The Good | Law Enforcement Arrest Extortionist, Phobos Affiliate & Financial Scammers
A Dutch man was arrested this week after he allegedly downloaded confidential documents mistakenly shared with him and tried to extort authorities by refusing to delete them without compensation. The man kept the files, prompting a hacking investigation and a search of his home. Authorities say knowingly accessing misdirected, sensitive data constitutes computer trespass and emphasize that recipients must report such mistakes and avoid keeping unauthorized materials.
In Poland, authorities detained an individual tied to the Phobos Ransomware-as-a-Service (RaaS) operation, seizing stolen credentials, credit card data, and server access information. The arrest, part of Europol-coordinated “Operation Aether”, specifically targets the group’s affiliates and infrastructure.
Investigators found files enabling unauthorized system access and confirmed that the suspect communicated with other Phobos actors via encrypted messaging. He now faces charges for producing and distributing hacking tools, facing up to five years in prison. The international operation is part of a wide effort to disrupt sprawling Phobos ransomware networks and warn potential targets of ongoing and emerging attacks.
A joint effort coordinated by Interpol’s African Joint Operation against Cybercrime (AFJOC) brought together various agencies to arrest 651 suspects and recover over $4.3 million in a coordinated crackdown on investment fraud, mobile money scams, and fake loan schemes. Tracked as “Operation Red Card 2.0”, law enforcement across 16 countries identified 1247 victims and targeted cybercrime linked to $45 million in losses.
Authorities seized 2341 devices, shut down 1442 malicious sites, and dismantled fraud networks in Nigeria, Kenya, and Côte d’Ivoire. Cross-border cooperation continues to be a key factor in combating organized cybercrime within regions of the world that are still rapidly digitizing.

The Bad | CRESCENTHARVEST Targets Protest Supporters in New Espionage Campaign
New research has brought to light a cyber espionage campaign, dubbed “CRESCENTHARVEST”, that targets Farsi-speaking supporters of Iran’s ongoing anti-government protests. Active since early January, the operation uses protest-themed lures to trick victims into launching malware designed for long-term surveillance and data theft.
The attackers distribute malicious archives filled with authentic protest images, videos, and reports in Farsi to appear credible and emotionally compelling, particularly to individuals seeking updates during internet blackouts and restricted media coverage.
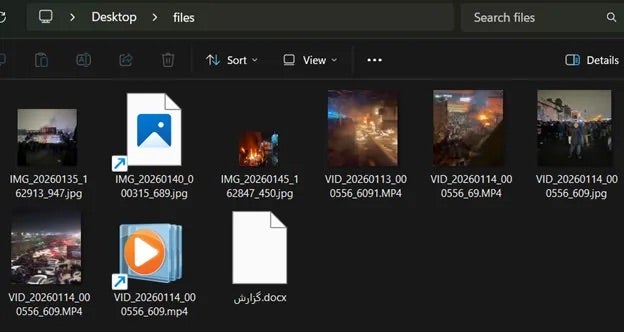
Inside the archive are Windows shortcut files disguised as media using double extensions such as *.jpg.lnk and *.mp4.lnk. When opened, the file runs PowerShell commands to download additional payloads while displaying a harmless image or video to avoid suspicion. The infection chain then leverages a legitimate, signed system binary to sideload rogue libraries, ultimately installing a previously undocumented remote access trojan (RAT) that doubles as an information stealer.
Once deployed, the malware can execute commands, log keystrokes, capture browser credentials, harvest cookies, extract Telegram data, and collect extensive system information. It also identifies installed security tools, allowing the actors to adjust their behavior to remain undetected. The researhers say communication with command-and-control (C2) servers blends into normal web traffic, enabling persistent espionage.
Although the campaign is currently unattributed, the tactics and targeting strongly suggest alignment with Iranian state-backed interests. Researchers believe attackers likely relied on spearphishing or prolonged social engineering, sometimes building up relationships with targets over extended periods before delivering the malicious files.
The operation reflects a broader pattern of politically-motivated digital surveillance operations aimed at journalists, activists, researchers, and diaspora communities as attackers continue to piggyback off of the turbulence of geopolitical crises.
The Ugly | Infostealers Exfiltrate OpenClaw AI Assistant’s Operational Secrets
The rapid rise of OpenClaw, a locally running agentic AI assistant, has introduced a new class of security risk: malware that targets the assistant itself. Because the framework stores persistent memory, configuration data, and authentication material on the user’s device, it effectively becomes a vault of API keys, tokens, private keys, and sensitive personal context. Security researchers have now observed infostealing malware exfiltrating these files (openclaw.json, device.json, and soul.md) in real-world infections, marking a move from traditional credential theft techniques toward hijacking the inherent identities and capabilities of autonomous agents.
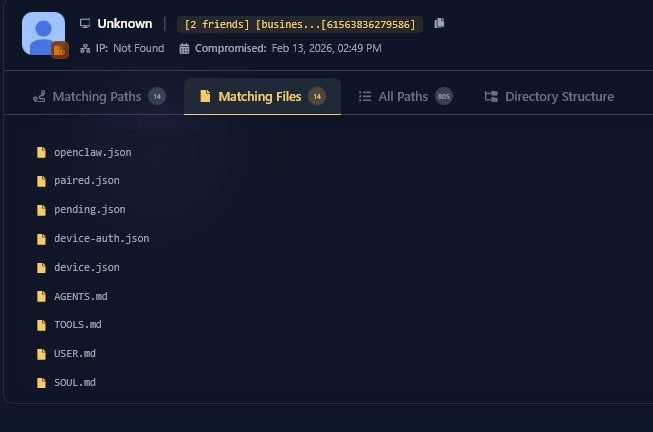
In this first in-the-wild instance, the malware did not exploit a vulnerability in the assistant. Instead, it used broad file-harvesting techniques that scan systems for keywords such as “token” and “private key”. This approach allows attackers to capture critical configuration files, including those that enable remote connections, device impersonation, and access to encrypted logs or cloud services. The stolen data could permit full takeover of the agent’s functions, effectively granting bad actors the same authority the assistant holds across email, apps, and online platforms.
Researchers warn that as agentic assistants become embedded in professional workflows, attackers will increasingly develop specialized tooling to parse these environments and weaponize them. Additional findings on this growing attack surface includes exposed instances vulnerable to remote code execution (RCE) and supply chain risks in community “skill” repositories.
In response to these emerging risks, Prompt Security from SentinelOne has introduced ClawSec and OneClaw, designed specifically for the agentic era to provide deep visibility into autonomous agent behavior and harden them from within. These tools help organizations monitor, control, and secure personal AI assistants such as OpenClaw, Nanobot, and Picoclaw before compromised agents can be leveraged as trusted insiders.


