligence feeds, AI, and various security controls for enhanced threat detection. |
| Compliance & Reporting | Supports compliance by ensuring proper access controls and generating reports on cloud entitlements. | Provides extensive compliance reporting capabilities, aligning with regulatory requirements like GDPR, HIPAA, etc. |
| Target Users | Cloud security teams, identity, and access management specialists. | Security operations centers (SOCs), cybersecurity analysts, and IT security teams. |
In simple words, CIEM is like that office admin who supports your activities and gives you the keys to the rooms you’re allowed to enter. You can’t access the areas you aren’t supposed to.
On the other hand, SIEM is like a security guard who watches over all the office rooms through surveillance cameras. If they spot suspicious activities, they raise an alarm and take action.
What are the Key Benefits of CIEM vs SIEM?
The key benefits of SIEM vs CIEM are as follows.
CIEM Benefits
- Optimized cloud security: Secures cloud environments by managing and fine-tuning access permissions; it benefits the user by providing a secure cloud environment, ensuring they only have access to the resources they need.
- Risk reduction: Reduces the risk of unauthorized access and data breaches, particularly in complex, multi-cloud infrastructures.
- Compliance support: Provides detailed oversight of cloud entitlements and access controls, aiding in compliance with cloud-specific regulations such as GDPR, HIPAA, and CCPA.
- Operational efficiency: Automating access rights management boosts efficiency by easing the administrative load on IT teams and lowering the risk of human error. Freed from routine tasks, IT teams can redirect their efforts toward enhancing security measures and optimizing system performance.
SIEM Benefits
- Comprehensive security framework: Secures cloud, on-premise, and hybrid environments by identifying and linking security incidents, ensuring consistent protection across all platforms where user data is stored.
- Real-time threat detection: Detects and responds to threats quickly, reducing the risk of damage from cyberattacks through faster monitoring and analysis.
- Compliance reporting: Provides logging and auditing to meet regulations like GDPR, HIPAA, and PCI DSS, ensuring user data is protected by compliance with key laws.
- Centralized security operations: Streamlines security management by unifying incident monitoring and response, minimizing downtime and improving user experience.
What are the Limitations of SIEM vs CIEM?
Understanding the limitations of SIEM vs CIEM is crucial for businesses to make informed decisions about their cloud security strategy. While both tools provide essential security functions, knowing where each falls short can help organizations address gaps and choose the right solutions to protect their data.
Here are the limitations of SIEM compared to CIEM:
SIEM Limitations
- High volume of alerts: SIEM tools often generate many alerts, including false positives. This can overwhelm security teams and lead to alert fatigue, where real threats may be overlooked.
- Limited cloud-specific capabilities: While SIEM provides broad security coverage, it may not offer the same level of granularity in managing cloud-specific entitlements and access controls as CIEM does.
- Log in threat detection: SIEM systems can sometimes struggle with real-time threat detection, especially if they are not properly optimized, or if the organization’s network generates a high volume of data.
- Dependency on correlation rules: SIEM relies heavily on predefined correlation rules, which need regular updates to keep up with evolving threats. If these rules are outdated or improperly configured, the system may miss new or sophisticated attacks.
CIEM Limitations
- Narrow focus: CIEM is designed explicitly for managing access and entitlements in cloud environments. That means it doesn’t provide comprehensive security coverage for on-premise or hybrid IT infrastructures.
- Limited threat detection: Unlike SIEM, CIEM does not focus on monitoring and correlating security events across the entire IT landscape. This makes it less effective in detecting broader security threats or incidents.
- Dependency on cloud environments: CIEM relies heavily on cloud infrastructure, so its effectiveness diminishes in environments where on-premise systems or hybrid solutions are predominant.
- Integration challenges: CIEM may face integration challenges when working alongside other security tools and systems, especially in diverse IT environments with multiple cloud service providers.
- Less comprehensive reporting: While CIEM offers strong compliance support within cloud environments, it may not provide the same level of detailed, cross-environmental reporting and forensic capabilities as SIEM systems.
When to Choose Between CIEM vs SIEM
Here’s the deal: Opt for CIEM if you follow a cloud-first strategy and are looking for specialized solutions for managing cloud identities and entitlements. Choose SIEM if you operate in a hybrid environment, as SIEM offers a comprehensive solution for aggregating and analyzing security data across on-premises and cloud resources.
But there’s more to it.
Here’s a detailed analysis of some use cases:
- Cloud-centric needs: CIEM is purpose-built for handling the nuances of cloud environments. It tackles challenges like dynamic permissions management, distributed workloads, and multi-cloud compliance by offering tools for controlling cloud identities and entitlements.
SIEM, while comprehensive, lacks the specialization needed to efficiently manage cloud-specific permissions and access configurations.
Which to Choose?
If your infrastructure is cloud-first, CIEM offers the necessary granularity to manage cloud identities and security, aligning with the dynamic nature of cloud-native architectures.
- Hybrid infrastructure: SIEM thrives in hybrid environments, consolidating data from both on-premises and cloud resources into a single pane of visibility. It allows you to monitor security events across your entire infrastructure, offering insights that bridge both traditional and cloud systems.
CIEM focuses solely on cloud resources, limiting its utility in environments with significant on-premise infrastructure.
Which to Choose?
In a hybrid setup, SIEM is the more effective solution because it unifies security monitoring across all environments, ensuring no gaps in visibility.
- Threat detection proficiency: SIEM employs advanced analytics, behavioral analysis, and machine learning to detect potential threats, including anomalies and suspicious activities across a diverse range of environments. Its detection capabilities span cloud assets.
CIEM, by contrast, is designed to identify misconfigurations and over-provisioned permissions, particularly within cloud environments, but lacks the broader threat detection scope.
Which to Choose?
For comprehensive threat detection that includes anomaly detection across multiple environments, SIEM’s capabilities are more aligned with the needs of a thorough security operation.
- Incident response capabilities: SIEM offers extensive incident response functionalities, including integration with security tools, automated workflows, and case management systems. These features are critical for quick identification and resolution of security events.
CIEM helps streamline cloud-specific incident management, particularly around cloud permissions but doesn’t provide the broader incident response framework that SIEM offers.
Which to Choose?
SIEM is the superior choice when incident response speed and efficiency are crucial, especially in environments that span cloud and on-premise resources.
- Cloud security program maturity: SIEM serves as the foundational security layer for organizations that are just beginning their cloud journey, offering wide visibility across both cloud and traditional environments. As cloud adoption progresses, integrating CIEM enhances your cloud security posture by addressing cloud-specific identity and entitlement risks.
CIEM, while specialized, might be overkill in the early stages of cloud adoption, where broader visibility is still necessary.
Which to Choose?
SIEM is ideal for early-stage cloud environments due to its comprehensive monitoring, while CIEM becomes increasingly valuable as your cloud infrastructure matures and demands more focused cloud security management.
Wrapping Up: Integrating CIEM and SIEM for Robust Security
Both CIEM and SIEM are essential in securing different aspects of an organization’s infrastructure. While CIEM focuses on managing cloud identities and permissions, SIEM addresses real-time threat detection across systems. In cloud-based environments, where identities, permissions, and security events are more fluid and distributed, integrating these tools provides a comprehensive approach.
Together CIEM controls cloud-specific access risks, while SIEM continuously monitors for security threats across the entire network, creating a stronger defense against modern cloud and hybrid infrastructure threats.
By combining these tools with SentinelOne, organizations can proactively manage their security posture, ensuring that both cloud-specific challenges and broader IT security needs are effectively addressed.
With SentinelOne, organizations can:
- Seamlessly integrate SentinelOne Singularity AI SIEM and Singularity Cloud Native Security which has CIEM capabilities to achieve a unified security posture that combines advanced threat detection with a comprehensive access management
- Experience unparalleled visibility and control over your servers, networks and cloud environment
- Allow for real-time threat detection and proactive incident response, ensuring that your organization stays ahead of emerging threats.
Take a demo with SentinelOne today to experience the seamless integration of CIEM vs SIEM in securing your organization’s digital environment.
Conclusion
CIEM and SIEM are both essential towards achieving holistic cloud security. One manages entitlements while the other handle logs for analysis. CIEM controls address cloud-specific risks and can proactively manage cloud security posture. While CIEM is great for the early stages of cloud adoption, SIEM is great for broadening visibility. We recommend using them both for best results.
FAQs
A CIEM tool manages and optimizes cloud-specific permissions and entitlements. This ensures that users and applications have only the access they need in cloud environments.
IAM manages identities and access across all environments, while CIEM controls and optimizes permissions within cloud environments.
CIEM is a security practice that manages and secures cloud permissions and entitlements. It helps reduce the risk of unauthorized access in cloud environments.
IAM controls user access and identities. SIEM, on the other hand, monitors, analyzes and responds to security events across an organization’s IT infrastructure.

